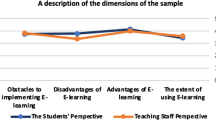
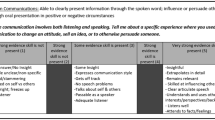
Abstract
This paper describes experiences in organizing and running an internship component of an undergraduate program in information systems security. In 2004, Sheridan College Institute of Technology and Advanced Learning introduced a novel Bachelor in Applied Information Sciences (Information Systems Security) program. The intent was to educate well-rounded specialists in the field and provide them with valuable work experience during the 8-month long co-op term. The research presented here is based on the co-op officer reports, statistics reported by the co-op office, interviews with the students and other anecdotal data mainly collected through conversations with the involved parties. Besides providing facts that speak to the quality of the program and appropriate organization of the job placements, the authors critically examine successes and challenges encountered in this process. Comparison with other information systems security postsecondary programs in Ontario, Canada, is given based on type of program, characteristics and focus of curriculum content and length of internship.
Similar content being viewed by others
Notes
Program Coordinator is a faculty member in charge of curriculum development, student enrollment issues, promotion of the program and contacts with partners.
PAC is a group of professionals, community members and alumni, who at least bi-annually meet with the Program Coordinator to exchange information about developments in the ISS field that may affect the program. They have a voting power over the program changes and provide valuable connections with the industry and community in general.
Sheridan offers one-term ‘bridging’ option in order to facilitate the direct entry into the later terms of the program to as many qualified applicants as possible. See: Ralevich and Martinovic (2010).
References
Ayoub, R., Chin, A., & Parberry, I. (2005). A new model for a student cyber security organization. Proceedings of the 2nd Annual Conference on Information Security Curriculum Development, September 23–24, pp. 12–15.
Bailey, T., Hughes, K., & Barr, T. (2000). Achieving scale and quality in school-to-work internships: Findings from two employer surveys. Educational Evaluation and Policy Analysis, 22(1), 41–64.
Borg, W. R., & Gall, M. D. (1989). Educational research: An introduction (5th ed.). New York: Longman.
Career Development Center of the Southern Illinois University. (2008). Internship Online Information, retrieved February 20, 2009, from www.siue.edu/careerdevelopmentcenter.
CERIAS. (2001). Security Visionary Roundtable Call to Action, retrieved March 30, 2008, from www.cerias.purdue.edu/news_end_events/events/securitytrends/accenture_exec_sum_1q2001.pdf.
Creswell, J. W. (2005). Educational research: Planning, Conducting and Evaluating Quantitative and Qualitative Research. (2e) New Jersey: Pearson Education, Upper Saddle River.
Crowley, E. (2003). Information system security curricula development. Proceedings of the 4th Conference on IT Curriculum, October 16–18, pp. 249–255.
Krippendorff, K. (2004). Content analysis: An introduction to its methodology (2nd ed.). Thousand Oaks: Sage Publications.
O’Leary, M. (2006). A laboratory based capstone course in computer security for undergraduates. ACM SIGCSE Bulletin, 38(1), 2–6.
Perrone, L. F., Auberdene, M., & Meng, X. (2005). Approaches to Undergraduate Instruction in Computer Security. Proceedings of the American Society for Engineering Education Annual Conference and Exposition, ASEE 2005, retrieved March 30, 2009, from http://www.ists.dartmouth.edu/library/116.pdf.
Ralevich, V., & Martinovic, D. (2007). Experience of designing and implementing an applied degree program in Information Systems Security. Proceedings of the i-Society 2007, October 7–10, pp. 24–29.
Ralevich, V., & Martinovic, D. (2010). Designing and implementing an undergraduate program in information system security. Education and Information Technology, Springer. doi:10.1007/s10639-010-9123-y.
Schlichting, C., & Mason, J. (2005). The computer curriculum and certification: A proposal. Journal of Computing Sciences in Colleges, 20(4), 84–91.
Stockman, M., Christopherson, C., Said, H., & Nyland, J. (2004). An Implementation of a Networking Track in an Information Technology Degree Program. Proceedings of the 5th Conference on Information Technology Education (formerly CITC), October 28–30, pp. 138–143.
Wieler, S. S., & Bailey, T. R. (1997). Going to scale: Employer participation in school-to-work programs at LaGuardia community college. Educational Evaluation and Policy Analysis, 19(2), 123–140.
Whitman, M., & Mattord, H. (2004a). Designing and teaching information security curriculum. Proceedings of the InfoSecCD Conference ’04, October 8, pp. 1–7.
Whitman, M., & Mattord, H. (2004b). A draft curriculum model for programs of study in information security and assurance, retrieved March 30, 2009, from http://infosec.kennesaw.edu/InfoSecCurriculumModel.pdf.
Author information
Authors and Affiliations
Corresponding author
Appendix A
Appendix A
1.1 A.1 Interviews with Duncan, Neil and Mick (these names are fictitious), the BAISc (ISS) Students
1.1.1 A.1.1 Duncan
Duncan is a “late bloomer” in the program. He is the one who made the most visible progress during the program. In the beginning, he was very frustrated as he did not have enough self-confidence. As he moved through the program, he found his niche in database design and security as well as in project management courses. He developed excellent organizational skills, managed and coordinated work of the large project team and made major contributions to the school graduation project.
During the co-op, Duncan proved himself to be a go-getter. He worked a lot and always asked for more: “I would come up with the situation and I would go: ‘Can I deal with this?’, and they would let me do it.” The course that helped him most in his placement was a malware–related course, in particular a section on intrusion detection: “At work, we had an outbreak and I was the one able to detect the virus and send it to MacAfee; they found it—it was signature-based.” He also very much appreciated database design, management, and security courses, and IS security risk-assessment courses.
On his placement, Duncan “got to apply pretty much everything [that he learned in school]”.
I had to do some crypto stuff; identity management was a big one; the project was launching IPS sensors across the main offices—applied what we learned in networking courses... A little bit of analytical skills that we picked up along the way; just in terms of doing things quickly—I used a lot of Access database; made the actual routine of user access reviews, basically, tripled the efficiency of what we normally take .... and, updating documentation as we go along. All what we learned about general security practices got filtered into those procedures that were used for reviews.
Duncan’s organization was “big on meetings.” Every week there was a video and teleconference team meeting. This forced Duncan “to learn how to deal with people ... how to communicate with the group.”
Not without pride, Duncan said: “I might have been a co-op student, but sometimes they allowed me to do more like an actual employee in the decision-making process. It probably took me about 3.5–4 months when I started showing that I know a little bit–then it was open doors.”
Duncan actually enjoyed the co-op: “I love 8 months. By the time you build confidence, it is 2–3 months. By the time I got to do something really interesting, I was 5 months in.”
Apart from the length of the co-op which was unusually long for this school, the biggest concern was the extent to which it was difficult for students to go back to school, after being away from it for 8 months. For Duncan, this worked well: “When I was returning from the co-op, I was super interested as I could relate everything that I did on co-op to the course material. As I was learning new content, I would go: ‘Oh man, I could have used that! Oh, I used that! Oh, I learned that!’”
1.1.2 A.1.2 Neil
Neil is academically one of the best students in his program. He is extremely curious and systematic. Prior to starting BAISc (ISS), he graduated from a 2-year college program with an emphasis on software programming. From the very beginning, he understood the difficulty and rigor of the program. His attitude was always to strive for excellence. He was known for helping other students by organizing study groups.
Neil’s co-op experience was also very positive: “After the company found out what are our skills, our usefulness was broadened to include other types of tasks that they originally did not think we will be suited for. It was of the sort ‘Oh, wow, you could do this, would you mind helping us out?’” For him, the three most useful courses in the program were Computer Forensics, as closely related to his placement; Operating Systems Design, “because when you are doing forensics it helps to know what kind of types of thousand logs OS generates”; and Algorithms and Data Structures that “came really handy,” during the tasks that involved time consuming searches.
Neil’s placement allowed him to use analytic skills gained in school, as “in a lot of the courses there was a need for proof and validity of numbers of data that we had to collect; being able to prove that they were generated without the bias–the need for accountability.”
However, while on placement, Neil had to alter the way he wrote his reports: “Now I was writing reports for accountants and lawyers, and I had to adjust the way how I normally write. I had to be able to explain computer concepts in a simpler way—by using analogy—which is something that I would not normally do.”
Asked about the length and position of the co-op, Neil said: “In terms of my work experience, [8-month co-op] helped me a lot, but when I had to come back to school, it hit me a bit. I lost a bit of academic edge.” He also liked going back to school after the co-op: “it was nice to bring your work experience to your 4th year. Also, my partner and I had a graduation project that was a direct result of our co-op.”
Neil proposed that instructors in the program encourage students to speak and write reports “in different formats.” For example, “one that you would give to someone in charge of IT, who knows the technical details; or a lawyer. Knowing what changes would be appropriate. Being able to identify the needs of that audience. The professor could be saying: ‘Assume in this report that I am the customer.’ Next time it can be for the IT manager and so on.”
1.1.3 A.1.3 Mick
Mick came directly to the third year of the program through bridging. Prior to that, he graduated from a 3-year Computer Science Technology (CST) program, also at Sheridan. In the 2 years he spent in the BAISc (ISS), he demonstrated tremendous improvement and suitability for the program, both academically and socially.
He described his co-op experience as being very positive: “it was interesting how the people were impressed by how much I know. I would start to recommend some forensics tools. ‘Pick this one,’ I would say. ‘Which school did you go to?’ ‘Sheridan’ ‘And you know this?’ ‘Yes, I had a class on forensics.’ ‘Ah.’ And everyone else sitting by the table did not know what is going on.”
Three courses that prepared Mick most for his co-op placement were Operating Systems Design, Database Security, and ISS Audit. Mick found it useful to apply his school knowledge in tasks related to “OS hardening,... programming in general, statistics, and dealing with auditors.”
When asked to specify “on-the-job” activities that helped him gain the most knowledge in his career field, Mick mentioned “reverse engineering stuff,” because he often dealt with non-proprietary software that needed to be tested and fixed; and working with different people, which helped him to further develop communication and negotiation skills. For example, he learned to “be nice, watch people’s toes, and be diplomatic.”
His organization was “big on training.” Mick often went on training workshops and professional conferences. Based on his co-op experience, Mick suggested putting “more emphasis [in the program] on document writing with regards to security, like process documentation.”
In retrospect, both Neil and Mick received job offers from their co-op employers. After finishing with the course work, they soon started working full time.
Rights and permissions
About this article
Cite this article
Ralevich, V., Martinovic, D. Organizing and implementing the internship component of undergraduate programs in IS Security. Educ Inf Technol 17, 27–48 (2012). https://doi.org/10.1007/s10639-010-9142-8
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10639-010-9142-8