Abstract
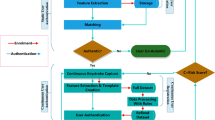
In digital home networks, it is expected that independent smart devices communicate and cooperate with each other, without the knowledge of the fundamental communication technology, on the basis of a distributed operating system paradigm. In such context, securing the access rights to some objects such as data, apparatus, and contents, is still a challenge. This paper introduces a risk-based authentication technique based on behavioral biometrics as solution approach to tackle this challenge. Risk-based authentication is an increasingly popular component in the security architecture deployed by many organizations to mitigate online identity fraud. Risk-based authentication uses contextual and historical information extracted from online communications to build a risk profile for the user that can be used accordingly to make authentication and authorization decisions. Existing risk-based authentication systems rely on basic web communication information such as the source IP address or the velocity of transactions performed by a specific account, or originating from a certain IP address. Such information can easily be spoofed, and as such, put in question the robustness and reliability of the proposed systems. In this paper, we propose a new online risk-based authentication system that provides more robust user identity information by combining mouse dynamics and keystroke dynamics biometrics in a multimodal framework. We propose a Bayesian network model for analyzing free keystrokes and free mouse movements involved in web sessions. Experimental evaluation of our proposed model with 24 participants yields an Equal Error Rate of 8.21 %. This is very encouraging considering that we are dealing with free text and free mouse movements, and the fact that many web sessions tend to be very short.





Similar content being viewed by others
Notes
Weka is an open source data mining software developed by the University of Waikato. It provides various machine learning algorithms.
In this work, we consider the most popular keyboard layout, which is the United States keyboard layout for Windows, Mac OS, and Linux.
References
[Online] Available: http://www.admitonesecurity.com. AdmitOne Security Suite
[Online] Available: http://www.rsa.com. RSA Adaptive Authentication System
Ahmed AA, Traore I (2007) A new biometric technology based on mouse dynamics. IEEE Transactions on Dependable and Secure Computing 4(3):165–179
Aksarı Y, Artuner H (2009) Active authentication by mouse movements. In Proc. of the IEEE 24th Intl. Symposium on Computer and Information Sciences (ISCIS’09), Metu, Northern Cyprus pp. 571–574
Bergadano F, Gunetti D, Picardi C (2002) User authentication through keystroke dynamics. ACM Trans Inf Syst Secur 5(4):367–397
Bouckaert RR (2004) Bayesian network classifiers in Weka. University of Waikato, http://weka.sourceforge.net/manuals/weka.bn.pdf
Bours P, Fullu CJ (2009) A login system using mouse dynamics. In Proc. of the 5th Intl. Conference on Intelligent Information Hiding and Multimedia Signal Processing (IIH-MSP’09), Kyoto, Japan, Sept. 12–14
Cheng P-C, Rohatgi P, Keser C, Karger P, Wagner GM, Reninger AS (2007) Fuzzy multi–level security: an experiment on quantified risk–adaptive access control. IBM Research Report RC24190
Diep NN, Lee S, Lee Y-K, Lee HJ (2007) Contextual risk-based access control. Secur Manag, pp. 406–412
Dimmock N, Bacon J, Ingram D, Moody K (2005) Risk models for trust–based access control. In Proc. of the 3rd Annual Conference on Trust Management (iTrust’05), Series LNCS, Vol. 3477, Springer, May, 426 pages
Dowland P, Furnell S, Papadaki M (2002) Keystroke analysis as a method of advanced user authentication and response. In Proc. of the 17th Intl. Conference on Information Security: Visions and Perspectives (IFIP TC11), The Netherlands, May 07–09, pp. 215–226
Dowland P, Singh H, Furnell S (2001) A preliminary investigation of user authentication using continuous keystroke analysis”, In Proc. of the 8th IFIP Annual Working Conference on Information Security Management and Small System Security, Las Vegas, Nevada
Enokido T, Takizawa M (2011) Purpose-based information flow control for cyber engineering. IEEE Trans Ind Electro 58(6):2216–2225
Fayyad UM, Irani KB (1993) Multi-interval discretization of continuous-valued attributes for classification learning. In Proc. of the 13th Intl. Joint Conference on Artificial Intelligence, Chambery, France, Aug. 28 – Sept. 3
Friedman N, Geiger D, Goldszmidt M (1997) Bayesian network classifiers. Mach Learn 29:131–163
Gaine R, Lisowski W, Press SJ, and Shapiro N (1980) Authentication by keystroke timing: Some preliminary results. Rand Report No R-2526-NSF, Rand Corporation
Gamboa H, Fred A (2003) An identity authentication system based on human computer interaction behaviour. In Proc. of the 3rd Intl. Workshop on Pattern Recognition in Information Systems, Angers, France, pp. 46–55
Gunetti D, Picardi C (2005) Keystroke analysis of free text. ACM Trans Inf Syst Secur 8(3):312–347
Jiang C-H, Shieh S, Liu J-C (2007) Keystroke statistical learning model for web authentication. In Proc. of the 2nd ACM Symposium on Information, Computer and Communications Security (ASIACCS’07), Singapore, Mar., pp. 359–361
Kononenko I (1995) On biases in estimating multi-valued attributes. In Proc. of the 14th Intl. Joint Conference on Artificial Intelligence, Montreal, Quebec, Canada, Aug. 20–25
Legget J, Williams G (1988) Dynamic identity verification via keystroke characteristics. International Journal on Man–machine Studies 35:859–870
Lian S, Chen X, Wang J (2012) Content distribution and copyright authentication based on combined indexing and watermarking. Multimedia Tools Appl 57(1):49–66
Monrose F, Rubin A (1997) Authentication via keystroke dynamics”, In Proc. of the 4th ACM Conference on Computer and Communications Security, Zurich, Switzerland, April 01–04, pp. 48–56
Obaidat MS, Macchairllo DT (1993) An on-line neural network system for computer access security. IEEE Trans Ind Electron 40(2):235–242
Obaidat MS, Sadoun B (1997) Verification of computer users using keystroke dynamics. IEEE Transactions on Systems, Man, and Cybernetics, Part B 27(2):261–269
Orozco M, Graydon M, Shirmohammadi S, El Saddik A (2012) Experiments in haptic-based authentication of humans, International Journal of Multimedia Tools and Applications - Springer Science + Business Media B.V. (To Appear)
Pusara M, Brodley C (2004) User Re-authentication via mouse movement. In Proc. of the 11th ACM Workshop on Visualization and Data Mining for Computer Security (CCS’04), Oct. 25–29, Washington, DC, USA
Revett K, Jahankhani H, De Magalhaes S, Santos H (2008) A survey of user authentication based on mouse dynamics, In Proc. of the 4th Intl. Conference on Global E-Security, London, UK, June 23–25, pp. 210–219
Syukri A, Okamoto E, Mambo (1998) A user identification system using signature written with mouse. In Proc. of the Australasian Conference on Information Security and Privacy (ACISP ’98), Vol. 1438, Brisbane, Australia, pp. 403–414
Traore I, Woungang I, Obaidat MS, Nakkabi Y, Lai I (2012) Combining mouse and keystroke dynamics biometrics for risk-based authentication in web environments. In Proc. of the 4th IEEE Intl. Conference on Digital Home (ICDH 2012), Guangzhou, China, pp. 138–145, Nov. 23–25
Tubin G (2005) Emergence of risk-based authentication in online financial services: You Can’t Hide Your Lyin’ IP. Whitepaper #V43:15N, Tower Group, May
Tuptuk N, Lupu E (2007) Risk based authorization for mobile Ad Hoc networks. In Proc. of the 1st Intl. Conference on Autonomous Infrastructure, Management and Security: Inter-Domain Management (AIMS 2007), LNCS 4543, Springer-Verlag, Berlin, Heidelberg, pp. 188–191
Villani M, Tappert C, Giang N, Simone J, Fort H, St., Sung-Hyuk C (2006) Keystroke biometric recognition studies on long-text input under ideal and application-oriented conditions, In Proc. of the IEEE Conference on Computer Vision and Pattern Recognition Workshop (CVPRW’06), New York, USA, June 17–22, pp. 39
Author information
Authors and Affiliations
Corresponding author
Additional information
An abridged version of this work [30] has been published in the Proc. of the 4th International Conference on Digital Home (ICDH 2012), Guangzhou, China, pp. 138–145, Nov. 23―25, 2012
Rights and permissions
About this article
Cite this article
Traore, I., Woungang, I., Obaidat, M.S. et al. Online risk-based authentication using behavioral biometrics. Multimed Tools Appl 71, 575–605 (2014). https://doi.org/10.1007/s11042-013-1518-5
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-013-1518-5