Abstract
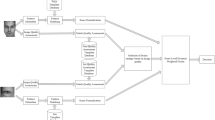
In spite of the benefits of biometric-based authentication systems, there are few concerns raised because of the sensitivity of biometric data to outliers, low performance caused due to intra-class variations, and privacy invasion caused by information leakage. To address these issues, we propose a hybrid fusion framework where only the protected modalities are combined to fulfill the requirement of secrecy and performance improvement. This paper presents a method to integrate cancelable modalities utilizing Mean-Closure Weighting (MCW) score level and Dempster-Shafer (DS) theory based decision level fusion for iris and fingerprint to mitigate the limitations in the individual score or decision fusion mechanisms. The proposed hybrid fusion scheme incorporates the similarity scores from different matchers corresponding to each protected modality. The individual scores obtained from different matchers for each modality are combined using MCW score fusion method. The MCW technique achieves the optimal weight for each matcher involved in the score computation. Further, DS theory is applied to the induced scores to output the final decision. The rigorous experimental evaluations on three virtual databases indicate that the proposed hybrid fusion framework outperforms over the component level or individual fusion methods (score level and decision level fusion). As a result, we achieve (48%, 66%), (72%, 86%) and (49%, 38%) of performance improvement over unimodal cancelable iris and unimodal cancelable fingerprint verification systems for Virtual_A, Virtual_B, and Virtual_C databases, respectively. Also, the proposed method is robust enough to the variability of scores and outliers satisfying the requirement of secure authentication.










Similar content being viewed by others
References
Bengio S, Mariéthoz J (2004) A statistical significance test for person authentication. In: Proceedings of Odyssey 2004: The Speaker and Language Recognition Workshop, pp 237–244
Camlikaya E, Kholmatov A, Yanikoglu B (2008) Multi-biometric templates using fingerprint and voice. In: Biometric technology for human identification V. vol. 6944, p 69440i. International society for optics and photonics
Canuto AM, Pintro F, Xavier-Junior JC (2013) Investigating fusion approaches in multi-biometric cancellable recognition. Expert Syst Appl 40(6):1971–1980
CASIA V-3-Interval database: Institute of automation, chinese academy of sciences(CASIA), CASIA iris image database version 3.0 (2010), http://www.cbsr.ia.ac.cn/Databases.htm
Chenghua Y, Qixiang C (2009) An improved algorithm for dempster-shafer theory of evidence. In: 2009 International conference on electronic commerce and business intelligence, pp 475–478
Chin Y, Ong T, Teoh A, Goh K (2014) Integrated biometrics template protection technique based on fingerprint and palmprint feature-level fusion. Information Fusion 18:161–174
Cimato S, Gamassi M, Piuri V, Sassi R, Scotti F (2008) Privacy-aware biometrics: Design and implementation of a multimodal verification system. In: 2008 Annual computer security applications conference (ACSAC), pp 130–139
Daugman J (2002) How iris recognition works. In: International conference on image processing. vol. 1, pp 33–36
Dwivedi R, Dey S (2018a) Securing fingerprint template using non-invertible ridge feature transformation. Unpublished manuscript
Dwivedi R, Dey S (2018b) Score-level fusion for cancelable multi-biometric verification. Pattern Recognition Letters pp –
Dwivedi R, Dey S, Singh R, Prasad A (2017) A privacy-preserving cancelable iris template generation scheme using decimal encoding and look-up table mapping. Computers & Security 65:373–386
FVC2002: Fingerprint Verification Competition (2002). https://biolab.csr.unibo.it/FVCOnGoing/UI/Form/Home.aspxp
Grover J, Hanmandlu M (2015) Hybrid fusion of score level and adaptive fuzzy decision level fusions for the finger-knuckle-print based authentication. Appl Soft Comput 31:1–13
He M, Horng SJ, Fan P, Run RS, Chen RJ, Lai JL, Khan MK, Sentosa KO (2010) Performance evaluation of score level fusion in multimodal biometric systems. Pattern Recogn 43(5):1789–1800
ISO/IEC 19795-1:2006 Information technology – Biometric performance testing and reporting – Part 1: Principles and framework: ISO/IEC 19795-1:2006 information technology – biometric performance testing and reporting – part 1: Principles and framework (2006). https://www.iso.org/standard/41447.html
ISO/IEC 2382-37:2012 information technology – vocabulary – part 37: biometrics 2012: ISO/IEC 2382-37:2012 information technology – vocabulary – part 37: biometrics 2012 (2012). https://www.iso.org/standard/55194.html
Joshi T, Dey S, Samanta D (2009) Multimodal biometrics: state of the art in fusion techniques. International Journal of Biometrics 1(4):393–417
Kabir W, Ahmad MO, Swamy MNS (2018) Normalization and weighting techniques based on genuine-impostor score fusion in multi-biometric systems. IEEE Trans Inf Forensics Secur 13(8):1989–2000
Kelkboom EJC, Zhou X, Breebaart J, Veldhuis RNJ, Busch C (2009) Multi-algorithm fusion with template protection. In: 2009 IEEE 3rd international conference on biometrics: Theory, applications, and systems, pp 1–8
Kolomvatsos K, Anagnostopoulos C, Hadjiefthymiades S (2015) Contextual reasoning under uncertainty in sensor data stream monitoring. International Journal of Monitoring and Surveillance Technologies Research 3 (1):1–19
Kolomvatsos K, Anagnostopoulos C, Hadjiefthymiades S (2017a) Data fusion and type-2 fuzzy inference in contextual data stream monitoring. IEEE Trans Syst Man Cybern Syst Hum 47(8):1839–1853
Kolomvatsos K, Anagnostopoulos C, Hadjiefthymiades S (2017b) Distributed localized contextual event reasoning under uncertainty. IEEE Internet of Things Journal 4(1):183–191
Kumar A, Kumar A (2016) Adaptive management of multimodal biometrics fusion using ant colony optimization. Information Fusion 32:49–63
Li SZ, Jain AK (2009) Encyclopedia of Biometrics, vol. 1 Springer Science & Business Media
Maiorana E, Hine GE, Campisi P (2015) Hill-climbing attacks on multibiometrics recognition systems. IEEE Trans Inf Forensics Secur 10(5):900–915
Masek L (2003) Recognition of human iris patterns for biometric identification. Tech. rep., University of Western Australia, Crawley
Mezai L, Hachouf F (2015) Score-level fusion of face and voice using particle swarm optimization and belief functions. IEEE Transactions on Human-Machine Systems 45(6):761–772
Multimedia University version-1.0: Multimedia university version-1.0, MMU1 iris image database (2014 (Accessed)).www.cs.princeton.edu/~andyz/downloads/MMUIrisDatabase.zip
Nandakumar K, Jain AK (Sept 2015) Biometric template protection: Bridging the performance gap between theory and practice. IEEE Signal Proc Mag 32(5):88–100
Nguyen K, Denman S, Sridharan S, Fookes C (2015) Score-level multibiometric fusion based on dempster shafer theory incorporating uncertainty factors. IEEE Transactions on Human-Machine Systems 45(1):132–140
Othman A, Ross A (2013) On mixing fingerprints. IEEE Trans Inf Forensics Secur 8(1):260–267
Paul PP, Gavrilova M (2012) Multimodal cancelable biometrics. In: 2012 IEEE 11th international conference on cognitive informatics and cognitive computing, pp 43–49
Prabhakar S, Jain AK (2002) Decision-level fusion in fingerprint verification. Pattern Recogn 35(4):861–874
Provan GM (1990) A logic-based analysis of dempster-shafer theory. Int J Approx Reason 4(5):451–495
Rathgeb C, Gomez-Barrero M, Busch C, Galbally J, Fierrez J (2015) Towards cancelable multi-biometrics based on bloom filters: a case study on feature level fusion of face and iris. In: 3rd international workshop on biometrics and forensics (IWBF 2015), pp 1–6
Ross AA, Nandakumar K, Jain AK (2006) Handbook of multibiometrics. Springer, New York
Sadhya D, Singh SK (2018) Construction of a bayesian decision theory-based secure multimodal fusion framework for soft biometric traits. IET Biometrics 7(3):251–259
Shafer G (1976) A mathematical theory of evidence, vol. 42, Princeton University Press, Princeton
Simoens K, Bringer J, Chabanne H, Seys S (2012) A framework for analyzing template security and privacy in biometric authentication systems. IEEE Trans Inf Forensics Secur 7(2):833– 841
Smets P (2002) Decision making in a context where uncertainty is represented by belief functions, pp. 17–61. Physica-Verlag HD, Heidelberg
Sutcu Y, Li Q, Memon N (2007) Secure biometric templates from fingerprint-face features. In: 2007 IEEE Conference on computer vision and pattern recognition, pp 1–6
Talreja V, Valenti MC, Nasrabadi NM (2017) Multibiometric secure system based on deep learning. In: 2017 IEEE Global conference on signal and information processing (globalSIP), pp 298–302
Tao Q, Veldhuis R (2008) Hybrid fusion for biometrics: Combining score-level and decision-level fusion. In: 2008 IEEE Computer society conference on computer vision and pattern recognition workshops, pp 1–6
Wong WJ, Teoh AB, Wong MD, Kho YH (2013) Enhanced multi-line code for minutiae-based fingerprint template protection. Pattern Recogn Lett 34(11):1221–1229
Yang W, Wang S, Hu J, Zheng G, Valli C (2018) A fingerprint and finger-vein based cancelable multi-biometric system. Pattern Recogn 78:242–251
Acknowledgements
The authors are thankful to SERB (ECR/2017/000027), Department of Science & Technology, Govt. of India for providing financial support. Also, we would like to acknowledge Indian Institute of Technology Indore for providing the laboratory support and research facilities to carry out this research.
Author information
Authors and Affiliations
Corresponding author
Appendices
Appendix A: Preliminaries on Dempster-Shafer theory of evidence
In Bayesian theory, the probabilities are assigned to each individual proposition from a set of mutually exclusive propositions. Alternatively, DS theory assigns masses to each combination of events. Unlike DS theory, the probability theory is unable to discriminate between ignorance and uncertainty due to sketchy information. Fundamentally, the Bayesian theory departs DS theory in the aspect of handling ignorance. DS theory does not assign belief to ignorance or to a falsified hypothesis. The mass is assigned particularly to the subsets for which we seek to assign belief. This implies neither belief nor disbelief for the evidence to a certain value. Hence we have utilized DS theory in our work.
Consider, 𝜃 be a finite set of all possible hypotheses known as a frame of discernment. The power set 2𝜃 contains all subsets of 𝜃 including a null set (ϕ) and itself. Each subset in the power set is referred as a focal element and assigned a value in between [0, 1] on the basis of their evidence. A value of 1 corresponds to total belief and 0 for no belief. In general, the assigned value is named as basic belief assignment (BBA). In DS theory [33], BBA is assigned to each subset i.e. hypothesis also known as the mass of the individual proposition,
If \(\theta =\left \{ A,B \right \} \ \text {then} \ 2^{\theta }=\left \{\varnothing ,A,B,\theta \right \}\). The mass function fulfills the following criteria:
where \(\varnothing \) represents the empty set. The measure of belief is defined by the function bel : 2𝜃 → [0, 1],
The bel can also be formally defined as:
This means the degree of belief x for the classifier Y at time t when w0 ∈ A. Here, EY,t represents the evidential information known to classifier Y at time t. For ease in representation, we use bel(A) instead of \( bel_{Y,t}^{\theta ,\Re }\left [ E_{Y,t} \right ]\left (w_{0}\in A \right )\). Next, plausibility (pl) is measured as:
If 𝜃 defines the set of all possible hypotheses, then the level of uncertainty is denoted by m (𝜃). In a hypothesis, beliefs and disbeliefs may not sum to 1 and may attain 0 value. A value of 0 signifies no evidence present for the hypothesis. The DS theory based aggregation involves the following steps:
-
The measure of belief is evaluated based on the facts from the different sources of information. As compared to Bayesian theory, the masses are not distributed among classes.
-
Dempster rule of combination is applied to aggregate belief measure obtained from the available information and facts.
For different sources, (1, 2,⋯ ,N), Dempster’s rule of combination is described in (16):
where A,B1,…,BN ⊆ 𝜃, and
where K denotes the conflict present between evidences; 1-K is the normalization factor.
A.1 Updation of masses
In a majority of the scenarios, mass updating is required if any new evidence or belief is encountered. Suppose, E ⊂ 𝜃 and Ed be the evidence not present in E. If this new evidence provides the exact value of Ed, then bel(A) is updated based on the following condition rule:
After the computation of the masses, the classification is performed onto the training set. One of the aggregation rules is applied to evaluate total conflicting mass. Next, the winner-take-all assignment is utilized to compute A(k), which is defined in (19):
where M + 1 represents is the total number of classes including the class of rejection and AM+ 1 = 𝜃.
Rights and permissions
About this article
Cite this article
Dwivedi, R., Dey, S. A novel hybrid score level and decision level fusion scheme for cancelable multi-biometric verification. Appl Intell 49, 1016–1035 (2019). https://doi.org/10.1007/s10489-018-1311-2
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10489-018-1311-2