Abstract
This chapter describes the “Internet” in the “Internet of Things”. It starts with a summary of the well-known Open System Interconnection (OSI) Model Layers. It then describes the TCP/IP Model, which is the basis for the Internet. The TCP/IP protocol has two big advantages in comparison with earlier network protocols: Reliability and flexibility to expand. The TCP/IP protocol was designed for the US Army addressing the reliability requirement (resist breakdowns of communication lines in times of war). The remarkable growth of Internet applications can be attributed to this reliable expandable model.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Notes
- 1.
IP packets are referred to as IP datagrams by many experts. However, some experts used the phrase “stream” to refer to packets that are assembled for TCP and the phrase “datagram” to packets that are assembled for UDP.
- 2.
InterNIC is a registered service mark of the US Department of Commerce. It is licensed to the Internet Corporation for Assigned Names and Numbers, which operates this website.
References
W. Odom, CCNA Routing and Switching 200–120 Official Cert Guide Library Book, ISBN: 978–1587143878, May 2013
P. Browning, F. Tafa, D. Gheorghe, D. Barinic, Cisco CCNA in 60 Days, ISBN: 0956989292, March 2014
G. Heap, L. Maynes, CCNA Piratical Studies Book (Cisco Press, April 2002)
Information IT Online Library.: http://www.informit.com/library/content.aspx?b=CCNA_Practical_Studies&seqNum=12
Inter NICFootnote
InterNIC is a registered service mark of the US Department of Commerce. It is licensed to the Internet Corporation for Assigned Names and Numbers, which operates this website.
—Public Information Regarding Internet Domain Name Registration Services, Online: http://www.internic.netUnderstanding TCP/IP addressing and subnetting basics, Online: https://support.microsoft.com/en-us/kb/164015
Tutorials Point, “IPv4 – Address Classes”, Online: http://www.tutorialspoint.com/ipv4/ipv4_address_classes.htm
Google IPv6, “What if the Internet ran out of room? In fact, it's already happening”, Online: http://www.google.com/intl/en/ipv6/
Wikipedia, “Internet Protocol version 6 (IPv6):, Online: https://en.wikipedia.org/wiki/IPv6
IPv6 Addresses, Microsoft Windows Mobile 6.5, April 8, 2010, Online: https://msdn.microsoft.com/en-us/library/aa921042.aspx
Binary to Hexadecimal Convert, Online: http://www.binaryhexconverter.com/binary-to-hex-converter
Technology White Paper, Cisco Systems online: http://www.cisco.com/c/en/us/tech/ip/ip-routing/tech-white-papers-list.html
M. Caeser, J. Rexford, “BGP routing policies in ISP networks”, Online: https://www.cs.princeton.edu/~jrex/papers/policies.pdf
A. Shaikh, A.M. Goyal, A. Greenberg, R. Rajan, An OSPF topology server: Design and evaluation. IEEE J. Sel. Areas Commun 20(4) (2002)
Y. Yang, H. Xie, H. Wang, A. Silberschatz, Y. Liu, L. Li, A. Krishnamurthy, On route selection for interdomain traffic engineering. IEEE Netw. Mag. Spec. Issue Interdomain Rout (2005)
N. Feamster, J. Winick, J. Rexford, “A model of BGP routing for network engineering,” in Proc. ACM SIGMETRICS, June 2004
N. Feamster, H. Balakrishnan, Detecting BGP configuration faults with static analysis, in Proc. Networked Systems Design and Implementation, (2005)
Apple History / Power Macintosh Gigabit Ethernet, Online: http://www.apple-history.com/g4giga. Retrieved November 5, 2007
Author information
Authors and Affiliations
Problems and Exercises
Problems and Exercises
-
1.
Ethernet and Point-to-Point Protocol (PPP) are two examples of data link protocols listed in this chapter. Name two other data link protocols.
-
2.
Provide an example of Session Layer protocol.
-
3.
In a table format, compare the bandwidth, distance, interference rating, cost and security of (1) twisted pair, (2) coaxial cabling, and (3) fiber optical cabling.
-
4.
A. What are the main components of a router? B. Which element is considered the most essential? C. Why?
-
5.
What is the main function of NVRAM? Why is such function important to operate a router?
-
6.
How do network administrators guarantee that changes in the configuration are not lost in case the router is restarted or loses power?
-
7.
What is a disaster recovery function in a router? Which router’s sub-component contains such function?
-
8.
Many argue that routers are special computers but built to handle internetwork traffic. List three main differences between routers and personal computers.
-
9.
There are no input devices for router like a monitor, a keyboard, or a mouse. How does a network administrator communicate with the router? List all possible scenarios. What are the main differences between such interfaces?
-
10.
How many IPv4 addresses are available? Justify your answer.
-
11.
What is the ratio of the number of addresses in IPv6 compared to IPv4?
-
12.
IPv6 uses a 128-bit address, allowing 2128 addresses. In decimal, how many IPv6 addresses exist? How many IPv6 addresses will each human have? Why do we need billions of addresses for each human being?
-
13.
How many IPv6 address will be available on each square meter of earth?
-
14.
What are the major differences between interior and exterior routing protocols?
-
15.
What is distance vector protocol? Why is it called a vector? Where is it used?
-
16.
When would you use static routing and when would use dynamic routing? Why?
-
17.
Most IP networks use dynamic routing to communicate between routers but may have one or two static routes. Why would you use static routes?
-
18.
We have mentioned that in TCP/IP networks, the entire route is not known at the beginning of the journey. Instead, at each stop, the next router hop is determined by matching the destination address within the packet with an entry in the current router’s routing table using internal information. IP does not provide for error reporting back to the source when routing anomalies occur.
-
A.
Which Internet Protocol provides error reporting?
-
B.
List two other tasks that this protocol provides?
-
A.
-
19.
Why is EGP considered to be obsolete for the current Internet?
-
20.
In a table, compare the speed and distance Standard Ethernet, Fast Ethernet, and Giga Ethernet. Why is Ethernet connection limited to 100 meters?
-
21.
Why the Internet does require both TCP and IP protocols?
-
22.
Are IPv4 and IPv6 protocols designed to be interoperable? How would an enterprise transition from IPv4 to IPv6?
-
23.
What are the four different reasons for packet loss? List remediation for each reason.
-
24.
List two factors that can affect throughput of a communication system.
-
25.
Figure 2.10 (in Section 2.4.3) stated the throughput between host A and host B is 20 mbps with the assumptions:
-
R2 = R3 = R5 = R6 = 10Mbps.
-
R1 = R4 = 100Mbps.
-
Data is equally divided between the two paths.
How did the authors arrive at 20 Mbps?
-
-
26.
Assuming host A is transferring a large file to host B. What is the throughput between host A and host B for the network shown below?
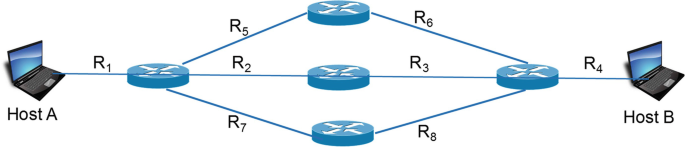
-
A.
Assumptions:
-
The speed of each router is higher than the speed of any link in the network.
-
No other host is sending data.
-
R2 = R3 = R5 = R6 = R7 = R8 = 10Mbps.
-
R1 = R4 = 1 Mbps.
-
Data is equally divided between the three paths.
-
-
B.
Assumptions:
-
The speed of each router is higher than the speed of any link in the network.
-
No other host is sending data.
-
R2 = R3 = R5 = R6 = R7 = R8 = 10Mbps.
-
R1 = R4 = 100 Mbps.
-
Data is equally divided between the three paths.
-
-
C.
Assumptions:
-
The speed of each router is 1 Mbps.
-
No other host is sending data.
-
R2 = R3 = R5 = R6 = R7 = R8 = 10Mbps.
-
R1 = R4 = 100 Mbps.
-
Data is equally divided between the three paths.
-
-
A.
-
27.
What is Traceroute? What does it typically report? What are the main advantageous of trace route? What is the main difference between Traceroute and Ping?
-
28.
For the network shown below, assume the network administer is interested in measuring the end-to-end delay from router A to the server.
-
A.
What is the Traceroute command? Hence, Traceroute command is sent from router A directly (i.e., via the shown connected terminal).
-
B.
Which device will send their delays?
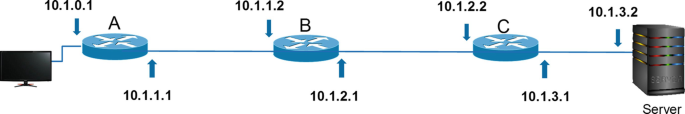
-
A.
-
29.
What is time to live command? Why is it needed?
Rights and permissions
Copyright information
© 2019 Springer Nature Switzerland AG
About this chapter
Cite this chapter
Rayes, A., Salam, S. (2019). The Internet in IoT. In: Internet of Things From Hype to Reality. Springer, Cham. https://doi.org/10.1007/978-3-319-99516-8_2
Download citation
DOI: https://doi.org/10.1007/978-3-319-99516-8_2
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-99515-1
Online ISBN: 978-3-319-99516-8
eBook Packages: EngineeringEngineering (R0)



