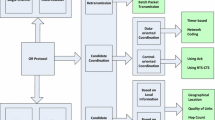
Abstract
Opportunistic Networks have evolved as special class of mobile ad hoc and delay tolerant networks which have a vast range of applications. In opportunistic networks, the permanent links among the nodes are absent and delay is high. Due to self-organized nature of opportunistic networks, these networks have many security threats, e.g, how to protect the data confidentiality, integrity, privacy as well as the trust among the nodes. In this article, we present the specific security challenges to opportunistic networks and analyze related security requirement. Based on these discussions, we propose a general security framework for opportunistic networks and point out the future research direction in opportunistic networks.
Similar content being viewed by others
References
Lilien, L., Gupta, A. & Yang, Z.: Opportunistic Networks for Emergency Applications and Their Standard Implementation Framework. 2007 IEEE Int. Perform. Comput. Commun. Conf. (2007)
Sadler, C. M. & Martonosi, M.: Implementing Software on Resource-Constrained Mobile Sensors : Experiences with Impala and ZebraNet. MobiSys ’04 Proc. 2nd Int. Conf. Mob. Syst. Appl. Serv. (2004). 256–269
Pentland, A., Fletcher, R. & Hasson, A.: DakNet: Rethinking Connectivity in Developing Nations. Computer (Long. Beach. Calif). 37, (2004). 78–83
PodNet - Mobile Distribution of User-Generated Content [PodNet Project]. at <http://www.podnet.ee.ethz.ch/>
Wang, W., Guo, F., Zheng, F., Tang, W. & Wang, J.: Research on Routing Protocols and Simulation Analysis for Opportunistic Networks. 10, (2015). 181–202
Lilien, L., Kamal, Z. H., Bhuse, V. & Gupta, A.: Opportunistic Networks : The Concept and Research Challenges in Privacy and Security. Proc WSPWN 140, (2006). 134–147
Chlamtac, I. & Lerner, A.: Fair Algorithms for Maximal Link Activation. IEEE Trans. Commun. 35, (1987). 739–746
Crowcroft, J., Hand, S., Mortier, R., Roscoe, T. & Warfield, A.: Plutarch: An Argument for Network Pluralism. Appl. Technol. Archit. Protoc. Comput. Commun. 33, (2003). 258–266
Wu, Y., Zhao, Y., Riguidel, M., Wang, G. & Yi, P.: Security and Trust Management in Opportunistic Networks : A Survey. Secur. Commun. NETWORKS 8, (2015). 1812–1827
Poonguzharselvi, B. & Vetriselvi, V.: Trust Framework for Data Forwarding in Opportunistic Networks Using Mobile Traces. 4, (2012). 115–126
Xi, C., Youliang, Guangsong, L. & Jianfeng, M.: Security in Opportunistic Networks. Int. Conf. Ind. Control Electron. Eng. (2012). 2006–2009
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2018 Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Kumar, P., Chauhan, N., Chand, N. (2018). Security Framework for Opportunistic Networks. In: Sa, P., Sahoo, M., Murugappan, M., Wu, Y., Majhi, B. (eds) Progress in Intelligent Computing Techniques: Theory, Practice, and Applications. Advances in Intelligent Systems and Computing, vol 719. Springer, Singapore. https://doi.org/10.1007/978-981-10-3376-6_50
Download citation
DOI: https://doi.org/10.1007/978-981-10-3376-6_50
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-10-3375-9
Online ISBN: 978-981-10-3376-6
eBook Packages: EngineeringEngineering (R0)