Abstract
In the Wyner wiretap channel a sender is connected to a receiver and an eavesdropper through two noisy channels. It has been shown that if the noise in the eavesdropper channel is higher than the receiver’s channel, information theoretically secure communication from Alice to Bob, without requiring a shared key, is possible. The approach is particularly attractive noting the rise of quantum computers and possibility of the complete collapse of todays’ cryptographic infrastructure. If the eavesdropper’s channel is noise free however, no secrecy can be obtained. The iJam protocol, proposed by Gollakota and Katabi, is an interactive protocol over noise free channels that uses friendly jamming by the receiver to establish an information theoretically secure shared key between the sender and the receiver. The protocol relies on the Basic iJam Transmission protocol (BiT protocol) that uses properties of OFDM (Orthogonal Frequency-Division Multiplexing) to create uncertainty for Eve (hence noisy view) in receiving the sent information, and use this uncertainty to construct a secure key agreement protocol. The protocol has been implemented and evaluated using extensive experiments that examines the best eavesdropper’s reception strategy. In this paper we develop an abstract model for BiT protocol as a wiretap channel and refer to it as a virtual wiretap channel. We estimate parameters of this virtual wiretap channel, derive the secrecy capacity of this channel, and design a secure message transmission protocol with provable semantic security using the channel. Our analysis and protocol gives a physical layer security protocol, with provable security, that is implementable in practice (BiT protocol has already been implemented).
This is a preview of subscription content, log in via an institution.
Buying options
Tax calculation will be finalised at checkout
Purchases are for personal use only
Learn about institutional subscriptionsReferences
802.1x & WPA settings. https://www.ietf.org/mail-archive/web/ietf/current/msg32026.html
The secure sockets layer (SSL) protocol version 3.0. https://tools.ietf.org/html/rfc6101
SSH protocol architecture. https://www.ietf.org/proceedings/52/I-D/draft-ietf-secsh-architecture-11.txt
Bellare, M., Tessaro, S.: Polynomial-time, semantically-secure encryption achieving the secrecy capacity. arXiv preprint arXiv:1201.3160 (2012)
Bellare, M., Tessaro, S., Vardy, A.: A cryptographic treatment of the wiretap channel. arXiv preprint arXiv: 1201.2205 (2012)
Bellare, M., Tessaro, S., Vardy, A.: Semantic security for the wiretap channel. In: Safavi-Naini, R., Canetti, R. (eds.) CRYPTO 2012. LNCS, vol. 7417, pp. 294–311. Springer, Heidelberg (2012). doi:10.1007/978-3-642-32009-5_18
Bergmans, P.: Random coding theorem for broadcast channels with degraded components. IEEE Trans. Inf. Theory 19(2), 197–207 (1973)
Csiszár, I., Körner, J.: Broadcast channels with confidential messages. IEEE Trans. Inf. Theory 24(3), 339–348 (1978)
Dickerson, K.: Microsoft lab predicts we’ll have a working ‘hybrid’ quantum computer in 10 years, October 2015. http://www.techinsider.io/microsoft-hybrid-quantum-computer-2015-10
Dodis, Y., Reyzin, L., Smith, A.: Fuzzy extractors: how to generate strong keys from biometrics and other noisy data. In: Cachin, C., Camenisch, J.L. (eds.) EUROCRYPT 2004. LNCS, vol. 3027, pp. 523–540. Springer, Heidelberg (2004). doi:10.1007/978-3-540-24676-3_31
Dong, L., Han, Z., Petropulu, A.P., Poor, H.V.: Cooperative jamming for wireless physical layer security. In: 2009 IEEE/SP 15th Workshop on Statistical Signal Processing, pp. 417–420. IEEE (2009)
Goldsmith, A.: Wireless Communications. Cambridge University Press, Cambridge (2005)
Gollakota, S., Katabi, D.: Physical layer wireless security made fast and channel independent. In: 2011 Proceedings IEEE INFOCOM, pp. 1125–1133. IEEE (2011)
Guruswami, V.: Bridging Shannon and Hamming: list error-correction with optimal rate (2010)
Han, Z., Marina, N., Debbah, M., Hjørungnes, A.: Physical layer security game: interaction between source, eavesdropper, and friendly jammer. EURASIP J. Wirel. Commun. Netw. 2009(1), 1 (2010)
Karagiannidis, G.K., Lioumpas, A.S.: An improved approximation for the Gaussian Q-function. IEEE Commun. Lett. 11(8) (2007)
Lai, L., El Gamal, H.: The relay-eavesdropper channel: cooperation for secrecy. IEEE Trans. Inf. Theory 54(9), 4005–4019 (2008)
Leung-Yan-Cheong, S.: On a special class of wiretap channels (Corresp.). IEEE Trans. Inf. Theory 23(5), 625–627 (1977)
Leung-Yan-Cheong, S., Hellman, M.: The Gaussian wire-tap channel. IEEE Trans. Inf. Theory 24(4), 451–456 (1978)
Mahdavifar, H., Vardy, A.: Achieving the secrecy capacity of wiretap channels using polar codes. IEEE Trans. Inf. Theory 57(10), 6428–6443 (2011)
Muramatsu, J., Miyake, S.: Construction of wiretap channel codes by using sparse matrices. In: 2009 IEEE Information Theory Workshop (2009)
Schulze, H., Lüders, C.: Theory and Applications of OFDM and CDMA: Wideband Wireless Communications. Wiley, Hoboken (2005)
Shor, P.W.: Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM Rev. 41(2), 303–332 (1999)
Strasser, M., Danev, B., Čapkun, S.: Detection of reactive jamming in sensor networks. ACM Trans. Sens. Netw. (TOSN) 7(2), 16 (2010)
Tal, I., Vardy, A.: Channel upgrading for semantically-secure encryption on wiretap channels. In: 2013 IEEE International Symposium on Information Theory Proceedings (ISIT), pp. 1561–1565. IEEE (2013)
Tang, X., Liu, R., Spasojevic, P., Poor, H.V.: The Gaussian wiretap channel with a helping interferer. In: 2008 IEEE International Symposium on Information Theory, pp. 389–393. IEEE (2008)
Tang, X., Liu, R., Spasojevic, P., Poor, H.V.: Interference assisted secret communication. IEEE Trans. Inf. Theory 57(5), 3153–3167 (2011)
Tekin, E., Yener, A.: Achievable rates for the general Gaussian multiple access wire-tap channel with collective secrecy. arXiv preprint cs/0612084 (2006)
Tekin, E., Yener, A.: The Gaussian multiple access wire-tap channel: wireless secrecy and cooperative jamming. In: 2007 Information Theory and Applications Workshop, pp. 404–413. IEEE (2007)
Tekin, E., Yener, A.: The general Gaussian multiple-access and two-way wiretap channels: achievable rates and cooperative jamming. IEEE Trans. Inf. Theory 54(6), 2735–2751 (2008)
Thangaraj, A., Dihidar, S., Calderbank, A.R., McLaughlin, S.W., Merolla, J.-M.: Applications of LDPC codes to the wiretap channel. IEEE Trans. Inf. Theory 53(8), 2933–2945 (2007)
Tse, D., Viswanath, P.: Fundamentals of Wireless Communication. Cambridge University Press, Cambridge (2005)
Wyner, A.D.: The wire-tap channel. Bell Syst. Tech. J. 54(8), 1355–1387 (1975)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Appendices
Appendix A: Achievable Transmission Rate Using BiT\(^N_{q,\eta }\)
For a noise free main channel, the secrecy capacity of BiT\(^N_{q,\eta }\) is given by:
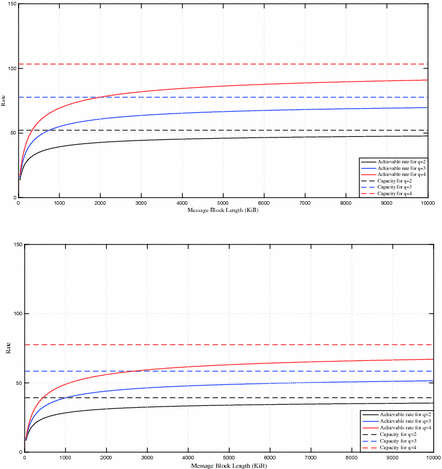
Figure 4 shows the rate of communication when, the information block length is Nq bits, \(q=2,3\) and 4, and \(N=64\). The graphs show the achievable rates for \(\sigma =128\) semantic security, and \(\eta =0.2\) (upper graph) and \(\eta =0.4\) (lower graph). The figures show that the achievable secrecy rate and secrecy capacity decreases as \(\eta \) grows. This is expected because higher \(\eta \) means that the adversary has a better chance of correctly decoding the jammed signal.
Appendix B: BiT over Noisy Receiver Channel—An Example
In this section we derive a sufficient relation between \(P_b\) and \(\eta \) so that the virtual wiretap channel is a stochastically degraded broadcast channel. Following Sect. 3, the transition matrix of the virtual wiretapper channel W for \(q=2\) is given by:
where \(u=\frac{1-\eta }{3}\), and \(v=\eta -\frac{1-\eta }{3}=\frac{4\eta -1}{3}\). Note that the sum of each row is \(4u+v=1\). On the other hand, we can compute:
Let \(a=1-P_b\) and \(b=P_b\). The above matrix can be written as:
The sum of entries of each row is given by, \(\frac{1}{(a-b)^2}(a^2-2ab+b^2)=1\). The following is used to prove the required relation.
Lemma 1
Let there be two matrices
If \(\sum _{j=1}^n a_{ij}=1\) and \(\sum _{j=1}^n b_{ij}=1\) for any \(i\in [n]\), then \(\sum _{j=1}^n (AB)_{ij}=1\), for any \(i\in [n]\).
Proof
For any \(i\in [n]\),
\(\square \)
Lemma 2
The virtual wiretap channel is a stochastically degraded broadcast channel if \(P_b\le \frac{1-\sqrt{\frac{4\eta -1}{3}}}{2}\) and \(\eta >\frac{1}{4}\).
Proof
The virtual wiretap channel is a stochastically degraded broadcast channel if there exists a matrix \(\mathbf {R}\) such that \(\mathbf {P}_{\mathsf {W}}=\mathbf {P}_{\mathsf {M}}\times \mathbf {R}\), and \(\mathbf {R}\) is a channel transition matrix; that is, has non-negative entries and each row sums to 1. Using the matrices \(\mathbf {P}_{\mathsf {M}}\) and \(\mathbf {P}_{\mathsf {W}}\) above, we have:
Using Lemma 1, entries in each row of \(\mathbf {R}\) sum to 1.
To ensure entries of \(\mathbf {R}\) are all non-negative, we first note that \(u(a-b)^2+va^2> 0\) and \(u(a-b)^2+vb^2>0\). So the virtual wiretap channel is a stochastically degraded broadcast channel if \(u(a-b)^2-vab\ge 0\) and so:
where \(4u+v=1\) and \(a+b=1\) are repeatedly invoked to simplify the expressions. The solution to the above inequality depends on the determinant \(1-4u\). When \(1-4u>0\), we have
By assumption, \(P_b\in [0,\frac{1}{2}]\) and so \(P_b\le \frac{1-\sqrt{\frac{4\eta -1}{3}}}{2} = \frac{1}{2} - \sqrt{\frac{4\eta -1}{12}}\). \(\square \)
Example 2
Let \(P_b=0.1\) and Let \(\eta =0.55\). Therefore,
and
Therefore
\(\mathbf {R}\) is the transition probability matrix of a virtual channel that confirms \(\mathbf {P}_{\mathsf {W}}\) is degraded with respect to \(\mathbf {P}_{\mathsf {M}}\). The secrecy capacity in this example is
Rights and permissions
Copyright information
© 2017 Springer International Publishing AG
About this paper
Cite this paper
Sharifian, S., Safavi-Naini, R., Lin, F. (2017). A Virtual Wiretap Channel for Secure Message Transmission. In: Phan, RW., Yung, M. (eds) Paradigms in Cryptology – Mycrypt 2016. Malicious and Exploratory Cryptology. Mycrypt 2016. Lecture Notes in Computer Science(), vol 10311. Springer, Cham. https://doi.org/10.1007/978-3-319-61273-7_9
Download citation
DOI: https://doi.org/10.1007/978-3-319-61273-7_9
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-61272-0
Online ISBN: 978-3-319-61273-7
eBook Packages: Computer ScienceComputer Science (R0)