Abstract
The ubiquity of mobile computing devices in the workplace has created a vast landscape of opportunity in rural communities centered on the increased population access owing to the improved mobility. Healthcare workers are able to reach previously disconnected communities and homesteads to deliver health related services through the use of custom mobile computing devices or applications that facilitate the viewing, recording and updating of patient records. Notably, the presence of electronic patient information presents privacy and confidentiality challenges that if not addressed, may affect the delivery of health services thereby negatively impacting on the overall health outcomes of the communities. Deficit based solutions target the needs and challenges of the communities in developing solutions and have been widely used; however, little emphasis has been placed on utilizing the existing asset resources that contribute positively to the overall health outcomes in the development of solutions. This paper leverages off an asset model developed by Morgan and Ziglio to identify existing community assets in a rural community through the use of a survey issued to community health workers and the supporting IT staff. The results point to assets in the cohesive social structures centered on the trust bond between the patients and the providers. Moreover, mentoring support structures and periodic training activities keep the health worker skills up to date. Furthermore, a positive appreciation of health information sensitivity and the need for patient privacy and confidentiality provide for productive interactions between health workers and patients.
You have full access to this open access chapter, Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
The proliferation of mobile hand-held devices such as smart phones and tablet computers has improved the mobility of the health workforce. This growth has been supported by the rapid deployment of wireless infrastructure communication networks which have greatly improved the capacity for service delivery [13]. As computers become cheaper and more powerful, the value is no longer measured on device capability but rather on the ability of organizations to develop processes and structures that leverage off this capability [5]. The applications market for mobile devices has also grown rapidly and has attracted a large community of developers whose efforts have in turn contributed significantly to shift towards mobile computing devices. These devices are increasingly making appearances in both homes and the workplace as preferred productivity and media consumption devices. This phenomenon has been termed the consumerization of IT.
2 Background: Mobility in the Workplace
The growing need for mobility when conducting work related activities has given rise to the growth in consumer owned devices in the workplace. In a survey conducted by Accenture in 2011, 23 % of the employees sampled were already making routine use of personal technology tools at work with a further 29 % making use of these tools at least once a week [11, 14]. Additionally, in a survey conducted by Harris Interactive and ESET, more than 80 % of employed adults use some kind of personally owned mobile device for work-related functions [16].
In the broad sense, consumerization refers to the penetration of consumer market devices into business settings [7]. In the IT context, consumerization describes the dual application of computing devices for personal and work related activities. In effect, the consumerization of mobile computing devices describes the phenomenon of employees using their personally owned devices to perform work-related activities [14], a view supported by D’Arcy [6], who defines consumerization as the “migration of consumer technology, devices, platforms and applications into enterprise computing environments”. These devices are typically used to access the resources on the corporate network and offer the added flexibility of enabling employee productivity from anywhere without the limitations of time or access to a workstation [16]. This phenomenon has commonly been described as “Bring Your Own Device” (BYOD).
Consumerization however, extends beyond “BYOD”, as according to Gens, Levitas, and Segal [9], applications such as Facebook, Twitter and other social networking platforms are extending the accessibility of business processes. Serving to further support this notion, Morrow [16] describes the “D” in BYOD as referring to more than just the physical devices but also consumer oriented web and cloud based applications. For the purposes of this study, the consumerization of mobile computing devices is an over-arching reference to BYOD (devices) and Bring Your Own Service (BYOS) and the use of mobile computing devices provided by an institution, Institution Provided Devices (IPDs).
It is commonplace for institutions to provide their employees with mobile computing devices that are subsequently used for both personal and work-related activities. The institution exercises more control on such devices and in many cases implements a Mobile Device Management system that enables them to manage the mobile devices operating within the organization. The major distinction point between IPDs and BYOD is the ownership of the devices. However, in terms of use and application, there is no distinction.
The rural healthcare landscape is unique due to the prevalence of various contextual constraints in the operational environment. Rural communities are typically resource constrained and lack various assets such as communications infrastructure, skilled health workforce, electricity, and sanitation in addition to the financial economic constraints associated with inadequate employment opportunities.
In the rural healthcare context, mobile computing devices extend the productivity of a health worker by enabling mobility thereby allowing the wider provision of health services to remote and digitally disconnected communities. The benefits of mobility in the rural context are further supported by Braun, Catalani, Wimbush, and Israelski [3] who suggest mobile technology can potentially enhance the capacity of community health workers to innovate, improve accuracy and productivity while achieving higher levels of protocol adherence. Community health workers typically commute between patients whilst carrying mobile computing devices that have either been customized or host applications that facilitate the provision of health related services.
The health workers and the mobile computing devices can be classified as tangible community assets having a direct impact on the positive health outcomes in their respective communities. On the other hand, the knowledge and experience of the health worker coupled with the information they retrieve, generate and store on the devices can be classified as intangible assets. In this paper, we aim to map the information security related assets that may have a direct or indirect positive effect on the overall health outcomes of a community.
3 Health Information Security
Healthcare organizations are information rich and have an implicit capacity to create or access the knowledge necessary for the successful delivery of their services [19]. Consequently, the need to ensure this information is protected and information systems are compliant with regulatory requirements is of paramount importance [1]. Patient health information is typically stored in the form of Electronic Health Records (EHRs) and the information stored within is private and confidential. The compromise of this information can have lasting negative effects on the patient and information custodian. Conforming to the security requirements however, is no easy feat, particularly in the rural context. The use of mobile computing devices adds to the complexity as data is no longer accessible from a single manageable location but through multiple terminals thereby increasing the vulnerability of the information. It is therefore important to establish existing information security assets in the environment to establish a foundation from which advanced security measures and implementations can be built upon on the road to compliance. Establishing information security assets from an asset-based perspective creates an opportunity for the identification of deployable security resources and opportunities to strengthen and fully utilize the resources for the general positive health outcomes of the community.
4 Defining IT Assets
IT assets fall into two main categories, the tangible and intangible assets. Tangible assets take on a physical form and can be seen or handled. These are typically physical resources that can contribute to the positive outcome of a community. Intangible assets have an implicit value to the community. Unfortunately, the nature of intangible assets means they are not always visible and consequently, organizations may fail to recognize them as assets and realize their full potential [19]. Intangible assets consist of resources such as information, knowledge, experience, goodwill and trust.
Assets contribute positively to the productivity and general well-being of a community. However, in developing IT systems, the focus has largely been placed on identifying needs and challenges of the communities and working towards solutions that can address the needs and challenges. This has been termed the deficit perspective. However, by definition, existing assets can play a major role in the development of community oriented solutions that leverage off the positive attributes of the existing assets to address some of the needs and challenges being faced.
The identification of assets requires a systematic methodology to identify those resources that contribute positively to the outcomes of a community. The methodology is discussed after introducing the theoretical lens applied to the study.
5 Theoretical Grounding
This section presents the theoretical lens that has been selected for use in this study. The significance of the salutogenic approach stems from the inherent lack of resources in rural settings, particularly in the African context. A salutogenic approach shifts the focus from the lack of resources (which is complex to address) to utilizing the existing resources that may or may not be readily identified as assets that can make a positive contribution to the community health outcomes.
5.1 Theory of Salutogenesis
Asset based perspectives encourage the shift in focus from identifying the pathogenic healthcare indicators to identifying the salutogenic indicators. According to Bauer, Davies, and Pelikan, [2], ongoing health development can be analyzed from salutogenic (health resources and positive health) or pathogenic (risk factors and disease) perspectives. Salutogenic perspectives emphasize the creation of health [15] and examines how resources in human life support development towards positive health (Bauer et al., 2006). Pathogenic perspectives focus on the prevention of disease by analyzing how risk factors of individuals and their environment lead to ill health [2]. All too often, health measurement instruments focus on measuring ill-health as opposed to a more holistic view on health [4]. Salutogenesis within the context of asset-based perspectives brings to focus the factors or traits, be it individual, group, or community based that contribute positively to the health outcomes of a community. The reality is that the salutogenic and pathogenic perspectives are simultaneous, co-dependent processes that interact and complement each other to achieve a common goal.
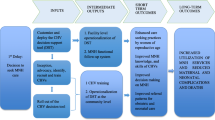
Figure 1 depicts the Asset Model developed by Morgan and Ziglio [15] which aims to redress the balance between evidence derived from the identification of problems to one which places a greater emphasis on the positive capability to jointly identify problems and activate solutions. The resulting effects promote the self-esteem of individuals and communities leading to less dependency on professional services. Morgan and Ziglio [15] define a health asset as “any factor (or resource), which enhances the ability of individuals, groups, communities, populations, social systems and/or institutions to maintain and sustain health and well-being and to help to reduce health inequities”.
The Asset Model [15]
From a rural health standpoint where fiscal and professional resources are scarce, asset-based perspectives are essential in redressing the challenges encountered in these settings. Bottom up approaches that incorporate the existing “asset infrastructure” in addressing the deficit derived challenges may result in more robust, self-propelling healthcare systems that have less of a reliance on the availability of professional skills and health information systems. On the other end of the scale are deficit-based perspectives, which are centered on identifying the community’s needs, deficiencies and problems. Deficit-based perspectives are the most commonly adopted views.
6 Methodology
There is limited literature surrounding salutogenic approaches to health information security in a rural context. Consequently, the study is exploratory in nature and employs qualitative methods of enquiry in order to obtain an in-depth view of the prevailing phenomena. A survey consisting of two qualitative questionnaires was developed. The first questionnaires were distributed to 25 rural healthcare workers who make use of netbook computers in conducting their day-to-day activities. These workers represent 80 % of the total workforce with that designated role in the organization. The second questionnaire was issued to the 5 IT support staff that directly support the community health workers. The questionnaires were developed in three parts to address three different aspects, namely, day-to-day activities, training and awareness and device and information security. In order to obtain a clear contextual perspective, the dataset used in this study was limited only to the data collected from the questionnaires. To the authors’ knowledge, no similar studies in this particular context have been conducted.
6.1 Methodology Bias
The study was conducted in the rural Eastern-Cape province of South Africa. The community health workers and the IT support staff were all conveniently sampled from the same community and report to the same non-profit organization. Consequently, the feedback could be biased towards presenting the community or the organization in a positive light for fear of reprimand. The following measures were put in place to avert bias:
-
Each participant was informed verbally and in writing that the feedback would be anonymous.
-
Confidentiality forms were distributed to each participant reassuring that the information gathered would be used explicitly for the study.
-
No participant personal details were recorded.
-
Each participant was asked to complete the questionnaire individually and the questionnaires were collected in no particular order.
6.2 Data Analysis
The development of a community asset infrastructure requires a salutogenic, systematic analysis of the operating environment in order to identify the resources that contribute positively towards the health outcomes of the community. Qualitative content analysis was used to analyze the dataset captured from the questionnaires. The pre-identified categories (day-to-day activities, training and awareness and device and information security) were used to logically organize the responses in the questionnaires. Coding was used to identify themes within the responses that represented assets within the context and those that could be deemed deficits.
The resulting output is a set of asset indicators that can be used as input in the development of community oriented healthcare solutions that contribute to the manifestation of positive community health outcomes.
7 Results
This section presents the results from the study. The results are presented according to the three aspects used in structuring the questionnaires.
7.1 Day-to-Day Activities
Community health workers in the context are issued with Institution Provided Devices (IPDs) to carry out their activities. These devices enable the faster processing and delivery of health related services while building an electronic knowledgebase of the community’s health indicators. The use of IPDs means the health workers do not have to commit any personal resources thereby removing the economic impact on the typically resource constrained workers themselves.
The presence of supervisors and team leaders in the field provides mentorship and may reassure the health workers in conducting their activities. Moreover, supervisors and team leaders may play a secondary role of surveillance which, as argued by Herath and Rao [12] may prove to be a deterrent of malicious or inappropriate activity by increasing the likelihood of getting caught. On a more positive note, the availability of mentors in the field to consult significantly reduces the likelihood for errors. The presence of a mentor also aids in the conformance to operational protocols and safe practices in the field. In this context, the supervisors and team leaders are said to be present at the distribution and collection of devices. They also ensure that recorded data is relatively error free. A final tally of the egress and ingress of devices is conducted by an IT staff member daily.
7.2 Training and Awareness
Refresher training keeps the community health worker abreast with the latest developments surrounding their line of work. These developments can include changes in operational practices and/or the introduction of new mechanisms to aid in their day-to-day activities. This periodic training provides a solid platform for the dissemination of critical information such as security reminders and security awareness. Von Solms and Von Solms [17] identify the lack of emphasis on the core importance of information security awareness amongst users as one of the “10 deadly sins of information security management. The frequent update/refresh of skills enables the health worker to consistently deliver an optimum level of care to his/her patients thereby improving the community health profile.
When asked whether they are aware of the sensitive nature of the health information stored and transmitted on the devices, the participants resoundingly responded positively indicating a high level of awareness regarding the confidentiality and privacy of the patient information. When conducting their duties, the health workers present the patients with physical documentation outlining the patients’ rights and the confidentiality requirements on the health workers part. In addition to the documentation, the health workers explain in detail the confidentiality of any information the patient may divulge to the health worker and reassures the patient that this information will only be used to assist in the delivery of health related services. The impact of the confidentiality awareness can further be substantiated by the participants who mostly indicated that the patients are generally forthcoming with their health information during consultation.
7.3 Device and Information Security
The community health workers typically work in the communities of origin, therefore, an embedded social trust relationship exists between the workers and their clients. These trust relationships nurture the development of communities that are more cohesive and characterized by strong social bonds. Morgan and Ziglio [15] suggest that such cohesive social bonds and ties are more likely to maintain and sustain health. This is substantiated further by participant responses indicating that the patients they visit in their daily routines are generally trusting of the activities of the health workers. Trust requires the patient to take some risk in believing that the health worker will in no way cause him/her harm [10] and once obtained, trust breeds confidence in proceedings and allows the patients to be forthcoming regarding various health conditions they may be experiencing thereby improving the patients’ overall health outlook.
The community health workers commute between patients while carrying (concealed) valuable devices such as netbooks and GPS mappers. However, only 2 of the 25 respondents cited security concerns when commuting with these devices. Interestingly, the view of the IT support staff was contradictory as they cited the potential for robbery while commuting with the devices as a major threat. However, taking into account the fact that the IT support staff do not work in the field and the specific communities themselves, the more accurate representation would be derived from the community health workers themselves who do the day-to-day commuting while carrying the devices.
7.4 Asset Mapping
Asset mapping supports health professionals to identify the strengths and gifts of the people who make up the community prior to intervening. The Glasgow Center for Population Health [8] describes asset mapping as documenting the tangible and intangible resources of a community. An asset-based perspective seeks to enhance these assets. Asset-based solutions leverage the existing knowledge and the positives from the community to build the foundation for self-propelling systems. The dataset was examined to identify the assets and deficits within the community as per the feedback of the participants. Factors that could be deemed as building health in the community were classified as assets and those that were deemed to be challenges were classified as deficits.
7.5 Asset Indicators
Asset indicators are the output of the asset mapping process. The set of indicators provide input into the development of community oriented solutions by leveraging off the identified indicators and developing solutions that are either built around or inclusive of the identified assets. The direct input from the community results in relevant applications that focus on furthering the health outcomes by utilizing the resources that have already been identified as enablers to the positive health outcomes (Table 1).
8 Discussion
Healthcare practitioners are bound by the Hippocratic Oath, which requires that information seen or disclosed by a patient should remain confidential. However, from a security perspective, the system is only as secure as the weakest link, and evidence suggests that in many cases, the health worker is the weakest link [16, 17]. Inadequate training and security awareness can compromise an otherwise secure system. It is therefore paramount that the Hippocratic Oath be complemented by mechanisms that can facilitate the provision of confidentiality, integrity, availability and privacy. Deficit based perspectives aim to address the needs and challenges within a community, and while necessary, a more comprehensive solution would take both perspectives into account.
The scope of this paper was to identify the asset infrastructure in the community and thus does not discuss the prevailing deficiencies. It is important however to note that no single perspective can be applied in isolation. Asset indicators can provide a good foundation for the development of self-propelling systems that rely less on the already scarce professional services.
9 Conclusion
This paper presented the asset indicators identified in a rural health community. The evidence suggests that various mechanisms can be leveraged to ease the deployment of secure systems. No single perspective provides a fully functional and sustainable solution, however, the insight gained from using both perspectives facilitates the development of a more sustainable solution that enhances deficit derived solutions by leveraging off the existing asset infrastructure.
10 Limitations and Future Work
The study was conducted in a single rural community in the Eastern Cape province of South Africa and while the results may be generalizable to similar contexts, various cultural differences cannot be accounted for. The participants surveyed only made use of netbooks, which represent a single class of mobile computing device. The feedback is therefore limited to the participants’ experiences on these particular devices. Future studies exploring a wider scope of devices and broader sample of communities may aid in the identification of additional asset indicators or place a stronger emphasis on specific assets.
The output from this study will serve as input towards the development of a framework to be used as a guide in the development of security controls in resource constrained settings. The asset indicators identified in this study will provide a baseline from which assets can be identified and further developed in other similar contexts. The success of such an endeavor will reinforce the notion that when it comes to developing security controls, one “size does not fit all” and variables such as context, culture and digital exposure must be taken into consideration.
References
Agbele, K., Nyongesa, H., Adesina, A.: lCT and information security perspectives in E-Health systems. J. Mob. Commun. 4(1), 17–22 (2010)
Bauer, G., Davies, J.K., Pelikan, J.: The EUHPID Health Development Model for the classification of public health indicators. Health Promot. Int. 21(2), 153–159 (2006)
Braun, R., Catalani, C., Wimbush, J., Israelski, D.: Community health workers and mobile technology: a systematic review of the literature. PLoS ONE 8(6), 4–9 (2013)
Bringsén, Å., Andersson, H.I., Ejlertsson, G.: Development and quality analysis of the Salutogenic Health Indicator Scale (SHIS). Scand. J. Public Health 37(1), 13–19 (2009)
Brynjolfsson, E., Hitt, L.M.: Beyond computation: information technology, organizational transformation and business performance. J. Econ. Perspect. 14(4), 23–48 (2000)
D’Arcy, P.: CIO strategies for consumerization: the future of enterprise mobile computing (Whitepaper).Dell (2011)
Disterer, G., Kleiner, C.: BYOD Bring Your Own Device. Procedia Technol. 9, 43–53 (2013)
Glasgow Center for Population Healthcph. Asset based approaches for health improvement: rederessing the balance, 1–24 October 2011
Gens, F., Levitas, D., Segal, R.: 2011 Consumerization of IT Study: Closing the “Consumerization Gap.” A report by IDC, sponsored by Unysis (2011)
Gilson, L., Palmer, N., Schneider, H.: Trust and health worker performance: exploring a conceptual framework using South African evidence. Soc. Sci. Med. 61(7), 1418–1429 (2005)
Harris, J., Ives, B., Junglas, I.: The genie is out of the bottle: managing the infiltration of consumer IT into the workforce (Whitepaper). Accenture Institute for High Performance (2011)
Herath, T., Rao, H.R.: Encouraging information security behaviors in organizations: role of penalties, pressures and perceived effectiveness. Decis. Support Syst. 47(2), 154–165 (2009)
Jovanov, E., Raskovic, D., Price, J., Chapman, J., Moore, A., Krishnamurthy, A.: Patient monitoring using personal area networks of wireless intelligent sensors. Biomed. Sci. Instrum. 37, 373–378 (2001)
Marshall, S.: IT consumerization: a case study of BYOD in a healthcare setting. Technology Innovation Management Review, pp. 14–18, March 2014
Morgan, A., Ziglio, E.: Revitalising the evidence base for public health: an assets model. Promot. Educ. 4(2 Suppl), 17–22 (2007)
Morrow, B.: BYOD security challenges: control and protect your most sensitive data. Netw. Secur. 2012(12), 5–8 (2012)
Von Solms, B., Von Solms, R.: The 10 deadly sins of information security management. Comput. Secur. 23(5), 371–376 (2004)
Vroom, C., Von Solms, R.: Towards information security behavioural compliance. Comput. Secur. 23(3), 191–198 (2004)
Wickramasinghe, N., Davison, G.: Making explicit the implicit knowledge assets in healthcare: the case of multidisciplinary teams in care and cure environments. Health Care Manag. Sci. 7(3), 185–195 (2004)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2016 IFIP International Federation for Information Processing
About this paper
Cite this paper
Kativu, K., Pottas, D. (2016). A Community Assets Infrastructure for the Secure Use of Mobile Computing Devices in the Rural Health Landscape. In: Mata, F., Pont, A. (eds) ICT for Promoting Human Development and Protecting the Environment. WITFOR 2016. IFIP Advances in Information and Communication Technology, vol 481. Springer, Cham. https://doi.org/10.1007/978-3-319-44447-5_10
Download citation
DOI: https://doi.org/10.1007/978-3-319-44447-5_10
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-44446-8
Online ISBN: 978-3-319-44447-5
eBook Packages: Computer ScienceComputer Science (R0)