Abstract
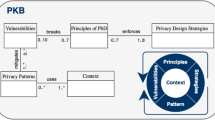
Integrating security and privacy requirements at every stage of the software development cycle is critical to guarantee the confidentiality, integrity and availability of the system and consequently of the data. Developers need to be supported in this challenge, as many different skills are required to respond effectively to the growing number of cyber-attacks. In such a context, this research study endeavors to define the key elements that support decision-making in privacy oriented software development. A Privacy Knowledge Base (PKB) is defined to support developers’ decisions in all software development phases, and a prototype (PKB-Tool) is developed to operationally integrate privacy and security requirements into the development of new systems and the re-engineering of legacy systems. An ongoing experimentation in the context of an industrial project is presented to validate the efficacy of the 5 key elements in supporting developers in integrating privacy and security requirements in the software life cycle.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
CIS benchmarks. https://www.cisecurity.org/cis-benchmarks
OWASP Top10 - 2017. Tthe ten most critical web application security risks. https://owasp.org
Al-Slais, Y.: Privacy engineering methodologies: a survey. In: 2020 International Conference on Innovation and Intelligence for Informatics, Computing and Technologies (3ICT), pp. 1–6 (2020). https://doi.org/10.1109/3ICT51146.2020.9311949
Ansari, M.T.J., Baz, A., Alhakami, H., Alhakami, W., Kumar, R., Khan, R.A.: P-STORE: extension of STORE methodology to elicit privacy requirements. Arab. J. Sci. Eng. 46(9), 8287–8310 (2021). https://doi.org/10.1007/s13369-021-05476-z
Ansari, M., Pandey, D., Alenezi, M.: STORE: security threat oriented requirements engineering methodology. J. King Saud Univ. Comput. Inf. Sci. 34(2), 191–203 (2018). https://doi.org/10.1016/j.jksuci.2018.12.005
Baldassarre, M., Barletta, V.S., Caivano, D., Raguseo, D., Scalera, M.: Teaching cyber security: the hack-space integrated model. In: CEUR Workshop Proceedings, vol. 2315 (2019)
Baldassarre, M.T., Barletta, V.S., Caivano, D., Scalera, M.: Integrating security and privacy in software development. Softw. Qual. J. 28(3), 987–1018 (2020). https://doi.org/10.1007/s11219-020-09501-6
Baldassarre, M.T., Barletta, V.S., Caivano, D., Piccinno, A.: A visual tool for supporting decision-making in privacy oriented software development. In: Proceedings of the International Conference on Advanced Visual Interfaces. AVI 2020. Association for Computing Machinery, New York (2020). https://doi.org/10.1145/3399715.3399818
Baldassarre, M.T., Barletta, V.S., Caivano, D., Scalera, M.: Privacy oriented software development. In: Piattini, M., Rupino da Cunha, P., García Rodríguez de Guzmán, I., Pérez-Castillo, R. (eds.) QUATIC 2019. CCIS, vol. 1010, pp. 18–32. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-29238-6_2
Cavoukian, A.: Operationalizing privacy by design: A guide to implementing strong privacy practices (2012)
Deng, M., Wuyts, K., Scandariato, R., Preneel, B., Joosen, W.: A privacy threat analysis framework: supporting the elicitation and fulfillment of privacy requirements. Requirements Eng. 16(1), 3–32 (2011). https://doi.org/10.1007/s00766-010-0115-7
He, Q.: A framework for modeling privacy requirements in role engineering. In: Proceedings of REFSQ, vol. 3, pp. 137–146 (2003)
Hoepman, J.H.: Privacy Design Strategies (The Little Blue Book) (2020). https://www.cs.ru.nl/~jhh/publications/pds-booklet.pdf
Jang-Jaccard, J., Nepal, S.: A survey of emerging threats in cybersecurity. J. Comput. Syst. Sci. 80(5), 973–993 (2014). https://doi.org/10.1016/j.jcss.2014.02.005, special Issue on Dependable and Secure Computing
Jensen, C., Tullio, J., Potts, C., Mynatt, E.D.: Strap: A structured analysis framework for privacy. Georgia Institute of Technology (2005). http://hdl.handle.net/1853/4450
Markus, S., Eduardo, F.B., Duane, H., Frank, B., Peter, S.: Security Patterns: Integrating Security and Systems Engineering. John Wiley & Sons, New York (2006)
Mead, N.R., Stehney, T.: Security quality requirements engineering (square) methodology. In: Proceedings of the 2005 Workshop on Software Engineering for Secure Systems-Building Trustworthy Applications, pp. 1–7. SESS 2005. Association for Computing Machinery, New York (2005). https://doi.org/10.1145/1083200.1083214
Notario, N., et al.: PRIPARE: integrating privacy best practices into a privacy engineering methodology. In: 2015 IEEE Security and Privacy Workshops, pp. 151–158 (2015). https://doi.org/10.1109/SPW.2015.22
Pattakou, A., Mavroeidi, A.G., Diamantopoulou, V., Kalloniatis, C., Gritzalis, S.: Towards the design of usable privacy by design methodologies. In: 2018 IEEE 5th International Workshop on Evolving Security Privacy Requirements Engineering (ESPRE), pp. 1–8 (2018). https://doi.org/10.1109/ESPRE.2018.00007
Pooch, U.W.: Translation of decision tables. ACM Comput. Surv. 6(2), 125–151 (1974). https://doi.org/10.1145/356628.356630
Rindell, K., Ruohonen, J., Holvitie, J., Hyrynsalmi, S., Leppänen, V.: Security in agile software development: a practitioner survey. Inf. Softw. Technol. 131, 106488 (2021). https://doi.org/10.1016/j.infsof.2020.106488
Teresa Baldassarre, M., Santa Barletta, V., Caivano, D., Piccinno, A.: Integrating security and privacy in HCD-Scrum. In: CHItaly 2021: 14th Biannual Conference of the Italian SIGCHI Chapter. CHItaly 2021. Association for Computing Machinery, New York (2021). https://doi.org/10.1145/3464385.3464746
Van Blarkom, G., Borking, J., Olk, J.: Handbook of Privacy and Privacy-Enhancing Technologies. The Case of Intelligent Software Agents (2003)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2022 IFIP International Federation for Information Processing
About this paper
Cite this paper
Baldassarre, M.T., Barletta, V.S., Caivano, D., Piccinno, A., Scalera, M. (2022). Privacy Knowledge Base for Supporting Decision-Making in Software Development. In: Ardito, C., et al. Sense, Feel, Design. INTERACT 2021. Lecture Notes in Computer Science, vol 13198. Springer, Cham. https://doi.org/10.1007/978-3-030-98388-8_14
Download citation
DOI: https://doi.org/10.1007/978-3-030-98388-8_14
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-98387-1
Online ISBN: 978-3-030-98388-8
eBook Packages: Computer ScienceComputer Science (R0)