Abstract
By using pointers, breadth-first algorithms are very easy to implement efficiently in imperative languages. Implementing them with the same bounds on execution time in purely functional style can be challenging, as explained in Okasaki’s paper at ICFP 2000 that even restricts the problem to binary trees but considers numbering instead of just traversal. Okasaki’s solution is modular and factors out the problem of implementing queues (FIFOs) with worst-case constant time operations. We certify those FIFO-based breadth-first algorithms on binary trees by extracting them from fully specified Coq terms, given an axiomatic description of FIFOs. In addition, we axiomatically characterize the strict and total order on branches that captures the nature of breadth-first traversal and propose alternative characterizations of breadth-first traversal of forests. We also propose efficient certified implementations of FIFOs by extraction, either with pairs of lists (with amortized constant time operations) or triples of lazy lists (with worst-case constant time operations), thus getting from extraction certified breadth-first algorithms with the optimal bounds on execution time.
The first author got financial support by the TICAMORE joint ANR-FWF project. The second author got financial support by the COST action CA15123 EUTYPES.
This is a preview of subscription content, log in via an institution.
Buying options
Tax calculation will be finalised at checkout
Purchases are for personal use only
Learn about institutional subscriptionsNotes
- 1.
Meaning that recursion would be pursued solely in that branch.
- 2.
- 3.
https://coq.inria.fr, we have been using the current version 8.9.0, and the authoritative reference on Coq is https://coq.inria.fr/distrib/current/refman/.
- 4.
For Coq, this method of rich specifications has been very much advocated in the Coq’Art, the first book on Coq [3].
- 5.
The authors of the current version are Filliâtre and Letouzey, see https://coq.inria.fr/refman/addendum/extraction.html.
- 6.
- 7.
Vernacular is a Coq idiom for syntactic sugar, i. e., a human-friendly syntax for type theoretical notation—the “Gallina” language.
- 8.
This is implemented in Coq by two constructors for the two rules together with an induction (or elimination) principle that ensures its smallestness.
- 9.
- 10.
- 11.
- 12.
Structural recursion is the built-in mechanism for recursion in Coq. It means that \(\mathtt {Fixpoint}\)s are type-checked only when Coq can determine that at least one of the arguments of the defined fixpoint (e. g., the first, the second...) decreases structurally on each recursive call, i. e., it must be a strict sub-term in an inductive type; and this must be the same argument that decreases for each recursive sub-call. This is called the guard condition for recursion and it ensures termination. On the other hand, it is a very restrictive form a recursion and we study more powerful alternatives here.
- 13.
As a general rule in this paper, when equations can be straightforwardly implemented by structural induction on one of the arguments, we expect the reader to be able to implement the corresponding \(\mathtt {Fixpoint}\) and so we do not further comment on this.
- 14.
The actual extracted codes for both \(\mathsf {itl}_{\mathrm {pfix}}\) and \(\mathsf {itl}_{\mathrm {eqs}}\) are not that clean but we simplified them a bit to single out two specific problems.
- 15.
Of course, it is not operationally equivalent.
- 16.
In the Coq code,
 is simply another \(\_\) hole left for the \(\mathtt {refine}\) tactic to either fill it by unification or postpone it. Because
is simply another \(\_\) hole left for the \(\mathtt {refine}\) tactic to either fill it by unification or postpone it. Because 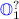 ,
, 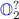 and
and  are postponed in this example, we give them names for better explanations.
are postponed in this example, we give them names for better explanations. - 17.
Because termination certificates have a purely logical content, we do not care whether \(\mathtt {omega}\) produces an “optimal” proof (b. t. w., it never does), but we appreciate its efficiency in solving those kinds of goals which we do not want to spend much time on, thus the gain is in time spent on developing the certified code. Efficiency of code execution is not touched since these proofs leave no traces in the extracted code.
- 18.
The \(\mathtt {refine}\) tactic was originally implemented by J.-C. Filliâtre.
- 19.
In his paper [14], Okasaki considered unlabeled leaves. When we compare with his findings, we always tacitly adapt his definitions to cope with leaf labels, which adds only a small notational overhead.
- 20.
We here intend to model branches from the root to nodes, rather than from nodes to leaves. It might have been better to call the concept paths instead of branches.
- 21.
The function \(\mathsf {niv}\) is called “levelorder traversal” by Jones and Gibbons [7].
- 22.
Where
 , i. e., \(\mathsf {concat}~[l_1;\ldots ;l_n] = l_1\mathop {{++}}\cdots \mathop {{++}}l_n\).
, i. e., \(\mathsf {concat}~[l_1;\ldots ;l_n] = l_1\mathop {{++}}\cdots \mathop {{++}}l_n\). - 23.
The \(\mathsf {bpn}~t\) relation, also denoted
 , relates branches and decorations.
, relates branches and decorations. - 24.
Let us stress that extensionality is not very meaningful for algorithms anyway.
- 25.
Notice that list append is denoted \(\mathbin {\texttt {@}}\) in OCaml and \(\mathop {{++}}\) in Coq.
- 26.
When a parameter X is marked implicit using the \(\{X\}\) notation, it usually means that Coq is going to be able to infer the value of the argument by unification from the constraints in the context. In the case of \(\mathsf {f2l}~l\), it means X will be deduced from the type of l which should unify with \(\mathsf {fifo}~X\). While not strictly necessary, the mechanism of implicit arguments greatly simplifies the readability of Coq terms. In particular, it avoids an excessive use of dummy arguments \(\_\).
- 27.
The fact that input and output FIFOs operate in mirror to each other was already pointed out by Okasaki in [14]. Using reversal avoids defining two types of FIFOs or bi-directional FIFOs to solve the issue.
- 28.
This condition could easily be weakened to \(\Vert {\mathsf {f2l}~q}\Vert \le |{l}|\) but in that case, the specification \(\mathsf {bfr\_fifo\_f\_spec}\) should be changed as well.
- 29.
Hence the \(\forall \{K\}\) where K is declared as implicit.
- 30.
He also found a simple solution for double-ended FIFOs.
- 31.
References
Anand, A., Boulier, S., Cohen, C., Sozeau, M., Tabareau, N.: Towards certified meta-programming with typed Template-Coq. In: Avigad, J., Mahboubi, A. (eds.) ITP 2018. LNCS, vol. 10895, pp. 20–39. Springer, Cham (2018). https://doi.org/10.1007/978-3-319-94821-8_2
Andronick, J., Felty, A.P. (eds.): Proceedings of the 7th ACM SIGPLAN International Conference on Certified Programs and Proofs, CPP 2018, Los Angeles, CA, USA, 8–9 January 2018. ACM (2018). http://dl.acm.org/citation.cfm?id=3176245
Bertot, Y., Castéran, P.: Interactive Theorem Proving and Program Development. Coq’Art: The Calculus of Inductive Constructions. Texts in Theoretical Computer Science. Springer, Heidelberg (2004). https://doi.org/10.1007/978-3-662-07964-5
Cormen, T.H., Leiserson, C.E., Rivest, R.L.: Introduction to Algorithms. The MIT Press and McGraw-Hill Book Company (1989)
Delahaye, D.: A proof dedicated meta-language. Electr. Notes Theor. Comput. Sci. 70(2), 96–109 (2002). https://doi.org/10.1016/S1571-0661(04)80508-5
Hupel, L., Nipkow, T.: A verified compiler from Isabelle/HOL to CakeML. In: Ahmed, A. (ed.) ESOP 2018. LNCS, vol. 10801, pp. 999–1026. Springer, Cham (2018). https://doi.org/10.1007/978-3-319-89884-1_35
Jones, G., Gibbons, J.: Linear-time breadth-first tree algorithms: an exercise in the arithmetic of folds and zips. Technical report, No. 71, Department of Computer Science, University of Auckland, May 1993
Larchey-Wendling, D., Monin, J.F.: Simulating induction-recursion for partial algorithms. In: Espírito Santo, J., Pinto, L. (eds.) 24th International Conference on Types for Proofs and Programs, TYPES 2018, Abstracts. University of Minho, Braga (2018). http://www.loria.fr/~larchey/papers/TYPES_2018_paper_19.pdf
Letouzey, P.: A new extraction for Coq. In: Geuvers, H., Wiedijk, F. (eds.) TYPES 2002. LNCS, vol. 2646, pp. 200–219. Springer, Heidelberg (2003). https://doi.org/10.1007/3-540-39185-1_12
Letouzey, P.: Programmation fonctionnelle certifiée - L’extraction de programmes dans l’assistant Coq. Ph.D. thesis, Université Paris-Sud, July 2004. https://www.irif.fr/~letouzey/download/these_letouzey_English.pdf
McCarthy, J.A., Fetscher, B., New, M.S., Feltey, D., Findler, R.B.: A Coq library for internal verification of running-times. Sci. Comput. Program. 164, 49–65 (2018). https://doi.org/10.1016/j.scico.2017.05.001
Mullen, E., Pernsteiner, S., Wilcox, J.R., Tatlock, Z., Grossman, D.: Œuf: minimizing the Coq extraction TCB. In: Andronick and Felty [2], pp. 172–185. https://doi.org/10.1145/3167089
Okasaki, C.: Simple and efficient purely functional queues and deques. J. Funct. Program. 5(4), 583–592 (1995)
Okasaki, C.: Breadth-first numbering: lessons from a small exercise in algorithm design. In: Odersky, M., Wadler, P. (eds.) Proceedings of the Fifth ACM SIGPLAN International Conference on Functional Programming (ICFP 2000), pp. 131–136. ACM (2000)
Paulson, L.C.: ML for the Working Programmer. Cambridge University Press, Cambridge (1991)
Picard, C., Matthes, R.: Permutations in coinductive graph representation. In: Pattinson, D., Schröder, L. (eds.) CMCS 2012. LNCS, vol. 7399, pp. 218–237. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-32784-1_12
Sozeau, M.: Subset coercions in Coq. In: Altenkirch, T., McBride, C. (eds.) TYPES 2006. LNCS, vol. 4502, pp. 237–252. Springer, Heidelberg (2007). https://doi.org/10.1007/978-3-540-74464-1_16
Sozeau, M.: Equations: a dependent pattern-matching compiler. In: Kaufmann, M., Paulson, L.C. (eds.) ITP 2010. LNCS, vol. 6172, pp. 419–434. Springer, Heidelberg (2010). https://doi.org/10.1007/978-3-642-14052-5_29
Spector-Zabusky, A., Breitner, J., Rizkallah, C., Weirich, S.: Total Haskell is reasonable Coq. In: Andronick and Felty [2], pp. 14–27. https://doi.org/10.1145/3167092
Acknowledgments
We are most grateful to the anonymous reviewers for their thoughtful feedback that included numerous detailed suggestions for improvement of the presentation.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
A Code Correspondence
A Code Correspondence
Here, we briefly describe the Coq vernacular files behind our paper that is hosted at https://github.com/DmxLarchey/BFE. Besides giving formal evidence for the more theoretical characterizations, it directly allows doing program extraction, see the README section on the given web page.
We are here presenting 24 Coq vernacular files in useful order:
-
list_utils.v: One of the biggest files, all concerning list operations, list permutations, the lifting of relations to lists (Sect. 2) and segments of the natural numbers – auxiliary material with use at many places.
-
wf_utils.v: The subtle tactics for measure recursion in one or two arguments with a \(\mathbb {N}\)-valued measure function (Sect. 2.4) – this is crucial for smooth extraction throughout the paper.
-
llist.v: Some general material on coinductive lists, in particular proven finite ones (including append for those), but also the rotate operation of Okasaki [13], relevant in Sect. 7.2.
-
interleave.v: The example of interleaving with three different methods in Sects. 2.3 (with existing tools—needs Coq v8.9 with package Equations) and Sect. 2.5 (with our method).
-
zip.v: Zipping with a rich specification and relations with concatenation – just auxiliary material.
-
sorted.v: Consequences of a list being sorted, in particular absence of duplicates in case of strict orders – auxiliary material for Sect. 3.2.
-
increase.v: Small auxiliary file for full specification of breadth-first traversal (Sect. 3.3).
-
bt.v: The largest file in this library, describing binary trees (Sect. 3.1), their branches and orders on those (Sect. 3.2) in relation with breadth-first traversal and structural relations on trees and forests (again Sect. 3.1).
-
fifo.v: the module type for abstract FIFOs (Sect. 5.1).
-
fifo_triv.v: The trivial implementation of FIFOs through lists, mentioned in Sect. 5.1.
-
fifo_2lists.v: An efficient implementation that has amortized \(\mathcal O(1)\) operations (see, e. g., the paper by Okasaki [13]), described in Sect. 7.1.
-
fifo_3llists.v: The much more complicated FIFO implementation that is slower but has worst-case \(\mathcal O(1)\) operations, invented by Okasaki [13]; see Sect. 7.2.
-
bft_std.v: Breadth-first traversal naively with levels (specified with the traversal of branches in suitable order), presented in Sect. 3.3.
-
bft_forest.v: Breadth-first traversal for forests of trees, paying much attention to the recursive equations that can guide the definition and/or verification (Sect. 4.1).
-
bft_inj.v: Structurally equal forests with the same outcome of breadth-first traversal are equal, shown in Sect. 4.3.
-
bft_fifo.v: Breadth-first traversal given an abstract FIFO, described in Sect. 5.2.
-
bfn_spec_rev.v: Characterization of breadth-first numbering, see Lemma 3.
-
bfn_fifo.v: The certified analogue of Okasaki’s algorithm for breadth-first numbering [14], in Sect. 5.3.
-
bfn_trivial.v: Just the instance of the previous with the trivial implementation of FIFOs.
-
bfn_level.v: A certified reconstruction of bfnum on page 134 (Sect. 4 and Fig. 5) of Okasaki’s article [14]. For its full specification, we allow ourselves to use breadth-first numbering obtained in bfn_trivial.v.
-
bfr_fifo.v: Breadth-first reconstruction, a slightly more general task (see next file) than breadth-first numbering, presented in Sect. 5.4.
-
bfr_bfn_fifo.v: Shows the claim that breadth-first numbering is an instance of breadth-first reconstruction (although they have been obtained with different induction principles).
-
extraction.v: This operates extraction on-the-fly.
-
benchmarks.v: Extraction towards .ml files.
Rights and permissions
Copyright information
© 2019 Springer Nature Switzerland AG
About this paper
Cite this paper
Larchey-Wendling, D., Matthes, R. (2019). Certification of Breadth-First Algorithms by Extraction. In: Hutton, G. (eds) Mathematics of Program Construction. MPC 2019. Lecture Notes in Computer Science(), vol 11825. Springer, Cham. https://doi.org/10.1007/978-3-030-33636-3_3
Download citation
DOI: https://doi.org/10.1007/978-3-030-33636-3_3
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-33635-6
Online ISBN: 978-3-030-33636-3
eBook Packages: Computer ScienceComputer Science (R0)


 is simply another
is simply another 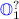 ,
, 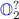 and
and  are postponed in this example, we give them names for better explanations.
are postponed in this example, we give them names for better explanations. , i. e.,
, i. e.,  , relates branches and decorations.
, relates branches and decorations.