Abstract
The paper presents the set of analytical tools for CBRN risk analysis. They are modules of WAZkA system, which is IT system supporting the analysis of contamination risks and alarming in Poland. The Event Tree is a graphical representation of a chronological sequence of events, substantial from the point of view of functioning of the object, which occur after a given event that initiates such sequence. Events Tree Analyser tool, which implements Event Tree, was built according to client-server architecture and apart from web browser it does not require any additional user-installed software. If the Event Tree is associated with an initiating event that has its location, the prototype of WAZkA system allows the calculation of the so-called Loss Table. Each row in the Loss Table corresponds to a single effect in the event tree (leaf of the tree). Having threat zones from simulation experiment (e.g. Aloha software), a specialized expert algorithm is launched, which calculates the potential human losses in each zone and inputs them in the Loss Table. Finally, the Common Operational Picture. Visualization module is used to visualize results of simulation and analyses.
You have full access to this open access chapter, Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
The main goal of the paper is to present set of software tools in WAZkA system, which are used for CBRN risk analysis and based on these analyses – ant-crisis decision making and alarming the population. WAZkA system demonstrator has been built within the scope of topics of the R&D project entitled: “Integration and support of the information management processes as well as optimization of decisions of the detection and alarming system” realized under the contest of the National R&D Center in Poland. The main objective of WAZkA [11, 18] was to develop and construct a highly developed ICT tool, required by the entities of National System for Detection of Contamination and Alarming (pol. Krajowy System Wykrywania Skażeń i Alarmowania, KSWSiA [3]) in Poland, which shall support the following processes: information exchange between the system elements and coordination of the system operations, as well as to prepare assessment and expert analyses, required by the decision-making bodies, with respect to risk emergency situations during natural disasters, technical failures or other events resulting in biological, chemical or radioactive contamination.
There is no common system in Poland that would integrate all data from different sources (i.e. threat monitoring systems, TMS), allow information exchange between KSWSiA system elements and support the decision-making bodies in performing the following actions: (a) assessment and expert analyses concerning the contamination risks and (b) warning and alarming the population about such risks. One of the components of WAZkA system is set of analytical tools for CBRN risk analysis and the paper is just focused on this subject.
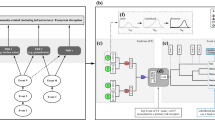
WAZkA system is aimed at collecting information obtained from various sources (Threats Monitoring Systems - TMS, see Fig. 1): starting from sensors and single observers (such as: PMS (Permanent Monitoring System) stations [7], ASS-500 stations [4, 7], stations of the Institute of Meteorology and Water Management, stations of the Automated Network of Radioactive Contamination Measurements (SAPOS), which belong to the military, and the System of Contamination Detection of the Armed Forces of the Republic of Poland), through particular levels of the anti-crisis management system and ending with national centers [3]. Furthermore, the following entities are responsible for the contamination monitoring: Provincial Sanitary-Epidemiological Stations, HACCP system, National Health Inspectorate, etc. Information in WAZkA is collected and supplemented with the results of the analyses conducted in the system environment. Such prepared data are made available to all interested parties: population, elements of the anti-crisis management system and other information media. The outcome data are made available in different forms: tabular, descriptive, graphic on a background map, text and voice notifications. Alerts and notifications, which confirm the expansion of threats and which constitute direct instruction to undertake preventive actions, are of special significance (see Sect. 2). In summary, WAZkA is a modern ICT system responsible for exchanging information on threats, preparing assessment and performing analyses of undesired events, coordinating actions, modeling scenarios, including identification of their risks, sending information to people via available warning systems (as Regional Warning System [12] or IP sirens [15]) and carrying out preparatory exercises.
The WAZkA system prototype structure [11].
The paper is organized as follows. In the Sect. 2 we describe requirements and structure of WAZkA system. Section 3 contains description of the analytical tools in WAZkA system such as: Event Tree Analyser, Loss Table and Common Operational Picture. Section 4 contains some conclusions and description of the future works.
2 Requirements and the Structure of the WAZkA System
The requirements on WAZkA system were formulated as follows:
-
1.
Exchange of information
The purpose of the requirement is to support the process of information exchange between the elements inside the contamination detection and alarming system.
-
2.
Assessment and analysis of threats
The requirement is a generalized functionality, aimed at developing and implementing a tool for the needs of the entities forming part of the contamination detection and alarming system of the tool supporting the process of preparation of expert assessments and analyses of contingency situations, resulting in biological, chemical or radioactive contamination, for the decision-making bodies.
-
3.
Coordination of activities
The purpose of the requirement is to deliver the functionality for coordinating activities of the elements inside the contamination detection and alarming system and analyses.
-
4.
Access to the threat knowledge base
The purpose of the requirement is to provide access to the developed electronic catalog of threats of chemical, biological and radioactive contamination. The catalog needs to be in a form of knowledge base, accessible and possible to expand by authorized users.
-
5.
Training session
The purpose of the requirement is to allow training of the public administration entities, using the developed products.
-
6.
Emulation of the monitoring systems
The purpose of the requirement is to feed the system with the generated test, user-controlled data on threats. It facilitates the training process and allows to verify co-operation between the system and services in case of unusual threats. Furthermore, the requirement is aimed at supporting the training system by generating the data on threats to implement the predefined scenario of development and consequences of such threats.
Figure 1 presents structure of WAZkA system prototype which has been built to fill the requirements. It consists of the following modules [11, 18]:
-
Data Acquisition & Analysis Module (DAAM) - central module of the system responsible for the analysis of data obtained from the Threats Monitoring Systems (TMS), via IM1. On the basis thereof, an assessment, arrangement in hierarchy and forecast of the risk development are made. In case of occurrence of such risks, an alert is sent to the Warning and Alarm Systems (via IM2);
-
Visualization Modules (VM) - responsible for the presentation of data and results of analyses (in particular - warnings about the risks), as needed by the KSWSiA entities. Two VMs are proposed:
-
Board - a web portal which facilitates quick access to the most recent information and the most serious risks. It is the central communication point between the KSWSiA entities. An access to the presented information is filtered depending on the privileges of a logged user;
-
Common Operational Picture (COP) - similarly to the Board module, the COP is accessed via the Internet. It presents information about the risks on a digital map.
-
-
Simulators of Threats Causes and Effects (STCE) - the simulators support the DAAM module. They allow to simulate the processes of occurrence and expansion of risks, thanks to which it is possible to generate warning and prepare appropriate measures in advance. The simulators allow also to play different variants of the risk development scenarios, which contribute to faster and less risky decision-making process with respect to risk elimination. We also use existing simulators: Aloha [14] (the hazard modeling program, which is used widely to plan for and respond to chemical emergencies) and SI Promien [8];
-
Emulators of the Threats Monitoring Systems (ETMS) allow to generate, in an artificial and user-controlled manner, data on risks, which “pretend” to be real data obtained from the monitoring systems. The approach significantly facilitates the organization of training and learning about rare situations or situations that have never occurred, but they are potentially dangerous. The subsystem of ETMS is described in detail in the paper [6];
-
Integration Module IM1 - responsible for the communication, transfer and initial processing of data from the current TMS. The data are obtained in an automated manner from the systems and entities having IT systems to process the risk-related information. For the purpose of the other entities, an interface for semi-automatic and manual data supplementation is launched (e.g. serial mail dispatch);
-
Integration Module IM2 - responsible for the integration with the existing warning and alarm systems (WAS). The risk alerts from WAZkA system are set through the above-mentioned module. WAZkA system is ready to integrate with Regional Warning System [12] and IP sirens [15]. During the testing of WAZkA system prototype, positive attempts of integration with those systems were also made [18].
3 Description of the Analytical Tools in WAZkA System
3.1 Overview
The analytical tools in WAZkA allow to process data acquired from Threats Monitoring Systems (TMS). The tools can be used by analysts in the following modes:
-
risk analysis and assessment (for a specific area of responsibility of the administration, for business, carried out periodically, for example one a year);
-
forecasting the consequences development of the danger event that took place (e.g. losses, endangered areas, etc.);
-
visualization on map of common operational picture and results of threats simulation.
Therefore, we describe the following analytical tools of WAZkA system: Event Tree Analyser, Loss Table, Common Operational Picture (COP) Visualization module.
3.2 Event Tree Analyser
The Event Tree is a graphical representation of a chronological sequence of events, significant from the point of view of functioning of the object, which occur after a given event that initiates such sequence [10] (Figs. 2, 3 and 4). This is one of the forms of the decision trees (e.g. stochastic PERT [2]). It can be used for risk analysis during planning of hazardous materials transport, risk assessment for LNG terminals [1], risk analysis of chemical industry [5]. The Event Tree [9] allows:
Recalculated Event Tree from Fig. 2 with situation after “tank bottom rupture” event done.
Recalculated Event Tree from Fig. 2 with situation after “Direct ignition” event not done.
-
determination of probability of the occurrence of a given scenario of events;
-
assessment of the final event consequences;
-
calculation of frequency of the occurrence of particular event scenarios;
-
modification of the Event Tree characteristics in case of the occurrence of specific events.
The vector of random variables constitutes the model of event sequence:
where:
A probabilistic description of the sequence model is known, if the following functions are known:
The probability of occurrence of a given scenario of events is determined based on the following relation:
where \( R(A^{(i)} ) \) is the number of scenarios for the initial event \( A^{(i)} \).
When the particular event depends on the directly preceding events, the above relation will have the following form:
In case when the occurrence of particular event does not depend on the preceding events, the above relations obtains the following form:
An example of the event tree created in the Event Tree Analyser module is presented in the Fig. 2. The tree consists of the initial event (black circle), intermediate events (rectangles with the names described inside), final events, i.e. the final states of the process (white circles) and arcs joining the tree events. Two arcs, described by the probability, are always derived from every event. One of them determines consequences of the fact that the event occurred, whereas the other one - that the event did not occur. The presented example describes development and consequences of the loss of integrity of an ammonia container. At the beginning, it is considered whether the bottom of the tank ruptured. The first consequence of the bottom of the tank rupture may be the direct ignition of the ammonia escaping. The probability of such event is equal 0.7 (opposite random event has probability equal 0.3). Then, we consider the next events which could be consequences of occurrence or non-occurrence of direct ignition. Sequence of events from initial event to final elements defines a specific scenario. Considering probability of occurrence of events in such scenario, we could evaluate probability of occurrence of a specific scenario and probability of occurrence the fixed final state, described by sequence of events. It is possible to assess of probability of occurrence of each of the intermediate events, provided that its predecessors have occurred. Event tree in Fig. 2 presents risk analyses before any events occur. But the Event Tree Analyser module allows to determine which of the events has occurred and automatically to recalculate the probabilities of events and scenarios. Figure 3 presents an example of such a situation. Green (or grey) color of the event named “Direct ignition” means that the directly preceding event “tank bottom rupture” has occurred. The probability of occurrence of the events following the event “tank bottom rupture” significantly increases. The events on an alternative scenario become improbable (it means the probability of occurrence is equal to zero). Figure 3 shows recalculated Event Tree from Fig. 2 with situation after “tank bottom rupture” not occurred and “direct ignition” not occurred.
The option of event tree recalculation, after occurrence of some events, is a new feature of the module dedicated to event tree analysis. Another significant difference is that the Event Tree Analyser module does not require to build complementary event in every scenario. If an event is not possible in a particular scenario, it is not included. It allows to avoid certain artificial aspects in the constructed trees.
An important problem relates to methods of assessment of the probability of occurrence of events in the tree. The most popular method is based on expert assessments after appropriate processing. It is also possible to apply tables of statistical data published in some reports such as in [13]. The probability of direct ignition for stationary installations and transportation units are given in the Tables 1 and 2.
Another possibility relates to application of Fault Tree model to evaluate probability of events in the event tree. The Fig. 5 presents the method of evaluation probability of occurrence initiate event “Tank rupture” in the analysed event tree.
The presented application constitutes an alternative to the solutions like the tree event analysis, e.g. Logan [16]. However, the significant difference is that the Event Tree Analyser module does not require the necessity to build complementary event in every case, even though it provides for such a possibility. Event Tree Analyser is built according to the client-server architecture, which does not need any additional user-installed software outside a web browser.
3.3 Loss Table
If the event tree is related to the initiating event, which has its location, then the prototype of WAZkA system makes it possible to calculate the so-called Loss Table (see Fig. 6). Each row in the Loss Table (a column “Nazwa Skutku”) corresponds to a single effect in the event tree (white circles, so-called tree leaves for Fig. 2). Loss Table relates to Event Tree Analyser module, Simulators of Threats Causes and Effects (STCE) module and human losses evaluation algorithm. Relationships between these elements are described below.
Loss Table for the event tree from Fig. 2 (location of the initiating event: rolling mill in Czechowice-Dziedzice, Poland).
CBRN Threats Simulation
CBRN threats simulation realizes the main numerical tasks of the module “Simulators of Threats Causes and Effects” (STCE). The current decision-making situation is reflected in the simulation scenario by the values of the parameter set, which is required by the simulation software. Most of the data is retrieved automatically from the Data Acquisition & Analysis Module (DAAM), and thus indirectly from the Threats Monitoring Systems (TMS). Other mandatory data must be completed manually by the simulator operators. The execution of a simulation experiment involves a sequence of the following steps:
-
1.
entering data into the simulation scenario (e.g. details about a real or potential chemical release);
-
2.
performing calculations based on the scenario and the operator’s decision, in accordance with hazard models and processes influencing the occurrence, evolution and effects of hazards; the simulation experiment has an autonomous run (batch mode, without interaction with the end user);
-
3.
during the experiment, all determined results shall be collected (e.g. threat zone);
-
4.
after completion of the simulation, the collected results are transferred to the evaluation and presentation components (Loss Table, COP), see, Fig. 6, left bottom corner.
The simulators, through both different computational models and differentiated scenario parameters, allow to play different variants of the risk evolution scenarios, which shall contribute to faster and less risky decision-making process with respect to risk elimination.
The main role plays Aloha [14], which is the simulation software typically for modelling air hazard. It has been developed as a part of CAMEO jointly by NOAA (National Oceanic & Atmospheric Administration) and EPA (Environmental Protection Agency). Firstly, based on scenario parameters describing a chemical release, Aloha’s models estimate the rate of leakage of a chemical a tank, puddle, or gas pipeline as well as hazardous gas cloud is formed. The complementary function calculates how that release rate may change over time (within the assumed time frame). Second, Aloha’s models how that hazardous gas cloud is migrating due to wind in two variants: neutrally buoyant and heavy gas dispersion. The other result shall appear if the chemical is flammable – the simulator will model pool fires, BLEVEs (Boiling Liquid Expanding Vapor Explosions), vapor cloud explosions, jet fires, and flammable gas clouds (i.e. when flash fires occur).
Among the different simulation outcomes, the most important are the boundary of the areas (zones) where a hazard (i.e. toxicity, thermal radiation) is predicted to exceed a specified LOC (Level of Concern) at given time after the release begins. The colour-coded zones (by red, orange, and yellow colours, see Fig. 6 – columns: RED, ORANGE, YELLOW) indicate areas where the LOC thresholds were exceeded (order by decreasing hazard). It should be mentioned that for the purpose of variant analysis the threat zones might be estimated for various parameters of hazards. Finally, the threat zone estimate will be displayed on COP map.
The highest impact for casualties from a CBRN hazards could be a distance from the source of hazard, type of environment (indoor, outdoor, roughness) and atmosphere/weather conditions. The next step is to calculate the concentration, deposition and dosages of CBRN materials outside and inside buildings with taking into account the contaminated areas and associated casualties (Loss Table).
The supported solutions have been integrated as a flexible and modular concept due to dedicated software interface. Thus, a future versions and alternative modular solutions (which have yet to be developed) might replace Aloha or compete simultaneously in order to produce series of result instead of a single.
Human Losses Evaluation Algorithm
To calculate the expected losses of human life, proceed as follows: (1) First, the user of WAZkA prototype system must simulate each of the effects in the event tree (tree leaves), using one of the threat cause and effect simulators, e.g. Aloha (output data format is KML) or SI Promien (output data format is the NATO ADatP-3); (2) After loading the simulation results into the appropriate row of the Loss Table (automatically the software tool is run, so called “parser”, which enters the simulation results into the table structure in the Data Acquisition & Analysis Module (DAAM), see Fig. 1), the columns “Promień Stref Zagrożenia” (“Radius of Risk Zones”) in the Loss Table (based on the simulation results) are automatically filled in; (3) having threat zones, a specialized expert algorithm is activated, which using the geographical coordinates of the envelopes of the zones classifies these zones into communes, column “Gminy objęte zagrożeniem” (specifying the part of each commune included in the zone, commune borders are taken from the TERYT register [17]) and, knowing the estimation of the number of inhabitants of communes and taking into account the time of day, calculates potential human losses in each zone and input them into the Loss Table in the column “Spodziewane straty w ludziach” (“Expected human losses”).
3.4 Common Operational Picture
The Common Operational Picture (COP) Visualization Module performs the following main functions:
-
presentation of objects on map backgrounds according to the NATO APP-6A symbol and the Ministry of Interior and Administration in Poland;
-
decision support, e.g. in the form of delimitation of flood zones and profiles of the site; they can be applied to the threat data under consideration, which significantly facilitates the analysis of the crisis situation under consideration;
-
making map measurements of indicated routes, areas;
-
management of WMS (Web Map Service) compliant data layers, allowing to enrich the image of operations with satellite data, analytical maps, terrain elevation models and other analytical data related to e.g. weather data;
-
displaying 30 predefined GIS layers from the following data sources: Geoportal.pl, Bing Maps, OpenStreetMap, Wikimedia, OpenWeatherMap;
-
displaying vector data layers of GIS in the form of KML, GeoJSON, TopoJSON, MVT;
-
management of geographical POI information (supplemented with data from threat zones) and mechanisms of searching (data visibility restrictions) for POIs (Point of Interest);
-
address data search engine and map location indication functions;
-
copying geographical coordinates and preparing them in many acceptable formats in the rest of WAZkA application;
-
management of reported data (recorded, analyzed) of threat data;
-
visualization of data from the simulation of threat development transferred in the form of vector data of KML layers.
Moreover, the COP Visualization Module has been integrated into WAZkA system in the following areas (see Fig. 7):
Integrated image of operations (COP) in the prototype of WAZkA system presenting both simulation data of threat development, as well as elements of static situation (infrastructure) and units of the Ministry of Interior and Administration and the Ministry of Foreign Affairs participating in crisis management.
-
entering the coordinates of the place where the initiating event took place in the Data Acquisition & Analysis Module (DAAM);
-
depicting the selected locations of the so-called ongoing threats visible in the Board Visualization Module, previously entered in the Data Acquisition & Analysis Module (DAAM);
-
results of simulations from Aloha and SI Promien.
4 Conclusions
The analytical tools presented in the paper have undergone testing with the participation of crisis management experts. The results of the tests are suggestions for further development of the analytic tools. It is foreseen:
-
replacing the event tree with a dynamic Bayesian Network, what give the possibility to consider the impact of “non-binary” factors on the probability of events occurring, a more flexible model of dependence of factors determining the occurrence of events and elapsed time between events (taking into account the duration of activities ending with events);
-
fully automated transfer of data from the simulation of the final states of the event tree to the analytical module;
-
implementation of a graph database for storing and searching for similar event trees;
-
use of spatial statistical data from the system “Geostatistics portal” of the Statistical Office (GUS in Polish).
References
Aneziris, O.N., Papazoglou, I.A., Konstantinidou, M., Nivolianitou, Z.: Integrated risk assessment for LNG terminals. J. Loss Prev. Process Ind. 28, 23–35 (2014)
Antkiewicz, R., Gąsecki, A., Najgebauer, A., Pierzchała, D., Tarapata, Z.: Stochastic PERT and CAST logic approach for computer support of complex operation planning. In: Al-Begain, K., Fiems, D., Knottenbelt, William J. (eds.) ASMTA 2010. LNCS, vol. 6148, pp. 159–173. Springer, Heidelberg (2010). https://doi.org/10.1007/978-3-642-13568-2_12
Binek, T., Czepiel, J.: The national system of contamination detection and alarm, currently operating in Poland. BiTP 36(4), 15–24 (2014)
Grabowski, D., Kurowski, W., Muszynski, W., Rubel, B., Smagala, G., Swietochowska, J.: Radiation monitoring network in Poland. Nukleonika 46(4), 147–149 (2001)
Jelemenský, L., Harisová, J., Molnár, A., Marko, J.: Reliable risk estimation in the risk analysis of chemical industry case study: ammonia storage pressurized spherical tank. Chem. Pap. Slovak Acad. Sci. 58(1), 48–54 (2004)
Kulas, W., Tarapata, Z.: An IT tool to support anti-crisis training in WAZkA system: a case study. In: Czachórski, T., Gelenbe, E., Grochla, K., Lent, R. (eds.) ISCIS 2018. CCIS, vol. 935, pp. 158–165. Springer, Cham (2018). https://doi.org/10.1007/978-3-030-00840-6_18
Lipiński, P., Isajenko, K., Biernacka, M., Żak, A.: Integration of polish monitoring networks (ASS-500 and PMS systems). Nukleonika 46(4), 143–146 (2001)
Mlynarczyk, M., Maciejewski, P., Szerszen, M.: CBRN analysis and SI Promień – comparison of the functionality of the software for the assessment of contamination. BiTP 40(4), 133–138 (2015)
Pate-Cornell, M.E.: Fault trees vs. event trees in reliability analysis. Risk Anal. 4(3), 177–186 (1984)
Schüller, J.C.H., Brinkman, J.L., Van Gestel, P.J., van Otterloo, R.W.: Methods for Determining and Processing Probabilities, Committee for Prevention of Disasters (Red Book), The Hague, Netherlands (1997)
Tarapata, Z., et al.: A computer system for CBRN contamination threats analysis support, prediction their effects and alarming the population: polish case study. In: CSCC 2017, MATEC Web of Conferences, vol. 125, p. 02012 (2017)
Tuśnio, R.: Applications for mobile devices informing about threats. In: FESE 2018, MATEC Web of Conferences, vol. 247, p. 00012 (2018)
Uijt de Haag, P.A.M., Ale, B.J.M.: Guidelines for Quantitative Risk Assessment (Purple Book), The Advisory Council on Dangerous Substances, The Hague, Netherlands (2005)
Aloha Software Homepage. https://www.epa.gov/cameo/aloha-software. Accessed 05 Dec 2018
digitexCZK/IP System Homepage. https://www.publicalerting.com/products/public-warning-system/advantages-of-digitexczkip/. Accessed 05 Dec 2018
LOGAN System Homepage. http://loganfta.com. Accessed 05 Dec 2018
TERYT register Homepage. http://eteryt.stat.gov.pl/eTeryt/english.aspx. Accessed 31 Dec 2018
WAZkA Project Homepage. http://wazka.wat.edu.pl/. Accessed 05 Dec 2018
Acknowledgements
This work was partially supported by grant No DOB-BIO7/12/01/2015 of Polish National Center for Research and Development (NCBiR) titled “Integration and support of information management processes and decision optimization in warning and alarm system” and Statutory Research Work in the Institute of Computer and Information Systems, Cybernetics Faculty, Military University of Technology in Warsaw, Poland.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2019 IFIP International Federation for Information Processing
About this paper
Cite this paper
Antkiewicz, R., Tarapata, Z., Pierzchała, D., Rulka, J., Najgebauer, A. (2019). CBRN Risk Analysis Using the Analytical Tools of the WAZkA System. In: Murayama, Y., Velev, D., Zlateva, P. (eds) Information Technology in Disaster Risk Reduction. ITDRR 2018. IFIP Advances in Information and Communication Technology, vol 550. Springer, Cham. https://doi.org/10.1007/978-3-030-32169-7_4
Download citation
DOI: https://doi.org/10.1007/978-3-030-32169-7_4
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-32168-0
Online ISBN: 978-3-030-32169-7
eBook Packages: Computer ScienceComputer Science (R0)