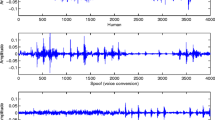
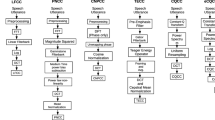
Abstract
Automatic Speaker Verification (ASV) systems are more vulnerable to being attacked than other biometric systems, such as speech synthesis, voice conversion, and replay. In this paper, two frameworks (Gaussian mixture model based and i-vector based) are used to detect a variety of specific attack types. Three scoring methods (probabilistic normalization, linear regression and support vector machine) are used for the Gaussian Mixture Model (GMM) model. And three different classifiers (cosine distance, probabilistic linear discriminant analysis, support vector machine) are used for the i-vector system. Furthermore, the cosine classifier based on the i-vector system which uses three scoring methods is proposed in this paper. Experiments on the ASVspoof 2019 challenge logical access scenario show that the GMM classifier with the Support Vector Machines (SVM) scoring method based on different spoofing algorithms obtains the best performance on the evaluation set with EER of 7.03%. Moreover, SVM scoring is also useful for improving the i-vector system based on different spoofing algorithms.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
ZhiZheng, W., Evans, N., Kinnunen, T., Yamagishi, J., Alegre, F., Li, H.: Spoofing and countermeasures for speaker verification: a survey. Speech Commun. 66, 130–153 (2015)
Hautamäki, R.S., et al.: Automatic versus human speaker verification: the case of voice mimicry. Speech Commun. 72, 13–31 (2015)
Zhizheng, W., Leon, P.L., Demiroglu, D., Khodabakhsh, A., et al.: Anti-spoofing for text-independent speaker verification: an initial database comparison of countermeasures and human performance. IEEE/ACM Trans. Audio Speech Lang. Process. 20(8), 768–783 (2016)
Zhizheng, W., Yamagishi, J., Kinnunen, T., Sahidullah, Md, et al.: ASVspoof: the automatic speaker verification spoofing and countermeasures challenge. IEEE J. Sel. Top. Sign. Process. 11(4), 588–604 (2017)
Yamagishi, J., Kinnunen, T., Evans, N., De Leon, P.L.: Introduction to the issues on spoofing and countermeasures for automatic speaker verification. IEEE J. Sel. Top. Sign. Process. 11(4), 585–587 (2017)
Xiaohai, T., SiuWa, L., Zhizheng, W., Eng Siong, C., Haizhou, L.: An example-based approach to frequency warping for voice conversation. IEEE/ACM Trans. Audio Speech Lang. Process. 25(10), 1863–1876 (2017)
Rohan Kuman, D., Haizhou, L.: Instantaneous phase and excitation source features for detection of replay attacks. In: Asia-Pacific Signal and Information Processing Association (APSIPA) Annual Summit and Conference (ASC) 2018, November 2018
ASVspoof 2019: Automatic speaker verification spoofing and countermeasures challenge evaluation plan. http://www.asvspoof.org/asvspoof2019/asvspoof2019evaluation/plan.pdf
Kinnunen, T., Wu, Z.-Z., Lee, K.A., Sedlak, F., Chng, E.S., Li, H.: Vulnerability of speaker verification systems against voice conversion spoofing attacks: the case of telephone speech. In: ICASSP (2012)
Lorenzo Trueba, J., et al.: The voice conversion challenge 2018: promoting development of parallel and nonparallel methods. In: The Speaker and Language Recognition Workshop, Odyssey, pp. 195–202 (2018)
Leon, P.L.D., Apsingekar, V.R., Pucher, M., Yamagishi, J.: Revisiting the security of speaker verification systems against imposture using synthetic speech. In: Proceedings ICASSP, pp. 1798–1801 (2010)
Farrús, M.: Voice disguise in automatic speaker recognition. ACM Comput. Surv. 51(4), 681–6822 (2018)
Alegre, F., Vipperla, R., Evans, N.W.D., Fauve, B.G.B.: On the vulnerability of automatic speaker recognition to spoofing attacks with artificial signals. In: Proceedings EUSIPCO, pp. 36–40 (2012)
Sahidullah, M., Kinnunen, T., Hanilci, C.: A comparison of features for synthetic speech detection. In: Proceedings INTERSPEECH, pp. 2087–2091 (2015)
Gomez-Alanis, A., et al.: Performance evaluation of front-and back-end techniques for ASV spoofing detection systems based on deep features. In: Proceedings IberSPEECH 2018, pp. 45–49 (2018)
Alam, M.J., Kenny, P., Bhattacharya, G., Stafylakis, T.: Development of crim system for the automatic speaker verification spoofing and countermeasures challenge 2015. In: Proceedings INTERSPEECH, pp. 2072–2076 (2015)
Kannangola, D., et al.: Factor analysis methods for joint speaker verification and spoof detection. In: Proceedings ICASSP, pp. 5385–5389 (2017)
Todisco, M., Delgado, H., Evans, N.: A new feature for automatic speaker verification anti-spoofing: constant Q cepstral coefficients. In: Proceedings Odyssey (2016)
Novoselov, S., Kozlov, A., Lavrentyeva, G., Simonchik, K., Shchemelinin, V.: STC anti-spoofing systems for the ASVspoof 2015 challenge. In: Proceedings IEEE International Conference Acoustics, Speech and Signal Processing (ICASSP), pp. 5475–5479 (2016)
Weng, S., et al.: The SYSU system for the interspeech 2015 automatic speaker verification spoofing and countermeasures challenge. In: Proceedings APSIPA, pp. 152–155 (2015)
Reynolds, D.A., Quatieri, T.F., Dunn, R.B.: Speaker verification using adapted Gaussian mixture models. Digit. Signal Process. 10(1–3), 19–41 (2000)
Wang, L., Yoshida, Y., Kawakami, Y., Nakagawa, S.: Relative phase information for detecting human speech and spoofed speech. In: Proceedings INTERSPEECH, pp. 2092–2096 (2015)
Nanxin, C., et al.: Robust deep feature for spoofing detection—The SJTU system for ASVspoof 2015 challenge. In: Sixteenth Annual Conference of the International Speech Communication Association (2015)
Dehak, N., Kenny, P., Dehak, R., Dumouchel, P., Ouellet, P.: Front-end factor analysis for speaker verification. IEEE Trans. Audio Speech Lang. Process. 19(4), 788–798 (2011)
Kinnunen, T., et al.: t-DCF: a detection cost function for the tandem assessment of spoofing countermeasures and automatic speaker verification. In: Proceedings Odyssey, Les Sables d’Olonne, France, June 2018
Hatch, A.O., Kajarekar, S.S., Stolcke, A.: Within-class covariance normalization for SVM-based speaker recognition. In: Proceedings ICSLP (2006)
Garcia-Romero, D., Espy-Wilson, C.Y.: Analysis of i-vector length normalization in speaker recognition systems. In: Proceedings INTERSPEECH, pp. 249–252 (2011)
Acknowledgements
This work is supported by National Natural Science Foundation of P.R. China (61365004, 61662030), and by Educational Commission of Jiangxi Province of P.R. China (GJJ170205).
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2019 Springer Nature Switzerland AG
About this paper
Cite this paper
Tang, H., Lei, Z., Huang, Z., Gan, H., Yu, K., Yang, Y. (2019). The GMM and I-Vector Systems Based on Spoofing Algorithms for Speaker Spoofing Detection. In: Sun, Z., He, R., Feng, J., Shan, S., Guo, Z. (eds) Biometric Recognition. CCBR 2019. Lecture Notes in Computer Science(), vol 11818. Springer, Cham. https://doi.org/10.1007/978-3-030-31456-9_55
Download citation
DOI: https://doi.org/10.1007/978-3-030-31456-9_55
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-31455-2
Online ISBN: 978-3-030-31456-9
eBook Packages: Computer ScienceComputer Science (R0)