Abstract
The success of a UAV mission depends on communication between a GCS (Ground Control Station) and a group of UAVs. It is essential that the freshness of the commands received by UAVs is maintained as mission parameters often change during an operation. Ensuring the freshness of the commands received by UAVs becomes more challenging when operating in an adversarial environment, where the communication can be impacted by interference. We model this problem as a game between a transmitter (GCS) equipped with directed antennas, whose task is to control a group of UAVs to perform a mission in a protected zone, and an interferer which is a source spherically propagated jamming signal. A fixed point algorithm to find the equilibrium is derived, and closed form solutions are obtained for boundary cases of the resource parameters.
You have full access to this open access chapter, Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
In many Unmanned Aerial Vehicle (UAV) applications, a Ground Control Station (GCS) communicates with a group of UAVs to send instructions to control each UAV’s mission. However, when such active communication faces the threat of hostile interference, the result can be delay or even interruption in getting such instructions. Larger periods of delay or interruption lead to reduced freshness of received instructions, and can decrease the probability of mission success. Thus we model the probability of mission success as a function of the age of the received information. Such considerations have been gaining prominence in the research literature lately, as reflected by interest in the age of information (AoI), a system delay performance metric that has been widely employed in different applications [1, 13, 23, 25, 26].
The pioneering paper, on the impact of hostile interference on age of information is [17]. Our work is based the model of [17] suggesting a relationship between SINR at the receiver and AoI of update packets. We employ this approach to model a scenario where a group of UAVs is cooperating to perform a mission. A transmitter GCS employs directional antennas to control the UAVs while jammer radiates a spherically symmetric interference intended to cause the mission to fail. We model this problem via a game-theoretical approach. An interesting feature of this problem is that the rivals have different structures for their strategies. Specifically, the GCS’s strategy is power allocation individually between the UAVs, while the interferer’s strategy involves assigning power to jam the whole UAV group. While for most jamming games studied in literature rivals strategies have the same structure: either power allocation for both rivals [16, 20, 24] or assigning power level [7, 12, 17, 22] for both rivals.
2 Model
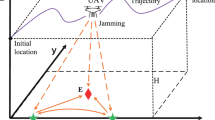
We consider a group of n UAVs that, following their route/mission to a target in a protected zone, must communicate with the GCS to get/verify position and mission data. The GCS is equipped with n antennas (or n separate antenna beams) to communicate with these UAVs. This communication can be damaged by active interference that might lead to loss of navigation commands and failure of the mission. An interferer, located in the protected zone, is a source of spherically symmetric interference intended to cause the UAV mission to fail. As a metric for data updating in this paper, we consider AoI which reflects the time that has passed since the last update. We assume that the probability \(\pi _S\) of mission success is a function of the average age of information A, and this function is decreasing with A such that: (a) \(\pi _S(0)=1\), i.e., if the data is up-to-date the mission succeeds with certainty; and (b) \(\pi _S(A)\downarrow 0\) for \(A\uparrow \infty \), i.e., if data is never updated, then the mission fails with certainty. To model the probability of mission success, we will use the ratio form contest success function. This is commonly used to translate involved resources into probability of winning or losing, and has been widely applied in different economic and attack-defense problems in the literature; see, for example, [5, 9, 11, 19, 21]. In our scenario, the metric that dictates whether the mission is successful or fails, is age of information. Specifically, in terms of positive constants a and b, the probability of mission success is
2.1 Age of Information
To model age of information, we will employ a generalization of the model introduced in [17]. For convenience of the readers, we give a brief description:
- (i) :
-
The GCS can transmit at a rate that is proportional to the signal to interference plus noise ratio (SINR) at the receiver. Following [17], when \(p_i\) and q are the powers of the transmitting signal by GCS to UAV i and interfering signal, and \(h_i\) and \(g_i\) are the corresponding channel gains to the UAV, the packet transmission rate associated with power profile \((p_i,q)\) is
$$\begin{aligned} \begin{aligned} \mu _i(p_i,q)=z_i\text{ SINR }(p_i,q)=z_i\frac{g_ip_i}{N_i+h_iq}, \end{aligned} \end{aligned}$$(2)where \(N_i\) is background noise power and \(z_i\) is a positive constant.
- (ii) :
-
Depending on the model for how update packets are delivered to the UAV, the age of information metric \(A_i\) takes on the form
$$\begin{aligned} \begin{aligned} A_i(p_i,q)=\frac{c}{\lambda _i}+\frac{d}{\mu _i(p_i,q)} \end{aligned} \end{aligned}$$(3)for packet arrival rate \(\lambda _i\) and constants \(c\ge 0\) and \(d>0\). In particular, when \((c,d)=(1,2)\) and fresh update packets are generated at the UAV as a rate \(\lambda \) Poisson process, the age metric A(p, q) corresponds to the average peak age of an M/G/1/1 queue [3, 10]. This is the age metric employed in [17].
We note that various other age metrics can be modeled by specifying (c, d) in (3). For example, with \((c,d)=(1,1)\), \(A_i(p_i,q)\) is the average AoI of an M/M/1/1 server supporting preemption in service [15]. Furthermore, with \((c,d)=(0,2)\) and just-in-time arrivals (i.e., a fresh update goes into service precisely when the server would become idle) at a rate \(\mu _i(p_i,q)\) memoryless server, \(A_i(p_i,q)\) is again the average AoI [14]. Finally, with \((c,d)=(0,3/2)\), \(A_i(p_i,q)\) corresponds to just-in-time updates transmitted with deterministic service times at rate \(1/\mu _i(p_i,q)\) [14]. In the following, we refer to \(A_i(p_i,q)\) as the AoI for any \(c\ge 0\) and \(d>0\).
2.2 Formulation of the Game
To define game we have to describe: (a) the set of players, (b) the set of feasible strategies of each player, and (c) the player’s payoff [4]. In our scenario, there are two players: the interferer and the GCS. A strategy of the GCS is a non-negative power vector \({\varvec{p}}=(p_1,\ldots ,p_n)\), where \(p_i\) is the power employed to communicate with UAV i, and \(\sum _{i=1}^n p_i={\overline{p}}\) is the total power. Let \(\varPi _{\text {GCS}}\) be the set of all feasible GCS strategies. A strategy of the interferer is a power level q of the jamming signal. Let \(\varPi _I={\mathbb {R}}_+\) be the set of all feasible interferer’s strategies. Note that the probability of mission success for UAV i is
We now introduce the auxiliary notations:
With this notation, (4) becomes
As criteria for mission success we consider proportional fairness criteria [6, 18] for mission success of each UAV, i.e.,
This utility is the payoff for the GCS. For the interferer, the cost function is the sum of the GCS payoff and the involved cost of the effort, i.e.,
where \(C_I\) is the cost per unit of jamming power. The GCS wants to maximize its payoff, while the interferer aims to minimize its cost function. So, \(-v_I\) is the payoff to the interferer. We are looking for Nash equilibrium. Recall that \(({\varvec{p}},q)\) is a Nash equilibrium [4] if and only if:
We denote this game by \(\varGamma =\varGamma (v_{\text {GCS}},\varPi _{\text {GCS}};-v_I,\varPi _I).\)
Lemma 1
\(v_{\text {GCS}}({\varvec{p}},q)\) is concave in \({\varvec{p}},\) and \(v_I({\varvec{p}},q)\) is convex in q.
Proof
Note that
and the result follows. \(\blacksquare \)
Lemma 1 and the Nash theorem [4] imply the following result.
Theorem 1
In the game \(\varGamma \) there exists at least one equilibrium.
3 Solution of the Game
In this section we design equilibrium strategies of the game \(\varGamma \). By (9), \({\varvec{p}}\) and q are equilibrium strategies if and only if each of them is the best response to the other, i.e., they are solutions of the equations:
To solve these best response equations we will employ a constructive approach.
3.1 Best Response Strategies
In this section we derive the best response strategies.
Theorem 2
The best response strategy \({\varvec{p}}\) of the GCS to jamming power q is unique and given as follows:
where for each fixed q, \(\varOmega (q)=\omega \) is the unique positive root of the equation
with
Proof
Since, by Lemma 1, (10) is a concave NLP problem, to find the best response strategy \({\varvec{p}}\) to q we have to introduce a Lagrangian depending on a Lagrange multiplier \(\omega \) as follows: \( L_{\omega }({\varvec{p}})= v_{\text {GCS}}({\varvec{p}},q)+\omega \left( {\overline{p}}-\sum _{i=1}^np_i\right) . \) Then, KKT Theorem implies that \({\varvec{p}}\in \varPi _{\text {GCS}}\) is the best response strategy to q if and only if the following condition holds:
By (16), we have that \(p_i>0\) for any i. Thus, also \(\omega >0\), and
Solving this equation in \(p_i\) implies \(p_i=P_i(\omega ,q)\) as given by (15).
Since \({\varvec{p}}\in \varPi _{\text {GCS}}\) the \(\omega \) is defined by the condition that the total power resource has to be utilized by the GCS, i.e., by Eq. (13).
Note that \(P_i(\omega ,q)\) given by (15) has the following properties:
- (i) :
-
\(P_i(\omega ,q)\) is differentiable in \(\omega \) and q
- (ii) :
-
\(P_i(\omega ,q)\) is decreasing in \(\omega \) from infinity for \(\omega \downarrow 0\) to zero for \(\omega \uparrow \infty \).
- (iii) :
-
\(P_i(\omega ,q)\) is increasing in q to \(1/\omega \) for \(q\uparrow \infty \).
Note that (i) and (ii) straightforwardly follow from (15). By (15), for a fixed \(\omega >0\)
Also, \(P_i(\omega ,q)=f_i(\varGamma _i(q))/(2\beta _i),\) where \(f_i(x)=x(\sqrt{1+m/x}-1)\) with \(m=4\beta _i/\omega \). Since \( \frac{df_i(x)}{dx}=\frac{2x+m}{2\sqrt{x^2+mx}}-1>0,\) \(P_i(\omega ,q)\) increases with q. This and (18) implies (iii). Then, (i) and (ii) yield existence of the unique root \(\omega =\varOmega (q)\) for Eq. (13). While (i)–(iii) and (18) imply that \(\varOmega (q)\) increases with q to \(n/{\overline{p}}\). \(\blacksquare \)
Note that, \(\varOmega (q)\) can be found via bisection method and \(\varOmega (q)\) is differentiable for \(q\ge 0\) and increasing from \(\omega _0\) for \(q=0\) to \(n/{\overline{p}}\) for \(q\uparrow \infty \), where \(\omega _0\) is the unique positive root of the equation:
Theorem 2 straightforwardly implies the following result.
Corollary 1
The inverse function \(Q(\omega )=\varOmega ^{-1}(q)\) to \(\varOmega (q)\) is defined for \(\omega \in [\omega _0,n/{\overline{p}})\) and increases from \(Q(\omega _0)=0\) to \(\lim _{\omega \uparrow (n/{\overline{p}})} Q(\omega )=\infty \). Moreover, \(S_P(\omega ,Q(\omega ))={\overline{p}}.\)
Theorem 3
The best response strategy q of the interferer to \({\varvec{p}}\) is unique and given as follows:

such that, when (20b) holds, \(q_+\) is the unique positive root of
Proof
Since, by Lemma 1, \(v_I({\varvec{p}},q)\) is a convex in q, by (11), q is the best response strategy to \({\varvec{p}}\) if and only if the following condition holds:
Since \(\gamma _i/(\beta _i p_i+\varGamma _i(q))\) is decreasing in q, the result straightforward follows from (22). \(\blacksquare \)
3.2 Equilibrium
In this section we establish threshold value of the jamming cost for the interferer to be active, derive the form the equilibrium has to have and design a fixed point algorithm to find the equilibrium.
Theorem 4
(a) If
then \(({\varvec{p}},q)=({\varvec{P}}(\omega _0,0),0)\) is the unique equilibrium where \(\omega _0\) and \({\varvec{P}}\) given by (15) and (19) correspondingly.
(b) If (23) does not hold then \(({\varvec{p}},q)=({\varvec{P}}(\varOmega (q),q),q)\) is the equilibrium where \({\varvec{P}}\) given by (15) and q is the positive root of the equation
where
Proof
Let \(({\varvec{p}},q)\) be an equilibrium. By Theorem 2, \({\varvec{p}}>0\). Thus, only two cases arise to consider: (a) \(q=0\) and (a) \(q>0\).
-
(a)
Let \(q=0\). Then, by Theorem 2, \({\varvec{p}}={\varvec{P}}(\omega _0,q)\). Substituting this \({\varvec{p}}\) into (20a) implies (20a).
-
(b)
Let \(q>0\). Then, by Theorem 2, \({\varvec{p}}={\varvec{P}}(\varOmega (q),q)\). Substituting this \({\varvec{p}}\) into (21) implies (24) and (25). By (21), q is decreasing in \(C_I\). Thus, by (24) and (25), F also decreasing in \(C_I\), and the result follows. \(\blacksquare \)
By Theorem 2, we have that \(\lim _{q\uparrow \infty } F(q)=0\). Moreover, if (23) does not hold then \(F(0)>C_I/2.\) Also, note that (23) establishes the threshold on the jamming cost for the interferer to be active (i.e., for \(q>0\) to be an equilibrium) or non-active (i.e., for \(q=0\) to be an equilibrium). While the GCS is always active in communication with each of the UAVS. This remarkably differs with OFDM jamming problem where some of sub-subcarriers could be not involved in transmission [8] and network security problem where some not might be not protected [2].
Interestingly, the equilibrium q can be found using fixed point algorithm. To do so, note that, by Theorem 2 and Corollary 1, there is one-to-one correspondence between \(\omega \) and q. That is why first in the following proposition we derive an equation for \(\omega \), and, then, in Theorem 5, we prove convergence of the fixed point algorithm to find the \(\omega \).
Proposition 1
Equation (24) is equivalent to
with \(q=Q(\omega )\), where
Proof
Note that
Substituting this into (24) and (25) imply the result. \(\blacksquare \)
The following theorem shows that Eq. (26) can be solved by fixed point algorithm.
Theorem 5
\(G(\omega )\) has the following properties:
- (i) :
-
\(G(\omega _0)<\omega _0\);
- (ii) :
-
\(G(\omega )\) is continuous and increasing on \(\omega \);
- (iii) :
-
There is \(\omega _*\) such that \(G(\omega )<\omega \) for \(\omega <\omega _*\) and
$$\begin{aligned} G(\omega _*)=\omega _*; \end{aligned}$$(28) - (iv) :
-
The fixed point \(\omega _*\) of (28) can be found via fixed point algorithm:
$$\begin{aligned} \omega ^m=G^{-1}(\omega ^{m-1}) \text{ for } m=1,2,\ldots \text{ with } \omega ^0 \text{ is } \text{ fixed. } \end{aligned}$$The algorithm converges to \(\omega _*\) for any \(\omega ^0\in (\omega _0,\omega _*)\).
Proof
(i) follows from (20b). (ii) follows from Corollary 1 and (27). (iii) follows from (i), (ii), Theorems 1, 4(b) and Proposition 1.
Since \(\omega ^0<\omega _*\), by (ii) and (iii), \(G(\omega ^0)<\omega ^0.\) Then, (28) implies that there is the unique \(\omega ^1\in (\omega ^0,\omega _*)\) such that \(G(\omega ^1)=\omega ^0.\) Thus, \(\omega ^1=G^{-1}(\omega ^0).\) Similarly, there is the unique \(\omega ^2\in (\omega ^1,\omega _*)\) such that \(G(\omega ^2)=\omega ^1,\) and so on, i.e., there is the unique \(\omega ^{m}\in (\omega ^{m-1},\omega _*)\) with \(m\ge 1\) such that \(G(\omega ^{m})=\omega ^{m-1}.\) Thus, \(\omega ^m\) is increasing and upper-bounded. Thus, there exists \(\lim _{m\uparrow \infty }\omega ^m\), and, this limit is equal to \(\omega _*\). \(\blacksquare \)
Note that for boundary cases of the jamming cost and total transmission power the equilibrium strategies can be obtained in closed form:
Proposition 2
(a) Let \(C_I\) be small. Then
(b) Let \({\overline{p}}\) be small. Then \(p_i\approx {\overline{p}}/n, i=1,\ldots , n\) and

where \(q_*\) is the unique positive root of the equation
(c) Let \({\overline{p}}\) be large. Then \(q=0\) and
Proof
Let \(C_I\) be small. Then, by (20b), \(q=q_+\). While, by (21), \(q_+\) is large. Then, Eq. (21) can be approximated by \(n/q_+\approx C_I\). Thus, \(q=n/C_I.\) Substituting this q into (15) implies that \(P_i(\omega ,q)\approx 1/\omega \), and (a) follows. Let \({\overline{p}}\) be small. Then \(p_i\) also is small for any i. Substituting these \(p_i\) into (20a), (20b) and (21) and taking into account that \({\varvec{p}}\in \varPi _{\text {GCS}}\) implies imply (b). Let \({\overline{p}}\) be large. Then \(p_i\) is large for at least one i. Then, by (20a), \(q=0\). Then, by (13) and (15), \(\omega \) is small, and \( p_i=P_i(\omega ,0)\approx \sqrt{\delta _i/\beta _i}/\sqrt{\omega }. \) Then, since \({\varvec{p}}\in \varPi _{\text {GCS}}\), (32) follows. \(\blacksquare \)
If background noise can be neglected, then equilibrium strategies also can be found in closed form.
Proposition 3
If \(\delta _i=0\) for all i, then,
-
(a)
if
$$\begin{aligned} \sum _{i=1}^n \sqrt{\gamma _i/\beta _i}\le \sqrt{{\overline{p}}C_I} \end{aligned}$$(33)then \(q=0\) is the unique interferer strategy, while there is a continuum of the GCS equilibrium strategies, namely, any strategy \({\varvec{p}}\in \varPi _{\text {GCS}}\) such that:
$$\begin{aligned} \sum _{i=1}^n \gamma _i/(p_i\beta _i)\le C_I. \end{aligned}$$(34) -
(b)
if
$$\begin{aligned} \sum _{i=1}^n \sqrt{\gamma _i/\beta _i}> \sqrt{{\overline{p}}C_I} \end{aligned}$$(35)then q and \({\varvec{p}}\) are uniquely defined as follows:
$$\begin{aligned} p_i= & {} P_i(\omega )=\frac{\sqrt{\left( {\overline{p}}\omega / C_I\right) ^2+4{\overline{p}}\beta _i/(\gamma _iC_I)}-{\overline{p}}\omega / C_I}{2\beta _i/\gamma _i} \text{ for } i=1,\ldots ,n,\end{aligned}$$(36)$$\begin{aligned} q= & {} \omega {\overline{p}}/C_I, \end{aligned}$$(37)where \(\omega \) is the unique positive root of the equation: \(\sum \limits _{i=1}^nP_i(\omega ) ={\overline{p}}.\)
Proof
Since \(\delta _i=0\) for all i, if \(q = 0\) then \({\varvec{p}}\) is any feasible strategy such that \(\sum _{i=1}^n \gamma _i/(\beta _ip_i)\le C_I.\) Such an equilibrium strategy exists if and only if
It is clear that left-side of (38) is a convex NLP problem, and straightforward applying the KKT theorem implies that its solution is
Substituting this strategy into (38) implies (33), and (a) follows. While, if \(q>0\) then by (21) and (33) we have that \(\sum _{i=1}^n \omega p_i/q=C_I.\) This and the fact that \({\varvec{p}}\in \varPi _{\text {GCS}}\) implies (37). Substituting (37) implies that \({\varvec{p}}\) is given by (36). Note that \(\varphi (\omega )=\sum _{i=1}^nP_i(\omega )\) decreases with \(\omega \) and tends to zero for \(\omega \uparrow \infty \). Then, equation \(\varphi (\omega )={\overline{p}}\) has the positive root if and only if \(\varphi (0)>{\overline{p}}\), and this condition is equivalent to (35). \(\blacksquare \)
Figure 1(a) illustrates a decrease in applied jamming power with an increase in jamming power cost and the total transmission power. Figure 1(b) illustrates that for \({\bar{p}}\) the GCS tends to serve the UAV uniformly. While an increase in \({\bar{p}}\) allows the GCS to serve in more individual form according to non-uniform power allocation (32). This makes the problem remarkably distinguish from OFDM transmission where uniform strategy arise for large total power resource [8]. This is caused by the fact that OFDM utility can be approximated by a superposition of logarithm and linear function of transmission power for large applied power while proportional fairness utility of the considered game can be approximated similar way for small applied power.
4 Conclusions
The problem to maintain freshness of the commands received by a group of UAVs to succeed a mission under hostile interference was modeled as non-zero game. Proportional fairness in mission success by each of the UAVs is considered as criteria for the GCS. The problem is formulated and solved as non-zero some game The considered game differs remarkably from the conventional jamming games considered in literature [16, 20, 24] because the structure of the rivals’ strategies differ from from each other. In particular, the GCS’s strategy is power allocation between the UAVs, while the interferer’s strategy is a common power level assignment to jam the whole UAV’s group. Moreover, in OFDM jamming game with throughput as transmitter’s payoff [8], transmitter’s equilibrium strategy is uniform power allocation for large total transmitting power, while, in the considered game, GCS’s equilibrium strategy is uniform power allocation for small total transmitting power.
References
Arafa, A., Yang, J., Ulukus, S., Poor, H.V.: Age-minimal online policies for energy harvesting sensors with incremental battery recharges. In: Information Theory and Applications Workshop (ITA), pp. 1–10 (2018)
Baston, V., Garnaev, A.: A search game with a protector. Naval Res. Logist. 47, 85–96 (2000)
Costa, M., Codreanu, M., Ephremides, A.: On the age of information in status update systems with packet management. IEEE Trans. Inf. Theory 62, 1897–1910 (2016)
Fudenberg, D., Tirole, J.: Game Theory. MIT Press, Boston (1991)
Garnaev, A., Baykal-Gursoy, M., Poor, H.V.: Security games with unknown adversarial strategies. IEEE Trans. Cybern. 46, 2291–2299 (2016)
Garnaev, A., Trappe, W.: Bargaining over the fair trade-off between secrecy and throughput in OFDM communications. IEEE Trans. Inf. Forensics Secur. 12, 242–251 (2017)
Garnaev, A., Trappe, W.: The rival might be not smart: revising a CDMA jamming game. In: IEEE Wireless Communications and Networking Conference (WCNC) (2018)
Garnaev, A., Trappe, W., Petropulu, A.: Equilibrium strategies for an OFDM network that might be under a jamming attack. In: 51st Annual Conference on Information Sciences and Systems (CISS), pp. 1–6 (2017)
Hausken, K.: Information sharing among firms and cyber attacks. J. Account. Public Policy 26, 639–688 (2007)
Huang, L., Modiano, E.: Optimizing age-of-information in a multi-class queueing system. In: IEEE International Symposium on Information Theory (ISIT), pp. 1681–1685 (2015)
Jia, H.: A stochastic derivation of the ratio form of contest success functions. Public Choice 135, 125–130 (2008)
Jia, L., Yao, F., Sun, Y., Niu, Y., Zhu, Y.: Bayesian Stackelberg game for anatijamming transmission with incomplete information. IEEE Commun. Lett. 20, 1991–1994 (2016)
Kam, C., Kompella, S., Nguyen, G., Wieselthier, J., Ephremides, A.: Information freshness and popularity in mobile caching. In: IEEE International Symposium on Information Theory (ISIT) (2018)
Kaul, S., Yates, R., Gruteser, M.: Real-time status: how often should one update? In: Proceedings of the IEEE INFOCOM, pp. 2731–2735 (2012)
Kaul, S., Yates, R., Gruteser, M.: Status updates through queues. In: Conference on Information Sciences and Systems (CISS), March 2012
Li, T., Song, T., Liang, Y.: Multiband transmission under jamming: a game theoretic perspective. In: Li, T., Song, T., Liang, Y. (eds.) Wireless Communications under Hostile Jamming: Security and Efficiency, pp. 155–187. Springer, Singapore (2018). https://doi.org/10.1007/978-981-13-0821-5_6
Nguyen, G., Kompella, S., Kam, C., Wieselthier, J., Ephremides, A.: Impact of hostile interference on information freshness: a game approach. In: 15th International Symposium on Modeling and Optimization in Mobile, Ad Hoc, and Wireless Networks (WiOpt) (2017)
Shi, H., Prasad, R.V., Onur, E., Niemegeers, I.G.M.M.: Fairness in wireless networks: issues, measures and challenges. IEEE Commun. Surv. Tutor. 16, 5–24 (2014)
Skaperdas, S.: Contest success functions. Econ. Theor. 7, 283–290 (1996)
Song, T., Stark, W.E., Li, T., Tugnait, J.K.: Optimal multiband transmission under hostile jamming. IEEE Trans. Commun. 64, 4013–4027 (2016)
Tullock, G.: Efficient rent seeking. In: Buchanan, J., Tollison, R., Tullock, G. (eds.) Toward a Theory of Rent-Seeking Society, pp. 97–112. Texas A&M University Press (2001)
Xiao, L., Chen, T., Liu, J., Dai, H.: Anti-jamming transmission Stackelberg game with observation errors. IEEE Commun. Lett. 19, 949–952 (2015)
Xiao, Y., Sun, Y.: A dynamic jamming game for real-time status updates. In: IEEE INFOCOM, Age of Information Workshop (2018)
Yang, D., Xue, G., Zhang, J., Richa, A., Fang, X.: Coping with a smart jammer in wireless networks: a Stackelberg game approach. IEEE Trans. Wirel. Commun. 12, 4038–4047 (2013)
Yates, R.D., Ciblat, P., Yener, A., Wigger, M.: Age-optimal constrained cache updating. In: IEEE International Symposium on Information Theory (ISIT) (2017)
Yates, R.D., Najm, E., Soljanin, E., Zhong, J.: Timely updates over an erasure channel. In: IEEE International Symposium on Information Theory (ISIT) (2017)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2019 IFIP International Federation for Information Processing
About this paper
Cite this paper
Garnaev, A., Zhong, J., Zhang, W., Yates, R.D., Trappe, W. (2019). Proportional Fair Information Freshness Under Jamming. In: Di Felice, M., Natalizio, E., Bruno, R., Kassler, A. (eds) Wired/Wireless Internet Communications. WWIC 2019. Lecture Notes in Computer Science(), vol 11618. Springer, Cham. https://doi.org/10.1007/978-3-030-30523-9_8
Download citation
DOI: https://doi.org/10.1007/978-3-030-30523-9_8
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-30522-2
Online ISBN: 978-3-030-30523-9
eBook Packages: Computer ScienceComputer Science (R0)