Abstract
The lattice model proposed by Denning in her seminal work provided secure information flow analyses with an intuitive and uniform mathematical foundation. Different organisations, however, may employ quite different security lattices. In this paper, we propose a connection framework that permits different organisations to exchange information while maintaining both security of information flow as well as their autonomy in formulating and maintaining security policies. Our prescriptive framework is based on the rigorous mathematical framework of Lagois connections given by Melton, together with a simple operational model for transferring object data between domains. The merit of this formulation is that it is simple, minimal, adaptable and intuitive, and provides a formal framework for establishing secure information flow across autonomous interacting organisations. We show that our framework is semantically sound, by proving that the connections proposed preserve standard correctness notions such as non-interference.
Supported by Indo-Japanese project Security in the IoT Space, DST, Govt of India.
You have full access to this open access chapter, Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
Denning’s seminal work [7] proposed complete latticesFootnote 1 as the appropriate mathematical framework for questions regarding secure information flow (SIF), i.e., only authorised flows of information are possible. An information flow model (IFM) is characterised as \(\langle N, P, SC, \sqcup , \sqsubseteq \rangle \) where: Storage objects in N are assigned security classes drawn from a (finite) complete lattice SC. P is a set of processes (also assigned security classes as clearances). The partial ordering \(\sqsubseteq \) represents permitted flows between classes; reflexivity and transitivity capture intuitive aspects of information flow; antisymmetry helps avoid redundancies in the framework, and the join operation \(\sqcup \) succinctly captures the combination of information belonging to different security classes in arithmetic, logical and computational operations. This lattice model provides an abstract uniform framework that identifies the commonalities of the variety of analyses for different applications – e.g., confidentiality and trust – whether at the language level or at a system level. In the ensuing decades, the vast body of secure information flow analyses has been built on these mathematical foundations, with the development of a plethora of static and dynamic analysis techniques for programming languages [13, 15, 17, 19,20,21], operating systems [2, 8, 12, 20, 25], databases [22], and hardware architectures [9, 27], etc.
The soundness of this lattice model was expressed in terms of semantic notions of system behaviour, for instance, as properties like non-interference [10] by Volpano et al. [23] and others. Alternative semantic notions of security such as safety properties have been proposed as well, e.g., [1], but for brevity we will not explore these further.
The objective of this paper is to propose a simple way in which large-scale distributed secure systems can be built by connecting component systems in a secure and modular manner. Our work begins with the observation that large information systems are not monolithic: Different organisations define their own information flow policies independently, and subsequently collaborate or federate with one another to exchange information. In general, the security classes and the lattices of any two organisations may be quite different—there is no single universal security class lattice. Moreover, modularity and autonomy are important requirements since each organisation would naturally wish to retain control over its own security policies and the ability to redefine them. Therefore, fusing different lattices by taking their union is an unsatisfactory approach, more so since the security properties of application programs would have to be re-established in this possibly enormous lattice.
When sharing information, most organisations limit the cross-domain communications to a limited set of security classes (which we call transfer classes). In order to ensure that shared data are not improperly divulged, two organisations usually negotiate agreements or memorandums of understanding (MoUs), promising that they will respect the security policies of the other organisation. We argue that a good notion of secure connection should require reasoning only about those flows from just the transfer classes mentioned in a MoU. Usually, cross-domain communication involves downgrading the security class of privileged information to public information using primitives such as encryption, and then upgrading the information to a suitable security class in the other domain. Such approaches, however, do not gel well with correctness notions such as non-interference. Indeed the question of how to translate information between security classes of different lattices is interesting [6].
Contributions of This Paper. In this paper, we propose a simple framework and sufficient conditions under which secure flow guarantees can be enforced without exposing the complexities and details of the component information flow models. The framework consists of (1) a way to connect security classes of one organisation to those in another while satisfying intuitive requirements; (2) a simple language that extends the operations within an organisation with primitives for transferring data between organisations; and (3) a type system and operational model for these constructs, which we use to establish that the framework conserves security.
In Sect. 2, we first identify, using intuitive examples, violations in secure flow that may arise when two secure systems are permitted to exchange information in both directions. Based on these lacunae, we formulate security and precision requirements for secure bidirectional flow. We then propose a framework that guarantees the absence of such policy violations, without impinging on the autonomy of the individual systems, without the need for re-verifying the security of the application procedures in either of the domains, and confining the analysis to only the transfer classes involved in potential exchange of data. Our approach is based on monotone functions and an elegant theory of connections [16] between the security lattices. Theorem 1 shows that Lagois connections between the security lattices satisfy the security and precision requirements.
We present in Sect. 3 a minimal operational language consisting of a small set of atomic primitives for effecting the transfer of data between domains. The framework is simple and can be adapted for establishing secure connections between distributed systems at any level of abstraction (language, system, database, ...). We assume each domain uses atomic transactional operations for object manipulation and intra-domain computation. The primitives of our model include reliable communication between two systems, transferring object data in designated output variables of one domain to designated input variables of a specified security class in the other domain. We also assume a generic set of operations in each domain for copying data from input variables to domain objects, and from domain objects to output variables. To avoid interference between inter-domain communication and the computations within the domains, we assume that the sets of designated input and output variables are all mutually exclusive of one another, and also with the program/system variables used in the computations within each domain. Thus by design we avoid the usual suspects that cause interference and insecure transfer of data. The operational description of the language consists of the primitives together with their execution rules (Sect. 3.1).
The correctness of our framework is demonstrated by expressing soundness (with respect to the operational semantics) of a type system (Sect. 3.2), stated in terms of the security lattices and their connecting functions. In particular, Theorem 7 shows the standard semantic property of non-interference in both domains holds of all operational behaviours. We adapt and extend the approach taken by Volpano et al. [23] to encompass systems coupled using the Lagois connection conditions, and (assuming atomicity of the data transfer operations) show that security is conserved. Since our language is a minimal imperative model with atomic transactions, reads and writes as the basic elements, we are able to work with a simplified version of the type system of Volpano et al.. In particular, our language does not include conditional constructs in the transfer of data between domains, and assumes all conditional computation is absorbed within atomic intradomain transactions. Thus, we do not have to concern ourselves with issues of implicit flows that arise due to branching structures (e.g., conditionals and loops in programming language level security, pipeline mispredictions at the architectural level, etc.) While non-interference is the property addressed in this paper, we believe that our formulation is general enough to be applicable to other behavioural notions of secure information flow as a safety property [1].
In Sect. 4, we briefly review some related work. We conclude in Sect. 5 with a discussion on our approach and directions for future work.
2 Lagois Connections and All that
Motivating Examples. Consider a university system in which students study in semi-autonomously administered colleges (one such is  ) that are affiliated to a university (
) that are affiliated to a university ( ). The university also has “university professors” with whom students can take classes. We assume each institution has established the security of its information flow mechanisms and policies.
). The university also has “university professors” with whom students can take classes. We assume each institution has established the security of its information flow mechanisms and policies.
We first observe that formulating an agreement between the institutions which respects the flow policies within each institution is not entirely trivial. Consider an arrangement where the College Faculty and University Faculty can share information (say, course material and examinations), and the Dean of Colleges in the University can exchange information (e.g., students’ official grade-sheets) with the college’s Dean of Students. Even such an apparently reasonable arrangement suffers from insecurities, as illustrated in Fig. 1 by the flow depicted using dashed red arrows, where information can flow from the college’s Faculty to the college’s Dean of Students. (Moral: internal structure of the lattices matters.)
As long as information flows unidirectionally from colleges to the University, monotone functions from the security classes of the college lattice  to those in the university security lattice
to those in the university security lattice  suffice to ensure secure information flow. A function
suffice to ensure secure information flow. A function  is called monotone if whenever
is called monotone if whenever  in
in  then
then  in
in  .Footnote 2 Monotonicity also constrains possible flows between classes of the two domains, once certain important flows between certain classes have been identified (see Fig. 2). Moreover, since monotone functions are closed under composition, one can chain them to create secure unidirectional information flow connections through a series of administrative domains. Monotonicity is a basic principle adopted for information flow analyses, e.g. [13].
.Footnote 2 Monotonicity also constrains possible flows between classes of the two domains, once certain important flows between certain classes have been identified (see Fig. 2). Moreover, since monotone functions are closed under composition, one can chain them to create secure unidirectional information flow connections through a series of administrative domains. Monotonicity is a basic principle adopted for information flow analyses, e.g. [13].
However, when there is “blowback” of information, mere monotonicity is inadequate for ensuring SIF. Consider the bidirectional flow situation in Fig. 3, where data return to the original domain. Monotonicity of both functions  and
and  does not suffice for security because the composition
does not suffice for security because the composition  may not be non-decreasing. In Fig. 3, both
may not be non-decreasing. In Fig. 3, both  and
and  are monotone but their composition can lead to information leaking from a higher class, e.g., College Principal, to a lower class, e.g., Faculty within
are monotone but their composition can lead to information leaking from a higher class, e.g., College Principal, to a lower class, e.g., Faculty within  —an outright violation of the college’s security policy. Similarly, composition
—an outright violation of the college’s security policy. Similarly, composition  may lead to violation of the University’s security policy.
may lead to violation of the University’s security policy.
Requirements. We want to ensure that any “round-trip” flow of information, e.g., from a domain  to
to  and back to
and back to  , is a permitted flow in the lattice
, is a permitted flow in the lattice  , from where the data originated. Thus we require the following (tersely stated) “security conditions” SC1 and SC2 on
, from where the data originated. Thus we require the following (tersely stated) “security conditions” SC1 and SC2 on  and
and  , which preclude any violation of the security policies of both the administrative domains (see Fig. 5):
, which preclude any violation of the security policies of both the administrative domains (see Fig. 5):

In other words, the data can flow only in accordance with the flows permitted by the ordering relations of the two lattices.
We also desire precision, based on a principle of least privilege escalation—if data are exchanged between the two domains without any computation done on them, then the security level should not be needlessly raised. Precision is important for meaningful and useful analyses; otherwise data would be escalated to security classes which permit very restricted access.

Further, if the data were to go back and forth between two domains more than once, the security classes to which data belong should not become increasingly restrictive after consecutive bidirectional data sharing (See Fig. 4, which shows monotone functions that keep climbing up to the top). This convergence requirement may be stated informally as conditions CC1 and CC2, requiring fixed points for the compositions  and
and  . Since security lattices are finite, CC1 and CC2 necessarily hold – such fixed points exist, though perhaps only at the topmost elements of the lattice. We would therefore desire a stronger requirement, where fixed points are reached as low in the orderings as possible.
. Since security lattices are finite, CC1 and CC2 necessarily hold – such fixed points exist, though perhaps only at the topmost elements of the lattice. We would therefore desire a stronger requirement, where fixed points are reached as low in the orderings as possible.
Galois Connections Aren’t the Answer. Any discussion on a pair of partial orders linked by a pair of monotone functions suggests the notion of a Galois connection, an elegant and ubiquitous mathematical structure that finds use in computing, particularly in static analyses. However, Galois connections are not the appropriate structure for bidirectional informational flow control.
Let  and
and  be two complete security class lattices, and
be two complete security class lattices, and  and
and  be two monotone functions such that
be two monotone functions such that  forms a Galois connection. Recall that a Galois connection satisfies the condition
forms a Galois connection. Recall that a Galois connection satisfies the condition

So in a Galois connection we have  . Since
. Since  holds trivially, we get
holds trivially, we get  . If
. If  then
then  (strictly), which would violate secure flow requirement SC2. Figure 6 illustrates such a situation.
(strictly), which would violate secure flow requirement SC2. Figure 6 illustrates such a situation.
Why Not Galois Insertions? Now suppose  and
and  are two complete security class lattices, and
are two complete security class lattices, and  and
and  be two monotone functions such that
be two monotone functions such that  forms a Galois insertion, i.e., a Galois connection where \(\alpha \) is surjective:
forms a Galois insertion, i.e., a Galois connection where \(\alpha \) is surjective:

Then the flow of information permitted by  and
and  is guaranteed to be secure. However, Galois insertions mandate conditions on the definitions of functions
is guaranteed to be secure. However, Galois insertions mandate conditions on the definitions of functions  and
and  that are much too strong, i.e.,
that are much too strong, i.e.,
-
 is injective, i.e.,
is injective, i.e., 
-
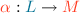 is surjective, i.e.,
is surjective, i.e.,  .
.
Typically data are shared only from a few security classes of any organisation. Organisations rarely make public their entire security class structure and permitted flow policies. Organisations also typically do not want any external influences on some subsets of its security classes. Thus, if not all elements of  are transfer classes, it may be impossible to define a Galois insertion
are transfer classes, it may be impossible to define a Galois insertion  because we cannot force
because we cannot force  to be surjective.
to be surjective.
Lagois Connections. Further, the connection we seek to make between two domains should allow us to transpose them. Fortunately there is an elegant structure, i.e., Lagois Connections [16], which exactly satisfies this as well as the requirements of security and bidirectional sharing (SC1, SC2, PC1, PC2, CC1 and CC2). They also conveniently generalise Galois insertions.
Definition 1
(Lagois Connection [16]). If  and
and  are two partially ordered sets, and
are two partially ordered sets, and  and
and  are order-preserving functions, then we call the quadruple
are order-preserving functions, then we call the quadruple  an increasing Lagois connection, if it satisfies the following properties:
an increasing Lagois connection, if it satisfies the following properties:

LC3 ensures that  is the least upper bound of all security classes in
is the least upper bound of all security classes in  that are mapped to the same security class, say
that are mapped to the same security class, say  in
in  .
.
The main result of this section is that if the negotiated monotone functions  and
and  form a Lagois connection between the security lattices
form a Lagois connection between the security lattices  and
and  , then information flows permitted are secure and precise.
, then information flows permitted are secure and precise.
Theorem 1
Let  and
and  be two complete security class lattices,
be two complete security class lattices,  and
and  be two monotone functions. Then the flow of information permitted by
be two monotone functions. Then the flow of information permitted by  ,
,  satisfies conditions SC1, SC2, PC1, PC2, CC1 and CC2 if
satisfies conditions SC1, SC2, PC1, PC2, CC1 and CC2 if  is an increasing Lagois connection.
is an increasing Lagois connection.
Proof
Condition SC1 holds because if  , by monotonicity of
, by monotonicity of  ,
,  . But by LC1,
. But by LC1,  . So
. So  . (A symmetric argument holds for SC2.) Conditions PC1 and PC2 are shown in Proposition 3.7 of [16]. Conditions CC1 and CC2 hold since the compositions
. (A symmetric argument holds for SC2.) Conditions PC1 and PC2 are shown in Proposition 3.7 of [16]. Conditions CC1 and CC2 hold since the compositions  and
and  are closure operators, i.e., idempotent, extensive, order-preserving endo-functions on
are closure operators, i.e., idempotent, extensive, order-preserving endo-functions on  and
and  .
.
In fact, Lagois connections (e.g. Fig. 7) ensure that information in a security class in the original domain remains accessible even after doing a round-trip from the other domain (Proposition 3.8 in [16]):


Properties of Lagois Connections. We list some properties of Lagois connections that assist in the construction of a secure connection, and in identifying those security classes that play an important role in the connection. Proposition 2 says that the two functions  and
and  uniquely determine each other.
uniquely determine each other.
Proposition 2
(Proposition 3.9 in [16]). If  is a Lagois connection, then the functions
is a Lagois connection, then the functions  and
and  uniquely determine each other; in fact
uniquely determine each other; in fact


Proposition 3 shows the existence of dominating members in their pre-images, which act as equivalence-class representatives of the equivalence relations  and
and  induced by the functions
induced by the functions  and
and  .
.
Proposition 3
(Proposition 3.7 in [16]). Let  be a Lagois connection and let
be a Lagois connection and let  and
and  . Then
. Then  has a largest member, which is
has a largest member, which is  , and
, and  has a largest member, which is
has a largest member, which is  .
.
That is, for all  and
and  ,
,  and
and  exist. Also, the images
exist. Also, the images  and
and  are isomorphic lattices.
are isomorphic lattices.  and
and  define a system of representatives for
define a system of representatives for  and
and  . Element
. Element  in
in  , called a budpoint, acts as the representative of the equivalence class
, called a budpoint, acts as the representative of the equivalence class  in the following sense:
in the following sense:

Symmetrically,  defines a system of representatives for
defines a system of representatives for  . These budpoints play a significant role in delineating the connection between the transfer classes in the two lattices.
. These budpoints play a significant role in delineating the connection between the transfer classes in the two lattices.
Further, Proposition 4 shows that these budpoints are closed under meets. This property enables us to confine our analysis to just these classes when reasoning about bidirectional flows.
Proposition 4
(Proposition 3.11 in [16]). If  is a Lagois connection and
is a Lagois connection and  , then
, then
-
1.
the meet of
 in
in 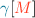 exists if and only if the meet of
exists if and only if the meet of  in
in 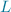 exists, and whenever either exists, they are equal.
exists, and whenever either exists, they are equal. -
2.
the join
 of
of  in
in  exists if the join
exists if the join  of
of  in
in  exists, and in this case
exists, and in this case 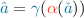
3 An Operational Model
3.1 Computational Model
Let us consider two different organisations  and
and  that want to share data with each other. We start with the assumptions that the two domains comprise storage objects
that want to share data with each other. We start with the assumptions that the two domains comprise storage objects  and
and  respectively, which are manipulated using their own sets of atomic transactional operations, ranged over by
respectively, which are manipulated using their own sets of atomic transactional operations, ranged over by  and
and  respectively. We further assume that these transactions within each domain are internally secure with respect to their flow models, and have no insecure or interfering interactions with the environment. Thus, we are agnostic to the level of abstraction of the systems we aim to connect securely, and since our approach treats the application domains as “black boxes”, it is readily adaptable to any level of discourse (language, system, OS, database) found in the security literature.
respectively. We further assume that these transactions within each domain are internally secure with respect to their flow models, and have no insecure or interfering interactions with the environment. Thus, we are agnostic to the level of abstraction of the systems we aim to connect securely, and since our approach treats the application domains as “black boxes”, it is readily adaptable to any level of discourse (language, system, OS, database) found in the security literature.
We extend these operations with a minimal set of operations to transfer data between the two domains. To avoid any concurrency effects, interference or race conditions arising from inter-domain transfer, we augment the storage objects of both domains with a fresh set of export and import variables into/from which the data of the domain objects can be copied atomically. We designate these sets  as the respective export variables, and
as the respective export variables, and  as the respective import variables, with the corresponding variable instances written as
as the respective import variables, with the corresponding variable instances written as  ,
,  and
and  ,
,  . These export and import variables form mutually disjoint sets, and are distinct from any extant domain objects manipulated by the applications within a domain. These variables are used exclusively for transfer, and are manipulated atomically. We let
. These export and import variables form mutually disjoint sets, and are distinct from any extant domain objects manipulated by the applications within a domain. These variables are used exclusively for transfer, and are manipulated atomically. We let  range over all variables in
range over all variables in  (respectively
(respectively  over
over  ). Domain objects are copied to export variables and from import variables by special operations
). Domain objects are copied to export variables and from import variables by special operations  and
and  (and
(and  and
and  in the other domain). We assume atomic transfer operations (trusted by both domains) \(T_{RL}, T_{LR}\) that copy data from the export variables of one domain to the import variables of the other domain as the only mechanism for inter-domain flow of data. Let “phrase” p denote a command in either domain or a transfer operation, and let s be any (empty or non-empty) sequence of phrases.
in the other domain). We assume atomic transfer operations (trusted by both domains) \(T_{RL}, T_{LR}\) that copy data from the export variables of one domain to the import variables of the other domain as the only mechanism for inter-domain flow of data. Let “phrase” p denote a command in either domain or a transfer operation, and let s be any (empty or non-empty) sequence of phrases.

A store (typically  ) is a finite-domain function from variables to a set of values (not further specified). We write, e.g.,
) is a finite-domain function from variables to a set of values (not further specified). We write, e.g.,  for the contents of the store
for the contents of the store  at variable
at variable  , and
, and  for the store that is the same as
for the store that is the same as  everywhere except at variable
everywhere except at variable  , where it now takes value
, where it now takes value  .
.
The rules specifying execution of commands are given in Fig. 8. Assuming the specification of intradomain transactions ( ) of the form
) of the form  and
and  , our rules allow us to specify judgments of the form
, our rules allow us to specify judgments of the form  for phrases, and the reflexive-transitive closure for sequences of phrases. Note that phrase execution occurs atomically, and the intra-domain transactions, as well as copying to and from the export/import variables affect the store in only one domain, whereas the atomic transfer is only between export variables of one domain and the import variables of the other.
for phrases, and the reflexive-transitive closure for sequences of phrases. Note that phrase execution occurs atomically, and the intra-domain transactions, as well as copying to and from the export/import variables affect the store in only one domain, whereas the atomic transfer is only between export variables of one domain and the import variables of the other.
3.2 Typing Rules
Let the two domains have the respective different IFMs:

such that the flow policies in both are defined over different sets of security classes  and
and  .Footnote 3
.Footnote 3
The (security) types of the core language are as follows. Metavariables  and
and  range over the sets of security classes,
range over the sets of security classes,  and
and  respectively, which are partially ordered by
respectively, which are partially ordered by  and
and  . A type assignment
. A type assignment  is a finite-domain function from variables
is a finite-domain function from variables  to
to  (respectively,
(respectively,  from
from  to
to  ). The important restriction we place on
). The important restriction we place on  and
and  is that they map export and import variables
is that they map export and import variables  only to points in the security lattices
only to points in the security lattices  and
and  respectively which are in the domains of
respectively which are in the domains of  and
and  , i.e., these points participate in the Lagois connection. Intuitively, a variable w mapped to security class
, i.e., these points participate in the Lagois connection. Intuitively, a variable w mapped to security class  can store information of security class
can store information of security class  or lower. The type system works with respect to a given type assignment. Given a security level, e.g.,
or lower. The type system works with respect to a given type assignment. Given a security level, e.g.,  , the typing rules track for each command within that domain whether all written-to variables in that domain are of security classes “above”
, the typing rules track for each command within that domain whether all written-to variables in that domain are of security classes “above”  , and additionally for transactions within a domain, they ensure “simple security”, i.e., that all variables which may have been read belong to security classes “below”
, and additionally for transactions within a domain, they ensure “simple security”, i.e., that all variables which may have been read belong to security classes “below”  . We assume for the transactions within a domain, e.g.,
. We assume for the transactions within a domain, e.g.,  , we have a type system that will give us judgments of the form
, we have a type system that will give us judgments of the form  . The novelty of our approach is to extend this framework to work over two connected domains, i.e., given implicit security levels of the contexts in the respective domains. Cross-domain transfers will require pairing such judgments, and thus our type system will have judgments of the form
. The novelty of our approach is to extend this framework to work over two connected domains, i.e., given implicit security levels of the contexts in the respective domains. Cross-domain transfers will require pairing such judgments, and thus our type system will have judgments of the form

We introduce a set of typing rules for the core language, given in Fig. 9. In many of the rules, the type for one of the domains is not constrained by the rule, and so any suitable type may be chosen as determined by the context, e.g.,  in the rules
in the rules  ,
,  ,
,  and
and  , and both
, and both  and
and  in Com0.
in Com0.
For transactions e.g.,  entirely within domain
entirely within domain  , the typing rule
, the typing rule  constrains the type in the left domain to be at a level
constrains the type in the left domain to be at a level  that dominates all variables read in
that dominates all variables read in  , and which is dominated by all variables written to in
, and which is dominated by all variables written to in  , but places no constraints on the type
, but places no constraints on the type  in the other domain
in the other domain  . In the rule
. In the rule  , since a value in import variable
, since a value in import variable  is copied to the variable
is copied to the variable  , we have
, we have  , and the type in the domain
, and the type in the domain  is
is  with no constraint on the type
with no constraint on the type  in the other domain. Conversely, in the rule
in the other domain. Conversely, in the rule  , since a value in variable
, since a value in variable  is copied to the export variable
is copied to the export variable  , we have
, we have  , and the type in the domain
, and the type in the domain  is
is  with no constraint on the type
with no constraint on the type  in the other domain. In the rule
in the other domain. In the rule  , since the contents of a variable
, since the contents of a variable  in domain
in domain  are copied into a variable
are copied into a variable  in domain
in domain  , we require
, we require  , and constrain the type in domain
, and constrain the type in domain  to
to  . The constraint in the other domain is unimportant (but for the sake of convenience, we peg it at
. The constraint in the other domain is unimportant (but for the sake of convenience, we peg it at  ). Finally, for the types of sequences of phrases, we take the meets of the collected types in each domain respectively, so that we can guarantee that no variable of type lower than these meets has been written into during the sequence. Note that Proposition 4 ensures that these types have the desired properties for participating in the Lagois connection.
). Finally, for the types of sequences of phrases, we take the meets of the collected types in each domain respectively, so that we can guarantee that no variable of type lower than these meets has been written into during the sequence. Note that Proposition 4 ensures that these types have the desired properties for participating in the Lagois connection.
3.3 Soundness
We now establish soundness of our scheme by showing a non-interference theorem with respect to operational semantics and the type system built on the security lattices. This theorem may be viewed as a conservative adaptation (to a minimal secure data transfer framework in a Lagois-connected pair of domains) of the main result of Volpano et al. [23].
We assume that underlying base transactional languages in each of the domains have the following simple property (stated for  , but an analogous property is assumed for
, but an analogous property is assumed for  ). Within each transaction
). Within each transaction  , for each assignment of an expression
, for each assignment of an expression  to any variable
to any variable  , the following holds: If
, the following holds: If  ,
,  are two stores such that for all
are two stores such that for all  , we have
, we have  , then after executing the assignment, we will get
, then after executing the assignment, we will get  . That is, if two stores are equal for all variables appearing in the expression
. That is, if two stores are equal for all variables appearing in the expression  , then the value assigned to the variable
, then the value assigned to the variable  will be the same. This assumption plays the rôle of “Simple Security” of expressions in [23] in the proof of the main theorem. The type system plays the rôle of “Confinement”. We start with two obvious lemmas about the operational semantics, namely preservation of domains, and a “frame” lemma:
will be the same. This assumption plays the rôle of “Simple Security” of expressions in [23] in the proof of the main theorem. The type system plays the rôle of “Confinement”. We start with two obvious lemmas about the operational semantics, namely preservation of domains, and a “frame” lemma:
Lemma 5
(Domain preservation). If  , then
, then  , and
, and  .
.
Proof
By induction on the length of the derivation of  .
.
Lemma 6
(Frame). If  , and w is not assigned to in s, then
, and w is not assigned to in s, then  and
and  .
.
Proof
By induction on the length of the derivation of  .
.
The main result of the paper assumes an “adversary” that operates at a security level  in domain
in domain  and at security level
and at security level  in domain
in domain  . Note however, that these two levels are interconnected by the monotone functions
. Note however, that these two levels are interconnected by the monotone functions  and
and  , since these levels are connected by the ability of information at one level in one domain to flow to the other level in the other domain. The following theorem says that if (a) a sequence of phrases is well-typed, and (b, c) we start its execution in two store configurations that are (e) indistinguishable with respect to all objects having security class below
, since these levels are connected by the ability of information at one level in one domain to flow to the other level in the other domain. The following theorem says that if (a) a sequence of phrases is well-typed, and (b, c) we start its execution in two store configurations that are (e) indistinguishable with respect to all objects having security class below  and
and  in the respective domains, then the corresponding resulting stores after execution continue to remain indistinguishable on all variables with security classes below these adversarial levels.
in the respective domains, then the corresponding resulting stores after execution continue to remain indistinguishable on all variables with security classes below these adversarial levels.
Theorem 7
(Type Soundness). Suppose  are the “adversarial” type levels in the respective domains, which satisfy the condition
are the “adversarial” type levels in the respective domains, which satisfy the condition  and
and  . Let
. Let
-
(a)
 ; (s has security type
; (s has security type  )
) -
(b)
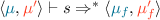 ; (execution of s starting from
; (execution of s starting from 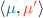 )
) -
(c)
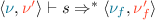 ; (execution of s starting from
; (execution of s starting from  )
) -
(d)
 and
and  ;
; -
(e)
 for all
for all 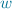 such that
such that 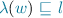 , and
, and  for all
for all  such that
such that  .
.
Then  for all
for all  such that
such that  , and
, and  for all
for all  such that
such that  .
.
Proof
By induction on the length of sequence s. The base case is vacuously true. We now consider a sequence \(s_1; p\).  and
and  and
and  and
and  By induction hypothesis applied to \(s_1\), we have
By induction hypothesis applied to \(s_1\), we have  for all
for all  such that
such that  , and
, and  for all
for all  such that
such that  .
.
Let  , and
, and  . We examine four cases for p (the remaining cases are symmetrical).
. We examine four cases for p (the remaining cases are symmetrical).
Case p is  : Consider any
: Consider any  such that
such that  . If
. If  (i.e., it doesn’t appear in
(i.e., it doesn’t appear in  ), or if
), or if  but is not assigned to in
but is not assigned to in  , then by Lemma 6 and the induction hypothesis,
, then by Lemma 6 and the induction hypothesis,  .
.
Now suppose  is assigned to in
is assigned to in  . From the condition
. From the condition  , we know that for all
, we know that for all  assigned in
assigned in  ,
,  and for all
and for all  read in
read in  ,
,  . Now if
. Now if  , then since in
, then since in  no variables
no variables  such that
such that  are assigned to. Therefore by Lemma 6,
are assigned to. Therefore by Lemma 6,  , for all
, for all  such that
such that  .
.
If  , then for all
, then for all  read in
read in  ,
,  . Therefore, by assumption on transaction
. Therefore, by assumption on transaction  , if any variable
, if any variable  is assigned an expression
is assigned an expression  , since
, since  ,
,  are two stores such that for all
are two stores such that for all  ,
,  , the value of
, the value of  will be the same. By this simple security argument, after the transaction
will be the same. By this simple security argument, after the transaction  , we have
, we have  . Since the transaction happened entirely and atomically in domain
. Since the transaction happened entirely and atomically in domain  , we do not have to worry ourselves with changes in the other domain
, we do not have to worry ourselves with changes in the other domain  , and do not need to concern ourselves with the adversarial level
, and do not need to concern ourselves with the adversarial level  .
.
Case p is  : Thus
: Thus  , which means
, which means  . If
. If  , there is nothing to prove (Lemma 6, again). If
, there is nothing to prove (Lemma 6, again). If  , then since by I.H.,
, then since by I.H.,  , we have
, we have  .
.
Case p is  : Thus
: Thus  , which means
, which means  . If
. If  , there is nothing to prove (Lemma 6, again). If
, there is nothing to prove (Lemma 6, again). If  , then since by I.H.,
, then since by I.H.,  , we have
, we have  .
.
Case p is  : So
: So  , and
, and  . If
. If  , there is nothing to prove (Lemma 6, again). If
, there is nothing to prove (Lemma 6, again). If  , then by transitivity,
, then by transitivity,  . By monotonicity of
. By monotonicity of  :
:  (By our assumption on
(By our assumption on  and
and  ). But by LC2,
). But by LC2,  . So by transitivity,
. So by transitivity,  . Now, by I.H., since
. Now, by I.H., since  , we have
, we have  .
.
4 Related Work
The notion of Lagois connections [16] has surprisingly not been employed much in computer science. The only cited use of this idea seems to be the work of Huth [11] in establishing the correctness of programming language implementations. To our knowledge, our work is the only one to propose their use in secure information flow control.
Abstract Interpretation and type systems [5] have been used in secure flow analyses, e.g., [3, 4] and [24], where security types are defined using Galois connections employing, for instance, a standard collecting semantics. Their use of two domains, concrete and abstract, with a Galois connection between them, for performing static analyses within a single domain should not be confused with our idea of secure connections between independently-defined security lattices of two organisations.
There has been substantial work on SIF in a distributed setting at the systems level. DStar [26] for example, uses sets of opaque identifiers to define security classes. The DStar framework extends a particular Decentralized Information Flow Control (DIFC) model [12, 25] for operating systems to a distributed network. The only partial order that is considered in DStar’s security lattice is subset inclusion. So it is not clear if DStar can work on general IFC mechanisms such as FlowCaml [19], which can use any partial ordering. Nor can it express the labels of JiF [17] or Fabric [13] completely. DStar allows bidirectional communication between processes R and S only if \(L_R \sqsubseteq _{O_R} L_S\) and \(L_S \sqsubseteq _{O_S} L_R\), i.e., if there is an order-isomorphism between the labels. Our motivating examples indicate such a requirement is far too restrictive for most practical arrangements for data sharing between organisations.
Fabric [13, 14] adds trust relationships directly derived from a principal hierarchy to support federated systems with mutually distrustful nodes and allows dynamic delegation of authority.
Most of the previous DIFC mechanisms [2, 8, 12, 17, 20, 25] including Fabric are susceptible to the vulnerabilities illustrated in our motivating examples, which we will mention in the concluding discussion.
5 Conclusions and Future Work
Our work is similar in spirit to Denning’s motivation for proposing lattices, namely to identify a simple and mathematically elegant structure in which to frame the construction of scalable secure information flow in a modular manner that preserved the autonomy of the individual organisations. From the basic requirements, we identified the elegant theory of Lagois connections as an appropriate structure. Lagois connections provide us a way to connect the security lattices of two (secure) systems in a manner that does not expose their entire internal structure and allows us to reason only in terms of the interfaced security classes. We believe that this framework is also applicable in more intricate information flow control formulations such as decentralised IFC [18] and models with declassification, as well as formulations with data-dependent security classes [15]. We intend to explore these aspects in the future.
In this paper, we also proposed a minimal operational model for the transfer of data between the two domains. This formulation is spare enough to be adaptable at various levels of abstraction (programming language, systems, databases), and is intended to illustrate that the Lagois connection framework can conserve security, using non-interference as the semantic notion of soundness. The choice of non-interference and the use of a type system in the manner of Volpano et al. [23] was to illustrate in familiar terms how those techniques (removed from a particular language formulation) could be readily adapted to work in the context of secure connections between lattices. In this exercise, we made suitable assumptions of atomicity and the use of fresh variables for communication, so as to avoid usual sources of interference. By assuming that the basic intra-domain transactions are atomic and by not permitting conditional transfer of information across domains in the language, we have avoided dealing with issues related to implicit flows. We believe that the Lagois connection framework for secure flows between systems is readily adaptable for notions of semantic correctness other than non-interference, though that is an exercise for the future.
In the future we intend to explore how the theory of Lagois connections constitutes a robust framework that can support the discovery, decomposition, update and maintenance of secure MoUs for exchanging information. In this paper, we concerned ourselves only with two domains and bidirectional information exchange. Compositionality of Lagois connections allows these results to extend to chaining connections across several domains. In the future, we also intend to explore how one may secure more complicated information exchange arrangements than merely chains of bidirectional flow.
We close this discussion with a reminder of why it is important to have a framework in which secure flows should be treated in a modular and autonomous manner. Consider Myer’s DIFC model described in [18], where a principal can delegate to others the capacity to act on its behalf. We believe that this notion does not scale well to large, networked systems since a principal may repose different levels of trust in the various hosts in the network. For this reason, we believe that frameworks such as Fabric [13, 14] may provide more power than mandated by a principle of least privilege. In general, since a principal rarely vests unqualified trust in another in all contexts and situations, one should confine the influence of the principals possessing delegated authority to only specific domains. A mathematical framework that can deal with localising trust and delegation of authority in different domains and controlling the manner in which information flow can be secured deserves a deeper study. We believe that algebraic theories such as Lagois connections can provide the necessary structure for articulating these concepts.
Notes
- 1.
Denning showed that the proposed structures, namely complete join semi-lattices with a least element, are in fact complete lattices.
- 2.
Note that it is not necessary for the function
 to be total or surjective.
to be total or surjective. - 3.
Without loss of generality, we assume that
 , since we can suitably rename security classes.
, since we can suitably rename security classes.
References
Boudol, G.: Secure information flow as a safety property. In: Degano, P., Guttman, J., Martinelli, F. (eds.) FAST 2008. LNCS, vol. 5491, pp. 20–34. Springer, Heidelberg (2009). https://doi.org/10.1007/978-3-642-01465-9_2
Cheng, W., et al.: Abstractions for usable information flow control in Aeolus. In: 2012 USENIX Annual Technical Conference, Boston, MA, USA, 13–15 June 2012, pp. 139–151 (2012)
Cortesi, A., Ferrara, P., Halder, R., Zanioli, M.: Combining symbolic and numerical domains for information leakage analysis. Trans. Comput. Sci. 31, 98–135 (2018)
Cortesi, A., Ferrara, P., Pistoia, M., Tripp, O.: Datacentric semantics for verification of privacy policy compliance by mobile applications. In: D’Souza, D., Lal, A., Larsen, K.G. (eds.) VMCAI 2015. LNCS, vol. 8931, pp. 61–79. Springer, Heidelberg (2015). https://doi.org/10.1007/978-3-662-46081-8_4
Cousot, P.: Types as Abstract Interpretations. In: Conference Record of POPL 1997: The 24th ACM SIGPLAN-SIGACT Symposium on Principles of Programming Languages, Papers Presented at the Symposium, Paris, France, 15–17 January 1997, pp. 316–331 (1997)
Deng, S., Gümüsoglu, D., Xiong, W., Gener, Y.S., Demir, O., Szefer, J.: SecChisel: language and tool for practical and scalable security verification of security-aware hardware architectures. IACR Cryptology ePrint Archive 2017/193 (2017). http://eprint.iacr.org/2017/193
Denning, D.E.: A lattice model of secure information flow. Commun. ACM 19(5), 236–243 (1976)
Efstathopoulos, P., et al.: Labels and event processes in the Asbestos operating system. In: Proceedings of the 20th ACM Symposium on Operating Systems Principles 2005, SOSP 2005, Brighton, UK, 23–26 October 2005, pp. 17–30 (2005)
Ferraiuolo, A., Zhao, M., Myers, A.C., Suh, G.E.: Hyperflow: a processor architecture for nonmalleable, timing-safe information flow security. In: Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, CCS 2018, Toronto, ON, Canada, 15–19 October 2018, pp. 1583–1600 (2018)
Goguen, J.A., Meseguer, J.: Security policies and security models. In: 1982 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 26–28 April 1982, pp. 11–20 (1982)
Huth, M.: On the equivalence of state-transition systems. In: Burn, G., Gay, S., Ryan, M. (eds.) Theory and Formal Methods 1993. Workshops in Computing, pp. 171–182. Springer, London (1993). https://doi.org/10.1007/978-1-4471-3503-6_13
Krohn, M.N., et al.: Information flow control for standard OS abstractions. In: Proceedings of the 21st ACM Symposium on Operating Systems Principles 2007, SOSP 2007, Stevenson, Washington, USA, 14–17 October 2007, pp. 321–334 (2007)
Liu, J., Arden, O., George, M.D., Myers, A.C.: Fabric: building open distributed systems securely by construction. J. Comput. Secur. 25(4–5), 367–426 (2017)
Liu, J., George, M.D., Vikram, K., Qi, X., Waye, L., Myers, A.C.: Fabric: a platform for secure distributed computation and storage. In: Proceedings of the 22nd ACM Symposium on Operating Systems Principles 2009, SOSP 2009, Big Sky, Montana, USA, 11–14 October 2009, pp. 321–334 (2009)
Lourenço, L., Caires, L.: Dependent information flow types. In: Proceedings of the 42nd Annual ACM SIGPLAN-SIGACT Symposium on Principles of Programming Languages, POPL 2015, Mumbai, India, 15–17 January 2015, pp. 317–328 (2015)
Melton, A., Schröder, B.S.W., Strecker, G.E.: Lagois connections - a counterpart to Galois connections. Theor. Comput. Sci. 136(1), 79–107 (1994)
Myers, A.C.: JFlow: practical mostly-static information flow control. In: Proceedings of the 26th ACM SIGPLAN-SIGACT Symposium on Principles of Programming Languages, POPL 1999, San Antonio, TX, USA, 20–22 January 1999, pp. 228–241 (1999)
Myers, A.C.: Mostly-static decentralized information flow control. Ph.D. thesis, Massachusetts Institute of Technology, Cambridge, MA, USA (1999). http://hdl.handle.net/1721.1/16717
Pottier, F., Simonet, V.: Information flow inference for ML. ACM Trans. Program. Lang. Syst. 25(1), 117–158 (2003)
Roy, I., Porter, D.E., Bond, M.D., McKinley, K.S., Witchel, E.: Laminar: practical fine-grained decentralized information flow control. In: Proceedings of the 2009 ACM SIGPLAN Conference on Programming Language Design and Implementation, PLDI 2009, Dublin, Ireland, 15–21 June 2009, pp. 63–74 (2009)
Sabelfeld, A., Myers, A.C.: Language-based information-flow security. IEEE J. Sel. Areas Commun. 21(1), 5–19 (2003)
Schultz, D.A., Liskov, B.: IFDB: decentralized information flow control for databases. In: Eighth Eurosys Conference 2013, EuroSys 2013, Prague, Czech Republic, 14–17 April 2013, pp. 43–56 (2013)
Volpano, D.M., Irvine, C.E., Smith, G.: A sound type system for secure flow analysis. J. Comput. Secur. 4(2/3), 167–188 (1996)
Zanotti, M.: Security typings by abstract interpretation. In: Hermenegildo, M.V., Puebla, G. (eds.) SAS 2002. LNCS, vol. 2477, pp. 360–375. Springer, Heidelberg (2002). https://doi.org/10.1007/3-540-45789-5_26
Zeldovich, N., Boyd-Wickizer, S., Kohler, E., Mazières, D.: Making information flow explicit in histar. In: 7th Symposium on Operating Systems Design and Implementation (OSDI 2006), Seattle, WA, USA, 6–8 November, pp. 263–278 (2006)
Zeldovich, N., Boyd-Wickizer, S., Mazières, D.: Securing distributed systems with information flow control. In: Proceedings of 5th USENIX Symposium on Networked Systems Design & Implementation, NSDI 2008, San Francisco, CA, USA, 16–18 April 2008, pp. 293–308 (2008)
Zhang, D., Wang, Y., Suh, G.E., Myers, A.C.: A hardware design language for timing-sensitive information-flow security. In: Proceedings of the Twentieth International Conference on Architectural Support for Programming Languages and Operating Systems, ASPLOS 2015, Istanbul, Turkey, 14–18 March 2015, pp. 503–516 (2015)
Acknowledgments
The second author thanks Deepak Garg for insightful discussions on secure information flow. Part of the title is stolen from E.M. Forster.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2019 IFIP International Federation for Information Processing
About this paper
Cite this paper
Bhardwaj, C., Prasad, S. (2019). Only Connect, Securely. In: Pérez, J., Yoshida, N. (eds) Formal Techniques for Distributed Objects, Components, and Systems. FORTE 2019. Lecture Notes in Computer Science(), vol 11535. Springer, Cham. https://doi.org/10.1007/978-3-030-21759-4_5
Download citation
DOI: https://doi.org/10.1007/978-3-030-21759-4_5
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-21758-7
Online ISBN: 978-3-030-21759-4
eBook Packages: Computer ScienceComputer Science (R0)










 (sc2)
(sc2)  .
.

 is injective, i.e.,
is injective, i.e., 
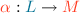 is surjective, i.e.,
is surjective, i.e.,  .
. in
in 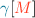 exists if and only if the meet of
exists if and only if the meet of  in
in 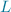 exists, and whenever either exists, they are equal.
exists, and whenever either exists, they are equal. of
of  in
in  exists if the join
exists if the join  of
of  in
in  exists, and in this case
exists, and in this case 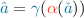


 ; (s has security type
; (s has security type  )
)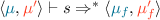 ; (execution of s starting from
; (execution of s starting from 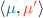 )
)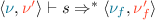 ; (execution of s starting from
; (execution of s starting from  )
) and
and  ;
; for all
for all 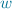 such that
such that 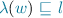 , and
, and  for all
for all  such that
such that  .
. to be total or surjective.
to be total or surjective. , since we can suitably rename security classes.
, since we can suitably rename security classes.