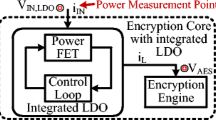
This work addresses the leakage information problem concerning cryptographic circuits. Physical implementations of cryptographic algorithms may let escape some side channel information, like electromagnetic emanations, temperature, computing time, and power consumption. With this information, an attacker can retrieve the data that is being computed, like cryptographic keys. This paper proposes a novel method to thwart DPA attacks, based on power consumption control. As main contribution, this approach not requires any modification on the cryptographic algorithm, the messages or keys.
Chapter PDF
Similar content being viewed by others
Keywords
These keywords were added by machine and not by the authors. This process is experimental and the keywords may be updated as the learning algorithm improves.
6. References
Rivest, R., Shamir, A., et al. “A Method for Obtaining Digital Signatures and Public-Key Cryptosystems”. ACM Communications, vol 21. pp. 120-126. 1978.
“Data Encryption Standard (DES)”. Federal Information Processing Standards Publications (FIPS PUBS) N 46-3. http://csrc.nist.gov/publications/fips/fips46-3/fips46-3.pdf.EUA. October 25, 1999.
Groupement des Cartes Bancaires CB. “ Les cartes Bancaires en Nombres 2004”. http://www.cartesbancaires.com/FR/info/communiques/2005/DPchiffresCB2004. pdf.Paris, march 2005.
Kocher, P., Jaffe J., et al. “Differential Power Analysis : Leaking Secrets”. Advances in Cryptology: Proceedings of CRYPTO'99, Vol. 1666, SpringerVerlag, pp. 388-397. 1999.
Messerges, T. S., Dabbish E. A., et al. “Power Analysis of Modular Exponentiation in Smartcards ”. Cryptographic Hardware and Embedded Systems -CHES 199. Lecture Notes in Computer Science, Vol. 1717, Springer, ISBN: 3-540-66646-X. pp. 144-157, 1999.
Goubin, L., Patarin, J. “DES and Differential Power Analysis -The “duplication” method”. Cryptographic Hardware and Embedded Systems -CHES 1999. Lecture Notes in Computer Science, Vol. 1717, Springer, ISBN: 3-540-66646-X. pp. 158-172, 1999.
Trichina, E., De Seta, D. et al. “Simplified Adaptive Multiplicative Masking for AES”. Cryptographic Hardware and Embedded Systems -CHES 2002. Lecture Notes in Computer Science, Vol. 2523, Springer, ISBN: 3-540-00409-2. pp. 187-197, 2003.
Golic, J. D., Tymen, C. “Multiplicative masking and Power Analysis of AES”. Cryptographic Hardware and Embedded Systems -CHES 2002. Lecture Notes in Computer Science, Vol. 2523, Springer, ISBN: 3-540-00409-2. pp. 198-212, 2003.
Benini, L., Macii, A., et al. “ Energy-aware design techniques for differential power analysis protection ”. Design Automation Conference -DAC 2003. Anaheim, USA. June, 2003.
Saputra, H. Vijaykrishnan, N., et al. “Masking behavior of DES encryption ”. Design, Automation and Test Europe -DATE 2003. ACM-Sigda, ISBN: 0-7695-1471-5. Munich, Germany, 2003.
Simon M., Ross A., et al. “Balanced Self-Checking Asynchronous Logic for Smart Card Applications”, Microprocessors and Microsystems Journal, 27(9). Elsevier, ISSN: 0141-9331. pp. 421-430, October 2003.
Clavier, C., Coron, J-S., et al. “ Differential Power Analysis in the presence of hardware countermeasures ”. Cryptographic Hardware and Embedded Systems -CHES 2000. Lecture Notes in Computer Science, Vol. 1965, Springer, ISBN: 3-540-41455-X. pp. 252-263, 2000.
Irwin, J., Page D., et al. “ Instruction stream mutation for non-deterministic processors. Internation conference on Application Specific Systems, Architectures and Processors -ASAP 2002. IEEE press. pp. 286-295. 2002
May, D., Muller H. L.et al., “Non-deterministic processors”. Information security and privacy -ACISP 2001. Lecture Notes in computer Science, volume 2119. Springer ISBN: 3-540-42300-1. pp. 115-129. Sydney, Australia. July 2001.
Mangard, S. “Hardware countermeasures against DPA -a statistical analysis of their effectiveness”. Topics in Cryptology -CT-RSA 2004. Lecture Notes in Computer Science, Vol. 2964, Springer, ISBN: ISBN 3-540-20996-4. pp. 222-235. San Francisco, USA. February 2004.
Fouque, P.-A., Muller F., et al. “Defeating Countermeasures Based on Randomized BSD Representations”. Cryptographic Hardware and Embedded Systems -CHES 2004. Lecture Notes in Computer Science, Vol. 3156, Springer, ISBN: 3-540-22666-4 pp. 312-327. Cambridge, EUA. 2004.
Shamir, A. “Protecting smart cards from passive power analysis with detached power supplies”. Cryptographic Hardware and Embedded Systems -CHES 2000. Lecture Notes in Computer Science, Vol. 1965, Springer, ISBN: 3-540-41455-X. pp.71-77, 2000.
Tummala, R. and Madisetti, V. “System on Chip or System on Package?” IEEE Design and Test of Computers Review. Vol. 16, N. 2. IEEE Press. ISSN: 0740-7475. pp. 48-56, April-June 1999.
Kocher, P., Jaffe, J., et al. “Introduction to Differential Power Analysis and Related Attacks”. Technical Report, Cryptography Research Inc., 1998. Available from http://www.cryptography.com/dpa/technical/index.html.
Coron, J-S. “Resistance against Differential Power Analysis for Elliptic Curve Cryptosystems”. Cryptographic Hardware and Embedded Systems, Proceedings of CHES 1999. Lecture Notes in Computer Science, Vol. 1717, Springer-Verlag, ISBN: 3-540-66646-X. pp. 292-302, 1999.
Chaum, D. “Security without identification: transaction systems to make Big Brother obsolete”. Communication of the ACM. Vol. 8., n° 10, pp. 1030-144. 1985.
Goubin, L. “A refined power-analysis attack on elliptic curve cryptosystems”. Publick Key Cryptography: Proceedings of PKC '03. Lecture Notes in Computer Science, Vol. 2567, Springer-Verlag, pp. 199-210. 2003.
Hideyo, M. and Atsuko, M. “Efficient Countermeasures against RPA, DPA, and SPA”. Cryptographic Hardware and Embedded Systems, Proceedings of CHES 2004. Lecture Notes in Computer Science, Vol. 3156, Springer-Verlag, ISBN: 3-540-22666-4. pp. 343-356, 2004.
Kocher, P. “Timing Attacks on Implementations of Diffie-Hellman, RSA, DSS, th and Other Systems”. 16 Workshop in Cryptology: Proceedings of Crypto '96. Lecture Notes in Computer Science, Vol. 1109, Springer-Verlag, ISBN: 3-540-61512-1, pp. 104-113. Santa Barbara, USA. 1996.
Boer, B. “A DPA Attack against the Modular Reduction within a CRT Implementation of RSA”. Cryptographic Hardware and Embedded Systems, Proceedings of CHES 2002. Lecture Notes in Computer Science, Vol. 2523, Springer-Verlag, ISBN: 3-540-00409-2, pp. 228-243, 2002.
Kim, C., Ha, J., et al. “A CRT-Based RSA Countermeasure against Physical Cryptanalysis”. International Conference on High Performance Computing and Communications: Proceedings of HPCC '05. pp. 549-554, Naples, Italy, 2005.
Bajard, J-C., Imbert, L., et al. “A Full RNS Implementation of RSA”. IEEE Transactions on Computers. Vol. 53, n° 6, pp. 769-774. 2004.
Ciet, M., Neve, M., et al. “Parallel FPGA implementation of RSA with residue th number systems -can side-channel threats be avoided?”. 46 IEEE International Midwest Symposium on Circuits and Systems: Proceedings of MWSCAS '03. Cairo, Egypt, December 2003.
Bajard, J-C., Imbert, L., et al. “Leak Resistant Arithmetic”. Cryptographic Hardware and Embedded Systems, Proceedings of CHES 2004. Lecture Notes in Computer Science, Vol. 3156, Springer-Verlag, ISBN: 3-540-22666-4. pp. 62-75, 2004.
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2007 Springer Science+Business Media, LLC
About this paper
Cite this paper
Mesquita, D. et al. (2007). Current Mask Generation: an Analog Circuit to Thwart DPA Attacks. In: Reis, R., Osseiran, A., Pfleiderer, HJ. (eds) Vlsi-Soc: From Systems To Silicon. IFIP International Federation for Information Proc, vol 240. Springer, Boston, MA. https://doi.org/10.1007/978-0-387-73661-7_20
Download citation
DOI: https://doi.org/10.1007/978-0-387-73661-7_20
Publisher Name: Springer, Boston, MA
Print ISBN: 978-0-387-73660-0
Online ISBN: 978-0-387-73661-7
eBook Packages: Computer ScienceComputer Science (R0)