Abstract
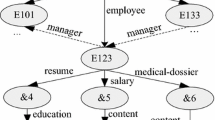
XML documents are frequently used in applications such as business transactions and medical records involving sensitive information. Access control on the basis of data location or value in an XML document is therefore essential. However, current approaches to efficient access control over XML documents have suffered from scalability problems because they tend to work on individual documents. To resolve this problem, we proposed a table-based approach in [28] . However, [28] also imposed limitations on the expressiveness, and real-time access control updates were not supported. In this paper, we propose a novel approach to XML access control through a policy matching tree (PMT) which performs accessibility checks with an efficient matching algorithm, and is shared by all documents of the same document type. The expressiveness can be expanded and real-time updates are supported because of the PTM’s flexible structure. Using synthetic and real data, we evaluate the performance and scalability to show it is efficient for checking accessibility for XML databases.
Chapter PDF
Similar content being viewed by others
Keywords
These keywords were added by machine and not by the authors. This process is experimental and the keywords may be updated as the learning algorithm improves.
References
Altinel, M., Franklin, M.: Efficient filtering of XML documents for selective dissemination of information. In: VLDB, pp. 53–64 (2000)
Bertino, E., Castano, S., Ferrari, E., Mesiti, M.: Controlled access and dissemination of XML documents. In: ACM WIDM, pp. 22–27 (1999)
Bertino, E., Castano, S., Ferrari, E., Mesiti, M.: Specifying and Enforcing Access Con-trol Policies for XML document Sources. World Wide Web Journal 3(3), 139–151 (2000)
Bertino, E., Ferrari, E.: Secure and selective dissemination of XML documents. In: ACM TISSEC, pp. 290–331 (2002)
Bishop, M., Snyder, L.: The transfer of information and authority in a protection system. In: Proc. 17th ACM Symposium on Operating Systems Principles (1979)
Boag, S., Chamberlin, D., Fernandez, M.F., Florescu, D., Robie, J., Simeon, J.: XQuery 1.0: An XML query language, W3C Working Draft, November 12 (2003), http://www.w3.org/TR/xquery/
Bray, T., Paoli, J., Sperberg-McQueen, C.M.: Extensible Markup Language (XML) 1.0. W3C Recommendation (Febrauary 1998), Available at http://www.w3g.org/TR/REC-xml
Chan, C.-Y., Felber, P., Garofalakis, M., Rastogi, R.: Efficient filtering of XML documents with XPath expressions. In: ICDE, pp. 235–244 (2002)
Cho, S., Amer-Yahia, S., Lakshmanan, L.V.S., Srivastava, D.: Optimizing the secure evaluation of twig queries. In: VLDB, pp. 490–501 (2000)
Clark, J., DeRose, S.: XML Path Language (XPath) version 1.0. W3C Recommendation (1999), Available at http://www.w3g.org/TR/xpath
Damiani, E., De Capitani di Vimercati, S., Paraboschi, S., Samarati, P.: Design and Implementation of an Access Control Processor for XML documents. In: WWW9 (2000)
Damiani, E., De Capitani di Vimercati, S., Paraboschi, S., Samarati, P.: A Fine-Grained Access Control System for XML Documents. In: ACM TISSEC, pp. 169–202 (2002)
Deutsch, A., Tannen, V.: Containment of regular path expressions under integrity constraints. In: KRDB (2001)
Diao, Y., Fischer, P., Franklin, M., To, R.: YFilter: Efficient and scalable filtering of XML documents. In: Demo at ICDE, p. 341 (2002)
Fan, W., Libkin, L.: On XML integrity constraints in the presence of DTDs. In: Symposium on Principles of Database Systems, pp. 114–125 (2001)
Fernandez, M.F., Suciu, D.: Optimizing regular path expressions using graph schemas. In: ICDE, pp. 14–23 (1998)
Gabillon, A., Bruno, E.: Regulating Access to XML Documents. In: Working Conference on Database and Application Security, pp. 219–314 (2001)
Gong, L.: A Secure Identity-Based Capability System. In: Proc. IEEE Symposium on Security and Privacy, pp. 56–65 (1989)
Hors, A.L., Hegaret, P.L., Wood, L., Nicol, G., Robie, J., Champion, M., Byrne, S.: Document Object Model (DOM) Level 3 Core Specification (2004), Available at http://www.w3.org/TR/2004/PR-DOM-Level-3-Core-20040205
Jones, A.K., Lipton, R.J., Snyder, L.: A Linear Time Algorithm for Deciding Security. In: Proc. 17th Symposium on Foundations of Computer Science, pp. 33–41 (1976)
Kaushik, R., Bohannon, P., Naughton, J.F., Korth, H.F.: Covering indexes for branching path queries. In: ACM SIGMOD, pp. 133–144 (2002)
Kha, D.D., Yoshikawa, M., Uemura, S.: An XML Indexing Structure with Relative Region Coordinate. In: ICDE, pp. 313–320 (2001)
Kudo, M., Hada, S.: XML Document Security based on Provisional Authorization. In: ACM CCS, pp. 87–96 (2000)
Li, Q., Moon, B.: Indexing and Querying XML Data for Regular Path Expressions. In: VLDB, pp. 361–370 (2001)
Murata, M., Tozawa, A., Kudo, M., Hada, S.: XML Access Control Using Static Analysis. In: ACM CCS, pp. 73–84 (2003)
OASIS. OASIS Extensible Access Control Markup Language (XACML) (Febrauary 2003), http://www.oasis-open.org/committees/xacml/docs
Neven, F., Schwentick, T.: XPath containment in the presence of disjunction, DTDs, and variables. In: ICDT, pp. 315–329 (2003)
Qi, N., Kudo, M.: Access-condition-table-driven access control for XML databases. In: ESORICS, pp. 17–23 (2004)
Sandhu, R.S., Coyne, E.J., Feinstein, H.L., Youman, C.E.: Role-Based Access Control Models. IEEE Computer 29(2), 38–47 (1996)
Yu, T., Srivastava, D., Lakshmanan, L.V.S., Jagadish, H.V.: Compressed Accessibility Map: Efficient Access Control for XML. In: VLDB, pp. 478–489 (2002)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2005 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Qi, N., Kudo, M. (2005). XML Access Control with Policy Matching Tree. In: di Vimercati, S.d.C., Syverson, P., Gollmann, D. (eds) Computer Security – ESORICS 2005. ESORICS 2005. Lecture Notes in Computer Science, vol 3679. Springer, Berlin, Heidelberg. https://doi.org/10.1007/11555827_2
Download citation
DOI: https://doi.org/10.1007/11555827_2
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-540-28963-0
Online ISBN: 978-3-540-31981-8
eBook Packages: Computer ScienceComputer Science (R0)