Abstract
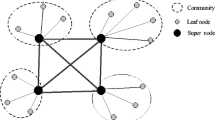
The special characteristics of the mobile environment, such as limited bandwidth, dynamic topology, heterogeneity of peers, and limited power, pose additional challenges on mobile peer-to-peer (MP2P) networks. Trust management becomes an essential component of MP2P networks to promote peer transactions. However, in an MP2P network, peers frequently join and leave the network, which dynamically changes the network topology. Thus, it is difficult to establish long-term and effective trust relationships among peers. In this paper, we propose a dynamic grouping based trust model (DGTM) to classify peers. A group is formed according to the peers’ interests. Within a group, mobile peers share resources and tend to keep stable trust relationships. We propose three peer roles (super peers, relay peers, and ordinary peers) and two novel trust metrics (intragroup trust and intergroup trust). The two metrics are used to accurately measure the trust between two peers from the same group or from different groups. Simulations illustrate that our proposed DGTM always achieves the highest successful transaction rate and the best communication overhead under different circumstances.
Similar content being viewed by others
References
Almenárez, F., Marín, A., Díaz, D., et al., 2011. Trust management for multimedia P2P applications in autonomic networking. Ad Hoc Netw., 9(4): 687–697. http://dx.doi.org/10.1016/j.adhoc.2010.09.005
Al-Oufi, S., Kim, H.N., El Saddik, A., 2012. A group trust metric for identifying people of trust in online social networks. Expert Syst. Appl., 39(18): 13173–13181. http://dx.doi.org/10.1016/j.eswa.2012.05.084
Castro, M.C., Kassler, A.J., Chiasserini, C.F., et al., 2009. Peer-to-peer overlay in mobile ad-hoc networks. In: Shen, X.M., Yu, H., Buford, J., et al. (Eds.), Handbook of Peer-to-Peer Networking. Springer US,p.1045–1080. https://doi.org/10.1007/978-0-387-09751-0_37
Chang, B.J., Kuo, S.L., 2009. Markov chain trust model for trust-value analysis and key management in distributed multicast MANETs. IEEE Trans. Veh. Technol., 58(4): 1846–1863. http://dx.doi.org/10.1109/TVT.2008.2005415
Chen, X., Proulx, B., Gong, X.W., et al., 2015. Exploiting social ties for cooperative D2D communications: a mobile social networking case. IEEE/ACM Trans. Netw., 23(5): 1471–1484. http://dx.doi.org/10.1109/TNET.2014.2329956
Chen, X., Gong, X.W., Yang, L., et al., 2016. Exploiting social tie structure for cooperative wireless networking: a social group utility maximization framework. IEEE/ACM Trans. Netw., 24(6): 3593–3606. http://dx.doi.org/10.1109/TNET.2016.2530070
Easa, F.R., Bafghi, A.G., Shakeri, H., 2012. A groupbased trust propagation method. 2nd Int. eConf. on Computer and Knowledge Engineering, p.313–317. http://dx.doi.org/10.1109/ICCKE.2012.6395398
Jeyaraj, J.A.S., Subadra, S., 2014. A study on dynamic source routing in ad hoc wireless networks. Int. J. Eng. Trends Technol., 8(7): 401–410. http://dx.doi.org/10.14445/22315381/IJETT-V8P269
Jia, M.J., Wang, H.Q., Ye, B., et al., 2016. A dynamic grouping-based trust model for mobile P2P networks. 13th IEEE Int. Conf. on Services Computing, p.848–851. http://dx.doi.org/10.1109/SCC.2016.121
Kamvar, S.D., Schlosser, M.T., Garcia-Molina, H., 2003. The eigentrust algorithm for reputation management in P2P networks. Proc. 12th Int. Conf. on World Wide Web, p.640–651. http://dx.doi.org/10.1145/775152.775242
Kassinen, O., Harjula, E., Korhonen, J., et al., 2009. Battery life of mobile peers with UMTS and WLAN in a Kademlia-based P2P overlay. 20th Int. Symp. on Personal, Indoor and Mobile Radio Communications, p.662–665. http://dx.doi.org/10.1109/PIMRC.2009.5450083
Largillier, T., Vassileva, J., 2012. Using collective trust for group formation. LNCS, 7493: 137–144. http://dx.doi.org/10.1007/978-3-642-33284-5_12
Leskovec, J., Huttenlocher, D., Kleinberg, J., 2010. Signed networks in social media. Proc. SIGCHI Conf. on Human Factors in Computing Systems, p.1361–1370. http://dx.doi.org/10.1145/1753326.1753532
Liang, Z.Q., Shi, W.S., 2005. PET: a PErsonalized Trust model with reputation and risk evaluation for P2P resource sharing. Proc. 38th Annual Hawaii Int. Conf. on System Sciences, p.201b. http://dx.doi.org/10.1109/HICSS.2005.493
Nayak, J., Naik, B., Kanungo, D.P., et al., 2015. An improved swarm based hybrid K-means clustering for optimal cluster centers. 2nd Int. Conf. on Information Systems Design and Intelligent Applications, p.545–553. http://dx.doi.org/10.1007/978-81-322-2250-7_54
Ou, Z.H., Song, M.N., Zhan, X.S., et al., 2008. Key techniques for mobile peer-to-peer networks. J. Softw., 19(2): 404–418 (in Chinese). http://dx.doi.org/10.3724/sp.j.1001.2008.00404
Qureshi, B., Min, G., Kouvatsos, D., 2010. M-Trust: a trust management scheme for mobile P2P networks. IEEE/IFIP 8th Int. Conf. on Embedded and Ubiquitous Computing, p.476–483. http://dx.doi.org/10.1109/euc.2010.79
Qureshi, B., Min, G., Kouvatsos, D., 2012. A distributed reputation and trust management scheme for mobile peer-to-peer networks. Comput. Commun., 35(5): 608–618. http://dx.doi.org/10.1016/j.comcom.2011.07.008
Ranjan, R., Zhao, L., 2013. Peer-to-peer service provisioning in cloud computing environments. J. Supercomput., 65(1): 154–184. http://dx.doi.org/10.1007/s11227-011-0710-5
Ratnasamy, S., Karp, B., Yin, L., et al., 2002. GHT: a geographic hash table for data-centric storage. ACM Int. Workshop on Wireless Sensor Networks and Applications, p.78–87. http://dx.doi.org/10.1145/570738.570750
Spaho, E., Kulla, E., Xhafa, F., et al., 2012. P2P solutions to efficient mobile peer collaboration in MANETs. 7th Int. Conf. on P2P, Parallel, Grid, Cloud and Internet Computing. http://dx.doi.org/10.1109/3pgcic.2012.50
Sun, Z.X., Tang, Y.W., 2007. Multilayer and grouping P2P trust model based on global reputation. J. Commun., 28(9): 133–140 (in Chinese).
Tan, H., Wang, Y., Hao, X.H., et al., 2010. Arbitrary obstacles constrained full coverage in wireless sensor networks. Proc. 5th Int. Conf. on Wireless Algorithms, Systems, and Applications, p.1–10. http://dx.doi.org/10.1007/978-3-642-14654-1_1
Tian, C., Jiang, J., Hu, Z., et al., 2010. A novel super-peer based trust model for peer-to-peer networks. Chin. J. Comput., 33(2): 345–355 (in Chinese). http://dx.doi.org/10.3724/sp.j.1016..2010.00345
Tian, H.R., Zou, S.H., Wang, W.D., et al., 2006. A group based reputation system for P2P networks. LNCS, 4158: 342–351. http://dx.doi.org/10.1007/11839569_33
Wu, X., 2011. A stable group-based trust management scheme for mobile P2P networks. Int. J. Dig. Cont. Technol. Appl., 5(2): 116–125. http://dx.doi.org/10.4156/jdcta.vol5.issue2.13
Xiong, L., Liu, L., 2004. PeerTrust: supporting reputationbased trust for peer-to-peer electronic communities. IEEE Trans. Knowl. Data Eng., 16(7): 843–857. http://dx.doi.org/10.1109/TKDE.2004.1318566
Yang, H.S., Sun, J.H., 2016. A study on hybrid trust evaluation model for identifying malicious behavior in mobile P2P. Peer-to-Peer Netw. Appl., 9(3): 578–587. http://dx.doi.org/10.1007/s12083-015-0411-6
Yates, J.S., Storch, M.F., Nijhawan, S., et al., 2012. Apparatus for Executing Programs for a First Computer Architecture on a Computer of a Second Architecture. US Patent 8 127 121.
Zhang, Y.C., Chen, S.S., Yang, G., 2009. SFTrust: a double trust metric based trust model in unstructured P2P system. IEEE Int. Symp. on Parallel & Distributed Processing, p.1–7. http://dx.doi.org/10.1109/IPDPS.2009.5161240
Zhou, R.F., Hwang, K., 2007. PowerTrust: a robust and scalable reputation system for trusted peer-to-peer computing. IEEE Trans. Parall. Distr. Syst., 18(4): 460–473. http://dx.doi.org/10.1109/TPDS.2007.1021
Zhou, R.F., Hwang, K., Cai, M., 2008. GossipTrust for fast reputation aggregation in peer-to-peer networks. IEEE Trans. Knowl. Data Eng., 20(9): 1282–1295. http://dx.doi.org/10.1109/TKDE.2008.48
Zhu, H.F., Bao, F., 2007. Quantifying trust metrics of recommendation systems in ad-hoc networks. IEEE Wireless Communications and Networking Conf., p.2904–2908. http://dx.doi.org/10.1109/WCNC.2007.538
Zhuge, H., Chen, X., Sun, X.P., et al., 2008. HRing: a structured P2P overlay based on harmonic series. IEEE Trans. Parall. Distr. Syst., 19(2): 145–158. http://dx.doi.org/10.1109/TPDS.2007.70725
Author information
Authors and Affiliations
Corresponding author
Additional information
Project supported by the National Natural Science Foundation of China (Nos. 61502118, 61370212, and 61402127) and the Natural Science Foundation of Heilongjiang Province, China (Nos. F2015029 and QC2015070)
A preliminary version was presented at the 13th IEEE International Conference on Services Computing, June 27–July 2, 2016, San Francisco, USA
ORCID: Jun-yu LIN, http://orcid.org/0000-0003-4807-0609
Rights and permissions
About this article
Cite this article
Jia, Mj., Wang, Hq., Lin, Jy. et al. DGTM: a dynamic grouping based trust model for mobile peer-to-peer networks. Frontiers Inf Technol Electronic Eng 18, 559–569 (2017). https://doi.org/10.1631/FITEE.1601535
Received:
Revised:
Published:
Issue Date:
DOI: https://doi.org/10.1631/FITEE.1601535