Abstract
Due to the unguaranteed connectivity, wireless sensor networks based on delay tolerant network (DTN) are typically characterized by the opportunistic forwarding mechanism in transmission. Such a mechanism requires nodes to participate in forwarding messages actively. However, when the mechanism is used in the real world, selfish nodes will exhibit some non-cooperation behaviors. Therefore, some incentive mechanism may be designed to encourage selfish nodes. In order to solve the selfishness problem, we propose a fair credit-based incentive mechanism for routing in DTN-based sensor networks. In this mechanism, when a source node sends messages to its destination, each relay node will be rewarded with some credits. The accumulated credits are then used to evaluate the level of cooperation in the network. The selfish nodes with few credits are not able to get enough service from other nodes. With the fair incentive, all participating relays will get equal rewards by the trusted third party. In order to evaluate the proposed mechanism, we also perform some simulation, and the results demonstrate that the method can be used to support efficient routing for DTN-based sensor networks.
Similar content being viewed by others
1 Introduction
As a kind of wireless technology, wireless sensor networks (WSNs) are systems that comprise large numbers (usually hundreds or thousands) of wirelessly connected heterogeneous sensor nodes that are spatially distributed across a large field of interest [1]. There is a wide range of applications where WSNs are extensively used, and their development in other applications is still growing. There exists a specific kind of WSN applications in which end-to-end connectivity [2, 3] between nodes rarely exists. For example, in the environmental and ecology observation, it is difficult to deploy WSNs in a vast field or some special environments such as a forest or a mountainous area. To solve this problem, we can implement the WSN based on delay tolerant network (DTN) using autonomous air vehicle as a data ferry [4]. DTN [5, 6] has currently been focused as a solution for communication in discontinuous networks, such as satellite sensor network [7], vehicular sensor network [8], and mobile sensor network [9]. Therefore, DTN has become a kind of important network architecture for WSNs. DTN-based sensor networks have a wide range of application scenarios in real life.
Due to the disruption connectivity of DTN-based sensor networks, the movement of nodes is exploited to transfer in-transit data by the “store-carry-and-forward” strategy and routing protocols are usually designed in an opportunistic way. Nodes usually have short-range radios that may not allow them to connect all other nodes in DTN-based sensor networks. Thus, nodes need to physically carry data from one location to another before it comes closer to other nodes and establishes connection. Therefore, it is more challenging to perform reliable routing in DTN-based sensor networks than typical WSNs.
Many existing studies on DTN routing protocol just depend on the hypothesis that each node is ready to relay data to others [10]. However, in some typical DTN-based applications, nodes may refuse to serve as data relay due to their limited resources, such as non-rechargeable batteries, buffer space, and wireless resources. In other words, the nodes intend to be selfish. As a result, a node may not be willing to relay data for others. Therefore, the previous hypothesis does not work when there are selfish or even malicious nodes and the cooperation among nodes cannot be guaranteed. Those selfish nodes want to maximize their own benefits. For example, a selfish node may be reluctant to join the forwarding that is not directly beneficial to it, which could make a designed DTN routing protocol useless. Such inactive cooperation will definitely influence the overall performance of the DTN routing protocols [11].
Specially, in certain DTN applications such as vehicular sensor networks, nodes are distributed over a majority of mobile devices that are controlled and operated by individuals. In such applications, it is highly possible that there exist some selfish operators, who may take selfish actions voluntarily. Therefore, a proper and efficient incentive mechanism should be integrated for DTN-based applications in real-world scenarios [12]. In this study, we design an incentive mechanism based on credit rewarding to achieve more efficient performance in DTN-based sensor networks under the constraint of nodes’ selfishness. The major contributions of this study are as follows:
First, we propose an incentive-compatible mechanism to deal with the nodes that want to conserve their own benefits and enjoy others service.
Second, we use some trust mechanism to avoid the problem that nodes attempt to cheat the network, and make sure the fairness among the nodes.
The remaining sections of the study are organized as follows. Section 2 gives a comprehensive review of the related works. Then, we introduce the network model and describe our incentive mechanism in Sections 3 and 4, respectively. We simulate our protocol and show the evaluation results in Section 5. Moreover, it is followed by the discussion and conclusion with some future research directions in Section 6.
2 Related works
DTN is typically featured with relay nodes and the store-carry-forward scheme. Obviously, such scheme requires nodes to forward messages in a cooperative way. For example, each node should use its own limited buffer and energy [13, 14] to store and relay messages for other nodes during the movement. Otherwise, many messages may not be delivered to destinations successfully. However, there are some selfish nodes among the relay nodes in real-life applications. They may exhibit selfish behaviors to conserve their limited resources like buffer and energy, even to maximize their expected profits. Some may drop messages from their buffer after they receive messages, or even block messages from others. Such selfish behaviors are also called non-cooperation behaviors. It is a great threat to both the performance and the QoS of DTN routing [15].
In order to overcome nodes’ selfishness in more suitable manner, a few existing works analyze such behavior and evaluate different levels of cooperation. Helgason et al. in [16] describe the benefit of node cooperation firstly and then evaluate how different levels of cooperation affect the delivery rate. The investigation is based on Markov chains analytical stochastic models and simulations. Balasubramanian evaluates the performance of routing protocol in a scenario where nodes exhibit various degrees of selfishness [17]. Li et al. in [18] take epidemic routing as an example to investigate the performance with non-cooperation behaviors in forwarding messages. They focused on the message delivery rate and delivery cost. The result of their research has shown that the non-cooperation behaviors (drooping and not receiving) deteriorated the routing performance.
The most promising way to address the selfishness issue is to enforce nodes to cooperate by using some incentive mechanisms. Incentive mechanisms can be broadly divided in three types: barter-based strategy, credit exchange strategy, and reputation strategy. Barter-based strategy is regarded as the simplest strategy, popularly known as tit-for-tat (TFT). The core of TFT is that two nodes will exchange the same amount of information when they encounter each other. In other words, the principle is “I will do for you as much as you did for me”. This strategy ensures the fairness of exchange and avoids selfish behaviors. Credit-based strategy uses virtual credit as the reward for forwarding. When a node forwards messages generated by others, it will get some credits as a return. Furthermore, virtual credit can be used to gain the services of other nodes. In our strategy, we use reputation to indicate the degree of cooperation. If the value of reputation is low, it means that a node is selfish, otherwise the node is cooperative. The incentive mechanisms based on reputation can be further divided into two categories, detection-based model and without detection model. In RADON [19] and MobiID [20], the authors proposed some methods to detect the reputation of nodes and forward messages according to their reputations. However, in this way, some nodes may cheat in collusion with other nodes in order to increase their reputation. The existing works about incentive mechanism are suitable for conventional mobile networks, like ad hoc networks. Jaramillo and Srikant proposed a reputation mechanism called DARWIN [21], which is designed to avoid a retaliation situation after some nodes have been falsely perceived as selfish, so cooperation can be done quickly. Zhong et al. proposed a system against the cheating and selfish behavior [22].
Moreover, in recent years, a few of novel mechanisms have been proposed to solve the selfishness problem based on the unique characteristics of DTN (e.g., the unguaranteed connectivity). Barter game [23], one of the most popular game-theoretic models, used an incentive mechanism to discourage selfish behavior based on barter. Similar with barter game, many research efforts are designed to address the problem of nodes’ selfishness by using game theory, such as incentive schemes in [24, 25]. In [26], Zhu et al. propose a credit-based incentive scheme called SMART and consider that there exist selfish and malicious nodes in DTN. In order to address their effect, SMART is implemented based on secure multilayer to prevent malicious and uses credits to encourage selfish nodes. Chen and Chan consider that detecting selfish actions is a difficult problem. They proposed a credit-based incentive system for DTN, named MobiCent [27] and designed a MDR (multiplicative decreasing reward) algorithm to calculate reward. Rolla and Curado describe a new credit-based mechanism for DTN, which uses a utility function to denote the monetary value and a buffer management algorithm to prevent the selfish behavior of nodes [28]. Seregina et al. study the reward and the time in relaying messages and design a reward policy for the source in a DTN with two hops [29]. Furthermore, some researches try to integrate fairness and secure idea for designing a better DTN routing. For example, Chen et al. in [30] propose a credit-based rewarding scheme to motivate the nodes to truthfully forward the messages during every contact opportunity. Another credit-based rewarding scheme is proposed by further considering that a node may get more contact information on others. Seregina et al. in [31] propose a practical incentive mechanism for a two-hop DTN. A reward is given only to the relay that is the first one to deliver the message to the destination. Jedari et al. in [32] propose a game-theoretic incentive scheme for social-aware routing, to stimulate socially selfish nodes in message relaying and guarantee that the routing performance gets maximized when selfish nodes follow the scheme.
In our work, we propose a new incentive mechanism called FCIM (fair credit-based incentive mechanism) for DTN-based sensor networks with selfish nodes. We incorporate a credit-based incentive mechanism into DTN message forwarding, which differs from previous works. We integrate the trusted third party (TTP) to make sure the fairness and avoid fraud among nodes.
3 Network model and assumptions
In this section, we mainly introduce the basic network model and assumptions for our method.
3.1 Network model
Based on the target communication environment, we assume that nodes in network are selfish, but not malicious. They may take any selfish actions as they wish, in order to maintain their benefits.
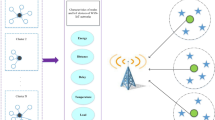
DTN-based sensor networks are typically characterized by the unguaranteed end-to-end connectivity. Figure 1 presents a scenario of a simple DTN. We denote the topology of the network as an undirected graph G=<V, E>, where V denotes the node set and E denotes the set of opportunistic contact edges. Each node has a unique non-zero identity Ni in the network. We assume that each node has limited resources (buffer, battery, etc.). We assume that a node has finite buffer space for carrying messages originated by others, but an unlimited buffer for messages originated by itself. As lack of permanent connectivity, a temporary network consists of nodes with high mobility. In this model, we assume nodes’ movement is totally random. As long as nodes enter the communication range and discover their neighbors, they will get transfer opportunity.
Messages are generated by the source nodes and delivered to the destination nodes. As there is no permanent end-to-end connectivity, relay nodes are required to participate in forwarding. Relay nodes with wireless interface are allowed to communicate with others in their proximity. In other words, communication opportunities emerge when two nodes enter into the radio range. During the transmission, several copies will be generated by relay nodes. Moreover, each copy has a time stamp indicating its time to live (TTL). Relays can drop the copies when it becomes useless. As nodes own limited resources, they may not be willing to receive messages and help in forwarding for others.
In our transmission model, each node acts both as the source wishing to deliver out its own generated messages and the relay carrying and forwarding others’ messages. We assume that each node in the network has three self-organizing actions:
-
1.
Transfer means that a node receives data from other nodes and forwards the data to other immediate node or the destination within the communication range. In other words, nodes transfer data generated locally.
-
2.
Non-transfer means that a node refuses to receive messages from others.
-
3.
Drop means that a node receives data from other nodes, but it does not transfer the data to neighbors and drop it directly.
Based on the characteristic of DTN and nodes’ own requirements, they will take different actions such as non-transfer and drop to save their limited resources for maximizing their benefits. However, such uncooperative behaviors have a strong impact on the performance of the whole network and obviously reduce the overall benefits of all nodes. In order to reduce the effect of nodes’ selfishness, cooperation among nodes must be encouraged by some incentive mechanisms.
Compulsive cooperation mechanisms would guarantee efficient and fair operations. Therefore, we try to introduce three primary ingredients in our incentive mechanisms: TTP, credit pattern, and rejecting pattern.
3.2 Trusted third party
As described in the previous sections, when we design a new incentive-based protocol, the problem of fairness must be considered. The TTP plays an impartial role to make sure the fairness among nodes. In order to avoid the cheating in nodes’ credit, the accumulated credits of each node are stored and updated by TTP. Due to the cooperation enforcement mechanism and the temptation of accumulated credits, some nodes may take some unfair behaviors. For example: (a) Some nodes are likely to falsify their credits by themselves. Especially, nodes may try to increase their credits for gaining more services by others. (b) Some destinations do not pay the promissory rewards to the participants. Therefore, two major functions of TTP are given as follows:
-
(1)
TTP is responsible for determining the credits of nodes. The node can only read it, but not modify it.
-
(2)
TTP also controls the messages to be forwarded. Each message is generated with two basic fields, source node and destination node. TTP blocks the message forwarding to the destination with few credits.
As the network in this study is totally dynamic, it is unnecessary for TTP to be a part of the network. On the contrary, the TTP can be a running server that acts as a central controller. Each node can use the long-range low-bandwidth links to communicate with the TTP for the verification and payment during the rewarding process.
3.3 Credit pattern
The credit pattern is the key element of our incentive-based protocol. It is a scale to evaluate the degree of nodes’ cooperation. The incentive mechanism takes nodes’ credits into consideration for intuitively reflecting the degree of nodes’ cooperation. Nodes’ credit value is denoted as a real number to measure the cooperative behavior of a node and stored in a node table maintained by TTP. In this table, each item is denoted in the format of [Ni, value]. Cooperative behavior implies how many times a node provides other nodes with required services. Therefore, we can evaluate the cooperative behavior for node Ni by [Ni, CR(Ni)]. All the participants involved in transmission will get some credits as a reward, after the messages are delivered to destinations successfully. In this way, a larger credit value indicates higher cooperation. On the contrary, a smaller credit value indicates lower cooperation. Moreover, the larger credit value nodes have, the more opportunity they will get for delivering their own data. Such mechanism aims to encourage nodes to participate in relaying messages generated by others.
The basic framework of the credit pattern is shown in Fig. 2. In this figure, node Ns wants to send message to node Nd, and there exists no end-to-end path between them. Thus, some relays (Ni) may participate in forwarding. To any Ni, it has knowledge about the message, such the source, the destination, and the size of message. After several hops, the message is delivered to the destination Nd. Further, Nd will pay the reward to TTP, and then TTP will distribute the reward to all participants.
According to the case shown in Fig. 2, if a source node Ns wishes to send data to a destination node Nd, we can see how the credit mechanism works in detail. In order to get a high credit, the relay node Ni is willing to receive and forward data. In the head of the data, we will record each relay’s identity (M[MID, Size, Ns, Ni, Ni + 1, ⋯, Nd]) from the source node Ns to the destination node Nd. When the data reaches its destination Nd, Ndwill confirm that the message is complete and correct. The forwarding process is over when the destination receives the data and sends back the ACK, and then TTP assigns reward to the relay nodes.
Specially, to some destination Nd with few credits, the message cannot be sent from source to any relay node. To each message, TTP will check the credits of its destination first. If the credits are too few, it will not have enough reward to pay for relay nodes.
3.4 Rejective pattern
As an exceptional case, there are some nodes that refuse to receive messages, due to their limited buffer size. In our incentive mechanism, we allow some nodes with high traffic load to be selfish. Therefore, we set a threshold to measure the level of traffic load, which is denoted as tlmax. When the traffic load of a node is over the threshold (tlmax), the rejective pattern will be enabled automatically. Node can refuse any message until its traffic load decreases under the threshold. The traffic load will be updated every 3 s by each node. Thus, each node has its own information table hold by the TTP (see Table 1).
Let us consider a simple case. There are two relay nodes, one has a high traffic load, and the other has a low traffic load. Messages will be forwarded by the later in priority. Therefore, FCIM consider that nodes with high traffic load can take selfish behavior. The detail of rejective pattern is given as below (see Fig. 3). Firstly, the routing protocol will choose some nodes to relay messages. If there is a node Ni with a higher traffic load tl(Ni) over the threshold tl(max), FCIM will remind the routing protocol about that truth. Then the routing protocol may choose another candidate with lower traffic load to relay messages.
4 Methods/experimental
In this section, we describe the incentive mechanism of FCIM with more details. It is the responsibility of the incentive mechanism to ensure that an individual node cannot acquire the desired services from the network unless it cooperates with others. Moreover, we also design an experimental simulation to evaluate the performance of the proposed method and present the process in detail.
4.1 Computing credit
Node’s credit is calculated and maintained as follows. We denote node’s credit as CR(Ni), which refers to the degree of cooperation. To each node, it has an initialization constant value of credit called CRinit, which is a non-zero value. Node has no right to modify its CR(Ni), and just owns the read-only permission. Only the TTP can perform the modification operations like subtracting, adding, etc. When a message is successfully delivered to the destination Nd, Nd needs to reward all the relay nodes that participated in forwarding the message. Thus, nodes are encouraged to participate in forwarding for increasing their CR(Ni). When a message is delivered, the destination will generate and send the ACK, which contains the messages ID, the source node ID, the destination node ID, and the list of relays (M[MID, S, Ni, Ni + 1, ⋯, D]).
In FCIM, the destination pays the reward to the TTP, and then participants are assigned reward by the TTP. We assume that each message is equally important. However, the message with an extra size is an exception. In our incentive mechanism, we have a threshold to control the size of messages. If the destination receives an over-sized message, it needs to pay an extra reward denoted by exp. The value exp is calculated by Eq. (1), where κ refers to the extra size, and η refers to the reward for per unit of extra size. Thus, the TTP will decrease the destination’s credit (CR(Nd)) according to Eq. (3), where RE(Nd) refers to the amount of reward Nd should pay to the relays. RE(Nd) is calculated by Eq. (2), where β refers to the reward Nd should pay with normal size messages. The delivery of messages decreases CR(Nd) until it goes to zero. Once the CR(Ni) of a node goes down to zero, no other nodes will forward messages originated from that node and also it cannot receive any message from others, because the forwarding services cannot get any reward for relays. In this case, that node is regarded as a selfish one.
Furthermore, FCIM considers that all relay nodes are equally important during the process of forwarding. The list of relays is recorded on the message head. Thus, the reward that each participant gets is equal, and noted as RE(Ni). RE(Ni) is calculated by Eq. (4), where c refers to the count of relays in the list. When the message is delivered, and the destination sends the ACK to the TTP, the TTP will update the credit of each participant, according to Eq. (5).
According to the above credit mechanism, nodes have to cooperate with others in order to get more credits and obtain services from others. As long as the credit of a node is greater than zero, it is able to pay the reward.
4.2 Cooperation enforcement
In FCIM, cooperation is mandatory according to the rewarding incentive mechanism. In our assumption, each node may require two kinds of service, (a) destination nodes want to receive messages that are sent to them and (b) source nodes want to send their messages to destination nodes. If nodes want to ensure their services, they have to increase their credits. In this case, nodes have no choice but to receive and relay messages. For relay nodes, once they receive messages, they must forward them in order to get rewards from destinations after delivering. The credit mechanism of FCIM will force nodes to cooperate with others in order to get more credits and obtain services from others.
In the network, each node holds a number of messages in its buffer space. Nodes carry and forward them to other relay nodes or deliver them to the respective destinations. A relay node may also forward the replicas of the same message to several nodes in order to increase the delivery rate. Similarly, for selfish nodes, they may forward the same message to more nodes in order to earn more rewards than it actually deserves. Such behavior will cause flooding in the network. Many existing routing protocols intend to avoid flooding. They are designed to select finite optimized nodes to relay messages. Therefore, the purpose of our incentive mechanism is to optimize the delivery rate without flooding. Therefore, we will perform FCIM after the routing. In other words, we require the nodes that are selected by the routing protocol to relay messages compulsively. Moreover, the TTP and rewarding process will not produce extra overhead on message delivery.
Figure 4 gives a detailed routing process with FCIM. When the source node generates a message, the TTP will check the CR(Nd) of the destination firstly. Only when CR(Nd) is over the maximum expected reward that the destination needs to pay, the source is able to send the message successfully. Then, the routing protocol will select (by node selector) the optimized relay nodes iteratively until the message is delivered to the destination. The task of relay selection just depends on what kind of routing protocol we used for the network. Moreover, if there is a selected node with high traffic load, the rejecting pattern of FCIM will remind the sender to select alternative nodes. When the message is delivered to the destination, it will pay reward to each relay node under the coordination of the TTP.
4.3 Experimental simulation
In order to evaluate the performance, we simulate our incentive mechanism in ONE (opportunistic network environment) simulator [33]. In our simulation, we set an initial credit value CRinit for FCIM. This allows each node to deliver at least 3 pieces of messages before its credit value goes down to zero, and it can earn its credits by relaying others’ messages at the same time. Also, we set the maximum traffic load for node tlmax to 90% of the node’s buffer size in simulation. When the traffic load of node Ni (\( {tl}_{\left({N}_i\right)} \)) is over tlmax, Ni can refuse to receive any message. In addition, the remainder of the parameters used in simulation is given in Table 2.
In this simulation, we mainly focus on evaluating the performance with four metrics [32]: delivery ratio, delivery delay [34], overhead, and hop count. We evaluate the incentive mechanism from the following two aspects:
-
(1)
Compare the performance of the routing protocol with and without the incentive mechanism.
-
(2)
Evaluate the incentive mechanism with three different scenes.
We implement the FCIM based on the prophet routing protocol and epidemic routing protocol to evaluate the performance. We perform the simulation in a real urban movement environment in this part .
In order to evaluate how FCIM works in optimizing performance, we perform several experiments by changing the cooperation varying from 0 to 100%. Table 3 summarizes the major parameters used in the simulation.
In order to confirm the validity and adaptability of FCIM, we compare the performance of prophet routing with FCIM and without FCIM in three different scenes, Infocom06 [35], Random, and RollerNet. Infocom06 data set recorded the 3-day data transmission between 78 portable Bluetooth devices and 20 static devices. RollerNet data set was derived from a group trip in the wild, recording the data transmission between 62 iMote-equipped nodes and 78 Bluetooth devices. Random refers to the trajectory of a random scene. Taking into account the various scenes, we set a longer message TTL for longer simulation time. The details about the parameters for the simulation are shown in Table 4.
5 Results and discussion
5.1 Evaluation for different operations
The result of the performance evaluation with and without the incentive mechanism is shown in Fig. 5. Figure 5a illustrates the message delivery rate for two routing protocols with and without FCIM. The delivery rate is high when the cooperation value is large. However, with the cooperation decreasing, the delivery rate of protocols without FCIM declines quickly, while the protocol with FCIM preserves a higher delivery rate. The result of delivery delay is given in Fig. 5b. Delivery delay [36] refers to the time consumption for forwarding messages from source to destination, and we use the average delivery delay in the simulation. According to Fig. 5b, it is ea sy to get the conclusion that FCIM is able to restrain selfish behavior. More nodes participate into forwarding, so the delay time does not increase obviously. Similarly, the protocols with FCIM take fewer hops during the forwarding process (see Fig. 5d). Hop count refers to how many relay nodes are involved in forwarding a message from source to destination. Obviously, if more nodes are willing to relay messages, the messages will be forwarded to destination more quickly. Figure 5c depicts the overhead for these two protocols with and without FCIM. Overhead is used to evaluate that how much the network resource is consumed [37]. We can see that the trend of the protocols with FCIM is much similar to the one without FCIM. It is mainly because that the incentive mechanism makes more nodes carry the copies of messages. This behavior also increases the burden on the network.
5.2 Evaluation for different scenes
The result of the performance evaluation in three different scenes is shown in Figs. 6, 7, 8 and 9. Figure 6 shows the delivery rate in three different scenes. Obviously, the delivery rate of Prophet routing with FCIM is higher than the one without FCIM. This is the result by using the incentive mechanism, and some selfish nodes are urged to participate in forwarding for accumulating their credits. Therefore, more messages are successfully delivered to the destination nodes.
Figure 7 shows the delay in three different scenes. When we adopt FCIM, the average delay time is clearly short. Apparently, when nodes actively participate in forwarding, the messages will be forwarded much more quickly.
We can find that prophet with FCIM has lower overhead in Fig. 8. Its trend is similar to prophet without FCIM. The former takes traffic load of node into account during the forwarding, so it keeps efficient at a lower level of overhead and thus saves the network resource.
Figure 9 shows the hop count in three different scenes. Because the prophet routing protocol forwards messages to nodes with high probability and FCIM forces nodes to participate into forwarding, most messages are delivered to destinations by fewer relay nodes. As the structure of Infocom06 and RollerNet is relative dense, the performance of the both protocols (with and without FCIM) show little difference in different scenes.
We have compared the performance of the same routing protocol (prophet) with and without FCIM in three different scenes. The structures of the three scenes are totally different, so the simulation results are also quite different. Generally, the routing protocol with FCIM performs better than that without FCIM in all the three scenes. This result has verified the effectiveness and adaptability of the proposed method in different environments.
5.3 Evaluation for different incentive schemes
We also compare the performance of FCIM with two existing methods with similar incentive schemes, MobiCent [27] and SMART [26]. According to the results in Fig. 10, it seems that FCIM performs better than the other two schemes, although the overall performance is very close for the three schemes. Figure 10a illustrates the message delivery rate for the three schemes and Figure 10b depicts the overhead for the three schemes.
All the three schemes have used an incentive mechanism to solve the problem nodes’ selfishness. However, both MobiCent and SMART take the mechanism of pay-by-source. It means that the credits are paid by the source node. All the relay nodes on the path will then share the total credits provided by the source node in advance. In contrast, we use a different strategy called pay-by-destination and it means that the credits are paid by the destination node that has received messages. This strategy seems to be more reasonable, because the destination node does not have to calculate the payment in advance. The destination node will know how much it should pay after receiving messages. Therefore, we can determine the credits dynamically in our method.
6 Conclusion
This study presents a fair credit-based incentive mechanism called FCIM for DTN-based sensor networks by optimizing the activity of selfish nodes. The proposed incentive mechanism considers that encouraging selfish nodes to cooperate is as important as tolerating reasonable selfish behaviors. On one hand, FCIM is able to guarantee high delivery rate to destination and makes sure that nodes are hard to cheat by using a credit pattern. On the other hand, FCIM allows nodes to have some specific selfish behaviors by using a rejecting pattern. Meanwhile, we implemented the simulation based on ONE simulator, and the results show that FCIM is able to optimize the routing performance and motivate more nodes to participate in forwarding.
This work considers some specific selfish behaviors in forwarding. In the future, we need to consider more patterns of selfish behaviors and take more attributes of nodes (e.g., energy, security) into account. Therefore, we can design a more comprehensive incentive mechanism for DTN routing.
Availability of data and materials
Data sharing is not applicable to this article as no datasets were generated or analyzed during the current study.
Abbreviations
- DTN:
-
Delay tolerant network
- FCIM:
-
Fair credit-based incentive mechanism
- TFT:
-
Tit-for-tat
- TTL:
-
Time to live
- TTP:
-
Trusted third party
- WSN:
-
Wireless sensor network
References
K.S. Low, W.N.N. Win, J.E. Meng. Wireless sensor networks for industrial environments[C]. International Conference on Computational Intelligence for Modelling, Control and Automation and International Conference on Intelligent Agents, Web Technologies and Internet Commerce Vol. IEEE Computer Society, 2005:271-276.
W. Guo, N. Xiong, A.V. Vasilakos, G. Chen, H. Cheng, Multi-Source Temporal Data Aggregation in Wireless Sensor Networks. Wireless Personal Communications 56(3), 359–370 (2011).
W. Guo, B. Zhang, G. Chen, X. Wang, N. Xiong, A PSO-Optimized Minimum Spanning Tree-Based Topology Control Scheme for Wireless Sensor Networks. Int. J. Distrib. Sens. Netw. 9(4), 985410 (2017).
T.H.P. Tran, H. Yamamoto, K. Yamazaki. Data synchronization method in DTN sensor network using autonomous air vehicle[C]. International Conference on Advanced Communication Technology. IEEE, 2014:382-387.
S. Burleigh, A. Hooke, L. Torgerson, et al., Delay-tolerant networking: an approach to interplanetary internet[J]. IEEE Communications Magazine. 41(6), 128–136 (2003)
K. Fall. A delay-tolerant network architecture for challenged internets[C]. SIGCOMM Proceedings of the Conference on Applications, Technologies, Architectures and Protocols for Computer Communications, ACM. 2003, 33(4):27-34.
F. Long, N. Xiong, A.V. Vasilakos, L.T. Yang, F. Sun, A sustainable heuristic QoS routing algorithm for pervasive multilayered satellite wireless networks. Wireless Netw. 16(6), 1657–1673 (2010).
K.Z. Ghafoor, K. Abu Bakar, J. Lloret, R.H. Khokhar, K.C. Lee, Intelligent beaconless geographical forwarding for urban vehicular environments. Wireless Netw. 19(3), 345–362 (2013).
H. Zheng, J. Li, X. Feng, W. Guo, Z. Chen, N. Xiong, Spatial-Temporal Data Collection with Compressive Sensing in Mobile Sensor Networks. Sensors 17(11), 2575 (2017).
K.Z. Ghafoor, M.A. Mohammed, J. Lloret,K. Abu Bakar, Z.M. Zainuddin, Routing Protocols in Vehicular Adhoc Networks: Survey and Research Challenges. Electron. Lett. 5(4), 39 (2013).
A. Chaintreau, P. Hui, J. Crowcroft, et al., Impact of human mobility on opportunistic forwarding algorithms[J]. IEEE Transactions on Mobile Computing 6(6), 606–620 (2007)
A. Panagakis, A. Vaios, I. Stavrakakis. On the effects of cooperation in DTNs[C]. International Conference on Communication Systems Software and MIDDLEWARE. IEEE, 2007:1-6.
C. Lin, N. Xiong, J.H. Park, T.-H. Kim, Dynamic power management in new architecture of wireless sensor networks. Int. J. Commun. Syst. 22(6), 671–693 (2009).
H. Cheng, R. Guo, Z. Su, N. Xiong, W. Guo, Service-Oriented Node Scheduling Schemes with Energy Efficiency in Wireless Sensor Networks. Int. J. Distrib. Sens. Netw. 10(2), 247173 (2014).
G. Resta, P. Santi. The effects of node cooperation level on routing performance in delay tolerant networks[C]. Sensor, Mesh and Ad Hoc Communications and Networks, 2009. SECON '09. IEEE Communications Society Conference on. IEEE, 2009:1-9.
O.R. Helgason, F. Legendre, V. Lenders, et al. Performance of opportunistic content distribution under different levels of cooperation[C]. Wireless Conference (EW), 2010 European. IEEE, 2010:903 - 910.
M. Karaliopoulos, Assessing the vulnerability of DTN data relaying schemes to node selfishness[J]. IEEE Communications Letters 13(12), 923–925 (2010)
Y. Li, G. Su, Z. Wang, Evaluating the effects of node cooperation on DTN routing[J]. AEU - International Journal of Electronics and Communications 66(1), 62–67 (2012)
N. Li, S.K. Das. RADON: Reputation-assisted data forwarding in opportunistic networks[C]. International Workshop on Mobile Opportunistic NETWORKING. ACM, 2010:8-14.
L.Wei, H. Zhu, Z. Cao, et al. MobiID: a user-centric and social-aware reputation based incentive scheme for delay/disruption tolerant networks[C]. International Conference on Ad-Hoc, Mobile, and Wireless Networks. Springer-Verlag, 2011:177-190.
J.J. Jaramillo, R. Srikant. DARWIN: distributed and adaptive reputation mechanism for wireless ad-hoc networks[C]. MOBICOM '07: Proceedings of the, ACM International Conference on Mobile Computing and NETWORKING. 2007:87-98.
S. Zhong, J. Chen, Y.R. Yang, Sprite: A simple, cheat-proof, credit-based system for mobile ad-hoc networks[C]. Proceedings - IEEE INFOCOM 3, 1987–1997 (2010)
L. Buttyán, L. Dóra, M. Félegyházi, et al., Barter trade improves message delivery in opportunistic networks[J]. Ad Hoc Networks 8(1), 1–14 (2010)
W. Chahin, H.B.A. Sidi, R. El-Azouzi, et al., Incentive mechanisms based on minority games in heterogeneous delay tolerant networks[C]. Teletraffic Congress. IEEE, 1–9 (2013)
S.P. Hulke, V. Attar, Game theory based incentive mechanisms in delay tolerant network[J]. International Journal of Computer Applications 115(1), 22–25 (2015)
H. Zhu, X. Lin, R. Lu, et al., SMART: a secure multilayer credit-based incentive scheme for delay-tolerant networks[J]. IEEE Transactions on Vehicular Technology 58(8), 4628–4639 (2009)
B.B. Chen, M.C. Chan, MobiCent: a credit-based incentive system for disruption tolerant network[C]. Proceedings - IEEE INFOCOM, 875–883 (2010)
V.G. Rolla, M. Curado, Enabling wireless cooperation in delay tolerant networks. Information Sciences 290(290), 120–133 (2015)
T. Seregina, O. Brun, R.E. Azouzi, et al., On the design of a reward-based incentive mechanism for delay tolerant networks[J]. Networking & Internet Architecture, 1–1 (2014)
H. Chen, W. Lou, Z. Wang, et al., A secure credit-based incentive mechanism for message forwarding in noncooperative DTNs[J]. IEEE Transactions on Vehicular Technology 65(8), 6377–6388 (2016)
T. Seregina, O. Brun, R. El-Azouzi, et al., On the design of a reward-based incentive mechanism for delay tolerant networks[J]. IEEE Transactions on Mobile Computing 16(2), 453–465 (2017)
B. Jedari, L. Liu, T. Qiu, et al., A game-theoretic incentive scheme for social-aware routing in selfish mobile social networks[J]. Future Generation Computer Systems 70(C), 178–190 (2016)
A. Keränen, J. Ott, T. Kärkkäinen. The ONE simulator for DTN protocol evaluation[C]. Proceedings of the 2nd International Conference on Simulation Tools and Techniques. 2009.
Y. Liu, K. Ota, K. Zhang, M. Ma, N. Xiong, A. Liu, J. Long, QTSAC: An Energy-Efficient MAC Protocol for Delay Minimization in Wireless Sensor Networks. IEEE Access 6, 8273–8291 (2018).
P. Hui, J. Crowcroft, E. Yoneki, BUBBLE Rap: social-based forwarding in delay-tolerant networks[J]. IEEE Transactions on Mobile Computing 10(11), 1576–1589 (2011)
E. Jones, P. Ward, Routing strategies for delay-tolerant network[EB/OL]. Submitted to ACM Computer Communication Review. (2006) https://www.netlab.tkk.fi/opetus/s383151/articles/dtn-routing-survey.pdf
J. Broch, D.A. Maltz, D.B. Johnson, et al. A performance comparison of multi-hop wireless ad hoc network routing protocols[C]. Proceeding of the 4th annual ACM/IEEE International Conference on Mobile Computing and Networking. 1998, 85-97.
Acknowledgements
This work is partially supported by grants from the National Social Science Foundation Program (No. 16BGL193).
Funding
This work is partially funded by grants from the National Social Science Foundation Program (No. 16BGL193).
Author information
Authors and Affiliations
Contributions
The work presented here was carried out in collaboration between all authors. Yuxin Mao, Chenqian Zhou, and Xudong Zhu defined the research theme. Yuxin Mao and Chenqian Zhou designed methods and experiments, carried out the experiments, interpreted the results, and wrote the paper. Ji Qi co-designed methods and made important revisions to the manuscript. Xudong Zhu co-designed experiments and co-worked on analysis. All authors have contributed to, seen, and approved the manuscript.
Corresponding author
Ethics declarations
Competing interests
The authors declare that they have no competing interests.
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Mao, Y., Zhou, C., Qi, J. et al. A fair credit-based incentive mechanism for routing in DTN-based sensor network with nodes’ selfishness. J Wireless Com Network 2020, 232 (2020). https://doi.org/10.1186/s13638-020-01823-0
Received:
Accepted:
Published:
DOI: https://doi.org/10.1186/s13638-020-01823-0