Abstract
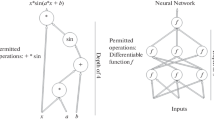
Programming of an adaptive information security system (ISS) is reduced to describing of information fields of neural networks (NN) in the form of batch neural-network programs. A similar description of data-field component makes it possible to study processes of operation and adaptation of neural-network ISS in the composition of computer-aided systems by modeling the interaction of operating data with the information field of NN.
Similar content being viewed by others
References
Osovetskii, L.G., Scientific-Techncial Prerequisities for the Growth the Role of Information Security in Modern Information Technologies, Izv. Vuzov, Priborostr., 2003, vol. 46, no. 7, pp. 5–18.
Kuznetsova, V.L. and Rakov, M.A., Samoorganizatsiya v tekhnicheskikh sistemakh (Self-organization in Technical Systems), Kiev: Naukova Dumka, 1987.
Nesteruk, G.F., Osovetskii, L.G., and Kharchenko, A.F., Informatsionnaya bezopasnost’i intellektual’nye sredstva zashchity informatsionnykh resursov (Immunologiya sistem informatsionnylh tekhnologii) (Information Security and Intellectual Security Means for Information Resources (Immunology of Information Technologies Systems)), St. Petersburg: SPbGUEF, 2003.
Nesteruk, G.F., Osovetskii, L.G., and Nesteruk, F.G., Application of Neural-Fuzzy Networks in Adaptive Information Security Systems, Neiroinform.-2005: Mat. VII Vseross. NTK, Moscow: MIFI, 2005, vol. 1, pp. 163–171.
Nesteruk, G.F., Kupriyanov, M.S., and Nesteruk, F.G., Logarithmic Neural Networks: Modeling of Work and Training, Sb. Dokl. VI Mezhd. Konf. Myagk. Vychisl. Izmer. SCM’2003, St. Petersburg: SPbGETU, 2003, vol. 1, pp. 359–362.
Mayers, G.J., Advances in Computer Architecture, New York: Wiley, 1982.
Neiroinformatik, Gorban’, A.N., Dunin-Barkovskii, V.L., Kirdin, A.N., et al., Eds., Novosibirsk: Nauka, 1998.
Kupriyanov, M.S., Nesteruk, G.F., and Puzankov, D.V., Realization of Soft Calculations in Distributed Systems, Izv. SPbGETU “LETI,” Seriya “Informatika, Upravlenie i Komp’yuternye Tekhnologii,” St. Petersburg: SPbGETU, 2002, no. 1, pp. 34–39.
Nesteruk, G.Ph. and Kupriyanov, M.S., Neural-Fuzzy Systems with Fuzzy Links, Proc. VI Int. Conf. SCM’2003, St. Petersburg, 2003, vol. 1, pp. 341–344.
Nesteruk, G.F. and Kupriyanov, M.S., Functional Stability of Neural Networks and Fuzzy Representation of Information, Izv. SPbGETU “LETI,” Seriya “Informatika, Upravlenie i Komp’yuternye Tekhnologii,” St. Petersburg: SPbGETU, 2003, no. 1, pp. 154–169.
Author information
Authors and Affiliations
Additional information
Original Russian Text © F.G. Nesteruk, L.G. Nesteruk, G.F. Nesteruk, 2009, published in Avtomatika i Telemekhanika, 2009, No. 3, pp. 160–171.
This work was supported by the Federal Agency for Science and Innovation, projects nos. 2006-RI-19.0/001/809 and 2006-RI-19.0/001/811.
Rights and permissions
About this article
Cite this article
Nesteruk, F.G., Nesteruk, L.G. & Nesteruk, G.F. Application of the formal model for describing processes of adaptive information security in computer-aided systems. Autom Remote Control 70, 491–501 (2009). https://doi.org/10.1134/S000511790903014X
Received:
Published:
Issue Date:
DOI: https://doi.org/10.1134/S000511790903014X