Abstract
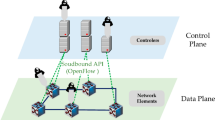
Software-Defined Network (SDN) has emerged as the new big thing in networking. The separation of the control plane from the data plane and application plane gives SDN an edge over traditional networking. With SDN, the devices are configured at the control plane which makes it easier to manage network devices from one central point. However, decoupled architecture creates a single point of failure. A single point of failure attracts cyber-attacks, such as Distributed Denial of Service (DDoS) attacks. Attackers have recently been using multi-vector attacks from single-vector attacks. The need for real-time detection as a countermeasure is of paramount importance. The attackers using sophisticated techniques to launch DDoS attacks dictates the need for a sophisticated intrusion detection system. This paper proposes a Deep Neural Network (DNN) solution for real-time detection of DDoS attacks in SDN. The proposed IDS produced a detection accuracy of 97.59% using fewer resources and less time.







Similar content being viewed by others
References
Akhunzada A, Ahmed E, Gani A, Khan MK, Imran M. Securing software defined networks. IEEE Commun Mag. 2015;53:36–44.
Garg S, Kumar N, Rodrigues JJPC, Rodrigues JJPC. Hybrid deep-learning-based anomaly detection scheme for suspicious flow detection in SDN: a social multimedia perspective. IEEE Trans Multimed. 2019;21(3):566–78. https://doi.org/10.1109/TMM.2019.2893549.
Malik J, Akhunzada A, Bibi I, Imran M, Musaddiq A, Kim SW. Hybrid deep learning: an efficient reconnaissance and surveillance detection mechanism in SDN. IEEE Access. 2020;8:134695–706. https://doi.org/10.1109/ACCESS.2020.3009849.
Li C, et al. Detection and defense of DDoS attack–based on deep learning in OpenFlow-based SDN. Int J CommunSyst. 2018;31(5):1–15. https://doi.org/10.1002/dac.3497.
Kim H, Feamster N. Improving network management with software defined networking. IEEE Commun Mag. 2013. https://doi.org/10.1109/MCOM.2013.6461195.
Polat H, Polat O, Cetin A. Detecting DDoS attacks in software-defined networks through feature selection methods and machine learning models. Sustain. 2020. https://doi.org/10.3390/su12031035.
Manukian H, Traversa FL, Di Ventra M. Accelerating deep learning with memcomputing. Neural Networks. 2019;110:1–7. https://doi.org/10.1016/j.neunet.2018.10.012.
Diego K, Fernando MVR, Paulo EV, Christian ER, Azodolmolky S, Steve U. Software-Defined Networking: a comprehensive survey. Ecum Rev. 2015;17(3):219–23. https://doi.org/10.1111/j.1758-6623.1965.tb02070.x.
Rehman AU, Aguiar RL, Barraca JP. Fault-tolerance in the scope of Software-Defined Networking (SDN). IEEE Access. 2019;7:124474–90. https://doi.org/10.1109/access.2019.2939115.
Xia W, Wen Y, Foh CH, Niyato D, Xie H. A Survey on Software-Defined Networking. IEEE CommunSurv Tut. 2015. https://doi.org/10.1109/COMST.2014.2330903.
Hwang RH, Peng MC, Huang CW, Lin PC, Nguyen VL. An unsupervised deep learning model for early network traffic anomaly detection. IEEE Access. 2020;8:30387–99. https://doi.org/10.1109/ACCESS.2020.2973023.
Su SC, Chen YR, Tsai SC, Lin YB. Detecting P2P Botnet in Software Defined Networks. SecurCommunNetw. 2018. https://doi.org/10.1155/2018/4723862.
Latah M, Toker L. Towards an efficient anomaly-based intrusion detection for software-defined networks. IET Netw. 2018;7(6):453–9. https://doi.org/10.1049/iet-net.2018.5080.
Cui Y, et al. SD-Anti-DDoS: fast and efficient DDoS defense in software-defined networks. J NetwComputAppl. 2016;68:65–79. https://doi.org/10.1016/j.jnca.2016.04.005.
Jamadar RA. Network intrusion detection system using machine learning. Indian J SciTechnol. 2018;11(48):1–6. https://doi.org/10.17485/ijst/2018/v11i48/139802.
Shone N, Ngoc TN, Phai VD, Shi Q. A deep learning approach to network intrusion detection. IEEE Trans Emerg Top ComputIntell. 2018;2(1):41–50. https://doi.org/10.1109/tetci.2017.2772792.
Yulianto A, Sukarno P, Suwastika NA. Improving AdaBoost-based Intrusion Detection System (IDS) performance on CIC IDS 2017 dataset. J Phys ConfSer. 2019;1192(1):2019. https://doi.org/10.1088/1742-6596/1192/1/012018.
Kreutz D, Ramos FMV, Verissimo PE, Rothenberg CE, Azodolmolky S, Uhlig S. Software-defined networking: a comprehensive survey. Proc IEEE. 2015. https://doi.org/10.1109/JPROC.2014.2371999.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of Interest
The authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article is part of the topical collection “Cyber Security and Privacy in Communication Networks” guest edited by Rajiv Misra, R K Shyamsunder, Alexiei Dingli, Natalie Denk, Omer Rana, Alexander Pfeiffer, Ashok Patel and Nishtha Kesswani.
Rights and permissions
About this article
Cite this article
Makuvaza, A., Jat, D.S. & Gamundani, A.M. Deep Neural Network (DNN) Solution for Real-time Detection of Distributed Denial of Service (DDoS) Attacks in Software Defined Networks (SDNs). SN COMPUT. SCI. 2, 107 (2021). https://doi.org/10.1007/s42979-021-00467-1
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s42979-021-00467-1