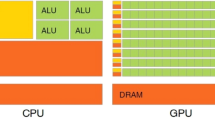
Abstract
In the past, Graphics Processing Unities (GPUs) were mainly used for graphics rendering. In the past 10 years, they have been redesigned and are used to accelerate a wide range of applications, including deep neural networks, image reconstruction and cryptographic algorithms. Despite being the accelerator of choice in a number of important application domains, today’s GPUs receive little attention on their security, especially their vulnerability to realistic and practical threats, such as side-channel attacks. In this work we present our study of side-channel vulnerability targeting a general purpose GPU. We propose and implement a side-channel power analysis methodology to extract all the last round key bytes of an AES (Advanced Encryption Standard) implementation on an NVIDIA TESLA GPU. We first analyze the challenges of capturing GPU power traces due to the degree of concurrency and underlying architectural features of a GPU, and propose techniques to overcome these challenges. We then construct an appropriate power model for the GPU. We describe effective methods to process the GPU power traces and launch a correlation power attack (CPA) on the processed data. We carefully consider the scalability of the attack with increasing degrees of parallelism, a key challenge on the GPU. Both our empirical and theoretical results show that parallel computing hardware systems such as a GPU are vulnerable to power analysis side-channel attacks, and need to be hardened against such threats.












Similar content being viewed by others
References
Brier E, Clavier C, Olivier F (2004) Correlation power analysis with a leakage model. InL: Cryptographic hardware & embedded systems, vol 3156, pp 16–29
Clavier C, Coron JS, Dabbous N (2000) Differential power analysis in the presence of hardware countermeasures. Springer, Berlin, pp 252–263
Cook D, Keromytis AD (2006) Cryptographics: exploiting graphics cards for security, vol 20. Springer Science & Business Media
Cook DL, Ioannidis J, Keromytis AD, Luck J (2005) Cryptographics: secret key cryptography using graphics cards. In: Topics in cryptology–CT-RSA 2005. Springer, pp 334–350
Daemen J, Rijmen V (1998) AES proposal: Rijndael
Fei Y, Ding AA, Lao J, Zhang L (2015) A statistics-based success rate model for DPA and CPA. J Cryptogr Eng 5(4):227–243
Gaster B, Howes L, Kaeli DR, Mistry P, Schaa D (2013) Heterogeneous computing with openCL: revised openCL 1.2 edition, 2nd edn. Morgan Kaufmann Publishers Inc., San Francisco
Genkin D, Shamir A, Tromer E (2014) RSA key extraction via low-bandwidth acoustic cryptanalysis. In: Advances in cryptology–CRYPTO 2014. Springer, pp 444–461
Gierlichs B, Batina L, Tuyls P, Preneel B (2008) Mutual information analysis. In: Cryptographic hardware & embedded systems, pp 426–442
Gilger J, Barnickel J, Meyer U (2012) GPU-acceleration of block ciphers in the OpenSSL cryptographic library. In: Information security. Springer, pp 338–353
Hwu WM (2011) GPU computing gems emerald edition, 1st edn. Morgan Kaufmann Publishers Inc., San Francisco
Iwai K, Kurokawa T, Nisikawa N (2010) Aes encryption implementation on cuda gpu and its analysis. In: 2010 First international conference on networking and computing, pp 209–214. https://doi.org/10.1109/IC-NC.2010.49
Jan MR, Anantha C, Borivoje N (2003) Digital integrated circuits: a design perspective
Jiang ZH, Fei Y, Kaeli D (2016) A complete key recovery timing attack on a gpu. In: 2016 IEEE International symposium on high performance computer architecture (HPCA), pp 394–405. https://doi.org/10.1109/HPCA.2016.7446081
Kocher P, Jaffe J, Jun B, Rohatgi P (2011) Introduction to differential power analysis. J Cryptogr Eng 1(1):5–27
Leischner N, Osipov V, Sanders P (2009) Nvidia fermi architecture white paper. http://www.nvidia.com/content/pdf/fermi_white_papers/nvidia_fermi_compute_architecture_whitepaper.pdf
Li Q, Zhong C, Zhao K, Mei X, Chu X (2012) Implementation and analysis of aes encryption on gpu. In: 2012 IEEE 14th International conference on high performance computing and communication, 2012 IEEE 9th international conference on embedded software and systems, pp 843–848. https://doi.org/10.1109/HPCC.2012.119
Lombardi F, Di Pietro R (2014) Towards a GPU cloud: benefits and security issues. In: Continued rise of the cloud. Springer, pp 3–22
Luo C, Fei Y, Luo P, Mukherjee S, Kaeli D (2015) Side-channel power analysis of a GPU AES implementation. In: IEEE Int. Con. on computer design (ICCD). IEEE, pp 281–288
Luo P, Fei Y, Fang X, Ding AA, Leeser M, Kaeli DR (2014) Power analysis attack on hardware implementation of MAC-Keccak on FPGAs. In: Int. Conf. on ReConFigurable computing and FPGAs (ReConFig), pp 1–7
Manavski S (2007) CUDA compatible GPU as an efficient hardware accelerator for AES cryptography. In: IEEE Int. Conf. on signal processing & communications, pp 65–68
Mangard S (2004) Hardware countermeasures against DPA – a statistical analysis of their effectiveness. Springer, Berlin, pp 222–235
Margara P (2015) Engine-CUDA, a cryptographic engine for CUDA supported devices. https://code.google.com/p/engine-cuda/
Maurice C, Neumann C, Heen O, Francillon A (2014) Confidentiality issues on a GPU in a virtualized environment. In: Financial cryptography and data security. Springer, pp 119–135
Messerges TS, Dabbish EA, Sloan RH (1999) Power analysis attacks of modular exponentiation in smartcards. In: Cryptographic hardware & embedded systems, pp 144–157
Moradi A, Hinterwälder G (2015) Side-Channel security analysis of ultra-low-power FRAM-based MCUs. In: Proc. Int WkShp on constructive side-channel analysis & secure design
NVIDIA (2015) CUDA C Programming Guide. http://docs.nvidia.com/cuda/pdf/CUDA_C_Programming_Guide.pdf
Ors SB, Gurkaynak F, Oswald E, Preneel B (2004) Power-analysis attack on an ASIC AES implementation. In: Int. conf. on info. tech.: coding & computing, vol 2, pp 546–552
Örs SB, Oswald E, Preneel B (2003) Power-analysis attacks on an FPGA–first experimental results. In: Cryptographic hardware & embedded systems, pp 35–50
Pietro RD, Lombardi F, Villani A (2016) CUDA leaks: a detailed hack for CUDA and a (partial) fix. ACM Trans Embedded Comput Syst (TECS) 15(1):15
Szerwinski R, Güneysu T (2008) Exploiting the power of GPUs for asymmetric cryptography. In: Cryptographic hardware and embedded systems. Springer, pp 79–99
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Luo, C., Fei, Y., Zhang, L. et al. Power Analysis Attack of an AES GPU Implementation. J Hardw Syst Secur 2, 69–82 (2018). https://doi.org/10.1007/s41635-018-0032-7
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s41635-018-0032-7