Abstract
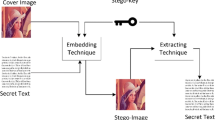
This article proposes a very high capacity steganography technique using differencing and substitution mechanisms. It divides the image into non-overlapped \(3{\times }3\) pixel blocks. For every pixel of a block, least significant bit (LSB) substitution is applied on two LSBs and quotient value differencing (QVD) is applied on the remaining six bits. Thus, there are two levels of embedding: (i) LSB substitution at lower bit planes and (ii) QVD at higher bit planes. If a block after embedding in this fashion suffers with fall off boundary problem, then that block is undone from the above hybrid embedding and modified 4-bit LSB substitution is applied. Experimentally, it is evidenced that the hiding capacity is improved to a greater extent. It is also experimentally proved that pixel difference histogram and RS analysis techniques cannot detect the proposed steganography technique.
Similar content being viewed by others
References
Cheddad, A.; Condell, J.; Curran, K.; Kevitt, P.M.: Digital image steganography: survey and analysis of current methods. Signal Process. 90, 727–752 (2010)
Martin, A.; Sapiro, G.; Seroussi, G.: Is image steganography natural? IEEE Trans. Image Process. 14(12), 2040–2050 (2005)
Fridrich, J.; Goljian, M.; Du, R.: Detecting LSB Steganography in color and gray-scale images. Mag. IEEE Multimed. Secur. 8(4), 22–28 (2001)
Wu, D.C.; Tsai, W.H.: A steganograhic method for images by pixel value differencing. Pattern Recogn. Lett. 24(9), 1613–1626 (2003)
Zhang, X.; Wang, S.: Vulnerability of pixel-value differencing steganography to histogram analysis and modification for enhanced security. Pattern Recogn. Lett. 25, 331–339 (2004)
Chang, K.C.; Chang, C.P.; Huang, P.S.; Tu, T.M.: A novel image steganography method using tri-way pixel value differencing. J. Multimed. 3(2), 37–44 (2008)
Lee, Y.P.; Lee, J.C.; Chen, W.K.; Chang, K.C.; Su, I.J.; Chang, C.P.: High-payload image hiding with quality recovery using tri-way pixel-value differencing. Inf. Sci. 191, 214–225 (2012)
Wu, H.C.; Wu, N.I.; Tsai, C.S.; Hwang, M.S.: Image steganographic scheme based on pixel-value differencing and LSB replacement methods. IEEE Proc. Vis. Image Signal Process. 152(5), 611–615 (2005)
Yang, C.H.; Weng, C.Y.; Wang, S.J.; Sun, H.M.: Varied PVD\(\,+\,\)LSB evading programs to spatial domain in data embedding systems. J. Syst. Softw. 83(10), 1635–1643 (2010)
Khodaei, M.; Faez, K.: New adaptive steganographic method using least-significant-bit substitution and pixel-value differencing. IET Image Proc. 6(6), 677–686 (2012)
Swain, G.: A steganographic method combining LSB substitution and PVD in a block. Proc. Comput. Sci. 85, 39–44 (2016)
Liao, X.; Wen, Q.Y.; Zhang, J.: A steganographic method for digital images with four-pixel differencing and modified LSB substitution. J. Vis. Commun. Image Represent. 22(1), 1–8 (2011)
Swain, G.: Digital image steganography using nine-pixel differencing and modified LSB substitution. Indian J. Sci. Technol. 7(9), 1444–1450 (2014)
Pradhan, A.; Sekhar, K.R.; Swain, G.: Digital image steganography based on seven way pixel value differencing. Indian J. Sci. Technol. 9(37), 1–11 (2016)
Darabkh, K.A.; Al-Dhamari, A.K.; Jafar, I.F.: A new steganographic algorithm based on multi directional PVD and modified LSB. J. Inf. Technol. Control 46(1), 16–36 (2017)
Swain, G.: Digital image steganography using eight directional PVD against RS analysis and PDH analysis. Adv. Multimed. (2018). (in press)
Jung, K.H.: Data hiding scheme improving embedding capacity using mixed PVD and LSB on bit plane. J. Real Time Image Process. 14(1), 127–136 (2018)
Yang, C.H.; Weng, C.Y.; Tso, H.K.; Wang, S.J.: A data hiding scheme using the varieties of pixel-value differencing in multimedia images. J. Syst. Softw. 84, 669–678 (2011)
Nilizadeh, A.F.; Nilchi, A.R.: Block texture pattern detection based on smoothness and complexity of neighborhood pixels. Int. J. Image Graph. Signal Process. 5, 1–9 (2014)
Yesilyurt, M.; Yalman, Y.: New approach for cloud computing security: using data hiding methods. Sadhana 41(11), 1289–1298 (2016)
Xiang, T.; Hu, J.; Sun, J.: Outsourcing chaotic selective image encryption to the cloud with steganography. Digit. Signal Proc. 43, 28–37 (2015)
Singh, P.; Raman, B.: Reversible data hiding based on Shamir’s secret sharing for color images over cloud. Inf. Sci. 422, 77–97 (2018)
Wu, C.C.; Kao, S.J.; Hwang, M.S.: A high quality image sharing with steganography and adaptive authentication scheme. J. Syst. Softw. 84, 2196–2207 (2011)
Tondwalkar, A.; Jani, P.V.: Secure localization of wireless devices with application to sensor networks using steganography. Proc. Comput. Sci. 78, 610–616 (2016)
USC-SIPI Image Database (Online). http://sipi.usc.edu/database/database.php?volume=misc
Pradhan, A.; Sahu, A.K.; Swain, G.; Sekhar, K.R.: Performance evaluation parameters of image steganography techniques. In: IEEE International Conference on Research Advances in Integrated Navigation Systems, pp. 1–8 (2016)
El-Emam, N.N.; AL-Zubidy, R.A.S.: New steganography algorithm to conceal a large amount of secret message using hybrid adaptive neural networks with modified adaptive genetic algorithm. J. Syst. Softw. 86(6), 1465–1481 (2013)
El-Emam, N.N.; Al-Diabat, M.: A novel algorithm for colour image steganography using a new intelligent technique based on three phases. Appl. Soft Comput. 37, 830–846 (2015)
El-Emam, N.N.; Qaddoum, K.S.: Improved steganographic security by applying an irregular image segmentation and hybrid adaptive neural networks with modified ant colony optimization. Int. J. Netw. Secur. Appl. 7(5), 23–47 (2015)
Al-Shatanawi, O.M.; El-Emam, N.N.: A new image steganography algorithm based on MLSB method with random pixels selection. Int. J. Netw. Secur. Appl. 7(2), 37–53 (2015)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Swain, G. Very High Capacity Image Steganography Technique Using Quotient Value Differencing and LSB Substitution. Arab J Sci Eng 44, 2995–3004 (2019). https://doi.org/10.1007/s13369-018-3372-2
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s13369-018-3372-2