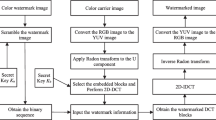
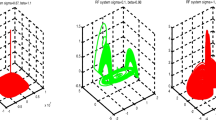
Abstract
Due to lightning growth in multimedia processing technologies and frequent usage of Internet, media contents often get exposed to malicious interventions. Hence it is very important to verify the authenticity and integrity of the digital contents by using proper security mechanisms. Thanks to the advancement in computer graphics processing technologies due to which higher dimensional rendering of real life objects has become apparent. Lately, three dimensional (3D) representations are more preferred in different application domains for better visualization and understanding. While talking about security related to 3D models, digital watermarking has come out to be an effective and prominent solution among various other authentication mechanisms. The purpose of this study is to present an in-depth review and investigation of the authentication based watermarking techniques for 3D models in spatial domain. The methods are classified based on various attributes that effect the design and working of an authentication protocol. The study also discusses different types of geometrical attacks that may occur to a 3D model and methodologies that help in detecting and locating the attacks. The paper concludes with a set of remarks and some of the research issues and challenges which are needed to be studied further.





Similar content being viewed by others
References
Al-Haj, A. M. (2010). Advanced techniques in multimedia watermarking: image, video and audio applications: Image, video and audio applications. Hershey: IGI Global.
Botsch, M., Kobbelt, L., Pauly, M., Alliez, P., & Lévy, B. (2010). Polygon mesh processing. Boca Raton: CRC Press.
Caldelli, R., Filippini, F., & Becarelli, R. (2010). Reversible watermarking techniques: An overview and a classification. EURASIP Journal on Information Security, 1, 1.
Cayre, F., & Macq, B. (2003). Data hiding on 3-d triangle meshes. IEEE Transactions on signal Processing, 51(4), 939–949.
Chang, Y. C., Wang, J. T., Chang, Y. T., & Yu, S. S. (2016). An error-detecting code based fragile watermarking scheme in spherical coordinate system. In: 2016 international symposium on computer, consumer and control (IS3C) (pp. 287–290). IEEE
Chen, T. Y., Hwang, M. S., & Jan, J. K. (2009). Adaptive authentication schemes for 3d mesh models. International Journal of Innovative Computing, Information and Control, 5(12), 4561–4572.
Cheung, Ym, & Wu, Ht. (2007). A sequential quantization strategy for data embedding and integrity verification. IEEE Transactions on Circuits and Systems for Video Technology, 17(8), 1007–1016.
Chou, C. M., & Tseng, D. C. (2006). A public fragile watermarking scheme for 3d model authentication. Computer-Aided Design, 38(11), 1154–1165.
Chou, C. M., & Tseng, D. C. (2007). Technologies for 3d model watermarking: A survey. International Journal of Computer Science and Network Security, 7, 328–334.
Chou, C. M., & Tseng, D. C. (2009). Affine-transformation-invariant public fragile watermarking for 3d model authentication. IEEE Computer Graphics and Applications, 29(2), 72–79.
Chuang, C.H., & Cheng, C.W., & Yen, Z.Y. (2010). Reversible data hiding with affine invariance for 3d models. In 2010 IET international conference on frontier computing. Theory, technologies and applications (pp. 77–81). IET
Corsini, M., Gelasca, E. D., Ebrahimi, T., & Barni, M. (2007). Watermarked 3-d mesh quality assessment. IEEE Transactions on Multimedia, 9(2), 247–256.
Dittmann, J., & Benedens, O. (2003). Invertible authentication for 3d meshes. In Electronic imaging 2003, international society for optics and photonics (pp. 653–664)
Gersho, A., & Gray, R. M. (2012). Vector quantization and signal compression (Vol. 159). Berlin: Springer.
Hrádek, J., Kuchař, M., & Skala, V. (2003). Hash functions and triangular mesh reconstruction. Computers & Geosciences, 29(6), 741–751.
Huang, C. C., Yang, Y. W., Fan, C. M., & Wang, J. T. (2013). A spherical coordinate based fragile watermarking scheme for 3d models. In International conference on industrial, engineering and other applications of applied intelligent systems (pp. 566–571). Springer
Huang, J., & Menq, C. H. (2002). Combinatorial manifold mesh reconstruction and optimization from unorganized points with arbitrary topology. Computer-Aided Design, 34(2), 149–165.
Huang, Y. H., & Tsai, Y. Y. (2015). A reversible data hiding scheme for 3d polygonal models based on histogram shifting with high embedding capacity. 3D Research, 6(2), 1–12.
Jeong, W. K., & Kim, C. H. (2001). Direct reconstruction of displaced subdivision surface from unorganized points. In Ninth pacific conference on computer graphics and applications, 2001. Proceedings (pp. 160–168). IEEE
Jhou, C. Y., Pan, J. S., & Chou, D. (2007). Reversible data hiding base on histogram shift for 3d vertex. In Third international conference on intelligent information hiding and multimedia signal processing, 2007, IIHMSP 2007 (vol. 1, pp. 365–370). IEEE
Ji, H., Yang, X., Zhang, C., & Gao, X. (2010). A new reversible watermarking of 3d models based on ratio expansion. In 2010 3rd International congress on image and signal processing (CISP) (vol. 8, pp. 3899–3903). IEEE
Jiang, D., Xu, Z., Chen, Z., Han, Y., & Xu, H. (2011). Joint time-frequency sparse estimation of large-scale network traffic. Computer Networks, 55(15), 3533–3547.
Jiang, D., Xu, Z., Li, W., & Chen, Z. (2015a). Network coding-based energy-efficient multicast routing algorithm for multi-hop wireless networks. Journal of Systems and Software, 104, 152–165.
Jiang, D., Xu, Z., & Xu, H. (2015b). A novel hybrid prediction algorithm to network traffic. Annals of Telecommunications-Annales Des téléCommunications, 70(9–10), 427–439.
Jiang, D., Nie, L., Lv, Z., & Song, H. (2016a). Spatio-temporal kronecker compressive sensing for traffic matrix recovery. IEEE Access, 4, 3046–3053.
Jiang, D., Yuan, Z., Zhang, P., Miao, L., & Zhu, T. (2016b). A traffic anomaly detection approach in communication networks for applications of multimedia medical devices. Multimedia Tools and Applications, 75(22), 14,281–14,305.
Jiang, D., Zhang, P., Lv, Z., & Song, H. (2016c). Energy-efficient multi-constraint routing algorithm with load balancing for smart city applications. IEEE Internet of Things Journal, 3(6), 1437–1447.
Jiang, D., Li, W., & Lv, H. (2017). An energy-efficient cooperative multicast routing in multi-hop wireless networks for smart medical applications. Neurocomputing, 220, 160–169.
Jiang, D., Huo, L., Lv, Z., Song, H., & Qin, W. (2018). A joint multi-criteria utility-based network selection approach for vehicle-to-infrastructure networking. IEEE Transactions on Intelligent Transportation Systems, 99, 1–15.
Jung, J. H., Hong, K., Park, G., Chung, I., Park, J. H., & Lee, B. (2010). Reconstruction of three-dimensional occluded object using optical flow and triangular mesh reconstruction in integral imaging. Optics Express, 18(25), 26,373–26,387.
Khan, A., Siddiqa, A., Munib, S., & Malik, S. A. (2014). A recent survey of reversible watermarking techniques. Information Sciences, 279, 251–272.
Lavoué, G. (2007). A roughness measure for 3d mesh visual masking. In Proceedings of the 4th symposium on applied perception in graphics and visualization (pp. 57–60). ACM
Lee, H., Dikici, Ç., Lavoué, G., & Dupont, F. (2011). Joint reversible watermarking and progressive compression of 3d meshes. The Visual Computer, 27(6–8), 781–792.
Lee, S., Yoo, C. D., & Kalker, T. (2007). Reversible image watermarking based on integer-to-integer wavelet transform. IEEE Transactions on Information Forensics and Security, 2(3), 321–330.
Lei, B., Tan, E. L., Chen, S., Ni, D., Wang, T., & Lei, H. (2014). Reversible watermarking scheme for medical image based on differential evolution. Expert Systems with Applications, 41(7), 3178–3188.
Lin, H. Y., Liao, H. Y., Lu, C. S., & Lin, J. C. (2005). Fragile watermarking for authenticating 3-d polygonal meshes. IEEE Transactions on Multimedia, 7(6), 997–1006.
Ling, C., & Ur-Rehman, O. (2015). Watermarking for image authentication. In N. Živić (Ed.), Robust image authentication in the presence of noise (pp. 43–73). Springer.
Luo, H., Lu, Z., & Wang, P., et al. (2010a). 3D model watermarking. In F. Yu, Z. Lu, H. Luo & P. Wang (Eds.), Three-dimensional model analysis and processing (pp. 305–370). Springer.
Luo, H., Lu, Z., & Wang, P., et al. (2010b). Reversible data hiding in 3d models. In: Three-dimensional model analysis and processing (pp. 371–416). Springer
Mao, X., Shiba, M., & Imamiya, A. (2001). Watermarking 3d geometric models through triangle subdivision. In: Photonics west 2001-electronic imaging (pp. 253–260). International Society for Optics and Photonics
Medimegh, N., Belaid, S., & Werghi, N. (2015). A survey of the 3d triangular mesh watermarking techniques. International Journal of Multimedia. https://doi.org/10.16966/ijm.102.
Molaei, A. M., Ebrahimnezhad, H., & Sedaaghi, M. H. (2013). A blind fragile watermarking method for 3d models based on geometric properties of triangles. 3D Research, 4(4), 1–9.
Mousavi, S. M., Naghsh, A., & Abu-Bakar, S. (2014). Watermarking techniques used in medical images: A survey. Journal of Digital Imaging, 27(6), 714–729.
Ni, Z., Shi, Y. Q., Ansari, N., & Su, W. (2006). Reversible data hiding. IEEE Transactions on Circuits and Systems for Video Technology, 16(3), 354–362.
Nie, L., Jiang, D., Guo, L., & Yu, S. (2016). Traffic matrix prediction and estimation based on deep learning in large-scale IP backbone networks. Journal of Network and Computer Applications, 76, 16–22.
Ohbuchi, R., Masuda, H., & Aono, M (1997). Watermaking three-dimensional polygonal models. In Proceedings of the fifth ACM international conference on multimedia (pp. 261–272). ACM
Ohbuchi, R., Masuda, H., & Aono, M. (1998). Data embedding algorithms for geometrical and non-geometrical targets in three-dimensional polygonal models. Computer Communications, 21(15), 1344–1354.
Piegl, L. A. (2005). Ten challenges in computer-aided design. Computer-Aided Design, 37(4), 461–470.
Sun, Z., Lu, Z. M., & Li, Z. (2006). Reversible data hiding for 3d meshes in the pvq-compressed domain. In 2006 international conference on intelligent information hiding and multimedia (pp. 593–596). IEEE
Thodi, D. M., & Rodríguez, J. J. (2007). Expansion embedding techniques for reversible watermarking. IEEE Transactions on Image Processing, 16(3), 721–730.
Tian, J. (2003). Reversible data embedding using a difference expansion. IEEE Trans Circuits Syst Video Techn, 13(8), 890–896.
Tsai, Y. Y., Cheng, T. C., & Huang, Y. H. (2017). A low-complexity region-based authentication algorithm for 3D polygonal models. Security and Communication Networks. https://doi.org/10.1155/2017/1096463.
Váša, L., & Rus, J. (2012). Dihedral angle mesh error: A fast perception correlated distortion measure for fixed connectivity triangle meshes. Computer Graphics Forum, Wiley Online Library, 31, 1715–1724.
Wang, J. T., Chang, Y. C., Yu, C. Y., & Yu, S. S. (2014). Hamming code based watermarking scheme for 3D model verification. Mathematical Problems in Engineering. https://doi.org/10.1155/2014/241093.
Wang, J. T., Fan, C. M., Huang, C. C., & Li, C. C. (2014). Error detecting code based fragile watermarking scheme for 3D models. In 2014 international symposium on computer, consumer and control (IS3C) (pp. 1099–1102). IEEE
Wang, J. T., Yang, W. H., Wang, P. C., & Chang, Y. T. (2014). A novel chaos sequence based 3d fragile watermarking scheme. In 2014 international symposium on computer, consumer and control (IS3C) (pp. 745–748). IEEE
Wang, J. T., Chang, Y. C., Lu, C. W., & Yu, S. S. (2016). An ofb-based fragile watermarking scheme for 3D polygonal meshes. In 2016 international symposium on computer, consumer and control (IS3C) (pp. 291–294). IEEE
Wang, K., Lavoué, G., Denis, F., & Baskurt, A. (2008a). A comprehensive survey on three-dimensional mesh watermarking. IEEE Transactions on Multimedia, 10(8), 1513–1527.
Wang, W. B., Zheng, G. Q., Yong, J. H., & Gu, H. J. (2008b). A numerically stable fragile watermarking scheme for authenticating 3d models. Computer-Aided Design, 40(5), 634–645.
Wang, Y. P., & Hu, S. M. (2009). A new watermarking method for 3d models based on integral invariants. IEEE Transactions on Visualization and Computer Graphics, 15(2), 285–294.
Werghi, N., Medimegh, N., & Gazzah, S. (2013). Data embedding of 3d triangular mesh models using ordered ring facets. In 2013 10th international multi-conference on systems, signals & devices (SSD) (pp. 1–6). IEEE
Wu, H. T., & Cheung, Y. M. (2005a). A fragile watermarking scheme for 3d meshes. In Proceedings of the 7th workshop on multimedia and security (pp. 117–124). ACM
Wu, H. T., & Cheung, Y. M. (2005b). A reversible data hiding approach to mesh authentication. In The 2005 IEEE/WIC/ACM international conference on web intelligence (WI’05) (pp 774–777). IEEE
Wu, H. T., & Cheung, Y. M. (2010). Reversible watermarking by modulation and security enhancement. IEEE Transactions on Instrumentation and Measurement, 59(1), 221–228.
Wu, H. T., & Dugelay, J. L. (2008). Reversible watermarking of 3D mesh models by prediction-error expansion. In 2008 IEEE 10th workshop on multimedia signal processing (pp. 797–802). IEEE
Xu, T., & Cai, Z. G. (2012). A novel semi-fragile watermarking algorithm for 3D mesh models. In 2012 international conference on control engineering and communication technology (ICCECT) (pp 782–785). IEEE
Yeo, B. L., & Yeung, M. M. (1999). Watermarking 3D objects for verification. IEEE Computer Graphics and Applications, 19(1), 36–45.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Borah, S., Borah, B. Watermarking Techniques for Three Dimensional (3D) Mesh Authentication in Spatial Domain. 3D Res 9, 43 (2018). https://doi.org/10.1007/s13319-018-0194-7
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s13319-018-0194-7