Abstract
Electronic medical record (EMR) is currently a popular topic in e-health. EMR includes the health-related information of patients and forms the main factor of e-health applications. Moreover, EMR contains the legal records that are created in the medical centre and ambulatory environments. These records serve as the data source for electronic health record. Although hospitals utilise the EMR system, healthcare professionals experience difficultly in trusting this system. Studies devoted to EMR acceptance in hospitals are lacking, particularly those on the EMR system in the contexts of privacy and security concerns based on multi-criteria perspective. Thus, the current study proposes a decision support examination framework on how individual, security and privacy determinants influence the acceptance and use of EMR. The proposed framework is based on a multi-criteria perspective derived from healthcare professionals in Malaysia as frame of reference. The framework comprises four phases. The sub-factors of individual, security and privacy determinants were investigated in the two initial phases. Thereafter, the sub-factors were identified with uniform multi-criteria perspective to establish a decision matrix. The decision matrix used individual uniform as basis to cluster the sub-factors and user perspectives. Subsequently, a new ‘multi-criteria decision-making (MCDM) approach’ was adopted. Integrated technique for order of preference by similarity (TOPSIS) and analytic hierarchy process (AHP) were used as bases in employing the MCDM approach to rank each group of factors. K-means clustering was also applied to identify the critical factors in each group. Healthcare professionals in Malaysia were selected as respondents and 100 questionnaires were distributed to those employed in 5 Malaysian public hospitals. A conceptual model adapted from Unified theory of acceptance and use of technology 2 (UTAUT2) was employed to clarify the connection between individual, privacy and security determinants and EMR system acceptance and use in the selected context. After collecting the data sets (363), structural equation modelling was used to analyse data related to EMR acceptance and use. Results are as follows. (1) Five determinants (i.e. data integrity, confidentiality, non-repudiation, facilitating conditions and effort expectancy) exerted an explicit and important positive effect on EMR acceptance and use. (2) Three determinants (i.e. unauthorised, error and secondary use) exerted a direct and significant negative effect on EMR acceptance and use. (3) Three other determinants (i.e. authentication, performance expectancy and habit) insignificantly affected the behavioural intention of healthcare experts in Malaysia to use EMR.








Similar content being viewed by others
References
Albahri OS, et al. Systematic Review of Real-time Remote Health Monitoring System in Triage and Priority-Based Sensor Technology: Taxonomy, Open Challenges Motivation and Recoomendatins. J Med Syst. 2018;42(5):80.
Zaidan BB, et al. A security framework for nationwide health information exchange based on telehealth strategy. J Med Syst. 2015;39(5):51.
Jawad MM, et al. An overview of laser principle, laser-tissue interaction mechanisms and laser safety precautions for medical laser users. Int J Pharmacol. 2011;7(2):149–60.
Kiah MLM, et al. MIRASS: medical informatics research activity support system using information mashup network. J Med Syst. 2014;38(4):37.
Potter LE, Purdie C, Nielsen S. The View from the Trenches: Satisfaction with eHealth systems by a group of health professionals. In ACIS 2012: Location, location, location: Proceedings of the 23rd Australasian Conference on Information Systems 2012, 2012. pp. 1–9.
Hussain M, et al. The landscape of research on smartphone medical apps: Coherent taxonomy, motivations, open challenges and recommendations. Comput Methods Prog Biomed. 2015;122(3):393–408.
Mishra R, Srivastava M, Upadhyay T, Farooqui NA. E-Health Information and its assesment. J Netw Commun Emerg Technol. 2016;6(5). www.jncet.org.
Li J, Land L, Ray P. Humanitarian Technology Challenge (HTC)-electronic health records perspective. A Rep. Jt. Proj. IEEE United Nations Found, 2008.
Zaidan AA, et al. Multi-criteria analysis for OS-EMR software selection problem: A comparative study. Decis Support Syst. 2015;78:15–27.
Kiah MLM, et al. Open source EMR software: Profiling, insights and hands-on analysis. Comput Methods Prog Biomed. 2014;117(2):360–82.
Al-qaysi ZT, et al. A review of disability EEG based wheelchair control system: Coherent taxonomy, open challenges and recommendations. Comput Methods Prog Biomed. 2018;164:221–37.
Naji AW, et al. Challenges of hidden data in the unused area two within executable files. J Comput Sci. 2009;5(11):890–7.
Zaidan AA, Zaidan BB. Novel approach for high secure data hidden in MPEG video using public key infrastructure. Int J Comput Netw Secur. 2009;1(1):1553–985.
Nabi MSA, et al. Suitability of using SOAP protocol to secure electronic medical record databases transmission. Int J Pharmacol. 2010;6(6):959–64.
Garets D, Mike D. Electronic Medical Records vs. Electronic Health Records: Yes, There Is a Difference By Dave Garets and Mike Davis Updated January 26, 2006 HIMSS Analytics, LLC 230 E. Ohio St., Suite 600 Chicago, IL 60611–3270 EMR vs. EHR: Definitions The marke. Heal. (San Fr., pp. 1–14, 2006.
Y. Y. Abdul-Talib et al. Optimizing security and flexibility by designing a high security system for e-government servers. ICOCI09, Univ. Utara Malaysia, 2009, pp. 355–358.
Yas QM, et al. A systematic review on smartphone skin cancer apps: coherent taxonomy, motivations, open challenges and recommendations, and new research direction. J Circuits, Syst Comput. 2018;27(05):1830003.
Alsalem MA, et al. Systematic Review of an Automated Multiclass Detection and Classification System for Acute Leukaemia in Terms of Evaluation and Benchmarking, Open Challenges, Issues and Methodological Aspects. J Med Syst. 2018;42(11):204.
Zaidan AA, et al. Challenges, Alternatives, and Paths to Sustainability: Better Public Health Promotion Using Social Networking Pages as Key Tools. J Med Syst. 2015;39(2):7.
Alsalem MA, et al. A review of the automated detection and classification of acute leukaemia: Coherent taxonomy, datasets, validation and performance measurements, motivation, open challenges and recommendations. Comput Methods Prog Biomed. 2018;158:93–112.
Hamada M, et al. A Systematic Review for Human EEG Brain Signals Based Emotion Classification, Feature Extraction, Brain Condition, Group Comparison. J Med Syst. 2018;42(9):162.
Othman F et al. An extensive empirical study for the impact of increasing data hidden on the images texture. In Proceedings - 2009 International Conference on Future Computer and Communication, ICFCC 2009, pp. 477–481. 2009.
Zaidan BB, et al. Quality of Image vs. Quantity of Data Hidden in the Image. IPCV. 2009;6:343–50.
Naji AW, Hameed SA, Al-khateeb WF, Khalifa OO, Gunawan TS. Novel Framework for Hidden Data in the Image Page within Executable File Using Computation between Advanced Encryption Standard and Distortion Techniques. Int J Comput Sci Inf Secur. 2009;3(1):1–6.
Naji AW, et al. Novel approach for cover file of hidden data in the unused area two within EXE file using distortion techniques and advance encryption standard. Proceeding World Acad Sci Eng Technol. 2010;56(5):498–502.
Ahlan AR, Ahmad BI. User Acceptance of Health Information Technology (HIT) in Developing Countries: A Conceptual Model. Procedia Technol. 2014;16:1287–96.
Abdulnabi M, et al. A distributed framework for health information exchange using smartphone technologies. J Biomed Inform. 2017;69:230–50.
Ali AH, et al. High capacity, transparent and secure audio steganography model based on fractal coding and chaotic map in temporal domain. Multimed Tools Appl. 2018;77(23):31487–516.
MLM K, et al. A review of audio based steganography and digital watermarking. Int J Phys Sci. 2011;6(16):3837–50.
A. Naji, T. Gunawan, … SH. IACSITSC’09, and undefined 2009, “" Stego-Analysis Chain, Session One" Investigations on Steganography Weakness vs Stego-Analysis System for Multimedia File,” ieeexplore.ieee.org. 2009.
Zaidan AA, et al. Novel approach for high (secure and rate) data hidden within triplex space for executable file (2010) eprints.um.edu.my
Jalab HA, et al. Frame Selected Approach for Hiding Data within MPEG Video Using Bit Plane Complexity Segmentation. J Comput. 2009;1(1):108–13.
Zaidan AA, et al. High securing cover-file of hidden data using statistical technique and AES encryption algorithm. World Acad Sci Eng Technol. 2009;54:463–74.
Ismail NIB, Abdullah NHB. Developing electronic medical records (EMR) framework for Malaysia’s public hospitals,” in Humanities, Science and Engineering (CHUSER), 2011 IEEE Colloquium on. 2011, pp. 131–136.
Mat Kiah ML, et al. An enhanced security solution for electronic medical records based on AES hybrid technique with SOAP/XML and SHA-1. J Med Syst. 2013;37(5):9971.
Hmood AK, et al. On the capacity and security of steganography approaches: An overview. J Appl Sci. 2010;10(16):1825–33.
Aos AZ, et al. Approved undetectable-antivirus steganography for multimedia information in PE-File. In 2009 International Association of Computer Science and Information Technology - Spring Conference, IACSIT-SC 2009, 2009, pp. 437–441.
Alanazi HO, et al. Meeting the security requirements of electronic medical records in the ERA of high-speed computing. J Med Syst. 2015;39(1):165.
Boonstra A, Broekhuis M. Barriers to the acceptance of electronic medical records by physicians from systematic review to taxonomy and interventions. BMC Health Serv Res. 2010;10(1):1.
Simon SR, et al. Physicians and electronic health records: a statewide survey. Arch Intern Med. 2007;167(5):507–12.
Hwang H-G, Han H-E, Kuo K-M, Liu C-F. The differing privacy concerns regarding exchanging electronic medical records of internet users in Taiwan. J Med Syst. 2012;36(6):3783–93.
Zaidan AA, et al. Novel multi-cover steganography using remote sensing image and general recursion neural cryptosystem (2010) academicjournals.org
Hussain M, et al. A security framework for mHealth apps on Android platform. Comput Secur. 2018;75:191–217.
Hmood AK, et al. On the accuracy of hiding information metrics: Counterfeit protection for education and important certificatesle. Int J Phys Sci. 2010;5(7):1054–62.
Islam R, et al. New system for secure cover file of hidden data in the image page within executable file using statistical steganography techniques. 2010.
Jalab HA, et al. New Design for Information Hiding with in Steganography Using Distortion Techniques. Int J Eng Technol. 2010;2(1):72–7.
Ahmed MA, et al. A Novel Embedding Method to Increase Capacity and Robustness of Low-bit Encoding Audio Steganography Technique Using Noise Gate Software Logic Algorithm. J Appl Sci. 2010;10(1):59–64.
Zaidan AA, et al. A survey on communication components for IoT-based technologies in smart homes. Telecommun Syst. 2018;69(1):1–25.
Zaidan BB, et al. StegoMos: A secure novel approach of high rate data hidden using mosaic image and ANN-BMP cryptosystem (2010) academicjournals.org.
Zaidan AA, et al. Investigate the capability of applying hidden data in text file: An overview. J Appl Sci. 2010;10(17):1916–22.
Al-Nabhani Y et al. A new system for hidden data within header space for EXE-file using object oriented technique. In Proceedings - 2010 3rd IEEE International Conference on Computer Science and Information Technology, ICCSIT 2010, 2010, 7:9–13.
Zaidan A et al. A new system for hiding data within (unused area two+ image page) of portable executable file using statistical technique and advance encryption (2010) ijcte.org.
Abdekhoda M, Ahmadi M, Gohari M, Noruzi A. The effects of organizational contextual factors on physicians’ attitude toward adoption of Electronic Medical Records. J Biomed Inform. 2015;53:174–9.
Asiri H, AlDosari B, Saddik B. Nurses’ attitude, acceptance and use of Electronic Medical Records (EMR) in King AbdulAziz Medical City (KAMC) in Riyadh, Saudi Arabia. Merit Res Journals. 2014;2(3):66–77.
Venkatesh V, Sykes TA, Zhang X. ‘Just what the doctor ordered’: a revised UTAUT for EMR system adoption and use by doctors. In System Sciences (HICSS), 2011 44th Hawaii International Conference on, 2011, pp. 1–10.
Arman AA, Hartati S. Development of user acceptance model for electronic medical record system. in Information Technology Systems and Innovation (ICITSI), 2015 International Conference on, 2015, pp. 1–6.
Nematollahi M, Moosavi A, Lazem M, Aslani N, Kafashi M, Garavand A. Factors affecting adoption and use of electronic medical record based on unified theory of acceptance and use of technology in Iran. Shiraz E-Med J. 2017.
Lin C, Lin I-C, Roan J. Barriers to physicians’ adoption of healthcare information technology: an empirical Study on multiple hospitals. J Med Syst. 2012;36(3):1965–77.
Baharom F, Khorma OT, Mohd H, Bashayreh MG. Developing an extended technology acceptance model: doctors’acceptance of electronic medical records in Jordan. ICOCI, 2011.
Al-Nassar BAY, Abdullah MS, Rozaini W, Osman S. Healthcare professionals use electronic medical records system (EMRs) in Jordan Hospitals. 2011;11:112–118.
Hsieh P-J. Physicians’ acceptance of electronic medical records exchange: An extension of the decomposed TPB model with institutional trust and perceived risk. Int. J. Med. Inform. 2014; 1–14.
Kim S, Lee K-H, Hwang H, Yoo S. Analysis of the factors influencing healthcare professionals’ adoption of mobile electronic medical record (EMR) using the unified theory of acceptance and use of technology (UTAUT) in a tertiary hospital. BMC Med Inform Decis Mak. 2015;16(1):12.
Noh M, Jang H, Khongorzul G. User Acceptance Model of Electronic Medical Record. Indian J Sci Technol. 2016;9(41).
Bensefia A, Zarrad A. A Proposed Layered Architecture to Maintain Privacy Issues in Electronic Medical Records. E-Health Telecommun Syst Networks. 2014;3(04):43.
Kuo K-M, Ma C-C, Alexander JW. How do patients respond to violation of their information privacy? Heal Inf Manag J. 2014;43(2):23–33.
V. Vathanophas and T. Pacharapha. Information technology acceptance in healthcare service: The study of electronic medical record (EMR) in Thailand. In PICMET 2010 Technology Management for Global Economic Growth, 2010; pp. 1–5.
Boonstra A, Versluis A, Vos JFJ. Implementing electronic health records in hospitals: a systematic literature review. BMC Health Serv Res. 2014;14(1):1.
Lakbala P, Dindarloo K. Physicians’ perception and attitude toward electronic medical record. Springerplus. 2014;3(1):1.
Najaftorkaman M, Ghapanchi AH, Talaei-Khoei A, Ray P. A taxonomy of antecedents to user adoption of health information systems: A synthesis of thirty years of research. J Assoc Inf Sci Technol. 2015;66(3):576–98.
Safadi H, Chan D, Dawes M, Roper M, Faraj S. Open-source health information technology: A case study of electronic medical records. Heal Policy Technol. 2015;4(1):14–28.
Mugo DM, Nzuki D. Determinants of electronic health in developing countries. 2014.
Ahmadi H, et al. Evaluating the critical factors for electronic medical record adoption using fuzzy approaches. Int J Innov Sci Res. 2014;9(2):268–84.
Nilashi M, Ahmadi H, Ahani A, Ibrahim O, Almaee A. Evaluating the Factors Affecting Adoption of Hospital Information System Using Analytic Hierarchy Process. J Soft Comput Decis Support Syst. 2015;3(1):8–35.
Ahmadi H, Osmani M, Nilashi M, Ibrahim O, Raisian K, Zakaria R. Ranking the Meso level critical factors of electronic medical records adoption using Fuzzy TOPSIS method. Int J Heal Phys Educ Comput Sci Sport. 2016;12(1):43–7.
Harman LB, Flite CA, Bond K. Electronic health records: privacy, confidentiality, and security. Virtual Mentor VM. 2012;14(9):712.
Burch TK. Demography in a new key: A theory of population theory. Demogr Res. 2003;9:263–84.
Ajzen I, Fishbein M. Belief, attitude, intention and behavior: An introduction to theory and research. Reading: Addison-Wesley; 1975.
Ajzen I. From intentions to actions: A theory of planned behavior. In: Action control: Springer; 1985. p. 11–39.
Kripanont N. Using a technology acceptance model to investigate academic acceptance of the internet. J Bus Syst Governance, Ethics. 2006;1(2):13–28.
Pelet J-E, Papadopoulou P. “Investigating the Effect of Color on Memorization and Trust in E-Learning: The Case of KMCMS. net,” Impact E-bus. Technol Public Priv Organ Ind Comp Perspect Ind Comp Perspect. 2011:52.
Wong W-T, Huang N-TN. The Effects of E-Learning System Service Quality and Users’ Acceptance on Organizational Learning. Int J Bus Inf, vol. 2011;2:6.
Venkatesh V, Morris MG, Davis GB, Davis FD. User acceptance of information technology: Toward a unified view. MIS Q. 2003:425–78.
Pahnila S, Siponen M, Zheng X. Integrating habit into UTAUT: the Chinese eBay case. Pacific Asia J Assoc Inf Syst. 2011;3(2).
Venkatesh V, Thong JYL, Xu X. Consumer acceptance and use of information technology: extending the unified theory of acceptance and use of technology. MIS Q. 2012;36(1):157–78.
Liu CF, Tsai YC, Jang FL. Patients’ acceptance towards a web-based personal health record system: An empirical study in Taiwan. Int J Environ Res Public Health. 2013;10(10):5191–208.
Taiwo AA, DOWNE AG. The theory of user acceptance and use of technology (UTAUT): A meta-analytic review of empirical findings. J Theor Appl Inf Technol. 2013;49(1).
Hassan IB, Murad MAA. Acceptance of Health Information Application in Smart National Identity Card (SNIC) Using a New IP Framework. World Acad Sci Eng Technol Int J Soc Behav Educ Econ Bus Ind Eng. 2014;8(12):3750–8.
Raman A, Don Y. Preservice teachers’ acceptance of learning management software: An Application of the UTAUT2 Model. Int Educ Stud. 2013;6(7):157.
Tavares J, Oliveira T. Electronic Health Record Patient Portal Adoption by Health Care Consumers: An Acceptance Model and Survey. J Med Internet Res. 2016;18(3).
Ahadzadeh AS, Sharif SP, Ong FS, Khong KW. Integrating health belief model and technology acceptance model: an investigation of health-related internet use. J Med Internet Res. 2015;17(2).
Tavares J, Goulão A, Oliveira T. Electronic Health Record Portals adoption: Empirical model based on UTAUT2. Informatics Heal Soc Care. 2018;43(2):109–25.
Rosli K, Yeow PHP, Siew E-G. Computer-Assisted Auditing Tools Acceptance Using I-Toe: A New Paradigm. Computer (Long Beach Calif). 2012;7:15–2012.
Ariaeinejad R, Archer N. Importance of Mobile Technology in Successful Adoption and Sustainability of a Chronic Disease Support System. Int J Soc Behav Educ Econ Bus Ind Eng. 2014;8:870–5.
Tavares J, Oliveira T, Electronic health record portal adoption by health care consumers-proposal of a new adoption model. In: WEBIST (1). 2014; 387–393.
Alazzam MB, Basari ASH, Sibghatullah AS, Doheir M, Enaizan OMA, Mamra AHK. Ehrs Acceptance in Jordan Hospitals By Utaut2 Model: Preliminary Result. J Theor Appl Inf Technol. 2015;78(3):473.
Lemire M, Paré G, Sicotte C, Harvey C. Determinants of Internet use as a preferred source of information on personal health. Int J Med Inform. 2008;77(11):723–34.
Wilson EV, Lankton NK. Modeling patients’ acceptance of provider-delivered e-health. J Am Med Inform Assoc. 2004;11(4):241–8.
Chang I-C, Hwang H-G, Hung W-F, Li Y-C. Physicians’ acceptance of pharmacokinetics-based clinical decision support systems. Expert Syst Appl. 2007;33(2):296–303.
Keselman A, Logan R, Smith CA, Leroy G, Zeng-Treitler Q. Developing informatics tools and strategies for consumer-centered health communication. J Am Med Inform Assoc. 2008;15(4):473–83.
Pai F-Y, Huang K-I. Applying the technology acceptance model to the introduction of healthcare information systems. Technol Forecast Soc Change. 2011;78(4):650–60.
Wu J-H, Shen W-S, Lin L-M, Greenes RA, Bates DW. Testing the technology acceptance model for evaluating healthcare professionals’ intention to use an adverse event reporting system. Int J Qual Health Care. 2008;20(2):123–9.
de Oliveira Rodrigues DEF, da C. de Lopes JÁ, and J. Tavares MSF. Manifold-Marketing: A new marketing archetype for the information age, applied to the adoption of oral contraceptives and other drugs by end-users. 2014.
Aggelidis VP, Chatzoglou PD. Using a modified technology acceptance model in hospitals. Int J Med Inform. 2009;78(2):115–26.
Enaizan OM, Alwi NH, Zaizi NJ. Privacy and Security Concern for Electronic Medical Record Acceptance and Use: State of the Art. J Adv Sci Eng Res Vol. 2017;7(2):23–34.
Mun YY, Jackson JD, Park JS, Probst JC. Understanding information technology acceptance by individual professionals: Toward an integrative view. Inf Manag. 2006;43(3):350–63.
Cocosila M, Archer N. Adoption of mobile ICT for health promotion: an empirical investigation. Electron Mark. 2010;20(3–4):241–50.
Ochieng OG, Hosoi R. Factors influencing diffusion of electronic medical records: a case study in three healthcare institutions in Japan. Heal Inf Manag. 2005;34(4):120–9.
Al-Nassar BAY, Abdullah MS, Osman WRS. Barriers for implementation of electronic medical record (EMR). In Proc. 4th International Conference on Information Technology, 2009.
W. Wilkowska and M. Ziefle. Perception of privacy and security for acceptance of E-health technologies: Exploratory analysis for diverse user groups. In 2011 5th International Conference on Pervasive Computing Technologies for Healthcare (PervasiveHealth) and Workshops, 2011, pp. 593–600.
Mugo DM, and Nzuki D. Determinants of electronic health in developing countries. Int. J. Arts Commer. 2014;3(3).
Salem Y, et al. A review on multimedia communications cryptography. Res J Inf Technol. 2011;3:146–52.
Hussain M, et al. Conceptual framework for the security of mobile health applications on Android platform. Telematics and Informatics, 2018.
Al-Bakri SH, et al. Securing peer-to-peer mobile communications using public key cryptography: New security strategy. International Journal of Physical Sciences. 2011;6(4):930–8.
Medani A, et al. Review of mobile short message service security issues and techniques towards the solution. Sci Res Essays. 2011;6(6):1147–65.
Zaidan BB, et al. Impact of data privacy and confidentiality on developing telemedicine applications: A review participates opinion and expert concerns. Int J Pharmacol. 2011;7(3):382–7.
Abomhara M, et al. An experiment of scalable video security solution using H. 264/AVC and advanced encryption standard (AES): Selective cryptography. International Journal of the Physical Sciences. 2011;6(16):4053–63.
Naji AW, et al. Security improvement of credit card online purchasing system. Sci Res Essays. 2011;6(16):3357–70.
Watari MA, et al. Securing m-Government Transmission Based on Symmetric and Asymmetric Algorithms: A review. Asian Journal of Scientific Ressearch. 2013;8:80–94.
Abomhara M, et al. Suitability of Using Symmetric Key to Secure Multimedia Data: An Overview. Journal of Applied Sciences(Faisalabad). 2010;10(15):1656–61.
Alam GM, et al. Using the features of mosaic image and AES cryptosystem to implement an extremely high rate and high secure data hidden: Analytical study. Sci Res Essays. 2010;5(21):3254–60.
Zaidan AA, et al. Securing cover-file without limitation of hidden data size using computation between cryptography and steganography. In Proceedings of the World Congress on Engineering (Vol. 1, pp. 1–7), 2009.
Alanazi HO, et al. Secure topology for electronic medical record transmissions. Int J Pharmacol. 2010;6(6):954–8.
Zaidan BB, Zaidan AA, Taqa A, Othman F. Stego-image vs stego-analysis system. International Journal of Computer and Electrical Engineering. 2009;1(5):572.
Naji AW, Zaidan AA, Zaidan BB, Muhamadi IA. New approach of hidden data in the portable executable file without change the size of carrier file using distortion techniques. Proceeding of World Academy of Science Engineering and Technology (WASET). 2009;56:493–7.
Alanazi H, Noor RM, Zaidan BB, and Zaidan AA. Intrusion detection system: overview. arXiv preprint arXiv:1002.4047. 2010.
Khalifa OO, Naji AW, Zaidan AA, Zaidan BB, Hameed SA. Novel approach of hidden data in the (unused area 2 within EXE file) using computation between cryptography and steganography. International Journal of Computer Science and Network Security (IJCSNS). 2010;9(5):294–300.
Zaidan BB, Zaidan AA, Othman F. Enhancement of the amount of hidden data and the quality of image. Faculty of Computer Science and Information Technology. Kuala Lumpur: University of Malaya; 2008.
Hamdan A, Jalab HA, Zaidan AA, Zaidan BB. New frame work of hidden data with in non multimedia file. Int J Comput Netw Secur. 2010;2(1):46–54.
Naji AW, Hameed SA, Islam MR, Zaidan BB, Gunawan TS, and Zaidan AA. Stego-analysis chain, session two novel approach of stego-analysis system for image file. In Computer Science and Information Technology-Spring Conference, 2009. IACSITSC'09. International Association of (pp. 410–413). IEEE. 2009.
Abdullateef BN, Elias NF, Mohamed H, Zaidan AA, and ZaidaN B. rStudy on open source learning management systems: a survey, profile, and taxonomy. Journal of Theoretical & Applied Information Technology. 2015; 82(1).
Zaidan BB, Zaidan AA, Taqa AY, and Othman F. An empirical study for impact of the increment the size of hidden data on the image texture. ICFCC09, 2009.
Lhotska L, Prague C, and Aubrecht P. Deliverable D09 security of the multi agent system. Agent Syst. 2008.
Arenas A, Banâtre J-P, and Priol T. Developing secure chemical programs with aspects. 2008.
Aich D. Secure query processing by blocking sql injection. National Institute of Technology Rourkela, 2009.
Sattarova Feruza Y, Kim T. IT security review: Privacy, protection, access control, assurance and system security. Int J Multimed ubiquitous Eng. 2007;2(2):17–32.
Pappas JA. A revitalized information assurance training approach and information assurance best practice rule set. Monterey: Naval Postgraduate School; 2008.
Elnajjar M, Zaidan AA, Zaidan BB, Sharif MEM, and Alanazi H. Optimization digital image watermarking technique for patent protection. arXiv preprint arXiv:1002.4049. 2010.
Smith GW, and Newton RB. A taxonomy of organisational security policies. In Proccedings of the 23rd National Information Systems Security Conference. NIST-National Institute of Standards and Technology, 2000.
Taute B. DST-funded information security centre of competence. 2009.
Zhang R, and Liu L. Security models and requirements for healthcare application clouds. In 2010 IEEE 3rd International Conference on Cloud Computing, 2010, pp. 268–275.
Hwang J, and Syamsuddin I. Information security policy decision making: an analytic hierarchy process approach. in 2009 Third Asia International Conference on Modelling & Simulation, 2009, pp. 158–163.
Hussain M, et al. The rise of keyloggers on smartphones: A survey and insight into motion-based tap inference attacks. Pervasive and Mobile Computing. 2016;25:1–25.
Andriole KP. Security of electronic medical information and patient privacy: What you need to know. J Am Coll Radiol. 2014;11(12):1212–6.
Nabi MS, et al. Suitability of adopting S/MIME and OpenPGP email messages protocol to secure electronic medical records. In Future Generation Communication Technology (FGCT), 2013 Second International Conference on (pp. 93–97). IEEE. 2013.
Hong W, Thong JYL. Internet privacy concerns: an integrated conceptualization and four empirical studies. MIS Q. 2013;37(1):275–98.
Barrows RC, Clayton PD. Privacy, confidentiality, and electronic medical records. J Am Med Inform Assoc. 1996;3(2):139–48.
Donaldson MS, Lohr KN. Health data in the information age: use, disclosure, and privacy. Washington, DC: National Academies Press; 1994.
Smith HJ, Milberg SJ, Burke SJ. Information privacy: measuring individuals’ concerns about organizational practices. MIS Q. 1996; 167–196.
Milberg SJ, Smith HJ, Burke SJ. Information privacy: Corporate management and national regulation. Organ Sci. 2000;11(1):35–57.
N. R. Council. For the record protecting electronic health information. 1997.
Stone EF, Gueutal HG, Gardner DG, McClure S. A field experiment comparing information-privacy values, beliefs, and attitudes across several types of organizations. J Appl Psychol. 1983;68(3):459.
Stewart KA, Segars AH. An empirical examination of the concern for information privacy instrument. Inf Syst Res. 2002;13(1):36–49.
Gostin LO, Turek-Brezina J, Powers M, Kozloff R, Faden R, Steinauer DD. Privacy and security of personal information in a new health care system. JAMA. 1993;270(20):2487–93.
Sheehan KB, Hoy MG. Dimensions of privacy concern among online consumers. J Public Policy Mark. 2000;19(1):62–73.
Nowak GJ, Phelps J. Direct marketing and the use of individual-level consumer information: Determining how and when ‘privacy’ matters. J Direct Mark. 1995;9(3):46–60.
Thomas CM, McIntosh CE, and Mensik JS, A nurse’s step-by-step guide to transitioning to the professional nurse role. Sigma Theta Tau, 2015.
Mitchell P, et al. Core principles & values of effective team-based health care. Washington, DC Inst. Med. 2012.
Reddy MC, Shabot MM, Bradner E. Evaluating collaborative features of critical care systems: a methodological study of information technology in surgical intensive care units. J Biomed Inform. 2008;41(3):479–87.
Ismail NI, Abdullah NH. Implementation and acceptance of hospital information system. 2013.
Zaidan AA, et al. A review on smartphone skin cancer diagnosis apps in evaluation and benchmarking: coherent taxonomy, open issues and recommendation pathway solution. Health Technol. (Berl). 2018.
Zaidan AA, et al. Evaluation and selection of open-source EMR software packages based on integrated AHP and TOPSIS. J Biomed Inform. 2015;53:390–404.
Triantaphyllou E, Shu B, Sanchez SN, Ray T. Multi-criteria decision making: an operations research approach. Encycl Electr Electron Eng. 1998;15(1998):175–86.
Kalid N, et al. Based Real Time Remote Health Monitoring Systems: A Review on Patients Prioritization and Related ‘Big Data’ Using Body Sensors information and Communication Technology. J Med Syst. 2018;42(2):30.
Yas QM, et al. Towards on Develop a Framework for the Evaluation and Benchmarking of Skin Detectors Based on Artificial Intelligent Models Using Multi-Criteria Decision-Making Techniques. Int J Pattern Recognit Artif Intell. 2017;31(03):1759002.
Zaidan BB, Zaidan AA. Comparative study on the evaluation and benchmarking information hiding approaches based multi-measurement analysis using TOPSIS method with different normalisation, separation and context techniques. Meas J Int Meas Confed. 2018;117:277–94.
Abdullateef BN, et al. An evaluation and selection problems of OSS-LMS packages. SpringerPlus. 2016;5(1):1–35.
Zaidan BB, et al. A new digital watermarking evaluation and benchmarking methodology using an external group of evaluators and multi-criteria analysis based on ‘large-scale data,’. Softw - Pract Exp. 2017;47(10):1365–92.
Mansooreh M, Pet-Edwards J. Technical briefing: making multiple-objective decisions. In: Inst. Electr. Ve electron. Eng. Inc., IEEE Comput. Soc. Press, USA; 1997.
Yas QM, et al. Comprehensive {Insights} into {Evaluation} and {Benchmarking} of {Real}-time {Skin} {Detectors}: {Review}, {Open} {Issues} & {Challenges}, and {Recommended} {Solutions}. Measurement. 2017.
Mat Kiah ML, et al. Design and Develop a Video Conferencing Framework for Real-Time Telemedicine Applications Using Secure Group-Based Communication Architecture. J Med Syst. 2014;38(10):133.
Zaidan AA, et al. Image skin segmentation based on multi-agent learning Bayesian and neural network. Eng Appl Artif Intell. 2014;32:136–50.
ZAIDAN AA, et al. an Automated Anti-Pornography System Using a Skin Detector Based on Artificial Intelligence: a Review. Int J Pattern Recognit Artif Intell. 2013;27(04):1350012.
Saaty TL, Ozdemir MS. Why the magic number seven plus or minus two. Math Comput Model. 2003;38(3–4):233–44.
Mohsin AH, et al. Real-Time Remote Health Monitoring Systems Using Body Sensor Information and Finger Vein Biometric Verification: A Multi-Layer Systematic Review. J Med Syst. 2018;42(12):238.
Albahri OS, et al. Real-Time Remote Health-Monitoring Systems in a Medical Centre: A Review of the Provision of Healthcare Services-Based Body Sensor Information Open Challenges and Methodological Aspects. J Med Syst. 2018;42(9):164.
Albahri AS, et al. Real-Time Fault-Tolerant mHealth System: Comprehensive Review of Healthcare Services, Opens Issues, Challenges and Methodological Aspects. J Med Syst. Aug. 2018;42(8):137.
Iqbal S, et al. Real-time-based E-health systems: design and implementation of a lightweight key management protocol for securing sensitive information of patients. Health Technol. (Berl). 2018.
Zaidan AA, et al. A review on intelligent process for smart home applications based on IoT: coherent taxonomy, motivation, open challenges, and recommendations. Artificial Intelligence Review, Springer Netherlands, pp. 1–25, 2018.
Nidhal S, et al. Computerized algorithm for fetal heart rate baseline and baseline variability estimation based on distance between signal average and alpha value. Int J Pharmacol. 2011;7(2):228–37.
Kalid N, et al. Based on Real Time Remote Health Monitoring Systems: A New Approach for Prioritization ‘Large Scales Data’ Patients with Chronic Heart Diseases Using Body Sensors and Communication Technology. J Med Syst. 2018;42(4):69.
Ahmadi H, Rad MS, Almaee A, Nilashi M, Ibrahim O, Mohamed H. Ranking the Macro-Level Critical Success Factors of Electronic Medical Record Adoption using Fuzzy AHP Method. International Journal of Innovation and Scientific Research. 2014;8(1):35–42.
Ahmadi H, Rad MS, Nilashi M, Ibrahim O, and Almaee A. Ranking the micro level critical factors of electronic medical records adoption using TOPSIS method,” Heal. Informatics. 2013; 4(2).
Krejcie RV, Morgan DW. Determining sample size for research activities. Educ Psychol Meas. 1970;30(3):607–10.
Sekaran U, Bougie R. Research methods for business: a skill building approach. Chichester: John Wiley & Sons; 2016.
Hair JF, Anderson RE, Babin BJ, Black WC. Multivariate data analysis: A global perspective, vol. 7. Upper Saddle River: Pearson; 2010.
Ho R. Handbook of univariate and multivariate data analysis and interpretation with SPSS. Boca Raton: Chapman and Hall/CRC; 2006
Hair JF, Black B, Babin B, Anderson RE, Tatham RL. Multivariate data analysis, 6. Baskı. Up. Saddle River: Pearson Prentice Hall; 2014
Hambrick DC, Finkelstein S, Cho TS, Jackson EM. Isomorphism Reverse Institutional Theory as an Explan. Recent Increases Intraindustry Heterog Manag. 2004;26:307–50
Fraser H, Biondich P, Moodley D, Choi S, Mamlin B, Szolovits P. Implementing electronic medical record systems in developing countries. J Innov Heal Informatics. 2005;13(2):83–95.
Omary Z, Lupiana D, Mtenzi F, Wu B. Challenges to E-healthcare adoption in developing countries: A case study of Tanzania. In 2009 First International Conference on Networked Digital Technologies, 2009, pp. 201–209.
Kifle M, Mbarika V, and Brandy R. The diffusion of telemedicine in Ethiopia: Potential benefits, present challenges, and potential factors. Commun. Assoc. Inf. Syst. 2006.
Mansouri-Rad P, Mahmood MA, Thompson SE, and Putnam K. Culture matters: factors affecting the adoption of telemedicine. In System Sciences (HICSS), 2013 46th Hawaii International Conference on, 2013, pp. 2515–2524.
Hesson M, Al-Ameed H. Online security evaluation process for new e-services. Bus Process Manag J. 2007;13(2):223–46.
Taherdoost H, Sahibuddin S, Ibrahim S, Kalantari A, Jalaliyoon N, Ameri S. Examination of electronic service definitions international conference on advanced computer science applications and technologies (ACSAT). Kuala Lumpur: IEEE; 2012. p. 73–7.
Zendehdel M, Paim L, Bojei J, Osman S. The effects of trust on online Malaysian students buying behavior. Aust J Basic Appl Sci. 2011;5(12):1125–32.
Ho SY, Chau PYK. The effects of location personalization on integrity trust and integrity distrust in mobile merchants. Int J Electron Commer. 2013;17(4):39–72.
Looi HC. E-commerce adoption in Brunei Darussalam: A quantitative analysis of factors influencing its adoption. Commun Assoc Inf Syst. 2005;15(1):3.
Wafa SA. The effect of perceived risk on the intention to use e-commerce: The case of Algeria. J. Internet Bank. Commer. 2009;14(1).
Eslami SG, Peiravi A, and Molavi B. A survey on factors affecting Iran’s fuel rationing smart card user acceptance and security. arXiv Prepr. arXiv1402.0945, 2014.
Han JS, Kurnia S, Peng F. The impact of two-factor authentication technology on the adoption of internet banking. In PACIS, 2010, p. 146.
Malhotra NK, Kim SS, Agarwal J. Internet users’ information privacy concerns (IUIPC): The construct, the scale and a casual model. Inf Syst Res. 2004;15(4):336–55.
Van Slyke C, Shim JT, Johnson R, and Jiang JJ. Concern for information privacy and online consumer purchasing. 2006.
Angst CM, Agarwal R. Adoption of electronic health records in the presence of privacy concerns: The elaboration likelihood model and individual persuasion. MIS Q. 2009;33(2):339–70.
Detmer DE, Steen EB, Dick RS. The computer-based patient record: an essential technology for health care. Washington, DC: National Academies Press; 1997.
Hunt DL, Haynes RB, Hanna SE, Smith K. Effects of computer-based clinical decision support systems on physician performance and patient outcomes: a systematic review. Jama. 1998;280(15):1339–46.
Walter Z, Lopez MS. Physician acceptance of information technologies: Role of perceived threat to professional autonomy. Decis Support Syst. 2008;46(1):206–15.
Wills MJ, El-Gayar OF, Bennett D. Examining healthcare professionals’ acceptance of electronic medical records using UTAUT. Issues Inf Syst. 2008;9(2):396–401.
Venkatesh V, Zhang X. Unified theory of acceptance and use of technology: US vs. China. J Glob Inf Technol Manag. 2010;13(1):5–27.
Mohsin AH, et al. Real-time Medical Systems based on Human Biometric Steganography: A Systematic Review. J Med Syst. 2018;42(12).
Jumaah FM, et al. Decision-making solution based multi-measurement design parameter for optimization of GPS receiver tracking channels in static and dynamic real-time positioning multipath environment. Meas J Int Meas Confed. 2018;118:83–95.
Salman OH, et al. Novel Methodology for Triage and Prioritizing Using ‘Big Data’ Patients with Chronic Heart Diseases Through Telemedicine Environmental. Int J Inf Technol Decis Mak. 2017;16(05):1211–45.
Rahmatullah B, et al. Multi-complex attributes analysis for optimum GPS baseband receiver tracking channels selection. In 2017 4th International Conference on Control, Decision and Information Technologies, CoDIT 2017, 2017, vol. 2017, pp. 1084–1088.
Jumaah FM, et al. Technique for order performance by similarity to ideal solution for solving complex situations in multi-criteria optimization of the tracking channels of GPS baseband telecommunication receivers. Telecommun Syst. 2018;68(3):425–43.
Qader MA, et al. A methodology for football players selection problem based on multi-measurements criteria analysis. Meas J Int Meas Confed. 2017;111:38–50.
Zaidan BB, Zaidan AA. Software and Hardware FPGA-Based Digital Watermarking and Steganography Approaches: Toward New Methodology for Evaluation and Benchmarking Using Multi-Criteria Decision-Making Techniques. J Circuits, Syst Comput. 2017;26(07):1750116.
Tariq I, et al. MOGSABAT: a metaheuristic hybrid algorithm for solving multi-objective optimisation problems. Neural Comput. Appl. 2018.
Zaidan BB, et al. A new approach based on multi-dimensional evaluation and benchmarking for data hiding techniques. Int. J. Inf. Technol. Decis. Mak. 2017; 1–42.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare no conflict of interest.
Ethical approval
All procedures performed in studies involving human participants were in accordance with the ethical standards of the institutional or national research committee and with the 1964 Helsinki declaration and its later amendments or comparable ethical standards.
Informed consent
Informed consent was obtained from all participants of the study.
Additional information
Highlights
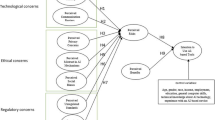
• Identify the privacy, security, and individual factors that could effect on acceptance and use of an EMR system in Malaysian public hospitals.
• Established a decision matrix incorporating the sub-factors and multi- criteria perspectives.
• Utilized decision-making technique based on performed decision matrix to rank each group of factors.
• Applied the K-mean clustering in order to identify the critical factors in each group.
• SEM was used to analyze data related to examine the influence of factors on EMR acceptance and use.
Appendix
Appendix
1.1 Questionnaire
Authentication
EMR ensures that the patients’ information I send is transmitted to the right health care staff member, to whom I want to transmit it to.
EMR ensures that the patients’ information I receive are transmitted from the right health care staff member, to whom I want to receive it.
EMR ascertains my identity before sending any patients’ information to me.
EMR ascertains my identity before processing patients’ information received from me.
Nonrepudiation
EMR ensures that other healthcare staff will not deny having participated in patient information after processing it.
EMR ensures that other healthcare staff will not deny having sent me patient information.
EMR ensures that other healthcare staff will not deny having received patients’ information from me.
EMR ensures that other healthcare staff provide me some evidence to protect from the denial of having sent the patient information.
EMR ensures that other healthcare staff provides me some evidence to protect from the denial of having received the patient information.
Confidentiality
EMR ensures that all communications of EMR system are restricted to all authorized healthcare staff.
I am convinced that the received information will be treated with respect and confidentiality by other healthcare staff.
EMR uses some security controls (e.g. firewall) for the confidentiality of patient information.
EMR checks all communications between me and the other healthcare staff are protected against wiretapping or eavesdropping.
Data Integrity
EMR checks the patient’s information communicated with me for accuracy.
EMR takes steps to make sure that the transmission of the patient information is accurate.
EMR takes steps to make sure that the transmitted information of the patient information is not deleted.
EMR devotes time and effort to verify the accuracy of the patient information in transit process.
EMR system devotes time and effort to verify that the patient information in transit process is not deleted or tampered.
Availability
The probability of patient information system breakdown and information service disruption in my hospital is low.
A legitimate user with medical needs can access hospital patient information at any time and place.
The hospital ensures that a backup exists to tolerate hardware failure.
All servers should be continuously available to patients.
Trust
The hospital’s EMR system is trustworthy.
I trust in the benefits that came from the hospital’s EMR.
The hospital’s EMR system keeps its promises.
The hospital’s EMR keeps health care staff’s best interests in mind.
Even if not monitored I would trust the hospital EMR system to do job right.
I would use EMR than the traditional way of collecting patients’ information.
Implementing EMR system is the right policy of the hospital.
Collection
It usually bothers me when hospital asks for patient information.
When hospital asks patients for personal information, I sometimes think twice before recording it.
It bothers to give the patients’ information to other health care companies.
I’m concerned that hospital is collecting excessive information about patients.
Secondary use
A hospital should not use patient information for any purpose unless it has been authorised by the patient who provided the information.
When a patient gives personal information to a hospital for a particular reason, the hospital should never use that information for any other reason.
Hospital should never sell any of the patient information to third party.
Hospital should never share the patient information with other companies unless they gain approval from the patients to do so.
Unauthorised access
Hospital should devote additional time and effort to prevent unauthorised access to personal information.
Computer databases that contain patient information should be protected from unauthorised access – no matter how much it costs.
Hospital should take more steps to make sure that unauthorised people cannot access any of the patient information in its computers.
Error
All the patient information in computer databases should be verified for accuracy—no matter how much this costs.
Hospital should take additional steps to make sure that the information in the patients’ files is accurate.
Hospital should have improved procedures to correct errors in patient information.
Hospital should devote additional time and effort to verifying the accuracy of the patient information in its databases.
Effort Expectancy
The EMR can be used easily.
Learning to use the EMR is easy.
The process for using EMR is clear.
Using EMR system is not burden during the transition.
The hospital is self-solving when an error occurs.
Performance Expectancy
EMR accelerates the healthcare process.
The EMR enhances staff’s performance.
The EMR enhances the efficiency of your service.
The EMR enhances the accessibility and communication with the patient.
Social Influence
Your colleagues expect that your service improves via EMR system.
Your colleagues expect that you can use the EMR system efficiently.
The patient believes that the EMR system is very useful for your organisation.
The hospital supports training and attending seminars to increase their knowledge of EMR.
Facilitating Conditions
The hospital gives importance to service driven by EMR technology.
The hospital always improves and upgrades their EMR.
The hospital provides me with the required tools to use EMR.
The hospital supports training for new staff by a professional trainer.
The hospital provides the training for healthcare professionals whenever there is important system/technology.
Hedonic Motivation
Using EMR system makes your job fun.
Using EMR system makes your job enjoyable.
Using EMR system is very entertaining.
Time passes fast when using EMR system.
Habit
The use of EMR system has become a habit for me.
I always use EMR system.
I must use EMR system.
Using EMR has become natural to me.
Behavioural Intention
I want to use new technology to serve the patients.
I intend to continue using EMR system in the future.
I will try to use EMR system in my daily life.
I plan to continue using EMR system frequently.
Rights and permissions
About this article
Cite this article
Enaizan, O., Zaidan, A.A., Alwi, N.H.M. et al. Electronic medical record systems: decision support examination framework for individual, security and privacy concerns using multi-perspective analysis. Health Technol. 10, 795–822 (2020). https://doi.org/10.1007/s12553-018-0278-7
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12553-018-0278-7