Abstract
Identifying and locating-dominating codes have been studied widely in circulant graphs of type \(C_{n}(1,2,3,\dots , r)\) over the recent years. In 2013, Ghebleh and Niepel studied locating-dominating and identifying codes in the circulant graphs \(C_{n}(1,d)\) for \(d = 3\) and proposed as an open question the case of \(d > 3\). In this paper we study identifying, locating-dominating and self-identifying codes in the graphs \(C_{n}(1,d)\), \(C_{n}(1,d-1,d)\) and \(C_{n}(1,d-1,d,d + 1)\). We give a new method to study lower bounds for these three codes in the circulant graphs using suitable grids. Moreover, we show that these bounds are attained for infinitely many parameters n and d. In addition, new approaches are provided which give the exact values for the optimal self-identifying codes in \(C_{n}(1,3)\) and \(C_{n}(1,4)\).






Similar content being viewed by others
References
Ben-Haim, Y., Litsyn, S.: Exact minimum density of codes identifying vertices in the square grid. SIAM J. Discret. Math. 19(1), 69–82 (2005)
Bertrand, N., Charon, I., Hudry, O., Lobstein, A.: Identifying and locating-dominating codes on chains and cycles. Eur. J. Comb. 25(7), 969–987 (2004)
Charon, I., Hudry, O., Lobstein, A.: Identifying codes with small radius in some infinite regular graphs. Electron. J. Combin. 9(1), Research Paper 11 (2002)
Chen, C., Lu, C., Miao, Z.: Identifying codes and locating-dominating sets on paths and cycles. Discret. Appl. Math. 159(15), 1540–1547 (2011)
Cohen, G., Gravier, S., Honkala, I., Lobstein, A., Mollard, M., Payan, C., Zémor, G.: Improved identifying codes for the grid. Electron. J. Combin. 6, Research Paper 19, Comment (1999)
Cohen, G., Honkala, I., Lobstein, A., Zémor, G.: On codes identifying vertices in the two-dimensional square lattice with diagonals. IEEE Trans. Comput. 50 (2), 174–176 (2001)
Exoo, G., Junnila, V., Laihonen, T.: Locating-dominating codes in cycles. Australas. J. Combin. 49, 177–194 (2011)
Ghebleh, M., Niepel, L.: Locating and identifying codes in circulant networks. Discret. Appl. Math. 161(13-14), 2001–2007 (2013)
Gravier, S., Moncel, J., Semri, A.: Identifying codes of cycles. Eur. J. Comb. 27(5), 767–776 (2006)
Honkala, I.: An optimal locating-dominating set in the infinite triangular grid. Discret. Math. 306(21), 2670–2681 (2006)
Honkala, I., Laihonen, T.: On locating-dominating sets in infinite grids. Eur. J. Comb. 27(2), 218–227 (2006)
Honkala, I., Laihonen, T.: On a new class of identifying codes in graphs. Inform. Process. Lett. 102(2-3), 92–98 (2007)
Junnila, V., Laihonen, T.: Optimal identifying codes in cycles and paths. Graphs Combin. 28(4), 469–481 (2012)
Junnila, V., Laihonen, T.: Collection of codes for tolerant location. In: Proceedings of the Bordeaux Graph Workshop, pp. 176–179 (2016)
Junnila, V., Laihonen, T.: Tolerant location detection in sensor networks. Submitted (2016)
Junnila, V., Laihonen, T., Paris, G.: Solving two conjectures regarding codes for location in circulant graphs. Submitted (2017)
Karpovsky, M.G., Chakrabarty, K., Levitin, L.B.: On a new class of codes for identifying vertices in graphs. IEEE Trans. Inform. Theory 44(2), 599–611 (1998)
Manuel, P.: Locating and liar domination of circulant networks. Ars Combin. 101, 309–320 (2011)
Rall, D.F., Slater, P.J.: On location-domination numbers for certain classes of graphs. Congr. Numer. 45, 97–106 (1984)
Roberts, D.L., Roberts, F.S.: Locating sensors in paths and cycles: The case of 2-identifying codes. Eur. J. Comb. 29(1), 72–82 (2008)
Slater, P.J.: Domination and location in acyclic graphs. Networks 17(1), 55–64 (1987)
Slater, P.J.: Dominating and reference sets in a graph. J. Math. Phys. Sci. 22, 445–455 (1988)
Slater, P.J.: Fault-tolerant locating-dominating sets. Discret. Math. 249(1–3), 179–189 (2002)
Xu, M., Thulasiraman, K., Hu, X.-D.: Identifying codes of cycles with odd orders. Eur. J. Comb. 29(7), 1717–1720 (2008)
Acknowledgements
We would like to thank the referees for their suggestions which improved the presentation of the paper.
Author information
Authors and Affiliations
Corresponding author
Additional information
Research of Gabrielle Paris has been supported by the ANR-14-CE25-0006 project of the French National Research Agency.
Appendix
Appendix
The proof of the Theorem 10(ii):
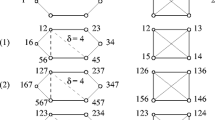
Let \(d\ge 15\), \(d\equiv 3 \pmod {6}\) and \(n = 3d-9\). Notice that \(n\equiv 0 \pmod {6}\). We divide the vertices of the circulant graph into three sections denoted by \(A_{1}=\{0,1,2\dots , d-1\}\), \(A_{2}=\{d,d + 1,\dots , 2d-1\}\) and \(A_{3}=\{0,1,\dots ,n-1\}\setminus (A_{1}\cup A_{2})\). We will first consider the code
Using this code we can construct (by adding later two more codewords) an identifying code in \(C_{n}(1,d-1,d,d + 1)\). The ratio \(|C_{d}|/n\) tends to \(2/9\) as d tends to infinity. First we exclude some ‘borderline’ vertices from the three sections and denote \(A_{1}^{\prime }=A_{1}\setminus \{0,1,2,3,4,5,6,7,8,9,d-1\}\), \(A_{2}^{\prime }=A_{2}\setminus \{d,2d-1\}\) and \(A_{3}^{\prime }=A_{3}\setminus \{2d\}\). We consider the borderline vertices later. It is straightforward to check that the I-sets with regard to the code \(C_{d}\) are as follows for \(x\in A_{1}^{\prime }\cup A_{2}^{\prime }\cup A_{3}^{\prime }\):



Let us compare these I-sets (that is, when \(x\in A_{1}^{\prime }\cup A_{2}^{\prime }\cup A_{3}^{\prime }\)). Clearly, the I-sets of size one are distinguished. Consider then the I-sets of size two. In the tables above, one can found the distances \(c_{1}-c_{2}\) of the codewords in \(I(x)\) with \(c_{1}>c_{2}\). If the distance is different, the I-sets cannot be the same. For those, which have the same distance, the \(c_{1} \pmod {6}\) and \(c_{2} \pmod {6}\) are different as shown in the table, and the I-sets again cannot be the same. Let us study the I-sets of size three then. According to the tables, the codewords in the I-sets are different modulo 6 unless \(x\in A_{1}^{\prime }\) where \(x\equiv 2 \pmod 6\) and \(y\in A_{3}^{\prime }\) where \(y\equiv 2\pmod {6}\). However, now \(I(y)\) has distance 2 between its two largest codewords, but \(I(x)\) has corresponding distance \(d-10\). Consequently, I(x)≠I(y).
For the rest of the vertices (i.e., the borderline vertices \(x\notin A_{1}^{\prime }\cup A_{2}^{\prime }\cup A_{3}^{\prime }\)) we get the following I-sets: \(I(0)=\{d + 1,2d-8,3d-10\}\), I(1) = {d + 1, 2d − 8}, \(I(2)=\{d + 1,d + 3,2d-8,2d-6\}\), \(I(3)=\{d + 3,2d-6\}\), \(I(4)=\{5,d + 3,2d-6\}\), \(I(5)=\{5\}\), \(I(6)=\{5,d + 7,2d-2\}\), \(I(7)=\{d + 7,2d-2\}\), \(I(8)=\{d + 7,d + 9,2d-2\}\), I(9) = {d + 9}, \(I(d-1)=\{2d-2,3d-10\},\)\(I(d)=\{d + 1,3d-10\}\), \(I(2d-1)=\{2d-2\}\) and \(I(2d)=\{d + 1\}\). It is straightforward to check (considering sizes of I-sets, codewords modulo 6 in I-sets and their distances) that we have exactly the following non-distinguished I-sets: \(I(9)=I(d + 9)\), \(I(d-1)=I(d-2)\), \(I(d + 1)=I(2d)\) and \(I(2d-2)=I(2d-1)\). We add two more codewords, namely, 0 and \(2d\) to the code \(C_{d}\) to avoid these same I-sets. Denote \(C_{d}^{\prime }=C_{d}\cup \{0,2d\}\). We should bear in mind that if \(I(C_{d};x)\neq I(C_{d};y)\), then also \(I(C_{d}^{\prime };x)\neq I(C_{d}^{\prime };y)\). Now we have (with respect to \(C_{d}^{\prime }\)) that \(2d\in I(9)\setminus I(d + 9)\), \(0\in I(d-1)\setminus I(d-2)\), 2d ∈ I(2d − 1) ∖ I(2d − 2) and \(0\in I(d + 1)\setminus I(2d)\). Therefore, \(C_{d}^{\prime }\) is an identifying code and the proof is completed.
Rights and permissions
About this article
Cite this article
Junnila, V., Laihonen, T. & Paris, G. Optimal bounds on codes for location in circulant graphs. Cryptogr. Commun. 11, 621–640 (2019). https://doi.org/10.1007/s12095-018-0316-3
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12095-018-0316-3