Abstract
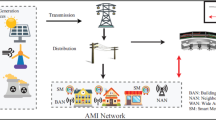
Cyber security has to gain a high level of awareness in the Network and Computer pasture due to the large spread of information transmission technology. A powerful False Data Injection (FDI) Intruder monitors the network activities and injects the malicious data thereby causing failure in the power system. To overcome this defense, the “Conviction based Intruder Defense Model” is proposed to identify and isolate it from the network by providing secure transmission. This scheme operates in three phases. In the first phase, the data are analyzed with the library files to identify the conviction values. Based on the conviction values the resulting factors are analyzed with different iterations and the suspicious drafts are identified and classified using Fuzzy Intrusion Detection System (FIDS) divider. In the second phase, three algorithms are used to organize the drafts categorized. In the third phase, abnormal nodes are isolated from the network. Experimental results show higher accuracy and detection rates with low false positives.







Similar content being viewed by others
Abbreviations
- \( S \) :
-
source
- \( D \) :
-
destination
- \( \varGamma h^{\tau } \) :
-
accuracy
- \( \delta m^{r} \) :
-
detection rate
- \( \xi^{hn} \) :
-
false measure
- \( \varPi_{t}^{S,D} \) :
-
library files
- \( I_{L} \) :
-
intruder
- \( V_{(s,h)} \) :
-
conviction table
- \( \{ X_{1} ,X_{2} ,X_{3} ,X_{4} \} \) :
-
sectors
- \( O_{1} ,O_{2} ,O_{3} ,O_{4} ,O_{5} \) :
-
output path
- \( \lambda_{1} ,\lambda_{2} \ldots \ldots \lambda_{K} \) :
-
intermediate node
- \( \tau \) :
-
threshold
- \( W_{K} \) :
-
weight
References
Kim S and Park S 2017 CPS based manufacturing system optimization. Procedia Comput. Sci. 122:518–24
Wei R, Kelly T P, Hawkins R and Armengaud E 2018 Deis: Dependability engineering innovation for cyber-physical systems. Federation of International Conferences on software technologies: applications and foundations. 10748:409–16
Irmak E and Erkek ˙I 2018 An overview of cyber-attack vectors on scada systems. In: Digital Forensic and Security (ISDFS), IEEE, pp. 1–5
Spuhler M, Giustiniano D, Lenders V, Wilhelm M and Schmitt J B 2014 Detection of reactive jamming in DSSS. Wireless Communications 13(3): 1593–1603
Strasser M, Danev B and Capkun S (2012) Detection of reactive jamming. Sensor Networks 7(2): 1–29
Richa A, Scheideler C, Schmid S and Zhang J 2018 An Efficient and Fair MAC protocol Robust to Reactive Interference. IEEE/ACM Transaction on Networking 21(3): 760–771
Xuan Y, Shen Nguyen N P and Thai M T 2011 A Trigger Identification Service for Defending Reactive Jammers in WSN. IEEE Transaction on Mobile Computing 11(5):793–806
Zhan, Liu X, Shuai Z, Li Z and Wen Y 2018 Cyber cascades screening considering the impacts of false data injection attacks. IEEE Trans. Power Syst. 33(6):6545–6556
Chen Maglaras 2018 Stuxnet worm impact on industrial cyber-physical system security. In: IEEE, pp. 4490–4494
Shiu A and Sastry S 2017 A taxonomy of cyber attacks on SCADA systems. In: IEEE, pp. 380–388.
Ahmed C M, Zhou J and Mathur A P 2018 Noise matters: Using sensor and process noise fingerprint to detect stealthy cyber attacks and authenticate sensors in cps. In: ACM, pp. 566–581
Shoukry 2017. Analysis of the cyber attack on the ukrainian power grid. In: Electric. Inform. Shar. Anal. Center
Hadziosmanovic, Tomin N V, Kurbatsky V G, Sidorov D Nand Zhukov A V 2017. Machine learning techniques for power system security assessment. IFAC-Papers OnLine 49(27):445–50
Junejo, Honeine P, Beauseroy P 2018 Lp-norms in one-class classification for intru- sion detection in SCADA systems. IEEE Trans. Ind. Informa. 10(4):2308–17
Nader P, Honeine P, Beauseroy P 2014 Mahalanobis-based one-class classification. Machine learning for signal processing. In: IEEE, pp. 1–6
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Benisha, R.B., Raja Ratna, S. An intruder defense model for the detection of power grid disturbances in wireless network. Sādhanā 45, 154 (2020). https://doi.org/10.1007/s12046-020-01404-3
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s12046-020-01404-3