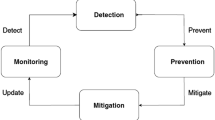
Abstract
Distributed Denial of Service (DDoS) attacks are a serious threat to Cloud. These attacks consume large amount of resources and increase the service usage cost by a significant factor. Due to multi-tenancy and self-provisioning properties of Cloud, traditional DDoS detection techniques cannot be directly applied. Hence, there is a need for Cloud-specific DDoS detection framework. In this paper, a statistical and distributed network packet filtering model is proposed against DDoS attacks in Cloud. The key idea of this scheme is to distribute multiple packet filters among individual virtual machines, which generate and share collective profile of normal behaviour with a coordinator node at constant intervals. Statistics of selected network attributes construct the normal behaviour profile. Based on the deviation from normal behaviour a decision is made whether to accept or reject the incoming packet. The coordinator node monitors filter and distribute the averaged profile to newly provisioned nodes. Individual profiles have low memory and storage requirements and are updated dynamically. Simulation study indicates the effectiveness of this scheme in detecting DDoS attacks in Cloud.







Similar content being viewed by others
References
Ries B 2010 Hackers’ most destructive attacks, http://www.thedailybeast.com/articles/2010/ 12/11/hackers-10-most-famous-attacks-worms-and-ddos-takedowns.html
Clark J 2011 Amazon cloud used in PlayStation Network hack. http://www.zdnet.com/amazon-cloud-used-in-playstation-network-hack-4010022454/
Mirkovic J and Reiher P 2004 A taxonomy of DDoS attack and DDoS defense mechanisms. ACM SIGCOMM Comput. Commun. Rev. 34(2): 39–53
Modi C, Patel D, Borisaniya B, Patel H, Patel A and Rajarajan M 2013 A survey of intrusion detection techniques in cloud. J. Netw. Comput. Appl. 36(1): 42–57
Leu F Y and Li Z Y 2009 Detecting DoS and DDoS attacks by using an intrusion detection and remote prevention system. In: Proceedings of IAS, pp. 251–254
Wang H, Jin C and Shin K G 2007 Defense against spoofed IP traffic using hop-count filtering. IEEE/ACM Trans. Netw. 15(1): 40–53
Kim Y, Lau W C, Chuah M C and Chao H J 2006 PacketScore: a statistics-based packet filtering scheme against distributed denial-of-service attacks. IEEE Trans. Depend. Secure Comput. 3(2): 141–155
Chen Q, Lin W, Dou W and Yu S 2011 CBF: a packet filtering method for DDoS attack defense in cloud environment. In: Proceedings of the 9th IEEE International Conference on Dependable, Autonomic and Secure Computing (DASC), pp. 427–434
Vieira K, Schulter A, Westphall C and Westphall C M 2010 Intrusion detection for grid and cloud computing. IT Profess. 12(4): 38–43
Lo C C, Huang C C and Ku J 2010 A cooperative intrusion detection system framework for cloud computing networks. In: Proceedings of the 39th International Conference on Parallel Processing Workshops (ICPPW), pp. 280–284
Jin H, Xiang G, Zou D, Wu S, Zhao F, Li M and Zheng W 2013 A VMM-based intrusion prevention system in cloud computing environment. J. Supercomput. 66(3): 1133–1151
Oktay U and Sahingoz O K 2013 Proxy network intrusion detection system for cloud computing. In: Proceedings of the International Conference on Technological Advances in Electrical, Electronics and Computer Engineering (TAEECE), pp. 98–104
Joshi B, Vijayan A S and Joshi B K 2012 Securing cloud computing environment against DDoS attacks. In: Proceedings of the International Conference on Computer Communication and Informatics (ICCCI), pp. 1–5
Ingram R, Shields P, Walter J E and Welch J L 2009 An asynchronous leader election algorithm for dynamic networks. In: Proceedings of the IEEE International Symposium on Parallel and Distributed Processing (IPDPS), pp. 1–12
Kasera S, Pinheiro J, Loader C, Karaul M, Hari A and LaPorta T 2001 Fast and robust signaling overload control. In: Proceedings of the 9th International Conference on Network Protocols, pp. 323–331
DARPA 1999 Intrusion Detection Evaluation Data Set, http://www.ll.mit.edu
Milojičić D, Llorente I M and Montero R S 2011 OpenNebula: a cloud management tool. IEEE Internet Comput. 15(2)
Guyon I and Elisseeff A 2003 An introduction to variable and feature selection. J. Mach. Learn. Res. 3: 1157–1182
Torkkola K 2003 Feature extraction by non-parametric mutual information maximization. J. Mach. Learn. Res. 3: 1415–1438
LOIC 2012 Low orbit ion cannon, http://sourceforge.net/projects/loic
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
PANDEY, V.C., PEDDOJU, S.K. & DESHPANDE, P.S. A statistical and distributed packet filter against DDoS attacks in Cloud environment. Sādhanā 43, 32 (2018). https://doi.org/10.1007/s12046-018-0800-7
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s12046-018-0800-7