Abstract
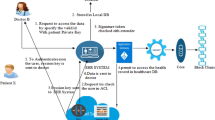
By the widespread use of cloud storage service, users get a lot of conveniences such as low-price file remote storage and flexible file sharing. The research points in cloud computing include the verification of data integrity, the protection of data privacy and flexible data access. The integrity of data is ensured by a challenge-and-response protocol based on the signatures generated by group users. Many existing schemes use group signatures to make sure that the data stored in cloud is intact for the purpose of privacy and anonymity. However, group signatures do not consider user equality and the problem of frameability caused by group managers. Therefore, we propose a data sharing scheme PSFS to support user equality and traceability meanwhile based on our previous work HA-DGSP. PSFS has some secure properties such as correctness, traceability, homomorphic authentication and practical data sharing. The practical data sharing ensures that the data owner won’t loss the control of the file data during the sharing and the data owner will get effective incentive of data sharing. The effective incentive is realized by the technology of blockchain. The experimental results show that the communication overhead and computational overhead of PSFS is acceptable.



Similar content being viewed by others
References
Yang, H. S., & Yoo, S. J. (2015). A study on smartwork security technology based on cloud computing environment. Wireless Personal Communications, 94(3), 1–10.
Yuan, J., & Yu, S. (2015). Public integrity auditing for dynamic data sharing with multiuser modification. IEEE Transactions on Information Forensics and Security, 10(8), 1717–1726.
Huang, L., Zhang, G., & Fu, A. (2016). Privacy-preserving public auditing for dynamic group based on hierarchical tree. Journal of Computer Research and Development, 53(10), 2334–2342.
Yu, S. (2017). Big privacy: Challenges and opportunities of privacy study in the age of big data. IEEE Access, 4, 2751–2763.
Li, X., Kumari, S., Shen, J., Wu, F., & Chen, C. (2017). Secure data access and sharing scheme for cloud storage. Wireless Personal Communications, 96(4), 5295–5314.
Wang, C., Chow, S. S. M., Wang, Q., Ren, K., & Lou, W. (2013). Privacy-preserving public auditing for secure cloud storage. IEEE Transactions on Computers, 62(2), 362–375.
Huang, L., Zhang, G., & Fu, A. (2017). Certificateless public verification scheme with privacy-preserving and message recovery for dynamic group. In Australasian computer science week multiconference (p. 76). ACM.
Li, J., Zhang, L., Liu, J. K., Qian, H., & Dong, Z. (2016). Privacy-preserving public auditing protocol for low-performance end devices in cloud. IEEE Transactions on Information Forensics and Security, 11(11), 2572–2583.
Wang, B., Li, B., & Li, H. (2012). Knox: Privacy-preserving auditing for shared data with large groups in the cloud. In International conference on applied cryptography and network security (pp. 507–525). Springer.
Li, H., Sun, W., Li, F., & Wang, B. (2014). Secure and privacy-preserving data storage service in public cloud. Journal of Computer Research & Development, 51(7), 1397–1409.
Wang, B., Li, B., & Li, H. (2014). Oruta: Privacy-preserving public auditing for shared data in the cloud. IEEE Transactions on Cloud Computing, 2(1), 43–56.
Wang, H., He, D., Yu, J., & Wang, Z. (2016). Incentive and unconditionally anonymous identity-based public provable data possession. IEEE Transactions on Services Computing, PP(99), 1.
Huang, L., Zhang, G., & Fu, A. (2017). Privacy-preserving public auditing for non-manager group. In IEEE international conference on communications (pp. 1–6). IEEE.
Fu, A., Yu, S., Zhang, Y., Wang, H., & Huang, C. (2017). NPP: A new privacy-aware public auditing scheme for cloud data sharing with group users. IEEE Transactions on Big Data, PP(99), 1.
Yang, G., Yu, J., Shen, W., Su, Q., Fu, Z., & Hao, R. (2016). Enabling public auditing for shared data in cloud storage supporting identity privacy and traceability. Journal of Systems & Software, 113(C), 130–139.
Yu, Y., Man, H. A., Mu, Y., Tang, S., & Ren, J. (2015). Enhanced privacy of a remote data integrity-checking protocol for secure cloud storage. International Journal of Information Security, 14(4), 307–318.
Zhang, J., Li, P., & Mao, J. (2015). An oriented-group supporting multi-user public auditing for data sharing. In IEEE international conference on smart city (pp. 996–1002). IEEE.
Achhra, A., Vaswani, P., Agale, R., & Chheda, M. (2015). Public auditing for the shared data in the cloud. International Journal of Advance Foundation and Research in Computer, 2(4), 125–129.
Christidis, K., & Devetsikiotis, M. (2016). Blockchains and smart contracts for the internet of things. IEEE Access, 4, 2292–2303.
Zyskind, G., Nathan, O., Pentland, A. (2015). Decentralizing privacy: Using blockchain to protect personal data. IEEE security and privacy workshops (pp. 180–184). IEEE Computer Society.
Blömer, J. (2011). How to share a secret. Communications of the ACM, 22(11), 612–613.
Ateniese, G., Burns, R., Curtmola, R., Herring, J., Kissner, L., Peterson, Z., et al. (2007). Provable data possession at untrusted stores. In ACM conference on computer and communications security (pp. 598–609). ACM.
Juels, A., & Kaliski, B. S. (2007). Pors: Proofs of retrievability for large files. In ACM conference on computer and communications security (pp. 584–597). ACM.
Fu, A., Li, Y., Yu, S., Yu, Y., & Zhang, G. (2018). DIPOR: An IDA-based dynamic proof of retrievability scheme for cloud storage systems. Journal of Network & Computer Applications, 104, 97–106.
Li, X., Qian, H., & Li, J. (2011). Democratic group signatures with threshold traceability. Journal of Shanghai Jiaotong University, 16(5), 530–532.
Lynn, B. (2012). The pairing-based cryptography (pbc) library. http://crypto.stanford.edu/pbc.
Huang, L., Zhang, G., Yu, S., Fu, A., & Yearwood, J. (2017). SeShare: Secure cloud data sharing based on blockchain and public auditing. Concurrency & Computation Practice & Experience. https://doi.org/10.1002/cpe.4359.
Acknowledgements
This work is supported by National Science Foundation of China (61572255), Six talent peaks project of Jiangsu Province, China (XYDXXJS-032), CERNET Innovation Project (NGII20170205). We would like to appreciate the anonymous referees for their helpful comments.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Huang, L., Zhang, G. & Fu, A. Privacy-Preserving Public Auditing for Non-manager Group Shared Data. Wireless Pers Commun 100, 1277–1294 (2018). https://doi.org/10.1007/s11277-018-5634-4
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-018-5634-4