Abstract
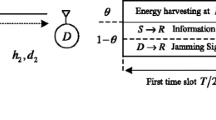
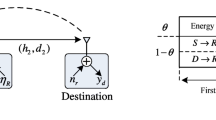
In this paper, we consider the secrecy performance of an energy-harvesting relaying system with Kth best partial relay selection where the communication of a multi-antenna source-destination pair is assisted via single-antenna untrusted relays. To protect confidential source messages from untrusted relays, transmit beamforming and destination jamming signals are used. The relays are energy-constrained nodes that use the power-splitting policy to harvest energy through the wireless signals from both the source and destination. For performance evaluation, closed-form expressions of the secrecy outage probability and average secrecy capacity (ASC) are derived for Nakagami-m fading channels. The analytical results are confirmed via Monte Carlo simulations. Numerical results provide valuable insights into the effect of various system parameters, such as relay location, number of relays, and power splitting ratio, on the secrecy performance. Specifically, the maximum ASC is achieved when the relay is located between the source and destination.





Similar content being viewed by others
References
Nasir, A., Zhou, X., Durrani, S., & Kennedy, R. (2013). Relaying protocols for wireless energy harvesting and information processing. IEEE Transactions on Communications, 12(7), 3622–3636.
Zhu, G., Zhong, C., Suraweera, H. A., Karagiannidis, G. K., Zhang, Z., & Tsiftsis, T. A. (2015). Wireless information and power transfer in relay systems with multiple antennas and interference. IEEE Transactions on Communications, 63(4), 1400–1418.
Zhou, X., Zhang, R., & Ho, C. K. (2013). Wireless information and power transfer: Architecture design and rate-energy tradeoff. IEEE Transactions on Communications, 61(11), 4754–4767.
Zhong, C., Suraweera, H., Zheng, G., Krikidis, I., & Zhang, Z. (2014). Wireless information and power transfer with full duplex relaying. IEEE Transactions on Communications, 62(10), 3447–3461.
Son, P. N., & Kong, H. Y. (2015). Cooperative communication with energy-harvesting relays under physical layer security. IET Communications, 9(17), 2131–2139.
Hanif, M., Yang, H. C., & Alouini, M. S. (2014). Capacity bounds for kth best path selection over generalized fading channels. IEEE Commu. Lett., 18(2), 261–264.
Ahn, K. S., Choi, S. W., & Ahn, J. M. (2015). Secrecy performance of maximum ratio diversity with channel estimation error. IEEE Signal Processing Letters, 22(11), 2167–2171.
Xing, H., Liu, L., & Zhang, R. (2016). Secrecy wireless information and power transfer in fading wiretap channel. IEEE Transactions on Vehicular Technology, 65(1), 180–190.
Liu, L., Zhang, R., & Chua, K. C. (2014). Secrecy wireless information and power transfer with MISO beamforming. IEEE Transactions on Signal Processing, 62(7), 1850–1863.
Zhang, H., Li, C., Huang, Y., & Yang, L. (2016). Secure beamforming for SWIPT in multiuser MISO broadcast channel with confidential messages. IEEE Communications Letters, 19(8), 1347–1350.
Kalamkar, S. S., & Banerjee, A. (2016). Secure communication via a wireless energy harvesting untrusted relay. IEEE Transactions on Vehicular Technology, 66(3), 2199–2213.
Hoang, T. M., Duong, T. Q., Vo, N. S., & Kundu, C. (2017). Physical layer security in cooperative energy harvesting networks with a friendly jammer. IEEE Wireless Communications Letters, 6(2), 174–177.
Khafagy, M. G., Ismail, A., Alouini, M. S., & Assa, S. (2015). Efficient cooperative protocols for full duplex relaying over Nakagami-m fading channels. IEEE Transactions on Wireless Communications, 14(6), 3456–3470.
Gradshteyn, I. S., Ryzhik, I. M., Jeffrey, A., & Zwillinger, D. (2007). Table of integral, series and products (7th ed.). Amsterdam: Elsevier.
David, H. A., & Nagaraja, H. N. (2003). Order statistics (3rd ed.). New York: Wiley.
Olver, F. W. J., Lozier, D. W., Boisvert, R. F., & Clark, C. W. (2010). NIST handbook of mathematical functions. Cambridge: Cambridge University Press.
Zhu, G., Zhong, C., Suraweera, H. A., Zhang, Z., Yuen, C., & Yin, R. (2014). Ergodic capacity comparison of different relay precoding schemes in dual-hop AF systems with co-channel interferer. IEEE Transactions on Communications, 62(7), 2314–2328.
Author information
Authors and Affiliations
Corresponding author
Appendices
Appendix 1
The secrecy outage probability in (15) can be rewritten as
Because \(\varXi (Y;\gamma_{\text{th}}) \geqslant 0\) if and only if \(y_1 \leqslant Y <\infty\), we can rewrite (36) as
1.1 Calculation for \(P_{\text{out,low}}^{\text{KBFC}}\)
Substituting \(F_X(x)\) and \(f_Y(y)\) for the KBFC scheme in to (37), and using [14, Eq. (8.356.3)], \(P_{\text{out,low}}^{\text{KBFC}}\) can be expressed as
Expressing \(\varGamma (\alpha ,x)\) as [14, Eq. (8.352.7)] and using the multinomial theorem [16, Eq. (26.4.9)] given by
\(P_{\text{out,low}}^{\text{KBFC}}\) can be expressed as in (16).
1.2 Calculation for \(P_{\text{out,low}}^{\text{KBSC}}\)
Using \(F_X(x)\) and \(f_Y(y)\) for the KBSC scheme, the expression for \(P_{\text{out,low}}^{\text{KBSC}}\) can be achieved using similar calculation steps for \(P_{\text{out,low}}^{\text{KBFC}}\).
Appendix 2
Because the exact analysis for (19) appears to be difficult, the high-power SOP is approached using the asymptotic formulas of \({F_\mathcal {X}}\left( {x;m,\lambda } \right)\) and \({F_{{\mathcal {X}^{\left( K \right) }}}}\left( {x;m,\lambda } \right)\) as \(x\rightarrow 0^+\). Using the series representation of the incomplete gamma function [14, Eq. (8.354.1)] and the fact that \(\mathop {\lim }\limits _{x \rightarrow {0^ + }} \varGamma \left( {\alpha ,x} \right) = \varGamma \left( \alpha \right)\), we yield the following asymptotic formulas:
2.1 Calculation for \(P_{\text{out,HPL}}^{\text{KBFC}}\)
Because \(\underset{{\mathfrak {b}}\rightarrow \infty }{\lim } y_0 = \underset{({\mathfrak {a,b}})\rightarrow (\infty ,\infty )}{\lim } x_0=0\), \(\mathcal {J}_1\) in (19) can be approximated using the asymptotic formula of \(F_Y(y)\) for the KBFC scheme as follows.
Using \(f_Y(y)\) and the asymptotic formula of \(F_X(x)\) for the KBFC scheme, \(\mathcal {J}_2\) in (19) can be approximated by
where \({\mathcal {J}_{{\text {2,a}}}} = \int \limits _{{m_2}{y_0}/{\lambda _2}}^\infty {z_1^{{N_2}{m_2} - n - 1}} {e^{ - {z_1}}}d{z_1}\) and \({z_1} = \frac{{{m_2}y}}{{{\lambda _2}}}\). It can be seen that in the case of \(n < {N_2}{m_2}\), we have
and in the case of \(n\geqslant N_2m_2\), \(\mathcal {J}_{2,a}\) can be solved with help from [14, Eq. (3.351.4)] as follows.
Using (42), (44) and (45), \(P_{\text{out,HPL}}^{\text{KBFC}}\) can be expressed as in (20).
2.2 Calculation for \(P_{\text{out,HPL}}^{\text{KBSC}}\)
Using the asymptotic formula of \(F_Y(x)\) and \(F_X(x)\) for the KBSC scheme, and follows the same steps of 6.3.1, \(P_{\text{out,HPL}}^{\text{KBSC}}\) can be expressed as in (21).
Appendix 3
According to [17], we can calculate \({\mathcal{C}}_{\text{erg,r}}\) as
where \(F_{\gamma _r}(\gamma )\) is the CDF of \(\gamma _r\). From (6), \(F_{\gamma _r}(\gamma )\) can be calculated as
Because \({\mathcal{C}}_{\text{erg,d}}\) does not admit closed form expressions, \({\mathcal{C}}_{\text{erg,d}}\) can be evaluated by its lower bound obtaining by using Jensen’s inequality for a convex function \(f(x)=\ln (1+e^{\ln (x)})\) as follows.
From (9a), (48) can be rewritten as
where \({\mathcal {J}_3} = \mathbb {E}\left\{ {\ln \left( X \right) } \right\} ,{\mathcal {J}_4} = \mathbb {E}\left\{ {\ln \left( Y \right) } \right\}\) and \({\mathcal {J}_5} = \ln ( {\mathfrak {c}} ) + \mathbb {E}\left\{ {\ln \left( { \tfrac{Y}{{\mathfrak {c}}} + 1} \right) } \right\}\).
3.1 Calculation for \(F_{{\gamma _r}}^{\text{KBFC }}\left( \gamma \right)\)
Substituting \({F_X}\left( x \right)\) and \({f_Y}\left( y \right)\) for the KBFC scheme into (47), we have
Using (1), ( 12), (39) and [14, Eq. (3.351.3)], (50) can be rewritten as
3.2 Calculation for \(\mathcal {C}^\text{KBFC}_{\text{erg,r}}\)
Substituting (51) into (46), \({\mathcal{C}}^{\text{KBFC}}_{\text{erg,r}}\) can be calculated as
where \({\mathcal {J}_6}\left( \gamma \right) = {\left( {1 + \gamma } \right) ^{ - 1}}{\left( {\gamma + {\mu _3}} \right) ^{ - {N_2}{m_2} - u}}\).
Using the partial fraction expansion for \({\mathcal {J}_6}(\gamma )\), we have \({\mathcal {J}_6}\left( \gamma \right) = \frac{{{\mathcal {A}_0}}}{{\left( {\gamma + 1} \right) }} + \sum \limits _{j = 1}^{{N_2}{m_2} + u} {\frac{{{\mathcal {A}_j}}}{{{{\left( {\gamma + {\mu _3}} \right) }^j}}}}\); then, applying [14, Eq. (3.383.10) and Eq. (9.211.4)] on (52), \(\mathcal {C}_{{\text {erg,r}}}^{{\text {KBFC}}}\) can be expressed as in (26).
3.3 Calculation for \(\mathcal {C}^{\text{KBFC}}_{\text{erg,d}}\)
Using \(f_X(x)\) for the KBFC scheme, (39) and [14, Eq. (4.352.1)], \(\mathcal {J}_3\) can be calculated as in (27).
Similarly, \(\mathcal {J}_4\) for the KBFC scheme can be calculated as \({\mathcal{J}}_{\text{4,a}}\) given as (28).
Using \(f_Y(y)\) for the KBFC scheme, \({\mathcal{J}}_{\text{5}}\) can be calculated as
where \(z_2=m_2y/{\lambda _2}\). With the help of [14, Eq. (4.337.5)], (53) can be rewritten as in (29).
Finally, \(\mathcal {C}^{\text{KBFC}}_{\text{erg,d}}\) can be bounded below as
To this end, substituting (26) and (54) into (24), we can obtain the desired result.
Rights and permissions
About this article
Cite this article
Tuan, V.P., Kong, H.Y. Secure communication in untrusted relay selection networks with wireless energy harvesting. Wireless Netw 25, 1431–1442 (2019). https://doi.org/10.1007/s11276-017-1602-2
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-017-1602-2