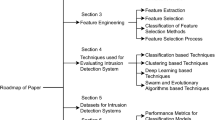
Abstract
Due to the rapid growth of internet services, the demand for protection and security of the network against sophisticated attacks is continuously increasing. Nowadays, in network security, an intrusion detection system (IDS) plays an important role to detect intrusive activity. With the purpose of reducing the search dimensionality and enhancing classification performance of IDS model, in the literature several hybrid evolutionary algorithms have been investigated to tackle anomaly detection problems, but they have few drawbacks such as poor diversity, massive false negative rate, and stagnation. To resolve these limitations, in this study, we introduce a new hybrid evolutionary algorithm combining the techniques of grasshopper optimization algorithm (GOA) and simulated annealing (SA), called GOSA for IDS that extracts the most noteworthy features and eliminates irrelevant ones from the original IDS datasets. In the proposed method, SA is integrated into GOA, while utilizing it to increase the solution quality after each iteration of GOA. Support vector machine is used as a fitness function in the proposed method to select relevant features which can help to classify attacks accurately. The performance of the proposed method is evaluated on two IDS datasets such as NSL-KDD and UNSW-NB15. From experimental results, we observe that the proposed method outperforms existing state-of-the-art methods and attains high detection rate as 99.86%, an accuracy as 99.89%, and low false alarm rate as 0.009 in NSL-KDD and high detection rate as 98.85%, an accuracy as 98.96%, and low false alarm rate as 0.084 in UNSW-NB15.








Similar content being viewed by others
References
Balakrishnan V, Khan S, Fernandez T, Arabnia HR (2019) Cyberbullying detection on twitter using big five and dark triad features. Person Individ Differ 141:252–257
Kim K, Kim I, Lim J (2017) National cyber security enhancement scheme for intelligent surveillance capacity with public iot environment. J Supercomput 73(3):1140–1151
Khosravi MR, Basri H, Rostami H, Samadi S (2018) Distributed random cooperation for vbf-based routing in high-speed dense underwater acoustic sensor networks. J Supercomput 74(11):6184–6200
Dwivedi S, Vardhan M, Tripathi S, Shukla AK (2019) Implementation of adaptive scheme in evolutionary technique for anomaly-based intrusion detection. Evolut Intell. https://doi.org/10.1007/s12065-019-00293-8
Zhang J, Gardner R, Vukotic I (2019) Anomaly detection in wide area network meshes using two machine learning algorithms. Future Gen Comput Syst 93:418–426
Spafford EH, Zamboni D (2000) Intrusion detection using autonomous agents. Comput Netw 34(4):547–570
Pitropakis N, Panaousis E, Giannetsos T, Anastasiadis E, Loukas G (2019) A taxonomy and survey of attacks against machine learning. Comput Sci Rev 34:100199
Khammassi C, Krichen S (2017) A ga-lr wrapper approach for feature selection in network intrusion detection. Comput Secur 70:255–277
Ambusaidi MA, He X, Nanda P (2015) Unsupervised feature selection method for intrusion detection system. In: IEEE Trustcom/BigDataSE/ISPA, vol 1. IEEE, pp 295–301
Wu SX, Banzhaf W (2010) The use of computational intelligence in intrusion detection systems: a review. Appl Soft Comput 10(1):1–35
Aburomman AA, Reaz MBI (2017) A survey of intrusion detection systems based on ensemble and hybrid classifiers. Comput Secur 65:135–152
Wang W, He Y, Liu J, Gombault S (2015) Constructing important features from massive network traffic for lightweight intrusion detection. IET Inf Secur 9(6):374–379
Shukla AK, Singh P, Vardhan M (2018) Neighbour teaching learning based optimization for global optimization problems. J Intell Fuzzy Syst 34(3):1583–1594
Črepinšek M, Liu S-H, Mernik M (2013) Exploration and exploitation in evolutionary algorithms: a survey. ACM Comput Surv (CSUR) 45(3):35
Gu J, Wang L, Wang H, Wang S (2019) A novel approach to intrusion detection using SVM ensemble with feature augmentation. Comput Secur 86:53–62
Hajisalem V, Babaie S (2018) A hybrid intrusion detection system based on ABC-AFS algorithm for misuse and anomaly detection. Comput Netw 136:37–50
Talbi E-G (2009) Metaheuristics: from design to implementation, vol 74. Wiley, New York
Shukla AK (2019) Building an effective approach toward intrusion detection using ensemble feature selection. Int J Inf Secur Priv 13(3):31–47
Modi CN, Acha K (2017) Virtualization layer security challenges and intrusion detection/prevention systems in cloud computing: a comprehensive review. J Supercomput 73(3):1192–1234
Luo H, Chen Z, Li J, Vasilakos AV (2017) Preventing distributed denial-of-service flooding attacks with dynamic path identifiers. IEEE Trans Inf Forensics Secur 12(8):1801–1815
Javidrad F, Nazari M, Javidrad H (2018) Optimum stacking sequence design of laminates using a hybrid PSO-SA method. Compos Struct 185:607–618
Bagherlou H, Ghaffari A (2018) A routing protocol for vehicular ad hoc networks using simulated annealing algorithm and neural networks. J Supercomput 74(6):2528–2552
Mirjalili SZ, Mirjalili S, Saremi S, Faris H, Aljarah I (2018) Grasshopper optimization algorithm for multi-objective optimization problems. Appl Intell 48(4):805–820
Pervez MS, Farid DM (2014) Feature selection and intrusion classification in NSL-KDD cup 99 dataset employing svms. In: The 8th International Conference on Software, Knowledge, Information Management and Applications (SKIMA 2014). IEEE, pp 1–6
Arora S, Anand P (2019) Chaotic grasshopper optimization algorithm for global optimization. Neural Comput Appl 31(8):4385–4405
Mafarja M, Aljarah I, Faris H, Hammouri AI, AlaM A-Z, Mirjalili S (2019) Binary grasshopper optimisation algorithm approaches for feature selection problems. Expert Syst Appl 117:267–286
Medjahed SA, Saadi TA, Benyettou A, Ouali M (2017) Kernel-based learning and feature selection analysis for cancer diagnosis. Appl Soft Comput 51:39–48
Javidrad F, Nazari M (2017) A new hybrid particle swarm and simulated annealing stochastic optimization method. Appl Soft Comput 60:634–654
Beigvand SD, Abdi H, La Scala M (2017) Hybrid gravitational search algorithm-particle swarm optimization with time varying acceleration coefficients for large scale chped problem. Energy 126:841–853
Rodriguez FJ, Garcia-Martinez C, Lozano M (2012) Hybrid metaheuristics based on evolutionary algorithms and simulated annealing: taxonomy, comparison, and synergy test. IEEE Trans Evol Comput 16(6):787–800
Kirkpatrick S, Gelatt CD, Vecchi MP (1983) Optimization by simulated annealing. Science 220(4598):671–680
Hamamoto AH, Carvalho LF, Sampaio LDH, Abrão T, Proença ML Jr (2018) Network anomaly detection system using genetic algorithm and fuzzy logic. Expert Syst Appl 92:390–402
Sinha A, Jana PK (2018) A hybrid mapreduce-based \(k\)-means clustering using genetic algorithm for distributed datasets. J Supercomput 74(4):1562–1579
Sadiq AS, Alkazemi B, Mirjalili S, Ahmed N, Khan S, Ali I, Pathan A-SK, Ghafoor KZ (2018) An efficient ids using hybrid magnetic swarm optimization in wanets. IEEE Access 6:29 041–29 053
Tsang C-H, Kwong S, Wang H (2007) Genetic-fuzzy rule mining approach and evaluation of feature selection techniques for anomaly intrusion detection. Pattern Recogn 40(9):2373–2391
Shahreza ML, Moazzami D, Moshiri B, Delavar M (2011) Anomaly detection using a self-organizing map and particle swarm optimization. Sci Iran 18(6):1460–1468
Zaman S, Karray F (2009) Lightweight ids based on features selection and ids classification scheme. In: 2009 International Conference on Computational Science and Engineering, vol 3. IEEE, pp 365–370
Buchtala O, Klimek M, Sick B (2005) Evolutionary optimization of radial basis function classifiers for data mining applications. IEEE Trans Syst Man Cybern Part B (Cybernetics) 35(5):928–947
Kuang F, Xu W, Zhang S (2014) A novel hybrid KPCA and SVM with GA model for intrusion detection. Appl Soft Comput 18:178–184
Vidal JM, Orozco ALS, Villalba LJG (2018) Adaptive artificial immune networks for mitigating DoS flooding attacks. Swarm Evolut Comput 38:94–108
Moon D, Im H, Kim I, Park JH (2017) DTB-IDS: an intrusion detection system based on decision tree using behavior analysis for preventing apt attacks. J Supercomput 73(7):2881–2895
Karami A, Guerrero-Zapata M (2015) A hybrid multiobjective RBF-PSO method for mitigating DOS attacks in named data networking. Neurocomputing 151:1262–1282
Zakeri A, Hokmabadi A (2019) Efficient feature selection method using real-valued grasshopper optimization algorithm. Expert Syst Appl 119:61–72
Fathy A (2018) Recent meta-heuristic grasshopper optimization algorithm for optimal reconfiguration of partially shaded PV array. Sol Energy 171:638–651
Ewees AA, Elaziz MA, Houssein EH (2018) Improved grasshopper optimization algorithm using opposition-based learning. Expert Syst Appl 112:156–172
Daneshmand SV, Heydari H (2016) A diversified multiobjective simulated annealing and genetic algorithm for optimizing a three-phase hts transformer. IEEE Trans Appl Supercond 26(2):1–10
Mafarja MM, Mirjalili S (2017) Hybrid whale optimization algorithm with simulated annealing for feature selection. Neurocomputing 260:302–312
Cortes C, Vapnik V (1995) Support-vector networks. Mach Learn 20(3):273–297
Alijla BO, Lim CP, Wong L-P, Khader AT, Al-Betar MA (2018) An ensemble of intelligent water drop algorithm for feature selection optimization problem. Appl Soft Comput 65:531–541
Ting T, Yang XS, Cheng S, Huang K (2015) Hybrid metaheuristic algorithms: past, present, and future. In: Yang XS (ed) Recent advances in swarm intelligence and evolutionary computation. Studies in computational intelligence, vol 585. Springer, Cham, pp 71–83
Maudes J, Rodríguez JJ, García-Osorio C (2007) Cascading for nominal data. In: Haindl M, Kittler J, Roli F (eds) Multiple Classifier Systems. MCS 2007. Lecture notes in computer science, vol 4472. Springer, Berlin, Heidelberg, pp 231–240
Tavallaee M, Bagheri E, Lu W, Ghorbani AA (2009) A detailed analysis of the KDD cup 99 data set. In: IEEE Symposium on Computational Intelligence for Security and Defense Applications. IEEE, pp 1–6
Mazini M, Shirazi B, Mahdavi I (2019) Anomaly network-based intrusion detection system using a reliable hybrid artificial bee colony and adaboost algorithms. J King Saud Univ Comput Inf Sci 31(4):541–553
Moustafa N, Misra G, Slay J (2018) Generalized outlier gaussian mixture technique based on automated association features for simulating and detecting web application attacks. IEEE Trans Sustain Comput. https://doi.org/10.1109/TSUSC.2018.2808430
Chang C-C, Lin C-J (2011) Libsvm: a library for support vector machines. ACM Trans Intell Syst Technol 2(3):27
Aljawarneh S, Aldwairi M, Yassein MB (2018) Anomaly-based intrusion detection system through feature selection analysis and building hybrid efficient model. J Comput Sci 25:152–160
Wang H, Gu J, Wang S (2017) An effective intrusion detection framework based on svm with feature augmentation. Knowl Based Syst 136:130–139
Abd Eldayem M (2014) A proposed http service based ids. Egypt Inform J 15:03
Lopez-Martin M, Carro B, Sanchez-Esguevillas A, Lloret J (2019) Shallow neural network with kernel approximation for prediction problems in highly demanding data networks. Expert Syst Appl 124:196–208
Kim G, Lee S, Kim S (2014) A novel hybrid intrusion detection method integrating anomaly detection with misuse detection. Expert Syst Appl 41(4):1690–1700
Bhuvaneswari Amma NG, Selvakumar S (2019) Deep radial intelligence with cumulative incarnation approach for detecting denial of service attacks. Neurocomputing 340:294–308
Salo F, Nassif AB, Essex A (2019) Dimensionality reduction with IG-PCA and ensemble classifier for network intrusion detection. Comput Netw 148:164–175
Moustafa N, Creech G, Slay J (2018) Anomaly detection system using beta mixture models and outlier detection. In: Pattnaik P, Rautaray S, Das H, Nayak J (eds) Progress in computing, analytics and networking. Advances in intelligent systems and computing, vol 710. Springer, Singapore, pp 125–135
Karami A, Guerrero Zapata M (2014) Mining and visualizing uncertain data objects and named data networking traffics by fuzzy self-organizing map. In: Proceedings of the Second International Workshop on Artificial Intelligence and Cognition (AIC 2014): Torino, Italy, November 26–27, 2014. CEUR-WS. org, pp 156–163
Moustafa N, Creech G, Slay J (2017) Big data analytics for intrusion detection system: statistical decision-making using finite dirichlet mixture models. In: Palomares Carrascosa I, Kalutarage H, Huang Y (eds) Data analytics and decision support for cybersecurity. Data Analytics, Springer, Cham, pp 127–156
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Dwivedi, S., Vardhan, M. & Tripathi, S. Incorporating evolutionary computation for securing wireless network against cyberthreats. J Supercomput 76, 8691–8728 (2020). https://doi.org/10.1007/s11227-020-03161-w
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-020-03161-w