Abstract
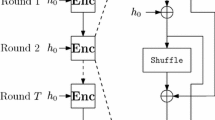
In this paper, we analyze the security of a chaos-based image encryption algorithm. We find that the algorithm is vulnerable to differential cryptanalysis. The differential cryptanalysis demonstrates that the security of the original scheme depends only on the permutation key instead of on all of the keys, which makes the key space of the cryptosystem greatly reduced. Specifically, \((H\times W+1)\) chosen plain-images can reveal the equivalent permutation key for one-round encryption, where \(H\times W\) is the size of the binary image. The two-way differential comparison method is proposed to break two-round cryptosystem. Basing on differential cryptanalysis, we propose a codebook attack under chosen-ciphertext conditions, design the codebook with \((H\times W)\) differential binary images, and totally break multi-round cryptosystem using XOR operation of \(O(H\times W)\) images. The simulation results indicate that the designed codebook attack is effective. Furthermore, we summarize some characteristics of a class of permutation–diffusion systems that also are vulnerable to the differential attack and the codebook attack.




Similar content being viewed by others
References
Huang, C.K., Nien, H.H.: Multi chaotic systems based pixel shuffle for image encryption. Opt. Commun. 282(11), 2123–2127 (2009)
Ye, G.: Image scrambling encryption algorithm of pixel bit based on chaos map. Pattern Recogn. Lett. 31(5), 347–354 (2010)
Fridrich, J.: Symmetric ciphers based on two-dimensional chaotic maps. Int. J. Bifurc. Chaos 8(6), 1259–1284 (1998)
Sam, I.S., Devaraj, P., Bhuvaneswaran, R.S.: A novel image cipher based on mixed transformed logistic maps. Multimedia Tools Appl. 56(2SI), 315–330 (2012)
Wang, X., Zhao, J., Liu, H.: A new image encryption algorithm based on chaos. Opt. Commun. 285(5), 562–566 (2012)
Wang, X., Teng, L.: An image blocks encryption algorithm based on spatiotemporal chaos. Nonlinear Dyn. 67(1), 365–371 (2012)
Zhou, G., Zhang, D., Liu, Y., Yuan, Y., Liu, Q.: A novel image encryption algorithm based on chaos and Line map. Neurocomputing 169(SI), 150–157 (2015)
Mirzaei, O., Yaghoobi, M., Irani, H.: A new image encryption method: parallel sub-image encryption with hyper chaos. Nonlinear Dyn. 67(67), 557–566 (2012)
Sun, Y., Chen, L., Xu, R., Kong, R.: An image encryption algorithm utilizing julia sets and hilbert curves. Plos ONE 9(1), e84655 (2014)
Tang, Z., Zhang, X., Lan, W.: Efficient image encryption with block shuffling and chaotic map. Multimedia Tools Appl. 74(15), 5429–5448 (2015)
Wu, X., Li, Y., Kurths, J.: A new color image encryption scheme using CML and a fractional-order chaotic system. Plos ONE 10, e01196603 (2015)
Wang, X., Xu, D.: A novel image encryption scheme based on Brownian motion and PWLCM chaotic system. Nonlinear Dyn. 75(1–2), 345–353 (2014)
Wang, X., Liu, C., Xu, D., Liu, C.: Image encryption scheme using chaos and simulated annealing algorithm. Nonlinear Dyn. 84(3), 1–13 (2016)
Chen, J., Zhu, Z., Fu, C., Yu, H.: An improved permutation–diffusion type image cipher with a chaotic orbit perturbing mechanism. Opt. Express 21(23), 27873–27890 (2013)
Chen, J.X., Zhu, Z.L., Fu, C., Yu, H., Zhang, L.B.: A fast chaos-based image encryption scheme with a dynamic state variables selection mechanism. Commun. Nonlinear Sci. Numer. Simul. 20(3), 846–860 (2015)
Ye, G., Huang, X.: A novel block chaotic encryption scheme for remote sensing image. Multimedia Tools Appl. 75(18), 11433 (2015). doi:10.1007/s11042-015-2861-5
Wang, Y., Wong, K., Liao, X., Xiang, T.: A block cipher with dynamic S-boxes based on tent map. Commun. Nonlinear Sci. 14(7), 3089–3099 (2009)
Xu, S., Chen, X., Zhang, R., Yang, Y., Guo, Y.: An improved chaotic cryptosystem based on circular bit shift and XOR operations. Phys. Lett. A 376(10–11), 1003–1010 (2012)
Li, S., Li, C., Chen, G., Bourbakis, N.G., Lo, K.T.: A general quantitative cryptanalysis of permutation-only multimedia ciphers against plaintext attacks. Signal Process. Image Commun. 23(3), 212–223 (2008)
Li, C., Lo, K.: Optimal quantitative cryptanalysis of permutation-only multimedia ciphers against plaintext attacks. Signal Process. 91(4), 949–954 (2011)
Rhouma, R., Belghith, S.: Cryptanalysis of a new image encryption algorithm based on hyper-chaos. Phys. Lett. A 372(38), 5973–5978 (2008)
Cokal, C., Solak, E.: Cryptanalysis of a chaos-based image encryption algorithm. Phys. Lett. A 373(15), 1357–1360 (2009)
Wang, B., Wei, X., Zhang, Q.: Cryptanalysis of an image cryptosystem based on logistic map. Optik 124(14), 1773–1776 (2013)
Tu, G., Liao, X., Xiang, T.: Cryptanalysis of a color image encryption algorithm based on chaos. Optik 124(22), 5411–5415 (2013)
Solak, E., Cokal, C., Yildiz, O.T., Biyikoglu, T.: Cryptanalysis of Fridrich’s chaotic image encryption. Int. J. Bifurc. Chaos 20(5), 1405–1413 (2010)
Chen, L., Wang, S.: Differential cryptanalysis of a medical image cryptosystem with multiple rounds. Comput. Biol. Med. 65, 69–75 (2015)
Özkaynak, F., Yavuz, S.: Analysis and improvement of a novel image fusion encryption algorithm based on dna sequence operation and hyper-chaotic system. Nonlinear Dyn. 78(2), 1311–1320 (2014)
Li, C., Liu, Y., Xie, T., Chen, M.Z.Q.: Breaking a novel image encryption scheme based on improved hyperchaotic sequences. Nonlinear Dyn. 73(3), 2083–2089 (2013)
Zhang, Y., Xiao, D.: Cryptanalysis of S-box-only chaotic image ciphers against chosen plaintext attack. Nonlinear Dyn. 72(4), 751–756 (2013)
Yap, W., Phan, R.C.W., Yau, W., Heng, S.: Cryptanalysis of a new image alternate encryption algorithm based on chaotic map. Nonlinear Dyn. 80(3), 1483–1491 (2015)
Zhu, C., Xu, S., Hu, Y., Sun, K.: Breaking a novel image encryption scheme based on Brownian motion and PWLCM chaotic system. Nonlinear Dyn. 79, 1511–1518 (2015)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Chen, L., Ma, B., Zhao, X. et al. Differential cryptanalysis of a novel image encryption algorithm based on chaos and Line map. Nonlinear Dyn 87, 1797–1807 (2017). https://doi.org/10.1007/s11071-016-3153-y
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11071-016-3153-y