Abstract
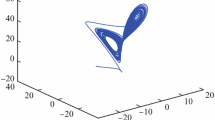
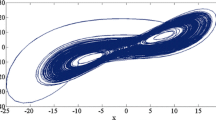
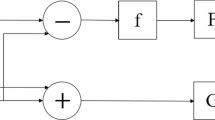
A new 2D Chebyshev-Sine map with natural evaluation is proposed and its dynamical behavior is analyzed. To investigate its application in information security, a color image encryption algorithm is designed. One-time initial condition expressed as ordered quaternion is extracted from colored non Gaussian noise before each encryption process. The algorithm can achieve desired effect after two rounds by exclusive or (XOR) operation with avalanche effect. Simulation results demonstrated that the speed is fast, so the algorithm is suitable for image encryption over the Cloud.










Similar content being viewed by others
References
Abdallah E, Ben AH, Prabir B (2007) MPEG video watermarking using tensor singular value decomposition. //International Conference Image Analysis and Recognition. Springer, Berlin, Heidelberg
Akhshani A, Akhavan A, Mobaraki A et al (2014) Pseudo random number generator based on quantum chaotic map[J]. Commun Nonlinear Sci Numer Simul 19(1):101–111
Arroyo D, Rhouma R, Alvarez G et al (2008) On the security of a new image encryption scheme based on chaotic map lattices[J]. Chaos 18(3):033112
Banerjee S, Yorke JA, Grebogi C (1998) Robust chaos[J]. Phys Rev Lett 80(14):3049
Belazi A, Khan M, El-Latif AAA et al (2017) Efficient cryptosystem approaches: S-boxes and permutation–substitution-based encryption[J]. Nonlinear Dyn 87(1):337–361
Cong L, Wu X, Sun S (1999) A general efficient method for chaotic signal estimation[J]. IEEE Trans Signal Process 47(5):1424–1428
Gao Z, Chen D, Zhang W et al (2017) Colour image encryption algorithm using one-time key and FrFT[J]. IET Image Process 12(4):472–478
Hamza AB, Krim H (2003) Jensen-Rényi divergence measure: theoretical and computational perspectives[C]//Information Theory, 2003. Proceedings. IEEE International Symposium on. IEEE, p 257–257
Hussain I, Shah T, Gondal MA (2012) Image encryption algorithm based on PGL(2,GF(28)) S-boxes and TD-ERCS chaotic sequence. Nonlinear Dyn 70(1):181–187
Kadir A, Aili M, Sattar M (2017) Color image encryption scheme using coupled hyper chaotic system with multiple impulse injections. Optik 129:231–238
Kurian AP, Leung H (2009) Weak signal estimation in chaotic clutter using model-based coupled synchronization[J]. IEEE Trans Circuits Syst I 56(4):820–828
L'Ecuyer P, Simard R (2013) TestU01: a software library in ANSI C for empirical testing of random number generators--user’s guide, Compact Version[J]
Liu H, Kadir A, Sun X (2017) Chaos-based fast colour image encryption scheme with true random number keys from environmental noise[J]. IET Image Process 11(5):324–332
Luo C, Wang X (2014) Adaptive modified function projective lag synchronization of hyperchaotic complex systems with fully uncertain parameters[J]. J Vib Control 20(12):1831–1845
Rozenbaum EB, Ganeshan S, Galitski V (2017) Lyapunov exponent and out-of-time-ordered correlator’s growth rate in a chaotic system[J]. Phys Rev Lett 118(8):086801
Seyedzadeh SM, Mirzakuchaki S (2012) A fast color image encryption algorithm based on coupled two-dimensional piecewise chaotic map. Signal Process 92(5):1202–1215
Shanon CE (1949) Communication theory of secrecy systems. Bell Syst Tech J 28(4):656–715
Wang X, Guo K (2014) A new image alternate encryption algorithm based on chaotic map[J]. Nonlinear Dyn 76(4):1943–1950
Wang XY, Zhang YQ, Zhao YY (2015) A novel image encryption scheme based on 2-D logistic map and DNA sequence operations[J]. Nonlinear Dyn 82(3):1269–1280
Wang X, Wang S, Zhang Y et al (2018) A one-time pad color image cryptosystem based on SHA-3 and multiple chaotic systems[J]. Opt Lasers Eng 103:1–8
Wang C, Wang X, Xia Z, Zhang C (2019) Ternary radial harmonic Fourier moments based robust stereo image zero-watermarking algorithm. Inf Sci 470:109–120
Xiao D, Zhang YS (2014) Self-adaptive permutation and combined global diffusion for chaotic color image encryption. AEU Int J Electron Commun 68(4):361–368
Ye G, Huang X (2017) An efficient symmetric image encryption algorithm based on an intertwining logistic map[J]. Neurocomputing 251:45–53
Ye G, Zhao H, Chai H (2016) Chaotic image encryption algorithm using wave-line permutation and block diffusion[J]. Nonlinear Dyn 83(4):2067–2077
Zhang Y, Xiao D (2014) An image encryption scheme based on rotation matrix bit-level permutation and block diffusion[J]. Commun Nonlinear Sci Numer Simul 19(1):74–82
Zhen P, Zhao G, Min L, Jin X (2016) Chaos-based image encryption scheme combining DNA coding and entropy. Multimed Tools Appl 75(11):6303–6319
Acknowledgments
This research is supported by the National Natural Science Foundation of China (No: 61662073, 61363082), the Natural Science Foundation of Shandong Province (No: ZR2018LF006).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest concerning the publication of this manuscript.
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Liu, H., Wen, F. & Kadir, A. Construction of a new 2D Chebyshev-Sine map and its application to color image encryption. Multimed Tools Appl 78, 15997–16010 (2019). https://doi.org/10.1007/s11042-018-6996-z
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-018-6996-z