Abstract
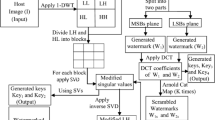
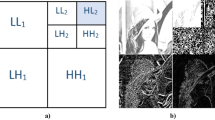
In this paper, a robust blind image watermarking method is proposed for copyright protection of digital images. This hybrid method relies on combining two well-known transforms that are the discrete Fourier transform (DFT) and the discrete cosine transform (DCT). The motivation behind this combination is to enhance the imperceptibility and the robustness. The imperceptibility requirement is achieved by using magnitudes of DFT coefficients while the robustness improvement is ensured by applying DCT to the DFT coefficients magnitude. The watermark is embedded by modifying the coefficients of the middle band of the DCT using a secret key. The security of the proposed method is enhanced by applying Arnold transform (AT) to the watermark before embedding. Experiments were conducted on natural and textured images. Results show that, compared with state-of-the-art methods, the proposed method is robust to a wide range of attacks while preserving high imperceptibility.

















Similar content being viewed by others
References
Ali M, Ahn CW, Pant M (2014) A robust image watermarking technique using SVD and differential evolution in DCT domain. Optik-International Journal for Light and Electron Optics 125(1):428–434
Barni M, Bartolini F, Piva A (2001) Improved wavelet-based watermarking through pixel-wise masking. IEEE Trans Image Process 10(5):783–791
Brodatz P (1966) Textures: a photographic album for artists and designers. Dover, New York
Cedillo-Hernandez M, Garcia-Ugalde F, Nakano-Miyatake M, Perez-Meana H (2012) Robust digital image watermarking using interest points and DFT domain. In: 35th IEEE international conference on telecommunications and signal processing (TSP), pp 715–719
Cox IJ, Kilian J, Leighton F, Shamoon T (1997) Secure spread spectrum watermarking for multimedia. IEEE Trans Image Process 6(12):1673–1687
Cox I, Miller M, Bloom J, Fridrich J, Kalker T (2007) Digital watermarking and steganography. Morgan Kaufmann, San Mateo
Das C, Panigrahi S, Sharma VK, Mahapatra KK (2014) A novel blind robust image watermarking in DCT domain using inter-block coefficient correlation. AEU-Int J Electron C 68(3):244–253
Dyson FJ, Falk H (1992) Period of a discrete cat mapping. Am Math Mon 99(7):603–614
Feng LP, Zheng LB, Cao P (2010) A DWT-DCT based blind watermarking algorithm for copyright protection. In: Third IEEE international conference on computer science and information technology (ICCSIT), vol 7, pp 455–458
Gangadhar Y, Akula VG, Reddy PC (2018) An evolutionary programming approach for securing medical images using watermarking scheme in invariant discrete wavelet transformation. Biomed Signal Process Control 43:31–40
Hsu CT, Wu JL (1999) Hidden digital watermarks in images. IEEE Trans Image Process 8(1):58–68
Jia SL (2014) A novel blind color images watermarking based on SVD. Optik-International Journal for Light and Electron Optics 125(12):2868–2874
Khayam SA (2003) The discrete cosine transform (DCT): theory and application. Michigan State University, p 114
Kumar C, Singh AK, Kumar P (2018) A recent survey on image watermarking techniques and its application in e-governance. Multimed Tools Appl 77(3):3597–3622
Kutter M, Petitcolas FA (1999) Fair benchmark for image watermarking systems. In: Electronic imaging, international society for optics and photonics, pp 226–239
Li M, Liang T, He YJ (2013) Arnold transform based image scrambling method. In: Third international conference on multimedia technology
Lin WH, Wang YR (2009) A wavelet-tree-based watermarking method using distance vector of binary cluster. Expert Systems with Applications 36(6):9869–9878
Liu L, Cheng L, Liu Y, Jia Y, Rosenblum DS (2016) Recognizing complex activities by a probabilistic interval-based model. In: AAAI, vol 30, pp 1266–1272
Liu Y, Nie L, Liu L, Rosenblum DS (2016) From action to activity: sensor-based activity recognition. Neurocomputing 181:108–115
Pereira S, Pun T (2000) Robust template matching for affine resistant image watermarks. IEEE Trans Image Process 9(6):1123–1129
Poljicak A, Mandic L, Agic D (2011) Discrete Fourier transform–based watermarking method with an optimal implementation radius. J Electron Imaging 20 (3):033008–033008
Press WH (1989) Numerical recipes in Pascal: the art of scientific computing, vol 1. Cambridge University Press, Cambridge
Qi X, Xin X (2011) A quantization-based semi-fragile watermarking scheme for image content authentication. J Vis Commun Image Represent 22(2):187–200
Roy S, Pal AK (2017) A robust blind hybrid image watermarking scheme in RDWT-DCT domain using Arnold scrambling. Multimed Tools Appl 76(3):3577–3616
Saha BJ, Kabi KK, Pradhan C (2014) Non blind watermarking technique using enhanced one time pad in DWT domain. In: 2014 international conference on computing, communication and networking technologies (ICCCNT). IEEE, pp 1–6
Sahraee MJ, Ghofrani S (2013) A robust blind watermarking method using quantization of distance between wavelet coefficients. Signal, Image and Video Processing 7(4):799–807
Singh D, Singh SK (2017) DWT-SVD and DCT based robust and blind watermarking scheme for copyright protection. Multimed Tools Appl 76(11):13001–13024
Singh AK, Dave M, Mohan A (2014) Hybrid technique for robust and imperceptible image watermarking in DWT-DCT-SVD domain. Natl Acad Sci Lett 37 (4):351–358
Singh AK, Dave M, Mohan A (2016) Hybrid technique for robust and imperceptible multiple watermarking using medical images. Multimed Tools Appl 75 (14):8381–8401
Singh AK, Dave M, Mohan A (2015) Robust and secure multiple watermarking in wavelet domain. Journal of Medical Imaging and Health Informatics 5(2):406–414
Singh AK, Kumar B, Dave M, Mohan A (2015) Robust and imperceptible dual watermarking for telemedicine applications. Wirel Pers Commun 80(4):1415–1433
Singh AK, Kumar B, Singh SK, Ghrera SP, Mohan A (2016) Multiple watermarking technique for securing online social network contents using Back Propagation Neural Network. Future Generat Comput Syst. Elsevier. https://doi.org/10.1016/j.future.2016.11.023
Singh S, Rathore VS, Singh R (2017) Hybrid NSCT domain multiple watermarking for medical images. Multimed Tools Appl 76(3):3557–3575
Singh S, Rathore VS, Singh R, Singh MK (2017) Hybrid semi-blind image watermarking in redundant wavelet domain. Multimed Tools Appl 76(18):19113–19137
Singh AK, Kumar B, Singh G, Mohan A (eds) (2017) Medical image watermarking: techniques and applications. Springer, Berlin
Su Q, Chen B (2017) Robust color image watermarking technique in the spatial domain. Soft Comput 22(1):91–106
Urvoy M, Goudia D, Autrusseau F (2014) Perceptual DFT watermarking with improved detection and robustness to geometrical distortions. IEEE Trans Inf Forensics Secur 9(7):1108–1119
Wang SH, Lin YP (2004) Wavelet tree quantization for copyright protection watermarking. IEEE Trans Image Process 13(2):154–165
Wang Z, Bovik AC, Sheikh HR, Simoncelli EP (2004) Image quality assessment: from error visibility to structural similarity. IEEE Trans Image Process 13(4):600–612
Weber AG (1997) The usc-sipi image database: http://sipi.usc.edu/services/database/Database.html. Signal and Image Processing Institute at the University of Southern California
Xiao D, Shih FY (2012) An improved hierarchical fragile watermarking scheme using chaotic sequence sorting and subblock post-processing. Opt Commun 285(10):2596–2606
Zear A, Singh AK, Kumar P (2018) A proposed secure multiple watermarking technique based on DWT, DCT and SVD for application in medicine. Multimed Tools Appl 77(4):4863–4882
Zhang Q, Li Y, Wei X (2012) An improved robust and adaptive watermarking algorithm based on dct. Journal of Applied Research and Technology 10(3):405–415
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Hamidi, M., Haziti, M.E., Cherifi, H. et al. Hybrid blind robust image watermarking technique based on DFT-DCT and Arnold transform. Multimed Tools Appl 77, 27181–27214 (2018). https://doi.org/10.1007/s11042-018-5913-9
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-018-5913-9