Abstract
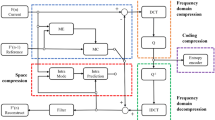
A joint encryption and authentication scheme for HEVC compressed video is proposed in this work. It produces a HEVC format compliant video stream that permits the authentication process to be carried out irregardless of the video being in the encrypted or plaintext (i.e., decrypted) form. To achieve this separable property, one set of syntax elements within the HEVC standard is utilized to achieve authentication, while another set is exploited for encryption. Specifically, for authentication, information such as coding unit size in each video slice is utilized to generate the authentication code, which is then embedded into each video slice to detect the tampered regions. A two-level authentication method is implemented to facilitate the legitimacy verification process. On the other hand, for video encryption, syntax elements in the HEVC standard including Sign Bins, Transform Skip Bins and Suffix Bins are randomized to perceptually distort the video. Experiment results show that by using the proposed encryption modules, the perceptual quality of the plaintext video can be distorted, and the distorted video can be restored to the original HEVC compressed video. Furthermore, the proposed joint scheme is verified to be viable in detecting and localizing the tampered regions. Finally, a pragmatic comparison among the proposed and conventional joint schemes is performed.








Similar content being viewed by others
References
Alassaf N, Alkazemin B, Gutub A (2017) Applicable light-weight cryptography to secure medical data in iot systems. Journal of Research in Engineering and Applied Sciences
Aljuaid N, Gutub A (2014a) 2-layer security system for hiding sensitive text data on personal computers. Lect Notes Inf Theory 2(2):151–157
Aljuaid N, Gutub A (2014b) Flexible stego-system for hiding text in images of personal computers based on user security priority. Proc 2014 Int Conf Adv Eng Technol 2(2):250–256
Aljuaid N, Gutub A, Khan E (2015) Stego-system for hiding text in images of personal computers. 12th Learning and Technology Conference: Wearable Tech / Wearable Learning
Atrey P K, Saddik A E, Kankanhalli M (2009) Digital video authentication hershey: IGI Global. United State of America, Hershey
Bjøntegaard G (2001) VCEG-M33: Calculation of average PSNR differences between RD curves. Technical report, Video Coding Experts Group (VCEG). United State of America, Austin
Gutub A A A (2010) Pixel indicator technique for rgb image steganography. J Emerg Technol Web Intell 2(1):56–64
Gutub AAA, Khan FAA (2012) Hybrid crypto hardware utilizing symmetric-key & public-key cryptosystems. International Conference on Advanced Computer Science Applications and Technologies
Hofbauer H, Uhl A, Unterweger A (2014) Transparent encryption for HEVC using bit-stream-based selective coefficient sign encryption. In: Proceeding of IEEE International Conference on Acoustic, Speech, Signal Processing, pp 1986–1990
ISO (2013) Information technology – High efficiency coding and media delivery in heterogeneous environments – part 2: High efficiency video coding. ISO/IEC 23008-2:2013 International Organization for Standardization, Geneva, Switzerland
Karim M S A, Wong K (2015) Data embedding in random domain. Signal Process 108:56–68
Khan F, Gutub A (2007) Message concealment techniques using image based steganography. 4th IEEE GCC Conference and Exhibition
Kundur D, Karthik K (2004) Video fingerprinting and encryption principles for digital rights management. Proc IEEE 92:918–932
Ma S, Huang Q, Zhang M, Yang B (2015) Efficient public key encryption with equality test supporting flexible authorization. IEEE Trans Inf Forensic Secur 10 (3):458–470
NIST (2002) Secure Hash Standard. FIPS PUB 180-2, National Institute of Standards and Technology, Gaithersburg
Ong S, Wong K, Qi X, Tanaka K (2015a) Beyond format-compliant encryption for {JPEG} image. Signal Process: Image Commun 31:47–60
Ong S, Wong K, Tanaka K (2015b) Scrambling-embedding for JPEG compressed image. Signal Process 109:38–53
Qian Z, Zhang X (2016) Reversible data hiding in encrypted images with distributed source encoding. IEEE Trans Circ Syst Video Technol 26(4):636–646
Rad R M, Wong K, Guo J M (2014) A unified data embedding and scrambling method. IEEE Trans Image Process 23(4):1463–1475
Shahid Z, Puech W (2014) Visual protection of hevc video by selective encryption of cabac binstrings. IEEE Trans Multimed 16:24–36
Stallings W (2010) Cryptography and network security: principles and practice, 5th edn. Prentice Hall Press, Upper Saddle River
Sullivan G J, Ohm J R, Han W J, Wiegand T (2012) Overview of the high efficiency video coding (HEVC) standard. IEEE Trans Circ Syst Video Technol 22 (12):1649–1668
Sze V, Budagavi M (2012) High throughput CABAC entropy coding in HEVC. IEEE Trans Circ Syst Video Technol 22:1778–1791
Tew Y, Wong K (2014) Information hiding in HEVC standard using adaptive coding block size decision. In: IEEE International Conference on Image Processing (ICIP), pp 5502–5506
Tew Y, Wong K, Phan R C W, Ngan K N (2016) Multi-layer authentication scheme for hevc video based on embedded statistics. J Vis Commun Image Represent 40:502–515
Vivienne Sze GJS, Budagavi M (2014) High efficieny video coding (HEVC): Algorithms and architectures, 1st edn. Springer International Publishing, Berlin
Waddilove R (2015) Best free video editing software 2016 uk. http://www.pcadvisor.co.uk/test-centre/photo-video/best-free-video-editing-software-2016-3614829/, [Accessed 1-April-2016]
Wien M (2014) High efficieny video coding: Coding tools and specification, 1st edn. Springer-Verlag, Berlin Heidelberg
Zhang X (2012) Separable reversible data hiding in encrypted image. IEEE Trans Inf Forensic Secur 7(2):826–832
Zhou J, Sun W, Dong L, Liu X, Au O C, Tang Y Y (2016) Secure reversible image data hiding over encrypted domain via key modulation. IEEE Trans Circ Syst Video Technol 26(3):441–452
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Tew, Y., Wong, K., Phan, R.CW. et al. Separable authentication in encrypted HEVC video. Multimed Tools Appl 77, 24165–24184 (2018). https://doi.org/10.1007/s11042-018-5611-7
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-018-5611-7