Abstract
A lot of watermarking algorithms for vector geographic data are presented in the literature. Due to widely application of digital watermarking, more demands are required, such as multiple watermarking algorithm. However, vector geographic data attracted less research focus on multiple watermarking. Consequently, a multiple watermarking algorithm for vector geographic data is proposed. In particular, the vertices are mapped to the logic domains firstly based on the constructed function. Then every domain is subdivided into blocks according to dichotomy and the number of embedding watermarks. Then, every watermark is embedded in the corresponding block. During the watermark detection, the watermarks are detected without the original vector geographic data. Finally, the experiments are made to test the multiple watermark capacity and robustness against attacks, with an emphasis on cropping attacks. The experimental results show that the proposed algorithm has good robustness against common attacks, such as, data simplification, vertex addition, vertex deletion, feature deletion, and cropping attacks. Moreover, the algorithm provides high multiple watermark capacity.
Similar content being viewed by others
1 Introduction
Digital watermarking has been used to protect the vector geographic data for more than ten years. Many watermarking algorithms have been proposed for vector geographic data [4, 9,10,11,12, 18, 19, 21, 22, 24, 25, 29]. With the rapid development of information technologies, more approaches are required for copyright protection. For example, data producers may update vector geographic data, and each version is marked with an identifier in the upgrade process. The data may be distributed to multiple parties in confidential environments, and every party marks the data to confirm authorization. Therefore, it is necessary to embed multiple watermarks in the data. Due to the data size of cover data, the number of embedding watermarks is restricted. Meanwhile, cropping is a typical operation for vector geographic data. One or several watermarks in the data may be removed after a cropping attack. However, because of the requirement of multiple authorizations, any damage to any watermark is undesired. This means that all watermarks should be preserved after cropping the vector geographic data.
However, current multiple watermarking algorithms commonly focus on multimedia as described in the [1, 2, 14,15,16, 20, 27, 28]. Multiple watermarking algorithm for vector geographic data are rarely investigated. To the best of our knowledge, only a few previous works have been proposed on this specific topic: for instance, in [23], two watermarks are combined into one composite watermark, and the new watermark is then embedded in the cover data using the DFT algorithm. The two watermarks must be provided before embedding and affect each other. In [13], the coordinates are recorded when the first watermark is embedded. According to the record, the other watermarks can be embedded again. In the watermark detection procedure, the original data and the record are required, and this process is not blind. In [3], four multiple watermarking algorithms are designed for GIS vector data. The first algorithm embeds two watermarks in the DCT domain and DFT domain. The second is based on frequency division, in which the watermarks are embedded in low, intermediate, or high frequency respectively. The third algorithm divides the data into different blocks to embed the watermarks, drawing on the algorithms of other scholars. In addition, the fourth is a combination of single watermarking and zero-watermarking algorithms. The watermark capacity is limited and is not robust to cropping attacks. In [31], the first watermark is embedded in the spatial domain, and the second watermark is embedded in the DFT domain. The embedding order cannot be changed. Cui proposed three methods in his doctorate dissertation [7]. The first is to embed the watermarks in both the X and Y coordinates. Thus, just two watermarks can be embedded in the cover data. The second is to combine all watermarks into one before embedding. These two methods require as a precondition that all watermarks are provided. To overcome these restrictions, the third method is to divide the cover data into blocks according to a quad-tree algorithm and to embed watermarks in different blocks. However, the algorithm in [7] has a limited applicability because it is weakness against cropping attacks. In [26], several watermarks are embedded in the same coordinates one by one by using additive embedding rule. In addition, the original data are required in detection process.
To preserve all watermarks in the watermarked data after cropping, we proposed a multiple watermarking algorithm to defend against cropping attacks for vector geographic data. The mapping relationships between the vertex coordinates, the logic domains, and the watermark bit indexes are first established. Then, the logic domains are subdivided into blocks to embed multiple watermarks. Since the mapping relationships are built before subdividing the blocks, the embedded watermarks are difficult to remove in a cropping attack. For the mapping and subdividing methods, high capacity is achieved as well.
The remaining sections are organized as follows. Section 2 presents the multiple digital watermarking algorithm. Section 3 provides the experimental results of the algorithm. The conclusions are summarized in Section 4.
2 The proposed multiple watermarking algorithm
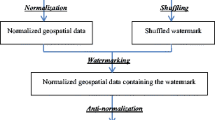
In a multiple watermarking algorithm, the watermarks can be embedded into the cover data step by step or simultaneously. The approach that embedding the watermarks step by step can be used for multi-user tracking and is more flexible than embedding the watermarks simultaneously. Therefore, we proposed a multiple watermark algorithm that embeds the watermarks step by step. Figure 1 shows the whole procedure of the algorithm.
2.1 Watermark generation
To improve the multiple watermark capacity and the watermark detection reliability, we use pseudorandom binary sequence as the watermarks. The pseudorandom sequence builder is used to generate watermarks. In the watermark generation, the watermark seed is generated, usually a random integer, and then, the pseudorandom binary sequence to be used as a watermark is generated based on the watermark seed. The watermarks are different due to the use of different watermark seeds. A watermark is W j = {w j [i], 0 ≤ i < L}, where 0 ≤ j < N, N is the number of watermarks, i is the watermark index, L is the length of the watermark, and w j [i] is the ith watermark bit of the jth watermark. Additionally, w j [i] ∈ {−1, 1},P(w j [i] = − 1) = 1/2, and P j (w[i] = 1) = 1/2,which means that w j [i] = − 1and w j [i] = 1 have the same probability, which is equal to 1/2. Figure 2 shows an example of the relationship between the watermark seed, the watermark, the watermark bits, and the watermark bit indexes.
2.2 Watermark embedding
2.2.1 Coordinate mapping and domain subdivision
The vector geographic data consist of the vertex coordinates. Vertex coordinates are the fundament units of points, polylines, and polygons that describe geographical objects, such as wells, rivers, and residential areas. Generally, digital watermarking is categorized into spatial domain [4, 10, 11] and frequency domain algorithms [12, 21]. Vertex coordinates provide the space for embedding watermark in two kinds of watermarking algorithms. The difference between these algorithms is that the watermark is embedded directly, either modifying the vertex coordinates or not. In addition, the spatial domain algorithm has good robustness against common attacks, such as vertex addition, vertex deletion, simplification, and cropping attacks. Additionally, the spatial domain algorithm based on vertex coordinate mapping is a good method for resisting cropping attack [30].
The range of vertex coordinates in the map changes with different maps. It is difficult to directly establish a stable relationship between vertex coordinates and watermark bit index. Therefore, the logic domain is defined artificially, which means fixed domain where the vertex coordinates are mapped to. And the logic domain is used as mediation to establish the mapping relationships between vertex coordinates and watermark bit index. For embedding multiple watermarks in a 2D vector geographic map, the logic domains are subdivided into blocks to embed different watermarks. Because the watermarks are embedded one by one, we use the dichotomy method to divide the logic domains for embedding watermarks as more as possible. The specific process is depicted as follows:
-
1.
Let the vertex coordinates of the vector geographic data be the setVC, and VC = {vc i | (x i , y i ), 0 ≤ i < M}, where M is the number of vertex coordinates, and (x i , y i )is the coordinate of the ith vertex. Let the logic domains be the set LD, and LD = {ld i , 0 ≤ i < N}. According to the following method, the mapping relationship is established. Figure 3 presents the process of coordinate mapping.
-
First, VC is mapped into the region with the size of R_x × R_y, where R_x < < OM_x, and R_y < < OM_y. OM_x and OM_y are respectively the width and height of the bounding rectangle for the map.
-
Second, the region is divided into NR × NC logic domains, ld i , according to Eq. (1), where NR × NC = L.
R_x,R_y,LD_x, and LD_y are all positive integers. Additionally, R_x can divide LD_x, and R_y can divide LD_y.
-
Finally, let kr_iand kc_i be the logic domain index where the coordinate (x i , y i ) is mapped to, and
where sc is a parameter controlling the distortions to the cover data after embedding the watermark. % represents complementation. ⌊a⌋ is the greatest integer that is smaller than a. Then, the mapping relationship between the logic domain in the kr_ith row and the kc_ith column and the watermark bit index, k, is
-
2.
According to the number of watermarks, N, every logic domain, ld i , is subdivided intoNblocks in a step by step process, which is shown in Fig. 4. Every block is embedded in the corresponding watermark, ld i_j (w j [i]), where 0 < j ≤ N, 0 ≤ i < L. In the process of watermark embedding, we use a quantization scheme so that the watermark currently being embedded will replace the existing watermark.
2.2.2 Embedding multiple watermarks
In the embedding process, the same watermark bit is repeatedly embedded into the coordinates that are in the block corresponding to a given index. Additionally, correspondent watermarks are successively embedded in the blocks in every logic domain. These watermarks purportedly provide robustness against cropping attacks. For instance, in Fig. 5, if the coordinates in the gray rectangles are cropped, the W 4 will not be removed.
The embedding process is described as follows. First, the mapping relationship is established according to the Section 2.2.1. Second, every mapping logic domain is subdivided into N blocks according to the number of watermarks. Finally, a quantization embedding algorithm is adopted in the program for embedding every watermark bit [5]. The Fig. 6 describes the embedding process for the watermark.
2.3 Watermark extraction and detection
Usually, the number of watermarks in the detected data is uncertain, so heuristic detection is adopted to detect potential multiple watermarks from the detected data in this paper. During watermark extraction and detection, these steps are followed.
-
1.
Let u, Ube the counts for statistics. u = 1, U = 64. Let the extracted watermarks be W ′, and W ′ = ∅.
-
2.
Suppose there are uwatermarks in the detected data. According to u, the subdividing blocks of every logic domain, ld i , are calculated.
-
3.
Extract the uwatermarks from the detected data according to the above logical domain subdivision. Figure 7 shows the process of extracting every watermark.
-
4.
Detect the watermarks by calculating correlated detection between the extracted watermark and original watermark as shown in Eq. (5). Let the detected watermarks be W ″, and let W ′ = W ′ ∪ W ″.
-
5.
Then, let u = u + 1. If u ≤ U, repeat the previous steps beginning with step 2. If u > U, the watermark extraction and detection processes are finished, and W ′contain all the watermarks detected from the detected data.
u is the supposed number of watermarks in current watermark detection, and U is the maximum probable number of watermarks. U = 64 in the experiments in Section 3.
After watermark extraction, the watermark is detected based on correlated detection. Let cor be the correlation coefficient between W j and \( {W}_j^{\prime } \), which is shown in Eq. (4).
If there is no watermark in the detected data, the extracted watermark bit \( {w}_j^{\prime}\left[\mathrm{i}\right] \) satisfies \( P\left({w}_j^{\prime}\left[\mathrm{i}\right]=1\right)=1/2 \) and \( P\left({w}_j^{\prime}\left[\mathrm{i}\right]=-1\right)=1/2 \). Therefore, the correlation coefficient, cor, has a distribution that can be approximated by a normal distribution, as shown in Eq. (5).
In the watermark detection, we can calculate the detection threshold by controlling the false positive rate (FPR). A 4∗ σ principle was used to calculate watermark detection threshold in this paper to ensure that FPR is less then10−4.
If the cor is bigger than the detection threshold, W j is present in the detected data.
3 Experimental results and analysis
The experiments were performed on different digital vector geographic maps in shapefile format, which were provided by GeoMarking Company [17]. The maps are organized as points, polylines, and polygons. Figure 8 shows three examples of these maps.
As a robust watermarking algorithm, the robustness of the proposed algorithm was first analyzed with respect to the common attacks in the first experimental stage. Following the robustness test, cropping attacks on the multiple watermarking algorithm were analyzed. In the second experimental stage the multiple watermark capacity of the algorithm was demonstrated.
3.1 Algorithm robustness
The algorithm robustness for vector geographic data refers to the ability to detect the watermark after common operations [6], such as data simplification, randomly adding or deleting vertices, deleting features (for example, a polyline in the map), and cropping.
In the experimental procedure, the four different watermarks were first embedded in the experimental map as shown in the Fig. 8(b). Then, the aforementioned operations were carried out on the watermarked maps. Finally, the watermarked maps after the attacks were assessed for whether the watermarks were present. The results are shown in Table 1. √ indicates that there is a corresponding watermark in the data after the attack, and × indicates the opposite result. The same experiments are made by using the other 29 experimental maps, and the experimental results are in accordance with the Table 1.
In the test case, the Douglas-Peucker method [8] was adopted to simplify the watermarked maps, and the simplification percentage is the ratio of the simplified data to the original data. The simplification attack is shown in Fig. 9. A vertex addition attack is where vertices are added to the watermarked maps randomly; vertex deletion involves deleting vertices from the watermarked maps randomly; a feature deletion attack denotes deleting features from watermarked data randomly (as shown in Fig. 10); and a data cropping attack is where regions of the watermarked data are cropped, and the cropping percentage refers to the ratio of the cropped data to the original data.
Furthermore, the vector sketch maps are used as experimental data to test the algorithm robustness, and Fig. 11 shows one example of the experimental maps. The experimental procedures, which are the same as above, are carried out using 10 different vector sketch maps, and the experimental results for Fig. 11 are shown in Table 2. The experimental results for other sketch maps are in accordance with Table 2.
Based on the experimental results listed in Tables 1 and 2, we can see that the proposed algorithm has good robustness against the attacks, such as data simplification, vertex addition, vertex deletion, feature deletion, and cropping. In addition the algorithm is suitable for different types of vector geographic data.
3.2 The robustness of the algorithm against a cropping attack
The main concept of common multiple watermarking algorithms is embedding the watermarks in non-overlapping regions. As a result, any watermark is easily removed after an unnoticed cropping attack. We demonstrate the robustness against cropping attacks in this section. Four watermarks were embedded in 10 vector geographic maps using the proposed algorithm. Then, the discretionary regions were cropped from the maps. Figure 12 shows four examples of cropping for the experimental vector geographic map. Meanwhile, the same 4 watermarks were embedded in the same 10 experimental maps by using the algorithm in [7]. In addition, the same cropping attacks were carried out on the watermarked maps. The above algorithm is an improved dividing blocks algorithm using a quad-tree method. The experimental results are listed in Table 3. In Table 3, a √ indicates that the watermark in present in the data after the attack, and × indicates the opposite result.
From the results shown in Table 3, we can observe that due to establish the logic domains by building the mapping relationship before subdivision, the proposed algorithm preserves the all of the watermarks in the watermarked map after cropping. Since a few watermarks are lost after the cropping attack when using the algorithm in [7], the robustness of this method against a cropping attack on the proposed algorithm is superior to that of the algorithm in [7].
3.3 Multiple watermark capacity
The multiple watermark capacity of multiple watermarking algorithm is the maximum number of watermarks that can be embedded. Generally, more watermarks can be embedded in maps with a greater data size (i.e., a greater number of vertex coordinates in the maps). Therefore, we chose 10 experimental maps that have different data sizes and that are either in point, polyline, or polygon maps.
In the experimental procedure, the watermarks were embedded in 10 vector geographic maps by using the proposed algorithm and the algorithm in [7]. The program did not stop until no additional watermarks could be embedded in the cover maps. Meanwhile, the number of watermarks embedded in these maps was recorded. Then, the detection of multiple watermarks was carried for the testing maps. With respect to practical applications, we set the maximum number of embedded watermarks to be 64 in our experiments. The experimental results are listed in Table 4. A √ indicates that all watermarks can be detected. In the experiments, L = 200.
For the results listed in Table 4, we can observe that number of embedded watermarks increases when the data size of the maps becomes larger, and all watermarks can be detected from the watermarked maps. The proposed algorithm is superior to the reference [7] algorithm in terms of multiple watermark capacity, primarily because the proposed algorithm uses the dichotomy method to subdivide the embedding region, while the reference [7] algorithm adopts the quad-tree method. However, due to the dichotomy method, the watermark number is not directly proportional to the map data size. For example, Map 3 and Map 4, which have different number of vertices, can be accommodated 4 watermarks. For the subdivision method shown in Fig. 4, the fifth block is 1/8th of the domain, so the coordinates in the fifth block are the 1/8 of 1224, i.e., 153. In addition, 153 is fewer than the length of the watermarks, 200, which means that the fifth watermark can not be embedded in the fifth block. For this reason, Map 4 accommodates only 4 watermarks instead of 6 watermarks. Consequently, the multiple watermark capacity is related to the data size and the length of the watermark. Additionally, the multiple watermark capacity of the proposed algorithm is sufficient for vector geographic data with common data sizes.
To analyze the relationship between L and N, let L = 100, L = 300, and L = 400. Then, the above experimental procedures are repeated, and the experimental results are shown in Tables 5, 6, and 7.
From the results listed in Tables 5, 6, and 7, the multiple watermark capacity is basically proportional to data size, which is accordance with the results in Table 4. According to the results in Tables 4, 5, 6, and 7, multiple watermark capacity is inversely proportional to the length of the watermark. That is, the multiple watermark capacity becomes larger as the length of each watermark becomes shorter.
4 Conclusions
We proposed a multiple watermarking algorithm for vector geographic data using vertex coordinates mapping and logic domain subdivision. The algorithm aims to improve the robustness against common attacks with an emphasis on cropping attacks. To address these issues, we first mapped the vertex coordinates to the logic domains. Then, based on the dichotomy method and the proposed rules, each logic domain was subdivided into blocks according to the number of watermark, and multiple watermarks were embedded into the corresponding blocks one by one. In the experimental validation, the results showed that the proposed algorithm has good performance on the robustness and multiple watermark capacity.
There are two drawbacks to the proposed algorithm. One drawback is that the multiple watermark capacity is decreased as the data size data becomes small, and another drawback is that the proposed algorithm lacks robustness against geometric transformation (such as rotation, scaling and translation). Our intention for future work is to increase the multiple watermark capacity for vector geographic maps with few vertices and to improve the robustness against geometric transformation attacks.
References
Bhatnagar G, QMJ W (2015) A new robust and efficient multiple watermarking scheme. Multimedia Tools and Applications 74(19):8421–8444. https://doi.org/10.1007/s11042-013-1681-8
Cai LJ, Li R, Yi YQ (2012) A multiple watermarks algorithm for image content authentication. J Cent South Univ 19(10):2866–2874. https://doi.org/10.1007/s11771-012-1353-2
Cao JH, Li AB, Lv GN (2010) Study on Multiple Watermarking Scheme for GIS Vector Data. In Proceedings of 18th International Conference on Geo-informatics. doi:10.1109/GEOINFORMATICS.2010.5568201
Cao L, Men C, Gao Y (2013) A recursive embedding algorithm towards lossless 2D vector map watermarking. Digital Signal Processing 23(3):912–918. https://doi.org/10.1016/j.dsp.2012.11.007
Chen B, Wornell GW (2001) Quantization index modulation: a class of provably good methods for digital watermarking and information embedding. IEEE Trans Inf Theory 47(4):1423–1442. https://doi.org/10.1109/18.923725
Cox IJ, Miller ML, Bloom JA (2002) Digital Watermarking. Morgan Kaufmann, San Diego
Cui HC (2013) Research on the Sharing Security of Vector Geography Data. Dissertation, Nanjing Normal University
Douglas DH, Peucker TK (1973) Algorithms for the reduction of the number of points required to represent a digitized line or its caricature. Cartographica: The International Journal for Geographic Information and Geovisualization 10(2):112–122. https://doi.org/10.3138/fm57-6770-u75u-7727
Hwan Il K, Kab Il K, Jong Uk C (2002) A vector watermarking using the generalized square mask. In Proceedings of the International Conference on Information Technology: Coding and Computing, 234–236
Lee SH, Kwon KR (2013) Vector watermarking scheme for GIS vector map management. Multimedia Tools and Applications 63(3):757–790. https://doi.org/10.1007/s11042-011-0894-y
Lee SH, Huo XJ, Kwon KR (2014) Vector watermarking method for digital map protection using arc length distribution. IEICE Trans Inf Syst E97-D(1):34–42. https://doi.org/10.1587/transinf.E97.D.34
Li YY, Xu LP (2003) A blind watermarking of vector graphics images. In: Proceedings of the 5th International Conference on Computational Intelligence and Multimedia Applications, 424–429
Li Q, Min LQ, He ZH, Yang YQ (2011) A solution research on multiple watermark embedding. Science of Surveying and Mapping 36(2):119–120. 10.16251/j.cnki.1009-2307.2011.02.022
Liao X, Shu CW (2015) Reversible data hiding in encrypted images based on absolute mean difference of multiple neighboring pixels. J Vis Commun Image R 28:21–27. https://doi.org/10.1016/j.jvcir.2014.12.007
Liao X, Li KD, Yin JJ (2017) Separable data hiding in encrypted image based on compressive sensing and Discrete Fourier Transform. Multimedia Tools and Applications 76(20):20739–20753. https://doi.org/10.1007/s1104
Luo H, FX Y, Chu SC, ZM L (2009) Hiding multiple watermarks in transparencies of visual cryptography. International Journal of Innovative Computing Information and Control 5(7):1875–1881. https://doi.org/10.1109/IIHMSP.2007.4457550
Nanjing GeoMarking Information Technolony Co., Ltd (2017). http://www.geomarking.cn/. Accessed 24 Apr 2017
Ohbuchi R, Ueda H, Endoh S (2002) Robust watermarking of vector digital maps. In: Proceedings of 2002 I.E. International Conference on Multimedia and Expo, 577–580
Peng Z, Yue M, Wu X, Peng Y (2015) Blind watermarking scheme for polylines in vector geo-spatial data. Multimedia Tools and Applications 74(24):11721–11739. https://doi.org/10.1007/s11042-014-2259-9
Roy S, Pal AK (2017) A blind DCT based color watermarking algorithm for embedding multiple watermarks. AEU-Int J Electron Commun 72:149–161. https://doi.org/10.1016/j.aeue.2016.12.003
Shao CY, Wang HL, Niu XM, Wang XT (2006) A shape-preserving method for watermarking 2d vector maps based on statistic detection. IEICE Trans. Inf. Syst. E89-D:1290–1293. https://doi.org/10.1093/ietisy/e89-d.3.1290
Solachidis V, Nikolaidis N, Pitas I (2000) Watermarking polygonal lines using Fourier descriptors. In: 2000 I.E. International Conference on Acoustics, Speech, and Signal Processing, 1955–1958
Sun JG, Men CG, Zhang GY (2010) Static dual watermarking of vector maps to anti-interpretation attacks. Journal of Harbin Engineering University 31(4):488–495. https://doi.org/10.3969/j.issn.1006-7043.2010.04.014
Voigt M, Yang B, Busch C (2004) Reversible watermarking of 2D–vector data. In: Proceedings of the Multimedia and Security Workshop 2004, 160–165
Wang NN, Zhao XJ (2017) 2D vector map data hiding with directional relations preservation between points. AEU-Int J Electron Commun 71:118–124. https://doi.org/10.1016/j.aeue.2016.10.010
Wang YY, Yang CS, Zhu CQ, Ren N, Chen P (2017) A Novel Multiple Watermarking Algorithm Based on Correlation Detection for Vector Geographic Data. In Proceedings of Geo-Spatial Knowledge and Intelligence: 4th International Conference on Geo-Informatics in Resource Management and Sustainable Ecosystem, 429–436
Wong PHW, OC A, Yeung YM (2003) A novel blind multiple watermarking technique for images. IEEE Trans. Circuits Syst. Video Technol. 13(8):813–830. https://doi.org/10.1109/tcsvt.2003.815948
Xiong L, Xu Z, Xu Y (2016) A multiple watermarking scheme based on orthogonal decomposition. Multimedia Tools and Applications 75(10):5377–5395. https://doi.org/10.1007/s11042-015-2504-x
Yang CS, Zhu CQ (2011) Robust watermarking algorithm for geometrical transform for vector geo-spatial data based on invariant function. Acta Geodaetica Et Cartographica Sinica 40(2):256–261. 10.13203/j.whugis2011.12.012
Yang CS, Zhu CQ, Tao DX (2010) A blind watermarking algorithm for vector geo-spatial data based on coordinate mapping. Journal of Image and Graphics 15(4):684–688. 10.11834/jig.20100421
Zhang LM, Yan HW, Qi JX, Zhang YZ (2016) Multiple blind watermarking algorithm based on spatial-frequency domain for vector map data. J Geom 41(5):32–36. 10.14188/j.2095-6045.2016.05.008
Acknowledgements
The work was supported by the National Natural Science Foundation of China (grant No. 41401518), the Natural Science Foundation of Jiangsu Province (grant No. BK20140066), the special scientific research of public service industry on state surveying and mapping (grant No. 201512019), and a project funded by the Priority Academic Program Development of Jiangsu Higher Education Institutions.
Author information
Authors and Affiliations
Contributions
Yingying Wang and Chengsong Yang have worked jointly to develop this paper. Changqing Zhu reviewed the manuscript. All authors have read and approved the final manuscript.
Corresponding author
Ethics declarations
Conflicts of interest
The authors declare no conflict of interest.
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 4.0 International License (http://creativecommons.org/licenses/by/4.0/), which permits unrestricted use, distribution, and reproduction in any medium, provided you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made.
About this article
Cite this article
Wang, Y., Yang, C. & Zhu, C. A multiple watermarking algorithm for vector geographic data based on coordinate mapping and domain subdivision. Multimed Tools Appl 77, 19261–19279 (2018). https://doi.org/10.1007/s11042-017-5358-6
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-017-5358-6