Abstract
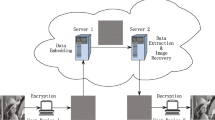
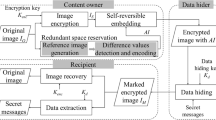
Encrypted image-based reversible data hiding methods have recently been introduced to conduct research on data encryption. In these methods, an image provider generates encrypted images that are supplied to a data sender. The data sender embeds secret data into the images in order to securely communicate with a data receiver. The data receiver can extract secret data and recover the cover image from the encrypted images. Past research has shown that attackers can easily become suspicious in such cases since all images are scrambled during communication. In this paper, we propose a reversible data hiding method that uses meaningful encrypted images. The proposed method is independent from image provider, data sender, and data receiver respectively by separating the images used and the secret data hidden from each other. In addition, the proposed method reduces distortion during image encryption, and features a data embedding scheme to conceal the existence of secret data from attackers. Experimental results show that the proposed method has high embedding capacity and yields satisfactory image quality with a meaningful image.












Similar content being viewed by others
References
Alattar M (2004) Reversible watermark using the difference expansion of a generalized integer transform. IEEE Trans Image Process 13(8):1147–1156
Al-Oershi OM, Khoo BE (2013) Two-dimensional difference expansion (2D-DE) scheme with a characteristics-based threshold. Signal Process 93:154–162
Alsmirat MA, Jararweh Y, Obaidat I, Gupta BB (2017) Internet of surveillance: a cloud supported large scale wireless surveillance system. J Supercomput 73(3):973–992
Alsmirat MA, Jararweh Y, Ayyoub M (2017) Accelerating compute intensive medical imaging segmentation algorithms using hybrid CPU-GPU implementations. Multimed Tools Appl 76(3):3537–3555
Atawneh S, Almomani A, Bazar HA, Sumari P (2017) Secure and imperceptible digital image steganographic algorithm based on diamond encoding in DWT domain. Multimed Tools Appl 76(18):18451–18472
Cao X, Du L, Wei X, Meng D (2016) High capacity reversible data hiding in encrypted images by patch-level sparse representation. IEEE Trans Cybern 46(5):1132–1143
Chan CK, Cheng LM (2004) Hiding data in images by simple LSB substitution. Pattern Recognit 37:469–474
Chang CC, Lin MH, Hu YC (2002) A fast and secure image hiding scheme based on LSB substitution. Int J Pattern Recognit 16:399–416
Chang KC, Huang PS, Tu TM, Chang CP (2007) Adaptive image steganographic scheme based on tri-way pixel-value differencing. IEEE Systems, Man and Cybernetics, pp 1165-1170
Chang KC, Huang PS, Tu TM, Chang CP (2007) Image steganographic scheme using try-way pixel-value differencing and adaptive rules. Intelligent Information Hiding and Multimedia Signal Processing, pp 449-452
Chen YC, Shiu CW, Horng G (2014) Encrypted signal-based reversible data hiding with public key cryptosystem. J Vis Commun Image Represent 25:1164–1170
Hong W, Chen TS, Wu HY (2012) An improved reversible data hiding in encrypted images using side match. Signal Process Lett 19(4):199–202
Hsiao JY, Chan KF, Chang JM (2009) Block-based reversible data embedding. Signal Process 89:556–569
Hu J, Li T (2015) Reversible steganography using extended image interpolation technique. Comput Electr Eng Comput Electr Eng 46:447–455
Hu Y, Lee HK, Li J (2009) DE-based reversible data hiding with improved overflow location map. IEEE Trans Circuits Syst Video Technol 19(2):250–260
Huang HC, Chang FC (2013) Hierarchy-based reversible data hiding. Expert Syst Appl 40(1):34–43
Huang HC, Fang WC (2011) Authenticity preservation with histogram-based reversible data hiding and quadtree concepts. Sensors 11(10):9717–9731
Huang LC, Tseng LY, Hwang MS (2013) A reversible data hiding method by histogram shifting in high quality medical images. J Syst Softw 86:716–727
Jana B (2016) High payload reversible data hiding scheme using weighted matrix. Optik 127:3347–3358
Jung KH, Yoo KY (2009) Data hiding method using image interpolation. Comput Stand Interfaces 31(2):465–470
Ker A (2005) Steganalysis of LSB matching in grayscale images. IEEE Signal Process Lett 12:441–444
Khodaei M, Faez K (2012) New adaptive steganographic method using least-significant-bit substation and pixel-value differencing. IET Image Process 6(5):677–686
Lee CF, Chen HC (2012) Adjustable prediction-based reversible data hiding. Digital Signal Process 22(6):941–953
Lee CF, Huang YL (2012) An efficient image interpolation increasing payload in reversible data hiding. Expert Syst Appl 39(8):6712–6719
Lee YP, Lee JC, Chen WK, Chang KC, Su IJ, Chang CP (2012) High-payload image hiding with quality recovery using tri-way pixel-value differencing. Inform Sci 191:214–225
Li X, Yang B, Zeng T (2011) Efficient reversible data watermarking based on adaptive prediction-error expansion and pixel selection. IEEE Trans Image Process 20(12):3524–3533
Li X, Li J, Li B, Yang B (2013) High-fidelity reversible data hiding scheme based on pixel-value-ordering and prediction-error expansion. Signal Process 93:198–205
Liao X, Wen QY, Zhang J (2011) A steganographic method for digital images with four-pixel differencing and modified LSB substitution. J Vis Commun Image Represent 22:1–8
Lin CC, Tai WL, Chang CC (2008) Multilevel reversible data hiding based on histogram modification of difference images. Pattern Recognit 41:3582–3591
Liu L, Chen T, Zhu S, Hong W, Si X (2016) A reversible data hiding method using improved neighbor mean interpolation and random-block division. Inf Technol J 13:2374–2384
Lu TC (2017) An interpolation-based lossless hiding scheme based on message recoding mechanism. Optik 130:1377–1396
Lu TC, Chang CC, Huang YH (2014) High capacity reversible hiding scheme based on interpolation, difference expansion and histogram methods. Multimedia Tools and Applications 72:417–435
Lu TC, Tseng CY, Wu JH (2015) Dual imaging-based reversible hiding technique using LSB matching. Signal Process 108:77–89
Lu TC, Lin MC, Huang CC, Deng KM (2016) Reversible data hiding based on image interpolation with a secret message reduction strategy. Int J Comput Softw Eng 1:102–112
Luo H, Yu FX, Chen H, Huang ZL, Li H, Wang PH (2011) Reversible data hiding based on block median preservation. Inform Sci 181:308–328
Ma K, Zhang W, Zhao X (2013) Reversible data hiding in encrypted images by reserving room before encryption. IEEE Trans Inf Forensics Secur 8(3):553–562
Malik A, Sikka G, Verma HK (2017) An image interpolation based reversible data hiding scheme using pixel value adjusting feature. Multimed Tools Appl 76(11):13025–13046
Marin J, Shih FY (2014) Reversible data hiding techniques using multiple scanning difference value histogram modification. J Inf Hiding Multimedia Signal Process 5(3):451–460
Mielikainen J (2006) LSB matching revisited. IEEE Signal Process Lett 13:285–287
Z. Ni, Y. Q. Shi, N. Ansari, and W. Su. (2003) Reversible data hiding. Proc. of International Symposium on Circuits and Systems, pp. 912-915
Qian Z, Zhang X (2016) Reversible data hiding in encrypted images with distributed source encoding. IEEE Trans Circuits Syst Video Technol 26(4):636–646
Sabeen GPV, Sajila MK, Bindiya MV (2016) A two stage data hiding scheme with high capacity based on interpolation and difference expansion. Procedia Technol 24:1311–1316
Tang M, Hu J, Song W, Zeng S (1745-1754) Reversible and adaptive image steganographic method. AEU Int J Electron Commun 69(12):2015
Thodi DM, Rodriguez JJ (2007) Expansion embedding techniques for reversible watermarking. IEEE Trans Image Process 16(3):721–730
Tian J (2003) Reversible data embedding using a difference expansion. IEEE Trans Circuits Syst Video Technol 13(8):890–896
Tsai YY, Chen JT, Kuo YC, Chan CS (2014) A generalized image interpolation-based reversible data hiding scheme with high embedding capacity and image quality. KSII Trans Internet Inf Syst 8(9):3286–3301
Wang RZ, Lin CF, Lin JC (2001) Image hiding by optimal LSB substitution and genetic algorithm. Pattern Recognit 34:671–683
Wang CM, Wu NI, Tsai CS, Hwang MS (2008) A high quality steganographic method with pixel-value differencing and modulus function. J Syst Softw 81:150–158
Weng SW, Pan JS (2014) Reversible watermarking based on eight improved prediction modes. J Inf Hiding Multimedia Signal Process 5(3):527–533
Wu DC, Tsai WH (2003) A steganographic method for images by pixel-value differencing. Pattern Recogn Lett 24:1613–1626
Wu NI, Wu KC, Wang CM (2002) Exploring pixel-value differencing and base decomposition for low distortion data embedding. Appl Soft Comput 12:942–960
Wu HC, Wu NI, Tsai CS, Hwang MS (2005) Image steganographic scheme based on pixel-value differencing and LSB replacement methods. IEE Processing Visualization, Image Signal Process 152:611–615
Yang CH, Weng CY (2006) A steganographic method for digital images by multi-pixel differencing. IEE International Computer Symposium, pp 831-836
Yang CN, Hsu SC, Kim C (2017) Improving stego image quality in image interpolation based data hiding. Comput Stand Interfaces 50:209–215
Zhang X (2011) Reversible data hiding in encrypted images. IEEE Signal Process Lett 18(4):255–258
Zhang X (2012) Separable reversible data hiding in encrypted image. IEEE Trans Inf Forensics Secur 7(2):826–832
Zhao Z, Luo H, Lu ZM, Pan JS (2011) Reversible data hiding based on multilevel histogram modification and sequential recovery. AEU Int J Electron Commun 65(10):814–826
Acknowledgments
The authors are grateful to anonymous reviewers for useful suggestions.
This research was supported by Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Education (No. 2015R1D1A1A01058019).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Shin, SH., Jung, KH. Reversible data hiding method using meaningful encrypted images. Multimed Tools Appl 77, 14841–14857 (2018). https://doi.org/10.1007/s11042-017-5065-3
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-017-5065-3