Abstract
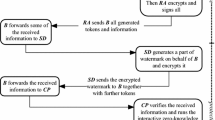
In the digital right management value chain, digital watermarking technology plays a very important role in digital product’s security, especially on its usage tracking and copyrights infringement authentication. However, watermark procedures can only effectively support copyright protection processes if they are applied as part of an appropriate watermark protocol. In this regard, a number of watermark protocols have been proposed in the literature and have been shown to facilitate the use of digital watermarking technology as copyright protection. One example of such protocols is the anonymous buyer-seller watermarking protocol. Although there are a number of protocols that have been proposed in the literature and provide suitable solutions, they are mainly designed as a watermarking protocol for the first-hand market and are unsuitable for second-hand transactions. As the complexity of online transaction increases, so does the size of the digital second-hand market. In this paper, we present a new buyer-seller watermark protocol that addresses the needs of customer’s rights problem in the digital secondary market. The proposed protocol consists of five sub-protocols that cover the registration process, watermarking process for the first, second and third-hand transactions as well as the identification & arbitration processes. This paper provides analysis that compares the proposed protocols with existing state-of-the-arts and shows that it has met not only all the buyer’s and seller’s requirements in the traditional sense but also accommodates the same requirements in the secondary market.






Similar content being viewed by others
References
Chen C, Chen C, Li D, Chen P (2015) A verifiable and secret buyer-seller watermarking protocol. IETE Tech Rev 32(2):104–113
Cox I, Bloom J, Miller M (2001) Digital watermarking: principles & practice. Morgan Kaufman, San Mateo
Frattolillo F (2007) Watermarking protocol for web context. IEEE Trans Inf Forensics Secur 2(3):350–363
Frattolillo F (2014) Watermarking protocol: problems, challenges and a possible solution. Comput J 58(4):944–960
Frattolillo F (2016) A buyer-friendly and mediated watermarking protocol for web context. ACM Trans Web 10(2):Article 9
Fu Z, Ren K, Shu J, Sun X, Huang F (2016) Enabling personalized search over encrypted outsourced data with efficiency improvement. IEEE Trans Parallel Distrib Syst 27(9):2546–2559
Gentry C (2009) A fully homomorphic encryption scheme. PhD dissertation, Department of Computer Science, Stanford University
Gittleson K (2012) US court to rule on ReDigi’s MP3 digital music resales. http://www.bbc.com/news/technology-19842851
Hu D, Li Q (2009) A secure and practical buyer-seller watermarking protocol. International Conference on Multimedia Information Networking and Security, 105–108, November, 2009
Hu Z, She K, Wang J, Tang J (2014) Game theory based false negative probability of embedded watermark under unintentional and steganalysis attacks. China Commun 11(5):114–123
Huang J, Jeng F, Chen T (2016) A new buyer-seller watermarking protocol without multiple watermarks insertion. Multimed Tools Appl 1–13
Katzenbeisser S (2001) On the design of copyright protection protocols for multimedia distribution using symmetric and public-key watermarking. 12th Internationalworkshop on database and expert systems applications 815–819
Khan KM, Malluhi Q (2010) Establishing trust in cloud computing. IT Professional 12(5):20–27
Khan M, Jeoti V, Malik A et al. (2011) A joint watermarking and encryption scheme for DCT based codecs. 17th Asia-pacific conference on communications, Malaysia
Langr D, Tvrdik P (2016) Evaluation criteria for sparse matrix storage formats. IEEE Trans Parallel Distrib Syst 27(2):428–440
Lei CL et al (2004) An efficient and anonymous buyer-seller watermarking protocol. IEEE Trans Image Process 13(12):1618–1626
Makbol N, Khoo B, Rassem T (2016) Block-based discrete wavelet transform-singular value decoomposition image watermarking scheme using human visual system characteristics. IET Image Process 10(1):34–52
Memon N, Wong PW (2001) A buyer-seller watermarking protocol. IEEE Trans Image Process 10(4):643–649
Nematollahi M, Haddad S (2013) An overview of digital speech watermarking. Int J Speech Technol 16(4):471–488
Ochi H, Ota T, Yamaoka A, Watanabe H, Kondo Y, Tokuda N, Taguchi H, Matsumoto T, Kobayashi H, Imai S (2013) Sealed mask ROM wafer with 5 mm magnetic resonant coupling for long-term digial data preservation. IEEE 26th International SOC Conference, 262–266, Erlangen, 4–6 Sep, 2013
Peng Y, Wang C, Fang Y, Li W (2012) Anonymous watermarking protocol for vector spatial data. International Conference on Computer Science & Service System, 2095–2098, Nanjing.
Qiao L, Nahrstedt K (1998) Watermarking schemes and protocols for protecting rightful ownership and customer’s rights. J Vis Commun Image Represent 9(3):194–210
Qin C, Chang C, Chiu Y (2014) A novel joint data-hiding and compression scheme based on SMVQ and image Inpainting. IEEE Trans Image Process 23(3):969–978
Qin C, Zhang X (2015) Effective reversible data hiding in encrypted image with privacy protection for image content. J Vis Commun Image Represent 31(C):154–164
Qin C, Chang C, Chen P (2012) Self-embedding fragile watermarking with restoration capability based on adaptive bit allocation mechanism. Signal Process 92(4):1137–1150
Ren Y, Shen J, Wang J, Han J, Lee S (2015) Mutual verifiable provable data auditing in public cloud storage. J Internet Technol 16(2):317–323
Rial A, Deng M, Bianchi T, Piva A, Preneel B (2010) A provably secure anonymous buyer-seller watermarking protocol. IEEE Trans Inf Forensics Secur 5(4):920–931
Rial A, Balasch J, Preneel B (2011) A privacy-preserving buyer-seller watermarking protocol based on priced oblivious transfer. IEEE Trans Inf Forensics Secur 6(1):202–212
Song C, Sudirman S, Merabti M (2012) A robust-adaptive dual image watermarking technique. J Vis Commun Image Represent 23:549–568
Waleed J, Hameed S, Huang D (2014) A robust optimal zero-watermarking technique for secret watermark sharing. Int J Secur Appl 8(5):349–360
Xia Z, Wang X, Sun X, Liu Q, Xiong N (2016a) Steganalysis of LSB matching using differences between nonadjacent pixels. Multimedia Tools Appl 75(4):1947–1962
Xia Z, Wang X, Zhang L, Qin Z, Sun X, Ren K (2016b) A privacy-preserving and copy-deterrence content-based image retrieval scheme in cloud computing. IEEE Trans Inf Forensics Secur 11(11):2594–2608
Zhang G, Ma Y (2010) Analysis on influence factors of digital preservation sustainability. Inform Sci (Chinese Journal) 28(11):1737–1740
Zhang X, Wang S, Qian Z, Feng G (2011) Reference sharing mechanism for watermark self-embedding. IEEE Trans Image Process 20(2):485–495
Zhou W, Bovik AC (2009) Mean square error: love it or leave it? A new look at signal fiedlity measures. IEEE Signal Process Mag 26(1):98–117
Zhou Z, Wang Y, Wu J, Yang C, Sun X (2016) Effective and efficient global context verification for image copy detection. IEEE Trans Inf Forensics Secur 12(1):48–63
Acknowledgements
The work was sponsored by Jiangnan University of Science & Technology Young Scholar Grant (No.JUSRP11462); Key Project of Jiangnan University Fund Grant (No. JUSRP51414A); the Priority Academic Program Development of Jiangsu Higher Education Institutions (PAPD) and Jiangsu Collaborative Innovation Center on Atmospheric Environment and Equipment Technology (CICAEET).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Song, C., Sang, J. & Sudirman, S. A buyer-seller watermarking protocol for digital secondary market. Multimed Tools Appl 77, 225–249 (2018). https://doi.org/10.1007/s11042-016-4247-8
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-016-4247-8