Abstract
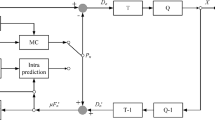
Aiming to protect H.264/AVC video in multimedia social network, a selective encryption scheme is put forward. In the scheme, after analyzing the impact of quantization parameter (QP) on the encryption of the sign of T1 s and the impact of encrypting inter-macroblock non-zero coefficients, the sign of intra-macroblock non-zero DCT coefficients, the sign of trailing ones (T1 s), the intra prediction modes (IPMs) and the sign of motion vector difference (MVD) are encrypted to protect the texture and motion information of H.264/AVC. Experimental results and analysis show that the computation cost is low and the bitrate increment is negligible, and it can achieve good performance in resisting brute-force attacks, histogram-based attacks and replacement attacks. Based on the encryption scheme, a framework of its implementation in multimedia social network is put forward. It has great potential to be implemented for the video data protection in multimedia social network.











Similar content being viewed by others
References
Ahn J, Shim H, Jeon B, Choi I (2004) Digital video scrambling method using intra prediction mode,” in Proc. PCM, LNCS 3333. pp. 386–393
Alvarez G, Li S (2006) Some basic cryptographic requirements for chaos-based cryptosystems. Int J Bifurcation Chaos 16(8):2129–2151
Au-Yeung SK, Zhu S, Zeng B (2009) Partial video encryption based on alternating transforms. IEEE Signal Process Lett 16(10):893–896
Draft ITU-T Recommendation and Final Draft International Standard of Joint Video Specification (ITU-T Rec. H.264/ISO/IEC 14496–10 AVC), document JVT-G050, Joint Video Team (JVT), Mar. 2003
Friedman WF (1987) The index of coincidence and its applications in cryptanalysis. Aegean Park Press, California
Fu Z, Sun X, Liu Q, Zhou L, Shu J (2015) Achieving efficient cloud search services: Multi-keyword ranked search over encrypted cloud data supporting parallel computing. IEICE Trans Commun E98-B(1):190–200
Furht B, Socek D, Eskicioglu A (2004) Multimedia security handbook. CRC Press, Boca Raton, pp. 93–131
Goldreich O (2009) Foundations of cryptography volume II basic applications. Cambridge University Press, New York, pp. 373–481
Hong G, Yuan C, Wang Y, Zhong Y (2006) A quality-controllable encryption for H.264/AVC video coding, in Proc. PCM, LNCS 4261. pp. 510–517
JM Reference Software, ver. 10.2 (2011) [Online]. Available: http://iphome.hhi.de/suehring/tml/download/old_jm/
Kwon S, Choi W, Jeon B (2005) Digital video scrambling using motion vector and slice relocation, in Proc. 2nd Int. Conf., ICIAR, pp. 207–214
Li Y, Jiang J, Liang L (2007) Research and improvement of the video encryption algorithm for H.264. Acta Electron Sin 35(9):1724–1727
Li X, Feng Z, Hu Y (2009) Video encrypting scheme based on H.264 CAVLC entropy coding. Comput Eng Appl 45(34):114–117
Lian S, Sun J, Wang Z (2004) Quality analysis of several typical MPEG video encryption algorithms. J Image Graph 9(4):483–490
Lian S, Liu Z, Ren Z, Wang H (2006) Secure advanced video coding based on selective encryption algorithms. IEEE Trans Consum Electron 52(2):621–629
Lian S, Sun J, Liu G, Wang Z (2008) Efficient video encryption scheme based on advanced video coding. Multimed Tools Appl 38(1):75–89
Liu F, Koenig H (2010) A survey of video encryption algorithms. Comput Secur 29(1):3–15
Liu Z, Li X (2004) Motion vector encryption in multimedia streaming, in Proc. 10th Int. Multimedia Modelling Conf., pp. 64–71
Liu Y, Yuan C, Zhong Y (2007) A new digital rights management system in mobile applications using H.264 encryption, in Proc. 9th Int. Conf. Advanced Communication Technology, pp. 583–586.
Peng F, Zhu X, Long M (2013) An ROI privacy protection scheme for H.264 video based on FMO and chaos. IEEE Trans. Inf Forensics Secur 8(10):1688–1699
Podesser M, Schmidt H, Uhl A (2002) Selective bitplane encryption for secure transmission of image data in mobile environments, in Proc. 5th IEEE Nordic Signal Process. Symp., pp. 4–6
Raju C, Srinathan K, Jawahar C (2008) A real-time video encryption exploiting the distribution of the DCT coefficients, in Proc. IEEE Region 10 Conf. (TENCON 2008), pp. 1–6
Ren Y, Shen J, Wang J, Han J, Lee S (2015) Mutual verifiable provable data auditing in public cloud storage. J Internet Technol 16(2):317–323
Shahid Z, Chaumont M, Puech W (2009) Fast protection of H.264/AVC by selective encryption, in Proc. SinFra IPAL Symp., pp. 11–21
Shahid Z, Chaumont M, Puech W (2011) Fast protection of H.264/AVC by selective encryption of CAVLC and CABAC for I and P frames. IEEE Trans Circuits Syst Video Technol 21(5):565–576
Stallings W (2011) Cryptography and network security, principles and practice, Fifth edn. Pearson, Upper Saddle River
Video Trace Library (2011) [Online]. Available: http://trace.eas.asu.edu/yuv/index.html
Wang Z, Bovik A (2009) Mean squared error: love it or leave it? A new look at signal fidelity measures. IEEE Signal Process Mag 26(1):98–117
Wang Z, Bovik A, Sheikh H, Simoncelli E (2004) Image quality assessment: from error visibility to structural similarity. IEEE Trans Image Process 13(4):600–612
Wang Y, Cai M, Tang F (2007) Design of a new selective video encryption scheme based on H.264, in Proc. Int. Conf. Computational Intelligence and Security, pp. 883–887
Wang Y, O’Neill M, Kurugollu F (2013) A tunable encryption scheme and analysis of fast selective encryption for CAVLC and CABAC in H.264/AVC. IEEE Trans Circuits Syst Video Technol 23(9):1476–1490
Wiegand T, Sullivan G, Bjontegaard G, Luthra A (2003) Overview of the H.264/AVC video coding standard. IEEE Trans Circuits Syst Video Technol 13(7):560–576
Xing S, Jiang J, Qi M (2009) An intra prediction mode-based video encryption algorithm in H.264, in Proc. Int. Conf. Multimedia Information Networking and Security (MINES ‘09), pp. 478–482
Xiph.org Video Test Media (2013) [Online]. Available: http://media.xiph.org/video/derf/
Zhang Z (2011) Digital rights management ecosystem and its usage controls: a survey. Int J Digital Content Technol Appl 5(3):255–272
Zhang Z (2012) Frontier and methodologies on digital rights management for multimedia social networks. Int J Digital Content Technol Appl 6(9):245–249
Acknowledgments
This work was supported in part by project supported by National Natural Science Foundation of China (Grant No. 61370225, 61572182), project supported by Hunan Provincial Natural Science Foundation of China (Grant No.15JJ2007), supported by the Scientific Research Plan of Hunan Provincial Science and Technology Department of China (2014FJ4161), supported by Project of the Priority Academic Program Development of Jiangsu Higher Education Institutions, and supported by Jiangsu Collaborative Innovation Center on Atmospheric Environment and Equipment Technology.
Thank for the reviewers and the guest editor for their kind suggestions.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Peng, F., Gong, Xq., Long, M. et al. A selective encryption scheme for protecting H.264/AVC video in multimedia social network. Multimed Tools Appl 76, 3235–3253 (2017). https://doi.org/10.1007/s11042-016-3710-x
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-016-3710-x