Abstract
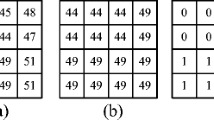
This paper presents two secret hiding schemes based on absolute moment block truncation coding (AMBTC). One is for embedding secrets into complex blocks and the other one is for smooth blocks. As for the smooth blocks, the small variation of the block is adopted to define the embedding rule to minimize the distortion after data embedding. As for the complex blocks, the large variation of the block is used to embed more secrets while maintaining good visual quality. In the experiments, when compared to Ou and Sun’s scheme, the positive data is to confirm the higher capacity while preserving better visual quality.











Similar content being viewed by others
References
Alturki F, Mersereau R (2001) Secure blind image steganographic technique using discrete Fourier transformation. In: 2001 International Conference on Image Processing, vol. 2, pp. 542–545
Balasubramanian C, Selvakumar S, Geetha S (2013) High payload image steganography with reduced distortion using coronary pixel pairing scheme. Multimedia Tool Appl: 1–23
Chan CK, Cheng LM (2004) Hiding data in images by simple LSB substitution. Pattern Recogn 37(3):469–474
Chang CC, Chen TS, Chung LZ (2002) A steganographic method based upon JPEG and quantization table modification. Inf Sci 141(1C2):123–138
Chang CC, Chen YH, Lin CC (2009) A data embedding scheme for color images based on genetic algorithm and absolute moment block truncation coding. Soft Comput 13(4):321–331
Chang CC, Kieu TD, Wu WC (2009) A lossless data embedding technique by joint neighboring coding. Pattern Recogn 42(7):1597–1603
Chang CC, Lin CY (2006) Reversible steganography for VQ-compressed images using side matching and relocation. IEEE Trans Inf Forensics Secur 1(4):493–501
Chang CC, Lin CY, Fan YH (2008) Lossless data hiding for color images based on block truncation coding. Pattern Recogn 41(7):2347–2357
Chen J, Hong W, Chen TS, Shiu CW (2010) Steganography for BTC compressed images using no distortion technique. Imaging Sci J 58(4):177–185
Chen B, Latifi S, Kanai J (1999) Edge enhancement of remote image data in the DCT domain. Image Vis Comput 17(12):913–921
Chen PY, Lin HJ (2006) A DWT based approach for image steganography. Int J Appl Sci Eng 4(3):275–290
Chuang JC, Chang CC (2006) Using a simple and fast image compression algorithm to hide secret information. Int J Comput Appl 28(4):329–333
Delp E, Mitchell O (1979) Image compression using block truncation coding. IEEE Trans Commun 27(9):1335–1342
Fridrich J, Goljan M, Du R (2001) Detecting LSB steganography in color, and gray-scale images. IEEE Multimedia 8(4):22–28
Guo JM, Lin CY (2010) Parallel and element-reduced error-diffused block truncation coding. IEEE Trans Commun 58(6):1667–1673
Guo JM, Liu YF (2010) Improved block truncation coding using optimized dot diffusion. IEEE Trans Image Process 23(3):2634–2637
Hashad AI, Madani AS, Wahdan A (2005) A robust steganography technique using discrete Cosine transform insertion. In: ITI 3rd International Conference on: Information and Communications Technology, 2005. Enabling Technologies for the New Knowledge Society, pp. 255–264
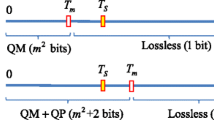
Hong W, Chen TS, Shiu CW (2008) Lossless steganography for AMBTC-compressed images. Int Congr Image Signal Process 2:13–17
Hu YC, Lo CC, Chen WL, Wen CH (2013) Joint image coding and image authentication based on absolute moment block truncation coding. J Electron Imaging 22(1):013,012–013,012
Kamstra L, Heijmans HJ (2005) Reversible data embedding into images using wavelet techniques and sorting. IEEE Trans Image Process 14(12):2082–2090
Lema M, Mitchell O (1984) Absolute moment block truncation coding and its application to color images. IEEE Trans Commun 32(10):1148–1157
Lin CC, Chang CC, Chen YH (2014) A novel SVD-based watermarking scheme for protecting rightful ownership of digital images. J Inf Hiding Multimedia Sign Proccess 5(2):124–143
Lin CC, Chen YH, Chang CC (2009) LSB-based high-capacity data embedding scheme for images. Int J Innov Comput Inf Cont 5(11B):4283–4289
Luo W, Huang F, Huang J (2010) Edge adaptive image steganography based on LSB matching revisited. IEEE Trans Inf Forensics Secur 5(2):201–214
Munteanu A, Cornelis J, Auwera GVD, Cristea P (1999) Wavelet image compression – the quadtree coding approach. IEEE Trans Inf Technol Biomed 3(3):176–185
Omoomi M, Samavi S, Dumitrescu S (2011) An efficient high payload +1 data embedding scheme. Multimedia Tool Appl 54(2):201–218
Ou D, Sun W (2014) High payload image steganography with minimum distortion based on absolute moment block truncation coding. Multimedia Tool Appl :1–23.
Petitcolas FA, Anderson RJ, Kuhn MG (1999) Information hiding—a survey. Proc IEEE 87(7):1062–1078
Shi YQ, Xuan G, Zou D et al (2005) Image steganalysis based on moments of characteristic functions using wavelet decomposition, prediction-error image, and neural network. Int Conf Multimedia Expo 2005:269–272
Sun W, Lu ZM, Wen YC, Yu FX, Shen RJ (2013) High performance reversible data hiding for block truncation coding compressed images. SIViP 7(2):297–306
Walker JS (1996) Fast Fourier transforms, 2nd edn. CRC Press, Boca Raton
Yang H, Yin J (2013) A secure removable visible watermarking for BTC compressed images. Multimedia Tool Appl :1–15.
Zhang Y, Shi-Ze G, Zhe-Ming L, Hao L (2013) Reversible data hiding for BTC-compressed images based on lossless coding of mean tables. IEICE Trans Commun 96(2):624–631
Acknowledgments
Many thanks for the support by Ministry of Science and Technology in Taiwan under Grant number MOST 104-2221-E-468-005. Our gratitude also goes to Michael Burton, Asia University.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Huang, YH., Chang, CC. & Chen, YH. Hybrid secret hiding schemes based on absolute moment block truncation coding. Multimed Tools Appl 76, 6159–6174 (2017). https://doi.org/10.1007/s11042-015-3208-y
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-015-3208-y