Abstract
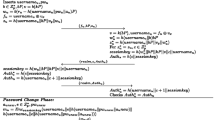
The Session Initiation Protocol (SIP) has revolutionized the way of controlling Voice over Internet Protocol (VoIP) based communication sessions over an open channel. The SIP protocol is insecure for being an open text-based protocol inherently. Different solutions have been presented in the last decade to secure the protocol. Recently, Zhang et al. authentication protocol has been proposed with a sound feature that authenticates the users without any password-verifier database using smart card. However, the scheme has a few limitations and can be made more secure and optimized regarding cost of exchanged messages, with a few modifications. Our proposed key-agreement protocol makes a use of two server secrets for robustness and is also capable of authenticating the involved parties in a single round-trip of exchanged messages. The server can now authenticate the user on the request message received, rather than the response received upon sending the challenge message, saving another round-trip of exchanged messages and hence escapes a possible denial of service attack.



Similar content being viewed by others
References
Abdalla M, Pointcheval D (2005) Simple password based encrypted key exchange protocols (CT-RSA 2005)
Arshad R, Ikram N (2011) Elliptic curve cryptography based mutual authentication scheme for session initiation protocol. Multimed Tools Appl. doi:10.1007/s11042-011-0787-0
Atkinson R. Security architecture for the Internet protocol, RFC 1825
Bellare M, Pointcheval D, Rogaway P (2000) Authenticated key exchange secure against dictionary attacks (Crypto 2000)
Boyko V, MacKenzie PD, Patel S (2000) Provably secure password authenticated key exchange using diffie-hellman (Crypto 2000)
Callegari C, Garroppo RG, Giordano S, Pagano M (2009) Security and delay issues in SIP systems. Int J Commun Syst 22:1023–1044
Certicom Research Standard for efficient cryptography, SEC 1, 2000: EC Cryptography. Ver. 1.0
Debiao H, Jianhua C, Yitao C (2012) A secure mutual authentication scheme for session initiation protocol using elliptic curve cryptography, Published online in Wiley Online Library wileyonlinelibrary.com. Security Comm Netw. doi:10.1002/sec.506
Diffie W, Hellman ME (1976) New directions in cryptography. IEEE Trans Inf Theory IT-22:644–654
Durlanik A, Sogukpinar I (2005) SIP authentication scheme using ECDH. World Enformatika Soc Trans Eng Comput Technol 8:350–353
Franks J, Hallam-Baker P, Hostetler J, Lawrence S, Leach P, Luotonen A, Stewart L (1999) HTTP authentication: basic and digest access authentication, IETF RFC2617
Geneiatakis D, Dagiuklas T, Kambourakis G, Lambrinoudakis C, Gritzalis S, Ehlert S (2006) Survey of security vulnerabilities in session initiation protocol. IEEE Commun Surv Tutorials 8(3):68–81
Hongbin T, Xinsong L (2012) Cryptanalysis of Arshad et al.’s ECC-based mutual authentication scheme for session initiation protocol. Multimed Tools Appl. doi:10.1007/s11042-012-1001-8
Huang H, Wei W, Brown G (2006) A new efficient authentication scheme for session initiation protocol. Proceedings of JCIS 06
Hussain TH, Marimuthu PN, Habib SJ (2012) Supporting multimedia applications through network redesign. Int J Commun Syst. doi:10.1002/dac.2371
Irshad A, Noshairwan W, Shafiq M, Khurram S, Irshad E, Usman M (2008) Security enhancement in MANET authentication by checking the CRL status of servers. Int J Adv Sci Technol 1:91–98
Jo H, Lee Y, Kim M, Kim S, Won D (2009) Off-line password-guessing attack to Yang’s and Huang’s authentication schemes for session initiation ptorocol. Proceedings of INC, IMS and IDC, pp 618–621
Karig D, Lee R (2001) Remote denial of service attacks and countermeasures. Department of Electrical Engineering, Princeton University, Technical Report CE-L2001-002
Kent S, Atkinson R (1998) Security architecture for the Internet protocol, RFC 2401
Kilian J (1992) A note on efficient zero-knowledge proofs and arguments. In: Proc. 24th Annual ACM Symposium on Theory of Computing, Victoria BC, pp 723–732
Koblitz N (1987) Elliptic curve cryptosystems. Math Comput 48:203–209
Lee CC (2009) On security of an efficient nonce based authentication scheme for SIP. Int J Netw Secur 3:201–203
Li J-S, Kao C-K, Tzeng J-J (2011) VoIP secure session assistance and call monitoring via building security gateway. Int J Commun Syst 24:837–851
Lu R, Cao Z (2006) Off-line password guessing attack on an efficient key agreement protocol for secure authentication. Int J Netw Secur 3(1):35–38
Menezes AJ, Oorschot PC, Vanstone SA (1997) Handbook of applied cryptograph. CRC Press, New York
Miller V (1986) Uses of elliptic curves in cryptography. In: Advances in cryptology CRYPTO’85, Lecture Notes in Computer Science, vol. 218. Springer-Verlag, pp 417–426
Pu Q (2010) Weaknesses of SIP authentication scheme for converged VoIP networks, http://eprint.iacr.org/2010/464
Raeburn K (2005) Encryption and checksum specifications for Kerberos 5, RFC 3961
Rescorla E (2000) SSL and TLS: designing and building secure systems. Addison-Wesley, New York
Rosenberg J, Schulzrinne H, Camarillo G, Johnston A, Peterson J, Sparks R, Handley M, Schooler E (2002) SIP: session initiation protocol, IETF RFC3261
Schneider B (1996) Applied cryptography second edition: protocols, algorithms, and source code in C. John Wiley & Sons Inc., Hoboken
Thomas M (2001) SIP security requirements. IETF internet draft (draftthomas-sipsec-reg-00.txt), work in progress
Tsai J (2009) Efficient nonce-based authentication scheme for session initiation protocol. Int J Netw Secur 8(3):312–316
Veltri L, Salsano S, Papalilo D (2002) SIP security issues: the SIP authentication procedure and its processing load. IEEE Netw 16(6):38–44
Wang B, Li ZQ (2006) A forward-secure user authentication scheme with smart cards. Int J Netw Secur 3(2):116–119
Wu L, Zhang Y, Wang F (2009) A new provably secure authentication and key agreement protocol for SIP using ECC. Comput Stand Interfaces 31(2):286–291
Xie Q (2011) A new authenticated key agreement for session initiation protocol. Int J Commun Syst. doi:10.1002/dac.1286
Yang C, Wang R, Liu WT (2005) Secure authentication scheme for session initiation protocol. Comput Secur 4:381–386
Ylonen T, Lonvick C (2006) (Eds) The secure shell (SSH) Transport layer protocol, RFC 4253
Yoon EJ, Koo KY (2010) Robust mutual authentication with a key agreement scheme for the session initiation protocol. IETE Tech Rev 27(3):203–213
Zhang L, Tang S, Cai Z (2013) Efficient and flexible password authenticated key agreement for Voice over Internet Protocol session initiation protocol using smart card. Int J Comm Syst
Zhou L, Chao H-C, Vasilakos A (Aug. 2011) Joint forensics-scheduling strategy for delay-sensitive multimedia applications over heterogeneous networks. IEEE J Sel Areas Commun 29(7):1358–1367
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Irshad, A., Sher, M., Eid Rehman et al. A single round-trip SIP authentication scheme for Voice over Internet Protocol using smart card. Multimed Tools Appl 74, 3967–3984 (2015). https://doi.org/10.1007/s11042-013-1807-z
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-013-1807-z