Abstract
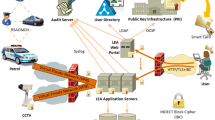
This paper provides an overview of the security architecture for Law Enforcement Agencies (LEAs) designed by the INDECT project, and in particular the security infrastructures that have been deployed so far. These security infrastructures can be organized in the following main areas: Public Key Infrastructure (PKI) and user management, communications security, and new cryptographic algorithms. This paper presents the new ideas, architectures and deployed testbeds for these areas. In particular, it explains the inner structure of the INDECT PKI employed for federated identity management, the different technologies employed in the VPN testbed, the INDECT Block Cipher (IBC) – a novel cryptographic algorithm that has being integrated into OpenSSL library, and how IBC-enabled TLS/SSL sessions and X.509 certificates are employed to protect INDECT applications. All proposed mechanisms have been designed to work in an integrated fashion as the security foundation of all systems being developed by the INDECT project for LEAs.




Similar content being viewed by others
Notes
Initially we planned to employ OpenCA for the proposed INDECT Public Key Infrastructure (PKI). However we stopped using OpenCA because of the key length limitations (up to 4096 bits). It is possible to issue keys with length up to 8192 bits by using EJBCA which covers INDECT CA requirements.
The INDECT project is also developing standalone, non-networked applications. We won’t consider it security here, since its usage is confined to particular systems and the information that can be disclosed by a security breach is limited to the local data of the application.
References
INDECT Consortium (2009) “D8.1: Specification of requirements for security and confidentiality of the system”, http://www.indect-project.eu/files/deliverables/public/INDECT_Deliverable_D8.1_v20091223.pdf/view. Accessed 20 December 2012.
Dierks T, Rescorla E (2008) “The Transport Layer Security (TLS) protocol version 1.2”, RFC 5246
EJBCA Enterprise PKI web site (2012) http://www.ejbca.org/. Accessed 1 April 2012.
Hickman K (1995) “The SSL Protocol”. Netscape communications corp.
INDECT project web site (2013) http://www.indect-project.eu. Accessed 13 January 2013.
Niemiec M, Dudek J, Romański Ł, Święty M (2012) “Towards hardware implementation of INDECT Block Cipher”. Proc. 5th International Conference of Multimedia Communications, Services and Security (MCSS 2012), Krakow, Poland
Niemiec M, Machowski L (2012) “A new symmetric block cipher based on key-dependent S-boxes”. Proc. 4th International Congress on Ultra Modern Telecommunications and Control Systems (ICUMT 2012), Saint Petersburg, Russia
OpenCA project web site (2012) http://www.openca.org/. Accessed 23 April 2012.
OpenSSL (2012) The open source toolkit for SSL/TLS. http://www.openssl.org. Accessed 21 December 2012.
OpenVPN Community Software. http://openvpn.net/index.php/open-source.html. Accessed 21 December 2012.
Stoianov N, Urueña M, Niemiec M, Machník P, Maestro G (2012) Security infrastructures: Towards the INDECT system security, MCSS 2012, CCIS 287, Springer-Verlag Berlin Heidelberg, pp. 304–315, ISBN 978-3-642-30720-1
Thomas SA (2000) “SSL and TLS Essentials: Securing the Web”. Wiley Computer Publishing.
Urueña M, Muñoz A, Larrabeiti D (2012) “Analysis of privacy vulnerabilities in single sign-on mechanisms for multimedia websites”, Multimedia Tools and Applications
Zhelyazkov D, Stoianov N (2009) PKI infrastructure in the BA – Prerequisite for minimization of the risk and enhancement of the information security, CIO journal, special issue communication & information technologies for the defense, pp. 19–20, ISSN 13112-5605
Acknowledgments
This work has been funded by the EU Project INDECT (Intelligent information system supporting observation, searching and detection for security of citizens in urban environment)—grant agreement number: 218086.
Author information
Authors and Affiliations
Corresponding author
Additional information
This paper is an improved version of “Security Infrastructures: Towards the INDECT System Security” from the same authors, presented in the 5th International Conference on Multimedia Communication Services & Security (MCSS 2012), Krakow (Poland), May 31- June 1, 2012.
Rights and permissions
About this article
Cite this article
Stoianov, N., Urueña, M., Niemiec, M. et al. Integrated security infrastructures for law enforcement agencies. Multimed Tools Appl 74, 4453–4468 (2015). https://doi.org/10.1007/s11042-013-1532-7
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-013-1532-7