Abstract
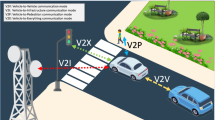
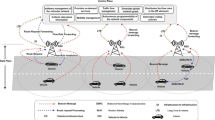
Message authentication that ensures a message is genuine and verifies the source of the sender is a key issue in vehicular ad hoc networks (VANETs). Because messages may provide life-critical traffic information or emergency messages transmitted by unfamiliar sources. Because the vehicle in a VANET transmits messages in real-time in a high-mobility environment, traditional PKI security schemes are not suitable for VANET. The use of roadside units (RSUs) makes message authentication in VANET easy, but it also causes two problems and needed to be solved: how to authenticate messages transmitted between two different RSU ranges, and how to hand off messages for the vehicles moving across different RSU communication ranges. This paper proposes a comprehensive message authentication scheme that enables the message authentication within intra and between inter RSU ranges and hand-off between different RSUs. The proposed scheme balances the overhead for computation and communication with security against attacks. Efficiency analysis and comparison with related works demonstrate that the proposed scheme is a superior message authentication method for VANET.





Similar content being viewed by others
References
Aijaz A, Bochow B, Florian D, Festag A, Gerlach M, Kroh R, Tim L (2006) Attacks on inter vehicle communication systems—an analysis. In: Proc. 3rd int. workshop intell. transp., Hamburg, Germany
Choi JY, Jakobsson M, Wetzel S (2005) Balancing auditability and privacy in vehicular networks. In: Proc. 1st ACM int. workshop Q2SWinet, pp 79–87
Hartenstein H, Laberteaux KP (2008) A tutorial survey on vehicular ad hoc networks. IEEE Commun Mag June:164–171
Hubaux J-P, Capkun S, Luo J (2004) The security and privacy of smart vehicles. IEEE Secur Priv 2(3):49–55
IEEE P802.11p/D6 (20098) Draft amendment for wireless access in vehicular environments (WAVE)
Kounga G, Walter T, Lachmund S (2009) Proving reliability of anonymous information in VANETs. IEEE Trans Veh Technol 58(6)2977–2989
Lee S, Pan G, Park J, Gerla M, Lu S (2007) Secure incentives for commercial ad dissemination in vehicular networks. In: Proc. ACM int symp. MobiHoc, pp 150–159
Lin X, Sun X, Ho P-H, Shen X (2007) GSIS: a secure and privacy preserving protocol for vehicular communications. IEEE Trans Veh Technol 56(6):3442–3456
Lin X, Sun X, Wang X, Zhang C, Ho P-H, Shen X (2008) TSVC: timed efficient and secure vehicular communications with privacy preserving. IEEE Trans Wirel Commun 7(12):4987–4998
Long M, Chwan-Hwa JW, Irwind JD (2008) Reducing communication overhead for wireless roaming authentication: methods and performance evaluation. Int J Netw Secur 6(3):331–341
Lu R, Lin X, Zhu H, Ho P-H, Shen X (2008) ECPP: efficient conditional privacy preservation protocol for secure vehicular communications. In: Proc. IEEE INFOCOM, Phoenix, AZ, pp 1229–1237
NIST (2002) The keyed-hash message authentication code (HMAC). FIPS PUB 198
Perrig A, Canetti R, Tygar JD, Song D (2002) The TESLA broadcast authentication protocol. RSA CryptoBytes 5(2):2–13
Plöβl K, Nowey T, Mletzko C (2006) Towards a security architecture for vehicular ad hoc networks. In: Proc. 1st int. conf. availab., rel. security, Vienna, Austria, pp 374–381
Raya M, Hubaux J-P (2005) The security of vehicular ad hoc networks. In: Proceedings of the 3rd ACM workshop on security of ad hoc and sensor networks (SASN ’05), Alexandria, VA, USA, pp 11–21
Stingson DR (2005) Cryptography: theory and practice, 3rd edn. CRC, Boca Raton
Toor Y, Muhlethaler P, Laouiti A (2008) Vehicle ad hoc networks: applications and related technical issues. In: IEEE communications surveys & tutorials, pp 74–88
Tung B (1999) Kerberos: a network authentication system. Addison-Wesley, Reading
U.S. Dept. Transp. (2006) Nat. highway traffic safety admin. Vehicle safety communications project
Zhang C, Lin X, Lu R, Ho P-H, Shen X (2008) An efficient message authentication scheme for vehicular communications. IEEE Trans Veh Technol 57(6):3357–3368
Zhang C, Lu R, Lin X, Ho P-H, Shen X (2008) An efficient identity-based batch verification scheme for vehicular sensor networks. In: Proc. IEEE INFOCOM, 2008, Phoenix, AZ, pp 246–250
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Wu, HT., Hsieh, WS. RSU-based message authentication for vehicular ad-hoc networks. Multimed Tools Appl 66, 215–227 (2013). https://doi.org/10.1007/s11042-011-0792-3
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-011-0792-3