Abstract
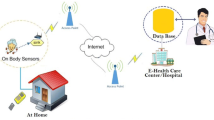
Due to tremendous development in the network technologies forms an Internet of Things (IoT) based Health Care System (HCS) is an essential application in day-today life. In HCS, constitute a group communication among doctors, patient, caretaker, ambulance, and hospital, which intern’s devices transfer personal information from one to many group members. Providing security on the personal health information is the most critical issue, because malicious access on this information may leads to life threads. Concurrently, traditional cryptographic framework has unsuccessful to protection to the HCS over lightweight communications network. So, the proposed framework deals the security flaws through hyper elliptic curve based public key cryptosystem, which combines Digital Signature algorithm, Elgamal approaches that ensure the entity authentication and secure group communication. The performance of the proposed work analyzed using efficient security measures and compared with related schemes.

Similar content being viewed by others
References
Yeh, K.-H., A secure IoT-based healthcare system with body sensor networks. IEEE Access 4:10288–10299, 2016.
Harn, L., and Lin, C., Authenticated group key transfer protocol based on secret sharing. IEEE transactions on computers 59:842–846, 2010.
Alphonse, P. J. A., and Reddy, Y. V., A method for obtaining authenticated scalable and efficient group key agreement for wireless ad-hoc networks. Cluster Computing.:17, 2018.
Hou, J.-L., and Yeh, K.-H., Novel authentication schemes for IoT based healthcare systems. International Journal of Distributed Sensor Networks 59:842–846, 2015.
Li, C.-T., Wu, T.-Y., Chen, C.-L., Lee, C.-C., and Chen, C.- M., An efficient user authentication and user anonymity scheme with provably security for IoT-based medical care system. Sensors 17:1482, 2017.
Veltri, L., Cirani, S., Busanelli, S., and Ferrari, G., A novel batch-based group key management protocol applied to the internet of things. Ad Hoc Networks 11:2724–2737, 2013.
Rafaeli, S., and Hutchison, D., A survey of key management for secure group communication. ACM Computing Surveys (CSUR) 35:309–329, 2003.
Ye, C., and Reznik, A., Group secret key generation algorithms, information theory. ISIT 2007. IEEE International Symposium:2596–2600, 2007.
Porambage, P., Braeken, A., Schmitt, C., Gurtov, A. V., Yliant-tila, M., and Stiller, B., Authenticated group key transfer protocol based on secretsharing. IEEE transactions on computers 3:842–846, 2010.
Jaiswal, P., and Tripathi, S., An authenticated group key transfer protocol using elliptic curve cryptography. Peer-to-Peer Networking and Applications. 10:857–864, 2017.
Kim, Yongdae and Perrig, Adrian and Tsudik, gene, group key agreement efficient in communication. IEEE transactions on computers 53:905–921, 2004.
Amir, Y., Kim, Y., Nita-Rotaru, C., and Tsudik, G., On the performance of group key agreement protocols. ACM Transactions on Information and System Security (TISSEC) 7:457–488, 2004.
Lake, D., Milito, R., Morrow, M., and Vargheese, R., Internet of things: Architectural framework for ehealth security. J. ICT Stand. 1:301–328, 2014.
Duncan, R., An overview of different authentication methods and protocols, report submitted to SANS institute, 2001, 10.
Xin, Mingyuan, A mixed encryption algorithm used in internet of things security transmission system, Cyber-Enabled Distributed Computing and Knowledge Discovery (CyberC), International Conference on. pp 62:65,.2015
Das, A. K., and Goswami, A., A secure and efficient uniqueness-and-anonymity-preserving remote user authentication scheme for connected health care. ACM Transactions on Information and System Security (TISSEC) 7:9948, 2013.
Bernstein, D. J., and Lange, T., Hyper-and-elliptic-curve cryptography. LMS Journal of computation and Mathematics 17:181–202, 2014.
Wankhede Barsgade, M. T., and Meshram, S. A., Comparative study of elliptic and hyper-elliptic curve cryptography in discrete logarithmic problem. IOSR J. Math. 10:61–63, 2014.
Wei, L.-f., Design of hyperelliptic curve system digital signature in identity authentication. Fifth International Conference on Digital Image Processing (ICDIP 2013)IEEE transactions on computers 7:457–488, 2013.
Lin, YOU and Sang, Yong-Xuan, Effective generalized equations of secure hyper elliptic curve digital signature algorithms, The Journal of China Universities
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
Kavitha.S declares that she has no conflict of interest. P.J.A. Alphonse declares that he has no conflict of interest. Y.Venkatramana Reddy declares that he has no conflict of interest.
Ethical approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article is part of the Topical Collection on Mobile & Wireless Health
Rights and permissions
About this article
Cite this article
Kavitha, S., Alphonse, P.J.A. & Reddy, Y.V. An Improved Authentication and Security on Efficient Generalized Group Key Agreement Using Hyper Elliptic Curve Based Public Key Cryptography for IoT Health Care System. J Med Syst 43, 260 (2019). https://doi.org/10.1007/s10916-019-1378-2
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-019-1378-2