Abstract
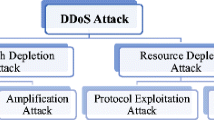
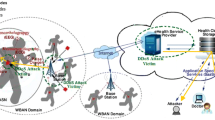
Wireless Body Area Networks (WBANs) have emerged as a promising technology that has shown enormous potential in improving the quality of healthcare, and has thus found a broad range of medical applications from ubiquitous health monitoring to emergency medical response systems. The huge amount of highly sensitive data collected and generated by WBAN nodes requires an ascendable and secure storage and processing infrastructure. Given the limited resources of WBAN nodes for storage and processing, the integration of WBANs and cloud computing may provide a powerful solution. However, despite the benefits of cloud-assisted WBAN, several security issues and challenges remain. Among these, data availability is the most nagging security issue. The most serious threat to data availability is a distributed denial of service (DDoS) attack that directly affects the all-time availability of a patient’s data. The existing solutions for standalone WBANs and sensor networks are not applicable in the cloud. The purpose of this review paper is to identify the most threatening types of DDoS attacks affecting the availability of a cloud-assisted WBAN and review the state-of-the-art detection mechanisms for the identified DDoS attacks.


Similar content being viewed by others
References
Latif, R., Abbas, H., Assar, S., Latif, S., Analyzing Feasibility for Deploying Very Fast Decision Tree for DDoS Attack Detection in Cloud Assisted WBAN. Proceedings of 10th International Conference, ICIC 2014, Taiyuan, China. pp: 507–519.
Irum, S., Ali, A., Aslam, F. K., Abbas, H., A Hybrid Security Mechanism for intra-WBAN and inter-WBAN Communication. International Journal of Distributed Sensor Networks. Volume 2013 (2013), Article ID 842608, 11 pages
Ali, A., Aslam, F. k., A Broadcast-Based Key Agreement Scheme using Set Reconciliation for Wireless Body Area Networks. Journal of Medical Systems (Springer), Volume: 38. Issue: 5. May 2014.
Latif, R., Abbas, H., and Assar, S., Cloud Computing Risk Assessment: A Systematic Literature Review. Future Information Technology. Future Tech 276:285–295, 2013.
Jiafu, W., Caifeng, Z., Ullah, S., Chin-Feng, L., Ming, Z., and Xiaofei, W., IoT Sensing Framework with Inter-cloud Computing Capability in Vehicular Networking. Journal of IEEE Network. 27:56–61, 2013.
Waqar, A., Raza. A., Abbas. H., Khurram, M. K., A framework for preservation of cloud users’ data privacy using dynamic reconstruction of metadata. Journal of Network and Computer Applications, Vol. 36, Iss. 1, January 2013, Pages 235–248, ISSN 1084–8045
Moshaddique, A. A., Jingwei, L., and Kyungsup, K., Security and Privacy Issues in Wireless Sensor Networks for Healthcare Applications. J. Medical Systems. 36(1):93–101, 2012.
AbuKhousa, E.; Najati, H.A. UAE-IHC: Steps towards Integrated E-Health Environment. Proceedings of the 4th e-Health and Environment Conference in the Middle East, Dubai, UAE, 30 January 2012–2 February 2012.
Foster, I.; Zhao, Y.; Raicu, L.; Lu, S. Cloud Computing and Grid Computing 360-Degree Compared. Proceedings of the Grid Computing Environments Workshop (GCE), Austin, TX, USA, pp. 1–10, 12–16 November 2008
Kitchenham, B., Brereton, O. P.,Systematic literature reviews in software engineering –A systematic literature review. Journal of Information and Software Technology, pp:7–15 2009.
Shahnaz, S., Sana Ullah, Kwak, K. S., A Study of IEEE 802.15.4 Security Framework for Wireless Body Area Networks, Journal of Sensor (Basel). Vol- 11, Iss. 2. Jan 2011
Akash, M., Shrivastava, A. K., Manish, M., A Review of DDOS Attack and its Countermeasures in TCP Based Networks. International Journal of Computer Science & Engineering Survey (IJCSES) Vol.2, No.4, pp:177–187, November 2011
Upma, G., Gayatri, B., Sandeep, M., A Dual Mechanism for defeating DDoS Attacks in Cloud Computing Model, International Journal of Application or Innovation in Engineering & Management (IJAIEM), Vol- 2, Issue 3, pp:34–39, March 2013
Fasheng, Y., Shui, Y., Wanlei, Z., Jing, H., and Alessio, B., Source-Based Filtering Scheme against DDOS Attacks. International Journal of Database Theory and Application 1(1):9–20, 2009.
Fang-Yie, L., Intrusion Detection, Forecast and Traceback Against DDoS Attacks. Journal of Information, Technology and Society 2009. Vol. 9, pp: 19–44, December 2009.
Vikas, C., Sateesh, K. P., Packet Monitoring Approach to Prevent DDoS Attack in Cloud Computing. International Journal of Computer Science and Electrical Engineering (IJCSEE). Vol-1 Iss-1, 2012.
Krunal, P., Security survey for cloud computing: threats & existing IDS/ IPS techniques. Proceedings of International Conference on Control, Communication and Computer Technology, IEEE. pp. 88–92, March 2013.
Ullah, S., Henry, H., Bart, B., Benoit, L., Chris, B., and Ingrid, M., A Comprehensive Survey of Wireless Body Area Networks On PHY, MAC, and Network Layers Solutions. Journal of Medical Systems 36(3):1065–1094, 2012.
Mitko, B., Analysis of the SYN Flood DoS Attack. International Journal of Computer Network and Information Security 8:1–11, 2013.
Ismail, M. N., Aborujilah, A., Shahrulniza M., AAmir, S., New Framework to Detect and Prevent Denial of Service Attack in Cloud Computing Environment. International Journal of Computer Science and Security (IJCSS), Vol. 6, Issue. 4, pp. 226–237, May 2012.
Sanchika, G., Padam, K., Ajith, A., A Profile Based Network Intrusion Detection and Prevention System for Securing Cloud Environment. International Journal of Distributed Sensor Networks, Hindawi Publishing Corporation. Vol. 2013, Article ID 364575, 12 pages, 2013.
Gulshan, S., Kavita, S., Swarnlata, R., A Technical Overview Dos and DDos Attack. Proceeding of International Conference in Computing 2010, pp 274–282, December 2010
Christos, D., and Aikaterini, M., DDoS attacks and defense mechanisms: classification and state-of-the-art. Journal of Computer Networks 44:643–666, 2004.
Asha, D., Chitra, R., Securing cloud from DDoS attacks using intrusion detection system in virtual machine. International Journal of Research in Engineering & Advanced Technology, IJREAT, Volume 1, Issue 1, March, 2013
Nisha H., Bhandari, Survey on DDoS Attacks and its Detection & Defence Approaches, International Journal of Science and Modern Engineering (IJISME). Volume-1, Issue-3, February 2013
Xin, X., Yongqiang, S., Zunguo, H., Defending DDoS Attacks Using Hidden Markov Models and Cooperative Reinforcement Learning. C.C. Yang et al. (Eds.): PAISI 2007, LNCS 4430, pp. 196–207, 2007
Saman, T. Z., James. J., David, T., A Survey of Defense Mechanisms Against Distributed Denial of Service (DDoS) Flooding Attacks. Communications Surveys & Tutorials, IEEE, Volume:15, Issue: 4, pp: 2046–2069. October 2013.
Lonea, A.M., Popescu, D.E., Tianfield, H., Detecting DDoS Attacks in Cloud Computing Environment. International Journal of Computers, Communications and Control. Vol. 8, Issue. 1, pp:70–78, February, 2013.
Gavaskar, S., Surendiran, R., Ramaraj, E., Three Counter Defense Mechanism for TCP SYN Flooding Attacks. International Journal of Computer Applications. Volume 6– No.6, September 2010.
Chi-Chun, L., Chun-Chieh, H., Joy, K., A Cooperative Intrusion Detection System Framework for Cloud Computing Networks. Proceedings of 39th International Conference on Parallel Processing Workshops, IEEE Computer Society, 2010.
Chen, Q., Wenmin, L., Wanchun, D., Shui, Y., CBF: A Packet Filtering Method for DDoS Attack Defense in Cloud Environment. Proceedings of the 2011, IEEE 9th International Conference on Dependable, Autonomic and Secure Computing. Pp: 427–434, IEEE Computer Society Washington DC, USA 2011.
Ahmad, Y. O., Noor Elaiza, A. K., Saadiah, Y., A Novel Framework for Jamming Detection and Classification in Wireless Networks 2012 8th International Conference on Computing and Networking Technology (ICCNT 2012), Gyeongju, South Korea August 2012
Technical report by CISCO, December 2006,http://www.cisco.com/web/about/ac123/ac147/archived_issues/ipj_9-4/syn_flooding_attacks.html. Accessed 12 Jan 2014
DDoS attacks in 2014: Smarter, bigger, faster, stronger. Technical Report. April 2014. http://venturebeat.com/2014/04/20/ddos-attacks-in-2014-smarter-bigger-faster-stronger/. Accessed 26 July 2014
Distributed Denial of Service Attack Protection Services, June 2014. http://www.incapsula.com/ddos/ddos-attacks/. Accessed 26 July 2014
2014 White paper, The Danger Deepens, Neustar Annual DDoS Attacks and Impact Report. http://www.neustar.biz/resources/whitepapers/ddos-protection/2014-annual-ddos-attacks-and-impact-report.pdf. Accessed 21 July 2014
Martin, R., Snort – Light Weight Intrusion Detection for Networks. http://www.snort.org. Accessed 20 Dec 2013
Chen, Q., Aickelin, U., Dempster-Shafer for Anomaly Detection. Proceedings of the International Conference on Data Mining (DMIN 2006), IEEE, pp: 232–238, USA 2008
Priyanka, N., Anupama, M., Gupta, B., Enhanced CBF Method to Detect DDoS Attack in Cloud Computing Environment. International Journal of Computer Science Issues, IJCSI. Vol. 10, Issue 2, No 1, pp 142–146, March 2013 (Science direct)
Modi, C., Patel, D., Patel, H., Borisaniya, B., Patel, A., and Rajarajan, M., A survey of intrusion detection techniques in Cloud. Journal of Network and Computer Applications 36(1):42–57, 2013.
Lonea, A., M., Popescu, D., E., Tianfield, H., Detecting DDoS Attacks in Cloud Computing Environment, INT J COMPUT COMMUN, 8(1):70–78, February, 2013
Keromytis, A., Misra, V., Rubenstein, D., SOS: an architecture for mitigating DDoS attacks, Selected Areas in Communications, IEEE Journal, Volume:22, Issue: 1, pp: 176 – 188, January 2004
Acknowledgments
The authors would like to extend their sincere appreciation to the Deanship of Scientific Research at King Saud University for its funding of this research through the Research Group Project no. RG-1435-048. The authors would also like to thank the National University of Sciences and Technology, Islamabad, Pakistan, for its support during this research.
Author information
Authors and Affiliations
Corresponding author
Additional information
“This article is part of the Topical Collection on Systems-Level Quality Improvement”
Rights and permissions
About this article
Cite this article
Latif, R., Abbas, H. & Assar, S. Distributed Denial of Service (DDoS) Attack in Cloud- Assisted Wireless Body Area Networks: A Systematic Literature Review . J Med Syst 38, 128 (2014). https://doi.org/10.1007/s10916-014-0128-8
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-014-0128-8