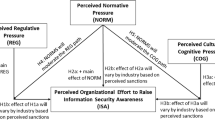
Abstract
Information security management (ISM) has become more important than ever, as the expansion of corporate information systems and the use of networks continue to increase. Many organizations consider ISM an important part of organizational innovation and key to strategic and operational efficiency. Managers require a firm understanding of the behavioral aspect of ISM, particularly of how their firms’ internal and external characteristics affect the ISM process. This study draws on need-pull–technology-push (NP–TP) theories and employs data on information security users to investigate the NP and TP factors influencing the awareness, development, and performance stages of ISM. This study also examines the moderating role of regulatory pressure in those relationships. The research model is tested with data taken from a random sample of global organizations obtained through the Korea Composite Stock Price Index, the Korean Securities Dealers Automated Quotation, and the Korea Foreign Company Association. The results indicate that all NP–TP variables had positive effects on the ISM process (with the exception of perceived benefits). Moreover, regulatory pressure had positive effects as a moderator between ISM awareness and ISM development and performance.


Similar content being viewed by others
References
Anderson DL, Agarwal R (2010) Practicing safe computing: a multimethod empirical examination of home computer user security behavioral intentions. MIS Q 34(3):613–643
Appari A, Johnson ME (2009) HIPAA compliance: an institutional theory perspective. In: AMCIS 2009 proceedings
Babatunde DA, Selamat MH (2012) Investigating information security management and its influencing factors in the Nigerian banking industry: a conceptual model. Int J Soc Sci Econ Art 2(2):55–59
Baker WH, Wallace L (2007) Is information security under control? IEEE Secur Priv 5(1):36–44
Barua A, Konana P, Whinston AB, Yin F (2004) An empirical investigation of net-enabled business value: an exploratory investigation. MIS Q 28(4):585–620
Bassellier G, Benbasat I (2004) Business competence of information technology professionals: conceptual development and influence on IT–business partnerships. MIS Q 28(4):673–694
Bentler PM (1990) Comparative fit indexes in structural models. Psychol Bull 107:238–246
Brandon DP, Hollingshead AB (2004) Transactive memory systems in organizations: matching tasks, expertise, and people. Organ Sci 15(6):633–644
Brown CV, Sambamurthy V (2001) Coordination theory in the context of the IT function: linking the logic of governance and coordination mechanisms. University of Maryland Working Paper
Browne MW, Cudeck R (1993) Alternative ways of assessing model fit. In: Bollen KA, Long JS (eds) Testing structural equation models. Sage, Newbury Park, pp 136–162
Bulgurcu B, Cavusoglu H, Benbasat I (2010) Information security policy compliance: an empirical study of rationality-based beliefs and information security awareness. MIS Q 34(3):523–548
Carmines EG, McIver JP (1981) Analyzing models with unobserved variables. In: Bohrnstedt GW, Borgatta EF (eds) Social measurement: current issues. Sage, Beverly Hills, pp 65–115
Chang SE, Ho CB (2006) Organizational factors to the effectiveness of implementing information security management. Ind Manag Data Syst 106(3):345–361
Chatterjee D, Grewal R, Sambamurthy V (2002) Shaping up for e-commerce: institutional enablers of the organizational assimilation of web technologies. MIS Q 26(2):65–89
Chau PYK, Tam KY (1997) Factors affecting the adoption of open systems: an exploratory study. MIS Q 21(1):1–24
Chau PYK, Tam KY (2000) Organizational adoption of open systems: a ‘technology-push, need-pull’ perspective. Inf Manag 37(5):229–239
Chidamber SR, Kon HB (1994) A research retrospective of innovation inception and success: the technology-push, demand-pull question. Int J Technol Manag 9(1):94–112
Chin W (1998) The partial least squares approach for structural equation modeling. In: Marcoulides GA (ed) Modern methods for business research. Lawrence Erlbaum, Hillsdale, pp 295–336
Cohen J (1992) A power primer. Psychol Bull 112(1):155–159
Cooper R, Zmud R (1990) Information technology implementation research: a technological diffusion approach. Manag Sci 36(2):123–139
D’Arcy J, Hovav A, Galletta D (2009) User awareness of security countermeasures and its impact on information systems misuse: a deterrence approach. Inf Syst Res 20(1):79–98
Dhillon G, Backhouse J (2000) Information system security management in the new millennium. Commun ACM 43(7):125–128
DiMaggio PJ, Powell WW (1983) The iron cage revisited: institutional isomorphism and collective rationality in organizational fields. Am Sociol Rev 48(2):147–160
Dodge CR, Carver C, Ferguson JA (2007) Phishing for user security awareness. Comput Sci 26(1):73–80
Fichman RG (2004) Real options and IT platform adoption: implications for theory and practice. Inf Syst Res 15(2):132–154
Flanagin AJ (2000) Social pressures on organizational website adoption. Hum Commun Res 26(4):618–646
Fornell C, Larcker DF (1981) Evaluating structural equation models with unobservable variables and measurement error. J Mark Res 18(1):39–50
Furnell S (2008) End-user security culture: a lesson that will never be learnt? Comput Fraud Secur 2008(4):6–9
Furnell SM, Gennatou M, Dowland PS (2002) A prototype tool for information security awareness and training. Logist Inf Manag 15(5/6):352–357
Galliers R (2007) Strategizing for agility: confronting information systems inflexibility in dynamic environments. In: DeSouza K (ed) Agile information systems. Butterworth-Heinemann, Elsevier Inc, Burlington, pp 1–15
Grover V, Saeed KA (2007) The impact of product, market, and relationship characteristics on interorganizational system integration in manufacturer–supplier dyads. J Manag Inf Syst 23(4):185–216
Grover V, Goslar MD (1993) The initiation, adoption, and implementation of telecommunications technologies in US organizations. J Manag Inf Syst 10(1):141–163
Guo KH, Yuan Y, Archer NP, Connelly CE (2011) Understanding nomnalicious security violations in the workplace: a composite behavior model. J Manag Inf Syst 28(2):203–236
Han IG, Sun HK (1998) A case study on the information security management system for major Korean business groups. Asia Pac J Inf Syst 8(2):105–119
Ho CR, Chi YP, Tai YM (2005) A structural approach to measuring uncertainty in supply chains. Int J Electron Commer 9(3):91–114
Hsu C, Lee JN, Straub DW (2012) Institutional influences on information systems security innovations. Inf Syst Res 23(1):1–22
Hu Q, Hart P, Cooke D (2007) The role of external and internal influences on information systems security—a neo-institutional perspective. J Strateg Inf Syst 16(2):153–172
Ives B, Olson MH (1984) User involvement and MIS success: a review of research. Manag Sci 30(5):586–603
Jung WJ, Shin Y, Lee SYT (2012) The behavioral attitude of financial firms’ employees on the customer information security in Korea. Asia Pac J Inf Syst 22(1):53–77
Kearns GS, Lederer AL (2004) The impact of industry contextual factors on IT focus and the use of IT for competitive advantage. Inf Manag 41(7):899–919
Keller S, Powell A, Horstmann B, Predmore C, Crawford M (2005) Information security threats and practices in small business. Inf Syst Manag 22(2):7–19
Khalifa M, Davison RM (2006) SME adoption of IT: the case of electronic trading systems. IEEE Trans Eng Manag 53(2):275–284
Kim HS (1999) A study on the quantification of information security level. Asia Pac J Inf Syst 9(4):181–201
Kim JK, Lee DH (2005) A research on information security risk-based antecedents influencing electronic commerce user’s trust. Asia Pac J Inf Syst 15(2):65–96
Kim S, Garrison G (2010) Understanding users’ behaviors regarding supply chain technology: determinants impacting the adoption and implementation of RFID technology in South Korea. Int J Inf Manag 30(5):388–398
Ko EJ, Kim SH, Kim MS, Woo JY (2008) Organizational characteristics and the CRM adoption process. J Bus Res 61(1):65–74
Koo JM, Park JS, Park JH (2013) Study about the impact of information security systems on corporate performance: based on IT relatedness theory. Asia Pac J Inf Syst 23(4):129–149
Kuan KKY, Chau PYK (2001) A perception-based model for EDI adoption in small businesses using a technology–organization–environment framework. Inf Manag 38(8):507–521
Lee CP, Shim JP (2007) An exploratory study of radio frequency identification (RFID) adoption in the healthcare industry. Eur J Inf Syst 16(6):712–724
Lee Y, Kozar KA (2008) An empirical investigation of anti-spyware software adoption: a multitheoretical perspective. Inf Manag 45(2):109–119
Lee Y, Larsen KR (2009) Threat of coping appraisal: determinants of SMB executives’ decision to adopt anti-malware software. Eur J Inf Syst 18(2):177–187
Lewis W, Agarwal R, Sambamurthy V (2003) Sources of influence on beliefs about information technology use: an empirical study of knowledge workers. MIS Q 27(4):657–678
Li H, Zhang J, Sarathy R (2010) Understanding compliance with internet use policy from the perspective of rational choice theory. Decis Support Syst 48(4):635–645
Liang H, Saraf N, Hu Q, Xue Y (2007) Assimilation of enterprise systems: the effect of institutional pressures and the mediating role of top management. MIS Q 31(1):59–87
Lu Y, Ramamurthy K (2011) Understanding the link between information technology capability and organizational agility: an empirical examination. MIS Q 35(4):931–954
Ma Q, Ratnasingam P (2008) Factors affecting the objectives of information security management. In: International conference on information resources management 2008 proceedings
Markus ML, Mao JY (2004) Participation in development and implementation—updating an old, tired concept for today’s IS contexts. J Assoc Inf Syst 5(11–12):514–544
Mowery D, Rosenberg N (1979) The influence of market demand upon innovation: a critical review of some recent empirical studies. Res Pol 8(2):102–153
Munro H, Noori H (1988) Measuring commitment to new manufacturing technology: integrating technological push and marketing pull concepts. IEEE Trans Eng Manag 35(2):63–70
Nunnally JC (1978) Psychometric theory. McGraw Hill, New York
Premkumar G, Ramamurthy K (1995) The role of interorganizational and organizational factors on the decision mode for adoption of interorganizational systems. Decis Sci 26(3):303–336
Rai A, Patnayakuni R (1996) A structural model for CASE adoption behavior. J Manag Inf Syst 13(2):205–234
Richardson R (2011) 2010/2011 CSI computer crime and security survey. Computer Security Institute, New york
Rogelberg SG, Stanton JM (2007) Introduction: understanding and dealing with organizational survey nonresponses. Organ Res Methods 10(2):195–209
Rogers EM (2003) Diffusion of innovations, 5th edn. The Free Press, New York
Schon DA (1967) Technology and change. Delacorte Press, New York
Sharma R, Yetton P (2007) The contingent effects of training, technical complexity, and task interdependence on successful information systems implementation. MIS Q 31(2):219–238
Shih HP (2006) Technology-push and communication-pull forces driving message-based coordination performance. J Strateg Inf Syst 15(2):105–123
Siponen MT (2001) Five dimensions of information security awareness. Comput Soc 31(2):24–29
Son JY, Narasimhan S, Riggins F (2005) Effects of relational factors and channel climate on EDI usage in the customer–supplier relationship. J Manag Inf Syst 22(1):321–353
Spears JL, Barki H (2010) User participation in information systems security risk management. MIS Q 34(3):503–522
Templeton G, Lewis B, Snyder C (2002) Development of a measure for the organizational learning construct. J Manag Inf Syst 19(2):175–218
Teo HH, Wei KK, Benbasat I (2003) Predicting intention to adopt interorganizational linkages: an institutional perspective. MIS Q 27(1):19–49
Wixom BH, Watson HJ (2001) An empirical investigation of the factors affecting data warehousing success. MIS Q 25(1):17–41
Xue Y, Liang H, Boulton WR (2008) Information technology governance in information technology investment decision processes: the impact of investment characteristics, external environment, and internal context. MIS Q 32(1):67–96
Yildirim EY, Akalp G, Aytac S, Bayram N (2011) Factors influencing information security management in small-and medium-sized enterprises: a case study from Turkey. Int J Inf Manag 31(4):360–365
Zaheer A, Zaheer S (1997) Catching the wave: alertness, responsiveness, and market influence in global electronic networks. Manag Sci 43(11):1493–1509
Zhu K, Kraemer KL, Xu S (2006) The process of innovation assimilation by firms in different countries: a technology diffusion perspective on e-business. Manag Sci 52(10):1557–1576
Zhu K, Dong S, Xu SX, Kraemer KL (2006) Innovation diffusion in global contexts: determinants of post-adoption digital transformation of European companies. Eur J Inf Syst 15(6):601–616
Zmud RW (1984) An examination of ‘push-pull’ theory applied to process innovation in knowledge work. Manag Sci 30(6):727–738
Acknowledgments
This research was supported by Kyungpook National University A.S Research Fund, 2014. The authors would like to thank the editor and anonymous reviewers for all their suggestions.
Author information
Authors and Affiliations
Corresponding author
Appendices
Appendix
See Table 6.
Questionnaire
2.1 Market volatility
-
The level of competition between firms for security technologies and management is very high.
-
Our firm often faces increasing costs associated with security management.
-
Security technologies and management ability required for our business administration change frequently.
-
Security technologies and management are introduced to our firm on an increasingly shorter cycle.
2.2 Proactive IT stance
-
We constantly keep abreast of new IT systems.
-
We have the ability and continue to experiment with new IT systems when necessary.
-
We have a climate that is supportive of trying out new ways to use IT.
-
We constantly seek new ways to make more effective use of IT.
2.3 Task interdependence
-
We can perform our tasks fairly independently of others.
-
Our task is affected by the performance of other individuals or departments.
-
Our task requires frequent coordination with others.
-
Our task performance depends on receiving accurate information from others.
2.4 Perceived benefits
-
Information security management reduces error rates for data management in our firm.
-
Information security management is useful for improving our firm’s image.
-
Information security management reduces unnecessary costs for our firm.
-
Information security management enhances our firm’s work capacity and decision-making process.
2.5 Level of cooperation
-
We have established standard operating procedures (e.g., goals, policies, and plans) with our business partners.
-
We have established strategic planning processes with our business partners.
-
We have established a system of liaison roles with our business partners.
-
We have established task force teams with our business partners to promote crucial or emerging projects.
2.6 Partner interdependence
-
The sustainable maintenance of management relationships with business partners is crucial for achieving our firm’s business goals.
-
Our total revenue depends heavily on our trade with business partners.
-
The supply and service of our firm have considerable influence on our business partners’ achievement of their business goals.
-
Our business partners have substantial power over our firm.
2.7 Regulatory pressure
-
Our firm actively supports and follows ISM undertaken by security supervision authorities.
-
Our firm operates under pressure from ISM undertaken by security supervision authorities.
-
Security supervision authorities require our firm to review and investigate ISM.
-
Security supervision authorities strongly urge our firm to manage our general information security.
2.8 ISM awareness
-
Our firm has positive attitudes toward ISM.
-
Our firm intends to manage and invest in information security.
-
Our firm considers ISM as a crucial factor in the development and implementation of business strategies.
-
In our firm, all members understand the seriousness of information security.
-
Our firm is interested in ISM.
2.9 ISM development
-
Our firm engages in good monitoring practices in terms of information security.
-
In our firm, information system users comply with information security policies (e.g., duties and regulations).
-
Our firm invests more in personnel and technologies associated with ISM than before.
-
Our firm provides better education and training programs regarding ISM more frequently than before.
2.10 ISM performance
-
Our firm’s internal and external ability has increased because of our efforts to manage information security.
-
In our firm, duties and regulations concerning ISM have improved considerably.
-
Our firm realizes financial and nonfinancial benefits from ISM.
-
Our firm has favorable attitudes toward new systems and programs in terms of ISM.
Rights and permissions
About this article
Cite this article
Kim, S., Kim, G. & French, A.M. Relationships between need-pull/technology-push and information security management and the moderating role of regulatory pressure. Inf Technol Manag 16, 173–192 (2015). https://doi.org/10.1007/s10799-015-0217-5
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10799-015-0217-5