Abstract
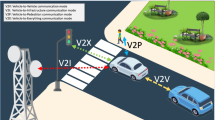
With the development of the intelligent transportation system (ITS) and increasing application of vehicular ad-hoc networks (VANETs), the security of VANETs has become a crucial issue for VANETs and ITS. In this study, we propose a quantum VANETs protection scheme to address the security issue of vehicular identity authentication. It based on BB84 quantum key distribution protocol and quantum mechanics. Furthermore, the novel quantum scheme can defend most VANETs-aimed attacks. It also can be applied on connection of vehicle to everything (V2X), this is because reliability and security problem can be solved in proposed quantum scheme. By tactfully exploiting properties of quantum mechanics, our proposed scheme offers remarkable advantages which include remote identity authentication, identity revocation and irreversibility. The security analysis shows that our proposed scheme can further insure the security of VANETs identity authentication.





Similar content being viewed by others
References
Raya, M., Hubaux, J.P.: Securing Vehicular Ad Hoc Networks[C]. In: International Conference on Pervasive Computing and Applications. IEEE, pp. 39–68 (2007)
Lin, X.D., Sun, X.T., Ho, P.H., Shen, X.M.: Gsis: a secure and privacy- preserving protocol for vehicular communications. IEEE Trans. Veh. Technol. 56(6), 3442–3456 (2007)
Cunha, F., Villas, L., Boukerche, A., Maia, G., Viana, A., Mini, R.A.F., Loureiro, A.A.F.: Data communication in VANETs: protocols, applications and challenges. Ad Hoc Networks 44, 90–103 (2016)
Lehner, A., Graca, C.R., Strang, T.: A multi-broadcast communication system for high dynamic vehicular ad-hoc networks. IEEE ICUMT. 2(2), 286–302 (2014)
Jianhong, Z., Min, X., Liying, L.: On the security of a secure batch verification with group testing for VANET. Int. J. Netw. Secur. 16(5), 355–362 (2014)
Horng, S.J., Tzeng, S.F., Pan, Y., Fan, P., Wang, X., Li, T., Khan, K.M.: b-specs+: Batch verification for secure pseudonymous authentication in VAENT. IEEE TIFS. 8(11), 1860–1875 (2013)
Lee, C.C., Lai, Y.M.: Toward a secure batch verification with group testing for VAENT. Wirel. Netw. 19(6), 1441–1449 (2013)
Horng, S.J., Tzeng, S.F., Li, T., Wang, X., Huang, P.H., Khan, M.K.: Enhancing security and privacy for identity-based batch verification scheme in VAENT. IEEE Trans. Veh. Technol. 99, 1–1 (2015)
Chien, H.Y., Jan, J.K., Tseng, Y.M.: Forgery attacks on multisignature schemes for authenticating mobile code delegates. IEEE Trans. Veh. Technol. 51(6), 1669–1671 (2003)
Chang, C.C., Hwang, K.F.: Some forgery attacks on a remote user authentication scheme using smart cards. Inform. 14(3), 289–294 (2003)
Wu, T.C., Hsu, C.L.: Cryptanalysis of digital multisignature schemes for authenticating delegates in mobile code systems. IEEE Trans. Veh. Technol. 52(2), 462–464 (2003)
Pironio, S., Acn, A., Brunner, N., Gisin, N., Massar, S., Scarani, V.: Device-independent quantum key distribution secure against collective attacks. New. J. Phys. 11(4), 1–2 (2009)
Harn, L., Hsin, W.J., Mehta, M.: Authenticated diffie-hellman key agreement protocol using a single cryptographic assumption. IEE P-Commun. 152(4), 404–410 (2005)
Lin, C.L., Wen, H.A., Hwang, T., Sun, H.M.: Provably secure three-party password-authenticated key exchange. Ieice. T. Fund. Electr. 87(11), 2990–3000 (2004)
Sun, H.M., Chen, B.C., Hwang, T.: Secure key agreement protocols for three-party against guessing attacks. J. Syst. Softw. 75(1), 63–68 (2005)
Wen, H.A., Lee, T.F., Hwang, T.: Provably secure three-party password-based authenticated key exchange protocol using weil pairing. IEE P-Commun. 152(2), 138–143 (2005)
Chen, I.C., Hwang, T., Li, C.M.: Efficient one-out-of-two quantum oblivious transfer based on four-coherent-state postselection protocol. Phys. Scripta. 78(3), 035005 (2008)
Hazay, C.: Oblivious polynomial evaluation and secure set-intersection from Al- Gebraic PRFs. Springer, Berlin (2015)
Dirac, P.A.M.: The physical interpretation of quantum mechanics. Proc. R. Soc. Lond. A 26(4), 1–40 (1927)
Dirac, P.A.M., Polkinghorne, J.C.: The principles of quantum mechanics. Clarendon Press, Oxford (1958)
Stewart, B.: An account of some experiments on radiant heat, involving an extension of prevost’s theory of exchanges. T. Roy. Soc. Edin-Earth. 22(1), 1–20 (2013)
Hottel, H.C., Cohen, E.S.: Radiant heat exchange in a gas enclosure: Allowance for nonuniformity of gas temperature. Aiche. J. 4(1), 3–14 (1958)
Bohr, N.: 3 c on the constitution of atoms and molecules. Philos. Mag. 26(151), 1–25 (1913)
Nielsen, M.A., Chuang, I.L., et al.: Quantum Computation and Quantum Information[J]. Math. Struct. Comput. Sci. 21(1), 1–59 (2002)
Mayers, D.: Unconditional security in quantum cryptography ACM (2001)
Bennett, C.H., Brassard, G.: Quantum Cryptgraphy: public key distribution and coin tossing. In: IEEE international conference on computers, systems, and signal processing, Bangalore, India (1984)
Scarani, V., Renner, R.: Quantum cryptography with finite resources: unconditional security bound for discrete-variable protocols with one-way postprocessing. Phys. Rev. Lett. 100(20), 200501 (2008)
Sano, Y., Matsumoto, R., Uyematsu, T.: Secure key rate of the bb84 protocol using finite sample bits. J. Phys. A: Math. Theor. 43(49), 495302 (2010)
Cai, R., Scarani, V.: Finite-key analysis for practical implementations of quantum key distribution. New. J. Phys. 11(4), 045024 (2009)
Wootters, W.K., Zurek, W.H.: A single quantum cannot be cloned. Nature. 299(5886), 802–803 (1982)
Barnett, S.M., Pegg, D.T.: On the Hermitian optical phase operator. Opt. Acta. Int. J. Opt. 36(1), 7–19 (1989)
Ni, Z.X.: Nonlinear lie algebra and ladder operators for orbital angular momentum. J. Phys. A: Gen. Phys. 32(11), 2217 (1999)
Price, W.C., Chissick, S.S., Brody, T.A.: The uncertainty Principleand-Foundations of Quantum Mechanics. J. Wiley, New York (1977)
Dirac, P.A.M.: Quantised singularities in the electromagnetic field. P. Roy. Soc. A. Mat. 133(133), 60–72 (1931)
Einstein, A.: Physics and reality. J. Franklin. I. 221(3), 349382 (1936)
Agassi, J., Faraday, M.: Faraday as a natural philosopher [1971]. Brit. Med. J. 2(4882), 287 (1971)
Kauffman, L.H., Lomonaco, S.J.: Comparing quantum entanglement and topological entanglement. New. J. Phys. 4(1), 73 (2002)
Scarani, V., Renner, R.: Quantum cryptography with finite resources: unconditional security bound for discrete-variable protocols with one-way postprocessing. Phys. Rev. Lett. 100(20), 200501 (2008)
Huang, J.Z., Weedbrook, C., Yin, Z.Q., Wang, S., Li, H.W., Chen, W., Guo, G.C., Han, Z.F.: Quantum hacking on continuous-variable quantum key distribution system using a wavelength attack. Phys. Rev. A. 87(6), 19932001 (2013)
Acknowledgments
The work was supported by the Fundamental Research Funds for the Central Universities of Central South University (Project No:2018zzts025).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Chen, Z., Zhou, K. & Liao, Q. Quantum Identity Authentication Scheme of Vehicular Ad-Hoc Networks. Int J Theor Phys 58, 40–57 (2019). https://doi.org/10.1007/s10773-018-3908-y
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10773-018-3908-y