Abstract
In this paper we present an improved algorithm for finding low-weight multiples of polynomials over the binary field using coding theoretic methods. The associated code defined by the given polynomial has a cyclic structure, allowing an algorithm to search for shifts of the sought minimum-weight codeword. Therefore, a code with higher dimension is constructed, having a larger number of low-weight codewords and through some additional processing also reduced minimum distance. Applying an algorithm for finding low-weight codewords in the constructed code yields a lower complexity for finding low-weight polynomial multiples compared to previous approaches. As an application, we show a key-recovery attack against  that has a lower complexity than the chosen security level indicate. Using similar ideas we also present a new probabilistic algorithm for finding a multiple of weight 4, which is faster than previous approaches. For example, this is relevant in correlation attacks on stream ciphers.
that has a lower complexity than the chosen security level indicate. Using similar ideas we also present a new probabilistic algorithm for finding a multiple of weight 4, which is faster than previous approaches. For example, this is relevant in correlation attacks on stream ciphers.




Similar content being viewed by others
Notes
This operation is equivalent to transforming \(K(x)\) into \(K(x) \hbox { mod }(1+x^{d})\).
References
Ågren M., Hell M., Johansson T., Löndahl C.: Improved message passing techniques in fast correlation attacks on stream ciphers. In: 7th International Symposium on Turbo Codes & Iterative Information Processing (2012).
Aumasson J., Finiasz M., Meier W., Vaudenay S.: TCHo: a hardware-oriented trapdoor cipher. In: Pieprzyk J., Ghodosi H., Dawson E. (eds.) ACISP. Lecture Notes in Computer Science, vol. 4586, pp. 184–199. Springer, Berlin (2007).
Becker A., Joux A., May A., Meurer A.: Decoding random binary linear codes in \(2^n/20\): How 1 + 1 = 0 improves information set decoding. In: Pointcheval D., Johansson T. (eds.) Advances in Cryptology—EUROCRYPT 2012. Lecture Notes in Computer Science, vol. 7237, pp. 520–536. Springer, Berlin (2012).
Bernstein D.J.: Introduction to post-quantum cryptography. In: Bernstein D.J., Buchmann J., Dahmen E. (eds.) Post-Quantum Cryptography, pp. 1–14. Springer, Berlin (2009).
Bernstein D.J., Lange T., Peters C.: Attacking and defending the McEliece cryptosystem. In: PQCrypto 2008, pp. 31–46 (2008).
Bernstein D.J., Lange T., Peters C.: Smaller decoding exponents: ball collision decoding. In: Rogway P. (ed.) Advances in Cryptology—CRYPTO 2011. Lecture Notes in Computer Science, vol. 6841, pp. 743–760. Springer, Berlin (2011).
Canteaut A., Chabaud F.: A new algorithm for finding minimum-weight words in a linear code: application to McEliece’s cryptosystem and to narrow-sense BCH codes of length 511. IEEE Trans. Inf. Theory 44, 367–378 (1998).
Canteaut A., Trabbia M.: Improved fast correlation attacks using parity-check equations of weight 4 and 5. In: Preneel B. (ed.) Advances in Cryptology–EUROCRYPT 2000. Lecture Notes in Computer Science, vol. 1807, pp. 573–588. Springer, Berlin (2000).
Chose P., Joux A., Mitton M.: Fast correlation attacks: an algorithmic point of view. In: Boneh D. (ed.) Advances in Cryptology–EUROCRYPT 2002. Lecture Notes in Computer Science, vol. 2332, pp. 209–221. Springer, Berlin (2002).
Didier F., Laigle-Chapuy Y.: Finding low-weight polynomial multiples using discrete logarithm. In: Goldsmith A., Shokrollahi A., Medard M., Zamir R. (eds.) International Symposium on Information Theory–ISIT 2007. IEEE, CCSd (2007).
El Aimani L., von zur Gathen J.: Finding low weight polynomial multiples using lattices. In: Cryptology ePrint Archive, Report 2007/423 (2007).
Finiasz M., Vaudenay S.: When stream cipher analysis meets public-key cryptography. In: Biham E., Youssef A.M. (eds.) Selected Areas in Cryptography. Lecture Notes in Computer Science, vol. 4356 , pp. 266–284. Springer, Berlin (2006).
Finiasz M., Sendrier N.: Security bounds for the design of code-based cryptosystems. In: Matsui M. (ed.) Advances in Cryptology—ASIACRYPT 2009. Lecture Notes in Computer Science, vol. 4586, pp. 88–105. Springer, Berlin (2009).
Golić, J.D.: Computation of low-weight parity-check polynomials. Electron. Lett. 32(21), 1981–1982 (1996).
Herrmann M., Leander G.: A practical key recovery attack on basic. In: Jarecki S., Tsudik G. (eds) Public Key Cryptography—PKC 2009. Lecture Notes in Computer Science, vol. 5443, pp. 411–424. Springer, Berlin (2009).
Johansson T., Löndahl C.: An improvement to Stern’s algorithm. Internal Report. http://lup.lub.lu.se/record/2204753 (2011). Accessed 20 Aug 2013.
Joux A.: Algorithmic Cryptanalysis. Chapman & Hall/CRC, Boco Raton (2009).
May A., Meurer A., Thomae E.: Decoding random linear codes in \(\tilde{\cal O}{2^{0.054n}}\). In: Lee D.-H., Wang X. (eds.) Advances in Cryptology–ASIACRYPT 2011. Lecture Notes in Computer Science, vol. 7073, pp. 107–124. Springer, Berlin (2011).
McEliece R.J.: A public-key cryptosystem based on algebraic coding theory. DSN Progress Report 42–44, pp. 114–116 (1978).
Meier W., Staffelbach O.: Fast correlation attacks on certain stream ciphers. J. Cryptol. 1(3), 159–176 (1989).
Shor P.W.: Algorithms for quantum computation: Discrete logarithms and factoring. In: 35th Annual Symposium on Foundations of Computer Science, 20–22 Nov 1994, Santa Fe, NM, pp. 124–134. IEEE Press, Washington (1994).
Stern J.: A method for finding codewords of small weight. In: Wolfmann J., Cohen G.D. (eds.) Coding Theory and Applications. Lecture Notes in Computer Science, vol. 388, pp. 106–113. Springer, Berlin (1989).
Wagner D.: A generalized birthday problem. In: Yung M. (ed.) Advances in Cryptology—CRYPTO 2002. Lecture Notes in Computer Science, vol. 2442, pp. 288–303. Springer, Berlin (2002).
Acknowledgments
We would like to thank the anonymous reviewers in the submission to DCC and WCC for their valuable and insightful comments that helped improve the manuscript. We also want to thank Martin Ågren for helping out with the initial implementation of the algorithm described in Sect. 6. This research was funded by a grant (621-2009-4646) from the Swedish Research Council.
Author information
Authors and Affiliations
Corresponding author
Additional information
This is one of several papers published in Designs, Codes and Cryptography comprising the “Special Issue on Coding and Cryptography.”
A part of this paper was presented at WCC 2013.
Appendix: Proof of Proposition 1
Appendix: Proof of Proposition 1
The complexity function \(C^*\) refers to the expected complexity of running Algorithm 1 with an instance where we have one single solution, i.e., only one codeword of weight \(w\) exists in the code, whereas in the case of LWPMb, there will exist several weight \(w\) codewords. Having \(y+1\) possible solutions instead of one suggests that finding at least one is roughly \(y+1\) times more likely. However, for this to be true, the probability \(\xi \) of finding one single codeword in one iteration must be small. In particular, we require that \(y\xi \ll 1\). Secondly, we require the events of finding the shifted low-weight codewords to be independent of each other.
Let the set of solutions, i.e., the set of shifts of \(K(x)\) represented as vectors, be the rows of the matrix
The weight reduction using of the expanded generator matrix \(\mathbf{{G}}_y\) will result in a new codeword matrix, which we write as
The column permutation \(\pi \) acting on \(\mathbf{\mathbf{{G}}_y \mathbf {\Gamma }}\) (used in Algorithm 1) permutes all codewords accordingly, thus permuting the columns of \(\mathbf{{K}}\). Let \(r=d-d_P\). For a set of arbitrary indices \(\{i_1,i_2,\ldots ,i_{r}\} \subset \{0,1,\ldots ,d-1\}\), the resulting permutation of \(\mathbf{{K}} \mathbf{{\Gamma }}\) is
Now, assume that the two vectors
constitute two rows of the first \(r\) columns of \(\pi (\mathbf{{K}} \mathbf{{\Gamma }})\) for some \(j\) such that \(1 \le j \le y\) and where each \(k_i\) is an i.i.d. random variable. Note that the indices are taken modulo \(d\). For a codeword \(\mathbf{{k}}\) to be considered as a possible solution in one iteration of Algorithm 1, a necessary but not sufficient condition is that \(\mathbf{{k}}\) can have at most \(2p\) nonzero elements in the first \(r\) columns. We want to show that these two events are approximately independent. We provide some informal argument. A more formal derivation would require quite some space, which we avoid.
The set of indices \(\{i_1, i_2,\ldots , i_{r}\}\) are chosen uniformly in the permutation. As a consequence, there is a non-zero probability that \(\{i_1, i_2,\ldots , i_r\}\cap \{i_{1}-j, i_{2}-j,..., i_{r}-j\}\ne \emptyset \), meaning that one or several random variables in \(\mathbf{{k}}\) and \(\mathbf{{k}}'\) are identical. More specifically, we have
common indices in \(\{i_1, i_2,\ldots , i_{r}\}\) and \(\{i_{1}-j, i_{2}-j,..., i_{r}-j\}\) on average. The probability of having \(i\) overlapping variables describes the probability function of a hypergeometric distribution, i.e.,
and thus,
Let \({A_{0}}\) denote the sum of random variables in positions \({i_1}, {i_2}, \ldots , {i_r}\) and \(A_1\) the sum of random variables in positions \(\{i_{1}-j, i_{2}-j,..., i_{r}-j\}\) respectively. Moreover, let B denote the sum of the intersecting variables in positions \(\{i_1, i_2,\ldots , i_r\}\cap \{i_{1}-j, i_{2}-j,..., i_{r}-j\}\). The expected intersection is \(\mu \), so \(B\) is sum of \(\mu \) random variables. By assuming the worst-case \(A_0 = 2p\), we obtain the following
Hence, if \(w \left( 1-\frac{d_P}{d}\right) \gg 2p\) then the expected value is significantly larger than \(2p\). If so, \(A_1\) is very unlikely to take a value below or equal to \(2p\) and, thus, we argue that the events of finding the shifted codewords are approximately independent.
Under the two conditions \(y \xi \ll 1\) and \(w \left( 1-\frac{d_P}{d}\right) \gg 2p\), we can conclude that the probability of finding at least one out of \(y+1\) codewords is \(1-(1-\xi )^{y+1} \approx (y+1) \xi \), since all codewords are equally likely to be found. Moreover, the complexity \(C^*\) is \(\mathcal {O}\left( \xi ^{-1}\right) \) and therefore Algorithm 2 has complexity \(\mathcal {O}\left( (y+1)^{-1}\xi ^{-1}\right) \). This concludes the proof of Proposition 1.
Rights and permissions
About this article
Cite this article
Löndahl, C., Johansson, T. Improved algorithms for finding low-weight polynomial multiples in \(\mathbb {F}_{2}^{}[x]\) and some cryptographic applications. Des. Codes Cryptogr. 73, 625–640 (2014). https://doi.org/10.1007/s10623-014-9960-6
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10623-014-9960-6
Keywords
- Low-weight polynomial multiple
- Low-weight codeword
- Information-set decoding
- Public-key cryptography
-
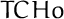
- Correlation attacks