Abstract
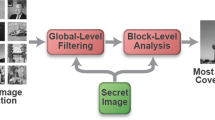
Most of the existing image steganographic approaches embed the secret information imperceptibly into a cover image by slightly modifying its content. However, the modification traces will cause some distortion in the stego-image, especially when embedding color image data that usually contain thousands of bits, which makes successful steganalysis possible. In this paper, we propose a novel coverless steganographic approach without any modification for transmitting secret color image. In our approach, instead of modifying a cover image to generate the stego-image, steganography is realized by using a set of proper partial duplicates of a given secret image as stego-images, which are retrieved from a natural image database. More specifically, after dividing each database image into a number of non-overlapping patches and indexing those images based on the features extracted from these patches, we search for the partial duplicates of the secret image in the database to obtain the stego-images, each of which shares one or several visually similar patches with the secret image. At the receiver end, by using the patches of the stego-images, our approach can approximately recover the secret image. Since the stego-images are natural ones without any modification traces, our approach can resist all of the existing steganalysis tools. Experimental results and analysis prove that our approach not only has strong resistance to steganalysis, but also has desirable security and high hiding capability.








Similar content being viewed by others
References
Cao Y, Zhou Z, Sun X, Gao C (2018) Coverless information hiding based on the molecular structure images of material. Comput Mater Continua 54(2):197–207
Chang C, Kieu T, Chou Y (2009) Reversible information hiding for VQ indices based on locally adaptive coding. J Vis Commun Image Represent 20:57–64
Cheddad A, Condell J, Curran K, Kevitt M (2010) Review: ‘Digital image steganography: survey and analysis of current methods’. J Signal Process 90:727–752
Chen W (2007) Color image steganography scheme using set partitioning in hierarchical trees coding, digital Fourier transform and adaptive phase modulation. Appl Math Comput 185:432–448
Chen B, Zhou C, Jeon B, Zheng Y, Wang J (2017a) Quaternion discrete fractional random transform for color image adaptive watermarking. Multimed Tools Appl. https://doi.org/10.1007/s11042-017-5511-2
Chen X, Chen S, Wu Y (2017b) Coverless information hiding method based on the Chinese character encoding. J Internet Technol 18(2):313–320
Efros A, Freeman W (2001) Image quilting for texture synthesis and transfer. In: Conference on computer graphics and interactive techniques, New York, USA, vol 2001, pp 341–346
Fridrich J, Kodovsky J (2012) Rich models for steganalysis of digital images. IEEE Trans Inf Forensics Secur 7:868–882
Hioki H (2002) A data embedding method using BPCS principle with new complexity measures. In: Proceedings of Pacific Rim Workshop on digital steganography, pp. 30–47
Johnson N, Jajodia S (1998) Exploring steganography: seeing the unseen. Computer 31:26–34
Kawaguchi E (2005) BPCS-steganography principle and applications. In: Knowledge-based intelligent information and engineering systems, Melbourne, Australia. vol 3684, pp 289–299
Ker A (2004) Improved detection of LSB steganography in grayscale images. Springer, Heidelberg, pp 97–115
Ker A (2005) Steganalysis of LSB matching in grayscale images. IEEE Signal Process Lett 12:441–444
Kieu M, Lai K, Tran T, Le T(2016) A fusion of bag of word model and hierarchical K-Means++ in image retrieval. In: International symposium on integrated uncertainty in knowledge modelling and decision making, Springer, Cham, pp 397–408
Liao X, Qin Z, Ding L (2017a) Data embedding in digital images using critical functions. Sig Process Image Commun 58:146–156
Liao X, Yin J, Guo S, Li X, Sangaiah A (2017b) Medical JPEG image steganography based on preserving inter-block dependencies. Comput Electr Eng. https://doi.org/10.1016/j.compeleceng.2017.08.020
Li Z, Chen X, Pan X, ZX (2009) Lossless data hiding scheme based on adjacent pixel difference. In: International conference on computer engineering and technology. IEEE Computer Society, Washington Vol 1, pp 588–592
Li X, Wang J (2007) A steganographic method based upon JPEG and particle swarm optimization algorithm. Inf Sci Int J 177:3099–3109
Luo W, Huang F, Huang J (2010) Edge adaptive image steganography based on LSB matching revisited. IEEE Trans Inf Forensics Secur 5:201–214
Mckeon R (2007) Strange Fourier steganography in movies. In: IEEE international conference on electro/information technology, Chicago, USA. vol 2007, pp 178–182
Mielikainen J (2006) LSB matching revisited. IEEE Signal Process Lett 13:285–287
Sivic J, Zisserman A (2003) Video Google: A text retrieval approach to object matching in videos. Proceedings of the 9th IEEE International Conference on Computer Vision, pp. 1470-1477
Sivic J, Zisserman A (2012) Video Google: a text retrieval approach to object matching in videos. In: IEEE international conference on computer vision, vol 7, pp 1470–1477
Sun H, Grishman R, Wang Y (2017) Active learning based named entity recognition and its application in natural language coverless information hiding. J Internet Technol 18(2):443–451
Wang Z, Bovik A, Sheikh H, Simoncelli E (2004) Image quality assessment: from error visibility to structural similarity. IEEE Trans Image Process 13:600–612
Wang J, Lian S, Shi Y (2017) Hybrid multiplicative multi-watermarking in DWT domain. Multidimension Syst Signal Process 28(2):617–636
Wu K, Wang C (2014) Steganography using reversible texture synthesis. IEEE Trans Image Process 24:130–139
Wu K, Wang C (2015) Steganography using reversible texture synthesis. IEEE Trans Image Process 24:130–139
Wu H, Wu N, Tsai C, Hwang M (2005) Image steganographic scheme based on pixel-value differencing and LSB replacement methods. Proc Vis Image Signal Process 152:611–615
Xia Z, Li X (2017) Coverless information hiding method based on LSB of the character’s unicode. J Internet Technol 18(6):1353–1360
Xiong L, Xu Z, Shi Y (2017) An integer wavelet transform based scheme for reversible data hiding in encrypted images. Multidimension Syst Signal Process 29(3):1191–1202
Yin Z, Niu X, Zhang X, Tang J, Luo B (2017b) Reversible data hiding in encrypted AMBTC compressed images. In: Multimedia tools and applications, pp 436–445
Yin Z, Niu X, Zhou Z, Tang J, Luo B (2017a) Improved reversible image authentication scheme. Cogn Comput 8(5):890–899
Yuan C, Xia Z, Sun X (2016) Coverless image steganography based on SIFT and BOF. J Internet Technol 18:209–216
Zhou Z, Sun X, Chen X, Chang C, Fu Z (2014) A novel signature based on combination of global and local signatures for image copy detection. Secur Commun Netw 7(11):1702–1711
Zhou Z, Sun H, Harit R, Chen X, Sun X (2015) Coverless image steganography without embedding. In: International conference on cloud computing and security, Nanjing, China, pp 123–132
Zhou Z, Cao Y, Sun X (2016a) Coverless information hiding based on bag-of-words model of image. J Appl Sci 34:527–536
Zhou Z, Wang Y, Wu Q, Yang C, Sun X (2016b) Effective and efficient global context verification for image copy detection. IEEE Trans Inf Forensics Secur 12:48–63
Zhou Z, Yang C, Chen B, Sun X, Liu Q, Wu Q (2016c) Effective and efficient image copy detection with resistance to arbitrary rotation. IEICE Trans Inf Syst E99.D(6):1531–1540
Zhou Z, Wu Q, Yang C, Sun X, Pan Z (2017a) Coverless image steganography based on histograms of oriented gradients-based hashing algorithm. J Internet Technol 18(5):1177–1184
Zhou Z, Wu Q, Huang F, Sun X (2017b) Fast and accurate near-duplicate image elimination for visual sensor networks. Int J Distrib Sens Netw 13(2):1–12
Acknowledgements
This work was supported, in part, by the National Natural Science Foundation of China under grant numbers 61602253, U1536206, 61232016, U1405254, 61373132, 61373133, 61502242, 61572258, and 61672294; in part, by the Jiangsu Basic Research Programs-Natural Science Foundation under grant numbers BK20150925 and BK20151530; in part, by the Priority Academic Program Development of Jiangsu Higher Education Institutions (PAPD) fund; and in part, by the Collaborative Innovation Center of Atmospheric Environment and Equipment Technology (CICAEET) fund, China.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflicts of interest
The authors declare that they have no conflict of interest.
Ethical approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Additional information
Communicated by V. Loia.
Rights and permissions
About this article
Cite this article
Zhou, Z., Mu, Y. & Wu, Q.M.J. Coverless image steganography using partial-duplicate image retrieval. Soft Comput 23, 4927–4938 (2019). https://doi.org/10.1007/s00500-018-3151-8
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00500-018-3151-8