Abstract
We characterize security strategies and payoffs for three mechanisms for dissolving partnerships: the Texas Shoot-Out, the \(K+1\) auction, and the compensation auction. A security strategy maximizes a participant’s minimum payoff, and represents a natural starting point for analysis when a participant is either uncertain of the environment or uncertain of whether his rivals will play equilibrium. For the compensation auction, a dynamic dissolution mechanism, we introduce the notion of a perfect security strategy. Such a strategy maximizes a participant’s minimum payoff along every path of play. We show that while a player has many security strategies in the compensation auction, he has a unique perfect security strategy.


Similar content being viewed by others
Notes
McAfee (1992) characterizes equilibrium in the Texas Shoot-Out when partners have independent private values.
These mechanisms also efficiently dissolve partnerships when all the players follow security strategy.
See, for instance, Raiffa (1982) p. 297 which develops a numerical example.
In an independent private values setting, the equilibrium in strictly increasing strategies of the \(K+1\) auction where \(K=0\) is also an equilibrium of the Tie-Favoring Auction.
In the event that \(b_{\mathrm{f}}=b_{\mathrm{s}}\), the winner is selected randomly from among the high bids.
This is the difference between bidder i’s demand and the compensation \( p_{1}\) given to the rival who dropped.
Player 2’s equilibrium strategy coincides with his security strategy.
See Cramton et al. (1987).
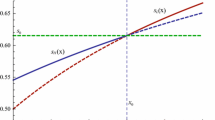
The auction is not ex-post efficient since \(\beta (x)\ne \bar{\beta }(x)\). The probability that the allocation is inefficient is 1 / 6.
See Van Essen and Wooders (2016).
If at round \(k^{\prime }\) bidder i bids \(p_{k^{\prime }}\), then he ties with another bid. We break the tie in the other bidder’s favor so that i does not drop out. This is justified since we consider i’s worst-case payoff.
References
Brams, S., Taylor, A.: Fair Division: From Cake Cutting to Dispute Resolution. Cambridge University Press, Cambridge (1996)
Chen, Y., Lai, J., Parkes, D., Procaccia, A.: Truth, justice, and cake cutting. Games Econ. Behav. 77, 284–297 (2013)
Cramton, P., Gibbons, R., Klemperer, P.: Dissolving a partnership efficiently. Econometrica 55, 615–632 (1987)
Crawford, V.: A game of fair division. Rev. Econ. Stud. 44, 235–247 (1977)
Crawford, V.: A procedure for generating Pareto efficient egalitarian equivalent allocations. Econometrica 47, 49–60 (1979)
Crawford, V.: Maximin behavior and efficient allocation. Econ. Lett. 6, 211–215 (1980a)
Crawford, V.: A self-administered solution of the bargaining problem. Rev. Econ. Stud. 47, 385–392 (1980b)
De Castro, L., Yannelis, N.: Uncertainty, efficiency and incentive compatibility: ambiguity solves the conflict between efficiency and incentive compatibility. J. Econ. Theory 177, 678–707 (2018)
Demange, G.: Implementing efficient egalitarian equivalent allocations. Econometrica 52, 1167–1178 (1984)
Dubins, E., Spanier, E.: How to cut a cake fairly. Am. Math. Mon. 68, 1–17 (1961)
Grant, S., Kline, J., Quiggin, J.: A matter of interpretation: ambiguous contracts and liquidated damages. Games Econ. Behav. 85, 180–187 (2014)
Lui, Z.: Implementation of maximin rational expectations equilibrium. Econ. Theory 62, 813–837 (2016). https://doi.org/10.1007/s00199-015-0932-5
Moulin, H.: Prudence versus sophistication in voting strategy. J. Econ. Theory 24, 398–412 (1981)
Moulin, H.: The conditional auction mechanism for sharing a surplus. Rev. Econ. Stud. 51, 157–170 (1984)
McAfee, R.P.: Amicable divorce: dissolving a partnership with simple mechanisms. J. Econ. Theory 56, 266–293 (1992)
Raiffa, H.: The Art and Science of Negotiation. Harvard University Press, Cambridge (1982)
Robertson, J., Webb, W.: Cake-Cutting Algorithms: Be Fair if You Can. AK Peters, Natick (1998)
Steinhaus, H.: The problem of fair division. Econometrica 16, 101–104 (1948)
Van Essen, M., Wooders, J.: Dissolving a partnership dynamically. J. Econ. Theory 166, 212–241 (2016)
Von Neumann, J.: Zur Theorie der Gesellschaftsspiele. Math. Ann. 100, 295–320 (1928)
Wolitzky, A.: Mechanism design with maxmin agents: theory and an application to bilateral trade. Theor. Econ. 11, 971–1004 (2016)
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
John Wooders is grateful for financial support from the Australian Research Council’s Discovery Projects funding scheme (Project Number DP140103566).
5 Appendix
5 Appendix
Proof of Proposition 0
The proof is well known and is only included for completeness. It is easy to verify that for the given strategies the players each obtain a payoff of at least \(x_{1}/2\) and \( x_{2}/2\), respectively.
We show there is no strategy which guarantees player 1 more than \(x_{1}/2\). Consider a strategy \(\beta ^{1}\) such that \(\beta ^{1}(x_{1})>x_{1}/2\) for some \(x_{1}\). If player 1 with value \(x_{1}\) sets a price \(\beta ^{1}(x_{1})=p\) and player 2 chooses Sell, then player 1’s payoff is \( x_{1}-p<x_{1}/2\). Likewise, if \(\beta ^{1}(x_{1})=p<x_{1}/2\) for some \(x_{1}\), then player 1 obtains a payoff less than \(x_{1}/2\) if \(\beta ^{2}(x_{2};p)=\) “Buy”.
Likewise, if \(\beta ^{2}(x_{2},p)=\)“Buy” for some \(p>x_{2}/2\), then player 2 obtains a payoff \(x_{2}-p<x_{2}/2\) if player 1 offers price p. \(\square \)
Proof of Proposition 1
For symmetric mechanisms, we can write \(v_{i}(\hat{x}_{i},x_{-i},\hat{\beta }^{i},\beta ^{-i})\) as \(v(\hat{x} _{i},x_{-i},\hat{\beta }^{i},\beta ^{-i})\).
Suppose to the contrary that bidder i with value \(\hat{x}_{i}\) can guarantee more than \(\hat{x}_{i}/N\), i.e., he has a (possibly mixed) strategy \(\hat{\beta }^{i}\) such that
Since the inequality holds for all \(x_{-i}\) and \(\beta ^{-i}\), then it holds in particular for \(\hat{x}_{-i}=(\hat{x}_{i},\ldots ,\hat{x}_{i})\) and \(\hat{ \beta }^{-i}=(\hat{\beta }^{i},\ldots ,\hat{\beta }^{i})\), i.e.,
Summing across the N bidders, the total payoff when all bidders have a value of \(\hat{x}_{i}\) and follow the same strategy \(\hat{\beta }^{i}\) is \(Nv( \hat{x}_{i},\hat{x}_{-i},\hat{\beta }^{i},\hat{\beta }^{-i})\), which is greater than \(\hat{x}_{i}\). This contradicts that the mechanism is payoff feasible. \(\square \)
Proof of Proposition 2
We need to establish two facts: (i) \(\bar{\beta }^{i}(x_{i})=x_{i}\) guarantees bidder i a payoff of at least \(x_{i}/N\), and (ii) \(\bar{\beta }^{i}(x_{i})=x_{i}\) is the unique security strategy.
Part (i): Suppose that \(\bar{\beta }^{i}(x_{i})=x_{i}\). If bidder i wins, then he obtains a payoff of
where the inequality holds since \(x_{i}\ge b_{\mathrm{s}}\) as \(x_{i}\) is the winning bid. If bidder i loses, then he obtains
where the inequality holds since \(b_{\mathrm{f}}\ge b_{\mathrm{s}}\ge x_{i}\). His payoff, therefore, is at least \(x_{i}/N\). By Proposition 00, \(\bar{\beta } ^{i}(x_{i})=x_{i}\) is a security strategy.
Part (ii). Suppose \(\bar{\beta }^{i}(x_{i})=x_{i}+\varDelta \) for \(\varDelta >0\). Suppose all the other bidders bid \(x_{i}+\varDelta /2\). Bidder i wins and obtains a payoff of
since \(K(x_{i}+\varDelta /2)+(1-K)(x_{i}+\varDelta )>x_{i}\) for \(K\in [0,1]\) . Suppose \(\bar{\beta }^{i}(x_{i})=x_{i}-\varDelta \) for \(\varDelta >0\). Suppose all the other bidders bid \(x_{i}-\varDelta /2\). Bidder i loses and obtains a payoff of
\(\square \)
Proof of Proposition 4
S \(\bar{\beta }^{i}\) that satisfies the conditions of the Proposition. Let \(x_{-i}\) and \(\beta ^{-i}\) be arbitrary.
We first show that the bids of bidder i are in the interval \([\frac{x_{i}}{ N}+p_{k-1},\frac{kx_{i}}{N}]\) for rounds k where he remains active. In round 1, \(p_{0}=0\) and \(\bar{\beta }_{1}^{i}(x_{i};\mathbf {p}_{0})=x_{i}/N\) is determined. Suppose i does not drop at round \(k-1\), i.e., \(p_{k-1}\le \bar{\beta }_{k-1}^{i}(x_{i};\mathbf {p}_{k-2})\). Then, \(\bar{\beta } _{k-1}^{i}(x_{i};\mathbf {p}_{k-2})\le (k-1)x_{i}/N\) implies
and thus the interval \([\frac{x_{i}}{N}+p_{k-1},\frac{kx_{i}}{N}]\) is non-empty and \(\bar{\beta }_{k}^{i}(x_{i};\mathbf {p}_{k-1})\in [\frac{ x_{i}}{N}+p_{k-1},\frac{kx_{i}}{N}]\) at round k.
Next, we show that bidder i obtains a payoff of at least \(x_{i}/N\) with \( \bar{\beta }^{i}\). Suppose bidder i drops at some round k. Then, \(\bar{ \beta }_{k}^{i}(x_{i};\mathbf {p}_{k-1})\ge x_{i}/N+p_{k-1}\) implies bidder i’s payoff is
If bidder i wins the auction, then \(p_{N-1}\le \bar{\beta }_{N-1}^{i}(x_{i}; \mathbf {p}_{N-2})\le \frac{(N-1)x_{i}}{N}\) and hence bidder i’s payoff is
In either case, bidder i’s payoff is at least \(x_{i}/N\). By Proposition 0, a bidder can guarantee at most \(x_{i}/N\), and thus \(\bar{\beta }^{i}\) is a security strategy.
We now establish that every security strategy satisfies the conditions of the proposition. Suppose to the contrary that \(\bar{\beta }^{i}\) is a security strategy and \(\bar{\beta }_{k}^{i}(x_{i};\mathbf {p} _{k-1})<x_{i}/N+p_{k-1}\) for some k, \(x_{i}\), and \(\mathbf {p}_{k-1}\) such that \(p_{m}\le \)\(\bar{\beta }_{m}^{i}(x_{i};\mathbf {p}_{m-1})\) for \( m=1,\ldots ,k-1\). We show that there are bids for the other bidders such that player i’s payoff is less than \(x_{i}/N\). Consider bids for the other bidders such that (i)\(\ \mathbf {p}_{k-1}\) is the sequence of dropout prices, and (ii) the bids at round k exceed \(\bar{\beta }_{k}^{i}(x_{i};\mathbf {p} _{k-1})\). Then, bidder i drops at round k and his payoff is \(\bar{\beta } _{k}^{i}(x_{i};\mathbf {p}_{k-1})-p_{k-1}<x_{i}/N\), which contradicts that \( \bar{\beta }^{i}\) is a security strategy.
Suppose that \(\bar{\beta }^{i}\) is a security strategy and \(\bar{\beta } _{k}^{i}(x_{i};\mathbf {p}_{k-1})>kx_{i}/N\) for some k, \(x_{i}\), and \( \mathbf {p}_{k-1}\) such that \(p_{m}\le \)\(\bar{\beta }_{m}^{i}(x_{i};\mathbf {p }_{m-1})\) for \(m=1,\ldots ,k-1\). Consider bids of the other bidders such that (i)\(\ \mathbf {p}_{k-1}\) is the sequence of dropout prices, (ii) some bidder \(j\ne i\) drops at round k at price \(p_{k}=kx_{i}/N+\varDelta \) for \( \varDelta >0\) and \(p_{k}<\bar{\beta }_{k}^{i}(x_{i};\mathbf {p}_{k-1})\), and (iii) for rounds \(k^{\prime }>k\) the remaining bidders bid \(\frac{x_{i}}{N} +p_{k^{\prime }-1}\).
There are two cases. First, if bidder i drops at some round \(k^{\prime }>k\) at a price strictly less than \(\frac{x_{i}}{N}+p_{k^{\prime }-1}\), then his payoff is \(\bar{\beta }_{k^{\prime }}^{i}(x_{i};\mathbf {p}_{k^{\prime }-1})-p_{k^{\prime }-1}<x_{i}/N\), which contradicts that \(\bar{\beta }^{i}\) is a security strategy.Footnote 13 Second, if bidder i wins the auction, then he pays
and hence his payoff is \(x_{i}-p_{N-1}<x_{i}/N\), which contradicts that \( \bar{\beta }^{i}\) is a security strategy. \(\square \)
Proof of Proposition 5
Using the same argument as in Proposition 1, it is immediate that each bidder i’s security payoff is at most \((x_{i}-p_{0})/n\). We show the given strategy achieves \((x_{i}-p_{0})/n\) , and therefore the given strategy is a security strategy in \(\varGamma (n,p_{0})\) and the security payoff is \((x_{i}-p_{0})/n\).
Let \(x_{-i}\) and \(\beta ^{-i}\) be arbitrary, and let \(p_{1},\ldots ,p_{n-1}\) be the sequence of dropout prices that results. Suppose that bidder i is not among the first \(\hat{k}-1\) bidders to drop. We show, by induction, that for \(k\in \{1,\ldots ,\hat{k}-1\}\) we have (i) \(p_{k}-p_{0}\le k(x_{i}-p_{0})/n\) and (ii) \(p_{k}-p_{k-1}\le (x_{i}-p_{k-1})/(n-k+1)\). Assume \(x_{i}>p_{0}\). Since bidder i is not the first to drop, then
i.e.,
Hence, (i) and (ii) hold for \(k=1\).
Assume that (i) and (ii) hold for some \(k^{\prime }<\hat{k}-1\). We show they hold for \(k^{\prime }+1\). By the induction hypothesis, \(p_{k^{\prime }}-p_{0}\le k^{\prime }(x_{i}-p_{0})/n\) and hence \(k^{\prime }<n\) and \( x_{i}>p_{0}\) imply \(p_{k^{\prime }}-p_{0}\le x_{i}-p_{0}\), i.e., \( p_{k^{\prime }}\le x_{i}\). Since bidder i did not drop at \(k^{\prime }+1\le \hat{k}-1\), then
which establishes (ii) for \(k=k^{\prime }+1\). This inequality can be rewritten as
By the induction hypothesis, \(p_{k^{\prime }}\le k^{\prime }(x_{i}-p_{0})/n+p_{0}\) and hence
and (i) holds for \(k=k^{\prime }+1\).
If bidder i drops in round \(\hat{k}\), then his payoff is \((x_{i}-p_{\hat{k} -1})/(n-\hat{k}+1)\). Since \(p_{\hat{k}-1}\le (\hat{k} -1)(x_{i}-p_{0})/n+p_{0}\), then
If bidder i is not among the first \(n-1\) bidders to drop, then \( p_{n-1}-p_{0}\le (n-1)(x_{i}-p_{0})/n\). He wins the auction and his payoff is
Hence, \(\bar{\beta }^{i}\) guarantee’s bidder i a payoff of \((x_{i}-p_{0})/n\) and is therefore a security strategy.
If \(x_{i}<p_{0}\), then bidder i’s payoff is negative if he wins the auction. We first show that \(\bar{\beta }^{i}\) guarantees bidder i a payoff of a least \((x_{i}-p_{0})/n\). Since \(\bar{\beta }_{1}^{i}\) calls for bidder i to drop immediately, his payoff is zero unless he wins the auction. The later occurs only if all \(n-1\) other bidders drop immediately and ties are broken in bidder i’s favor. In this case, bidder i’s payoff is \( x_{i}-p_{0}\). Since this occurs with at most probability 1 / n, his expected payoff is at least \((x_{i}-p_{0})/n\). \(\square \)
Proof of Proposition 6
Write \(\bar{v} _{N-(k-1),p_{k-1}}(x_{i})\) for the security payoff of a bidder with value \( x_{i}\) in the subauction \(\varGamma (N-(k-1),p_{k-1})\). Suppose that \(\bar{\beta }_{k}^{i}(x_{i};\mathbf {p}_{k-1})<(x_{i}-p_{k-1})/(N-(k-1))+p_{k-1}\) for some k, \(x_{i}\) and \(\mathbf {p}_{k-1}\) such that \(p_{0}\le p_{1}\le \cdots \le p_{k-1}\). We show that \(\bar{\beta }^{i}\) is not a perfect security strategy. In particular, we show that \(\bar{\beta }^{i}|_{\mathbf {p} _{k-1}}(x_{i})\) yields a payoff less than \(\bar{v}_{N-(k-1),p_{k-1}}(x_{i})\) for some \(x_{-i}\) and \(\beta ^{-i}\).
From Proposition 5, the security payoff of bidder i in \(\varGamma (N-(k-1),p_{k-1})\) is \(\bar{v} _{N-(k-1),p_{k-1}}(x_{i})=(x_{i}-p_{k-1})/(N-(k-1))\). Let \(x_{-i}\) and \( \beta ^{-i}\) be such that the bids of the other \(N-k\) bidders in round 1 of \( \varGamma (N-(k-1),p_{k-1})\) are greater than \(\bar{\beta }_{1}^{i}|_{\mathbf {p} _{k-1}}(x_{i})=\bar{\beta }_{k}^{i}(x_{i};\mathbf {p}_{k-1})\). Then, bidder i drops in round 1 and his payoff is
Hence, \(\bar{\beta }_{i}\) is not a perfect security strategy.
Suppose that \(\bar{\beta }_{k}^{i}(x_{i};\mathbf {p} _{k-1})>(x_{i}-p_{k-1})/(N-k+1)+p_{k-1}\) for some k, \(x_{i}\) and \(\mathbf {p }_{k-1}\) such that \(p_{0}\le p_{1}\le \cdots \le p_{k-1}\). Let \(x_{-i}\) and \(\beta ^{-i}\) be such that (i) one of the other \(N-k\) bidders in \(\varGamma (N-(k-1),p_{k-1})\) has a dropout price \(\hat{p}_{k}\) satisfying
and (ii) the remaining bidders’ dropout prices are above \(\bar{\beta } _{1}^{i}|_{\mathbf {p}_{k-1}}(x_{i})=\bar{\beta }_{k}^{i}(x_{i};\mathbf {p} _{k-1})\). Then, bidder 1 does not drop out in round 1 of \(\varGamma (N-(k-1),p_{k-1})\), but enters the subauction \(\varGamma (N-k,\hat{p}_{k})\). From Proposition 5, the largest payoff he can guarantee himself in this subauction is \(\bar{v}_{N-k,\hat{p}_{k}}(x_{i})=(x_{i}-\hat{p}_{k})/(N-k)\). We have that
Hence, \(\bar{\beta }_{i}\) is not a perfect security strategy. \(\square \)
Rights and permissions
About this article
Cite this article
Van Essen, M., Wooders, J. Dissolving a partnership securely. Econ Theory 69, 415–434 (2020). https://doi.org/10.1007/s00199-019-01177-9
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00199-019-01177-9