Abstract
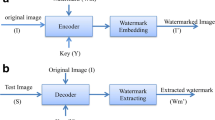
Digital watermark can be used for image ownership verification or authentication. In this paper, we propose a new image authentication plan concentrating on its security performance. Digital watermark is first turbo coded, scaled and then processed in wavelet domain. To enhance security level, public key cryptosystem is utilized to replace traditional watermark key. Simulation results are finally given by experiment.
Similar content being viewed by others
References
Diffie D, Hellman M. New Directions in Cryptography.IEEE Transactions on Information Theory, 1976,22 (6): 644–654.
Kuroda K, Nishigaki M, Soga M,et al. A Digital Watermark Using Public-key Cryptography for Open Algorithm.http://charybdis. mit. scu. edu. au/~mantolov/CD/CITA2002/papers/131-21.pdf, March 2004.
Berrou C, Glavieux A. Near Optimum Error Correcting Coding and Decoding: Turbo-Codes.IEEE Transactions on Communications, 1996,44(10):1261–1271.
Mallat S G. Multifrequency Channel Decompositions of Images and Wavelet Models.IEEE Transactions on Acoustics, Speech, and Signal Processing, 1989,37(12):2091–2110.
Chou J, Ramchandran K. Robust Turbo-Based Data Hiding for Image and Video Sources.Proceedings of ICME 2002. New York: IEEE Press, 2002. 565.
Cvejic N, Tujkovic D, Seppanen T. Increasing Robustness of an Audio Watermark Using Turbo Codes.Proceedings of ICME 2003. New York: IEEE Press, 2003. 217.
Cox I J, Kilian J, Leighton F T,et al. Secure Spread Spectrum Watermarking for Multimedia.IEEE Transactions on Image Processing, 1997,6(12): 1673–1687.
Author information
Authors and Affiliations
Corresponding author
Additional information
Foundation item: Supported by the National Natural Science Foundation of China (90104005) and the National High Technology Research and Development Program of China (2001AA144060)
Biography: YANG Qing (1977-), male, Ph. D. candidate, research direction: digital watermark, coding theory.
Rights and permissions
About this article
Cite this article
Qing, Y., Ke-fei, C. A secure public-key image authentication plan. Wuhan Univ. J. Nat. Sci. 10, 289–292 (2005). https://doi.org/10.1007/BF02828671
Received:
Issue Date:
DOI: https://doi.org/10.1007/BF02828671